How to filter wan output through linux box
-
Hello. Sorry if this has been answered before, but I can't find it anywhere.
I want to have a linux box sitting between pfSense and my modem. The reason for this is that I want to run a vpn on it. I know it can be done as part of pfSense, but I need to change vpn servers fairly often, and doing it within pfSense is a pain. On a separate box, I can just click once. The external box has two ethernet ports.
So I'm looking to do this:
pfSense (LAN 192.168.4.0/24) -->> 192.168.4.31 external box 192.168.1.2 ->> modem 192.168.1.1
Ideally I'd like to set up some rules to divert some sites directly to the web via the WAN interface, and the rest through the external box and the vpn app mounted there.
I have set up the external box, and installed the vpn app, and it works fine locally. But I haven't been able to work out how to divert traffic there from pfSense.
(I could always put a default route on each machine, but then I'd have to change it back and forth when I wanted to bypass the vpn)
Nothing I've tried works. Suggestions would be appreciated!
-
@kdv666
You have to disconnect the "external box" from your LAN and set up a separate transit network between it and pfSense. This might also be a VLAN hooking up on your LAN. Then add a static route for your LAN network to it and point it to pfSense.
After that you can policy route to it what ever you want. -
Hi, and thank you. I very much appreciate your taking the time and trouble to try to help me out.
The box between pfSense and the modem is called "ada". (After Ada Lovelace)
At the moment, the eth0 port is connected directly to my lan, it's IP is 192.168.4.31. If I understand what you wrote, I should unplug that cable from my lan, and ... not sure, set up a new net, eg 192.168.5.1 on ada and 192.168.5.2 on ... a vlan on my lan using a smart switch perhaps?
I'm not sure where the static route that you mention is set up. On pfSense, or on ada... ? I'd really appreciate a few more details there.
Sorry for being obtuse. I haven't done much in the routing sort of areas, so I'm feeling my way a bit in the dark. I really appreciate your holding a candle for me.
Regards
-
The easiest way to the ada into a separate network segment is living it plugged as it is, but set up a VLAN on both ada and pfSense.
This requires that the device is VLAN capable. I don’t know if it is.The static route for your LAN network has to be added to the ada and point to pfSense VLAN IP.
Additionally you have to configure masquerading (S-NAT) on the ada on its WAN facing interface, so that response packets come back to it. -
Thank you once again. I’m going to try it out as best I can and hope I can get it going. I really appreciate your help.
-
@kdv666 Just set it up like this
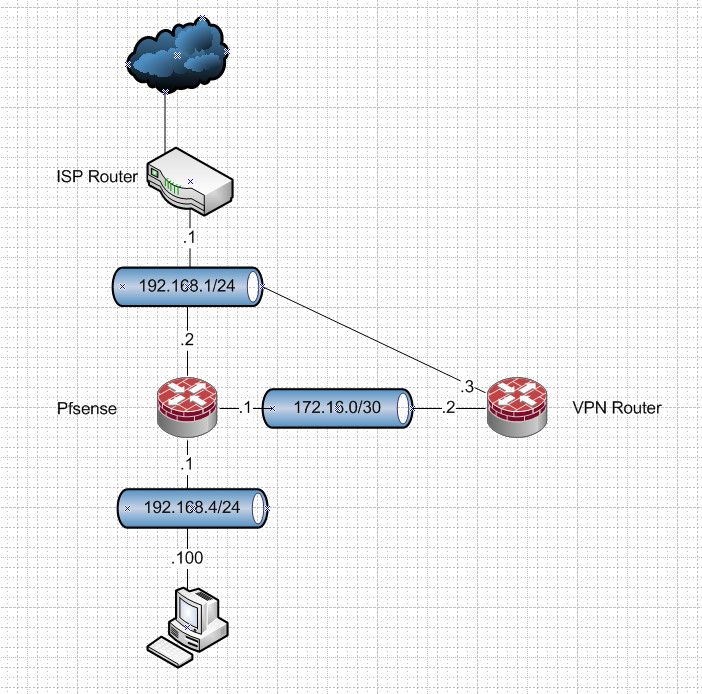
This is transit network to the other "router" doing the vpn stuff.
If the network behind your "modem" is 192.168.1 then its not a "modem" its a gateway doing both modem and router duties (nat)
If you just hang this vpn router off a transit to pfsense you can use pfsense to policy route what taffic you want send to the vpn router.
-
Wow, thank you. You know what they say about "one picture". Very clear. I think it's a similar setup to what @viragomann was describing, but it's clearer in my head from your diagram.
I'm assuming that the pfsense would regard its link to the modem/router as a standard WAN. And its link to the local network is a standard LAN. Its link to the VPN box must be an OPTx, I assume. From reading the pfsense docs, I need to give it a specific gateway so that pfsense can treat it as an internet connection rather than a LAN connection. Am I right, or am I totally at sea? So would the OPT gateway have its pfsense IP, with the upstream port being the VPN machine's ethernet IP?
I do need my network to be able to ssh into the VPN router, so that I can change the VPN host as needed. So I guess I'll have to manually route from 192.168.4/24 to 172.16.0/30.
It's really gratifying to see how people here are prepared to give their time and effort to help others.
-
<sigh> I thought I had it. I really did. I underestimated my own stupidity.
I set it up just like in the diagram, and thought all would be well. But the machines just don't want to talk properly to each other.
On the good side, my home network 192.168.4.0/24 was able to talk to pfSense 192.168.4.7, and in turn to the modem/router. That side of things went fine.
And pfSense 192.168.5.1/30 was able to ping the VPN router (ada). But ... ada wasn't able to ping pfSense.
ada was able to talk to the modem/router, and thence to the internet. But not pass through anything from pfSense.
My network (192.168.4.0/24) reached ada, but indirectly ... via the ports connected to the modem/router, 192.168.1.100 and 192.168.1.101.
I obviously have to do a lot more reading. I've already started, and can't for the life of me see where the problem lies.
The gods send these things to keep us humble!
-
@kdv666 said in How to filter wan output through linux box:
ada wasn't able to ping pfSense.
What rules did you put on the transit interface - out of the box there would be no rules on a new interface. So no ada wouldn't be able to ping pfsense
You have to setup the routing on on both, where your going to nat - or if your going to triple nat. And the appropriate firewall rules.
I personally would not set it up this way. Why are you changing vpns so often - you understand pfsense could have multiple vpn connections setup. Switching to an endpoint of vpn service would be as simple as changing the IP in the vpn client config to where you point. Or you could have multiple different vpn services setup, etc.
If I for some crazy reason wanted to route to different vpn services - I would just set them all up on pfsense directly. Not that its all that hard to do it this way - its just easier to manage if done on pfsense directly.
If you were running on netgate appliance - you could use the import feature to help setup your connection. This "might" be something that will work once they allow for + to be installed on your own hardware for home/lab use.. Which should be sometime soon (when its ready) ;)
Running the vpn connection directly on the edge router (pfsense) is much easier than a 2nd router in your network. Especially if your not well versed in such a setup. Pretty much every day there is some post around here were someone setups up asymmetrical flow, and no understanding of what a transit network actually is, etc.
-
Hi. Didn't get to the point of masquerade. I just wanted to make sure they could talk to each other first.
Of course I set them all up, I didn't just plug them in and expect them to work. For the record, the outputs of "netstat -r" were:
On the pfSense machine ...
Internet:
Destination Gateway Flags Netif Expire
default 192.168.1.1 UGS em0
localhost link#3 UH lo0
192.168.1.0/24 link#1 U em0
192.168.1.1 1c:1b:0d:b2:3e:23 UHS em0
192.168.1.100 link#1 UHS lo0
192.168.4.0/24 link#6 U ue0
randi link#6 UHS lo0
192.168.5.0/30 link#7 U ue1
192.168.5.1 link#7 UHS lo0(em0 -> modem/router, ue0 -> my network, ue1 -> VPN box)
On the VPN box:
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
default 192-168-1-1.tpg 0.0.0.0 UG 0 0 0 eth1
link-local 0.0.0.0 255.255.0.0 U 0 0 0 eth0
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
192.168.5.0 0.0.0.0 255.255.255.252 U 0 0 0 eth0And yes, it's enough of a hassle changing the vpn server for me that I would really like to work this out. I have tried many times to add multiple VPN setups to pfSense and it's just too much hassle for me. It's not just a matter of changing the IP. Have to make alterations in the Rules/Gateways, Firewal//NAT, Firewall/Rules, VPN/Openvpn. Each and every time. It would be much easier to to click a mouse on ada.
I need to do it often because I often have to search for a server that isn't blocked by Netflix, Amazon, Stan, and others. As I switch services, the same IP's don't work for each of them. Not to mention when the server goes down ... here in Australia we don't enjoy the reliability of service you might get in America.
I respect that you wouldn't be doing it this way. But I've been greatly annoyed by this for some time, and that's why I'm trying to solve it. I appreciate your suggestions.
-
@kdv666 said in How to filter wan output through linux box:
Have to make alterations in the Rules/Gateways, Firewal//NAT, Firewall/Rules,
No not really..
If you setup VPN A and B on pfsense.. All that would be should be required is change the gateway on the policy route rule to send traffic to A or B..
If you have vpn A pointing to vpn service node 1.2.3.4, and you wan to route to say different node in a different country it would be as simple as changing the IP to 5.6.7.8 in the client config - why would rules need to be changed?
I often have to search for a server that isn't blocked by Netflix, Amazon
Have fun playing wack-a-mole, that is going to be a never ending game.
As to your output there.. What was the rule you put on the 192.168.5 interface in pfsense? Again ada is not going to be able to ping 192.168.5.1 unless you allow that on the new pfsense interface
If you have 192.168.5.1 on pfsense, and 192.168.5.2 on ada - and they are directly connected to each other the only reason they wouldn't be able to ping is firewall rule. Or they are not actually connected, can they see each others mac address for the IP be it 5.1 or 5.2?
-
Hi.
I set up the port on the pfSense machine using pfSense's command line options 1 to create the interface, and 2 set the address. After failing to connect to a manually defined address, I turned on the DHCP server for that port, and set the VPN's matching port to receive the DHCP settings. The latter port was set up with sensible values, so they certainly recognise each other's existence. Still no luck. I used "route add -net 192.168.5.0/30" on both ends, with the appropriate local port as gateway. There were no entries in the iptables on the VPN machine. I don't know the equivalent command for BSD.
I'm going to have a break from it now and do some thinking. Maybe look for some similar situations on the net.
Many thanks indeed for your willingnes to help.
Regards
-
@kdv666 said in How to filter wan output through linux box:
command line options 1 to create the interface, and 2 set the address.
Neither of which would set up the firewall rule on the interface.. As have stated - when you create a new interface there is no firewall rules. So no you wouldn't be able to ping it until you create a rule on the interface to all that.
There is ZERO reason to ever have to create a route to a network that an interface is attached too..
Pfsense not really from cmd line sort of box - you should just go to the gui and assign the interface and enable it put an IP on it and set the firewall rule(s) on the interface.