Isolate Secure LAN, Different IP Range, Management VLAN, Lab LAN
-
Goals:
Setting up the following, but same type firewall rules should accomplish both:
Secure LAN with private data and an isolated lab with physical switches and devices (not just VM). Need to block all internet access, have self-contained isolated 2nd secure LAN to include management VLAN in its range, and will use similar techniques for Lab.
Completed: Trunking vlans of different rfc ranges 192, 172 and 10 from SG-2100. distributed to managed switches, all tagged and working properly.
All internet connections needed are functioning as planned and internet only (no rfc).-
Is there a security risk to having LAN as parent interface for all? LAN is not used for anything else. Should I setup a 2nd interface to be parent to further isolate? Native vlans not used for device connections. Physical access is not a concern.
-
What is the best practice to setup a management VLAN? This is something I cannot get in-depth info on.
I would like this VLAN to be able to manage pfsense and other network devices (i.e. routers, switches), but be isolated via port access and no access to the internet. It is not on the same rfc range as all of the devices.
2a. How does one block all internet access from a vlan, but allow LAN access? Screenshot example could do it and I can figure out the rest.
Is it NAT or gateway based (by not providing one) or firewall rule based.
I have tried the no-NAT, but then cannot access pfsense or anything else. I am not very up-to-speed on NAT yet, obviously... :)- What is the most secure way to separate and isolate an entire 'sub' LAN?
Currently: 1 trunk from 2100 port with VLANS on different ranges into 1 managed switch, with each vlan on its own physical port. Can further trunk to another switch if need be from 2nd, as can be colocated, while netgate cannot. Need it rock solid isolated. Feedback?
(Air-gapped - metaphorically, since will still be connected to pfsense and shared managed switch)
Truly appreciate your time and help!
-
-
- no why would it be if your rules and isolation are setup correctly
- A management vlan is just a vlan that normally has limited access to only "admins" to manage infrastructure or devices. How you accomplish that would be up to the equipment and functionality of said equipment. Best practice is yes to isolate the management of your networking infrastructure from "users" ;)
2a) By default rule is deny... So allow what you want, if you don't end it with an any any rule, then not going to be able to get to the internet.
Example this is a locked down vlan, that can talk lan net, but nothing else - other than what is allowed above that..
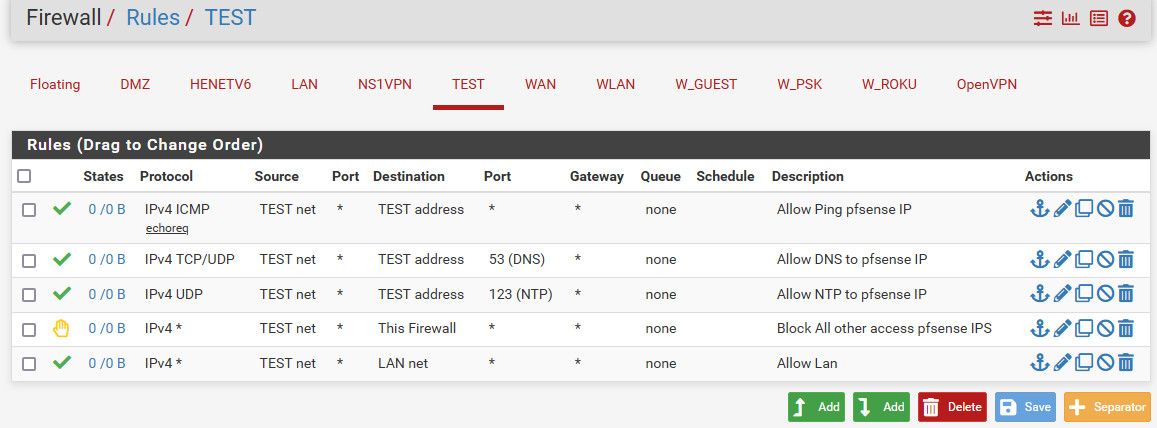
This network would not be able to talk "internet' Since there is no rule that allows any as destination..
- An isolated vlan is an isolated vlan - as long as you have correctly isolated the vlans you will be fine. Now if your talking DOD type level isolation - then your talking full physical isolation, different hardware.. So this network or networks, would be on their own physical switch(es)
This physical isolation could be handled with just dumb switches.. Directly connected to a physical interface on pfsense for example.
-
@johnpoz That is awesome, thank you!!! I’ve been reading and testing for many hours, and could not get those definitive answers.
-
Fair enough. I do not know enough about vlan exploits, other than they exist, so needed to ask.
-
Understood. What firewall rule(s) would allow that vlan to have access to endpoint devices on different subnets/ip ranges? Is it possible for a vlan in a different range to connect to a routers web interface that is only LAN facing and no SSH?
2a. Does NAT still need to be setup for a device that one does not want to access the internet - no outbound?
2a.i Does a gateway still need to be chosen?
2a.ii That is very similar to my internet only vlans, except without the reject all rfc alias. If I would like to use that to isolate a management vlan, could I use the rule you posted, just without the block this firewall, without any further pass rules?
- Got it. Should vlan 1 still be tagged on all the ports of the managed switch with the untagged isolated vlans?
Thank you!
edit: Since LAN is the parent interface of all vlans, by having the allow any/all LAN rule, does that allow that vlan to ping all through the different LAN subnets?
I knew all incoming was blocked by default, but all outgoing too? So no block on WAN or gateway necessary to block outbound?
Sorry for the couple of dumb ones in there, want to make sure I'm grasping it correctly.
Got the management vlan with no internet configured... -
-
- The rules I show, the devices in that vlan would not be able to access anything on pfsense other than ping it, and use its dns and ntp. Not gui or ssh access would be allowed. See the block/reject "this firewall" rule.
This would even prevent test net from access lan net pfsense IP, the whole point of the "this firewall" alias ;)
2a) It doesn't - but if auto it would be, but who cares if your rules do not allow, then the nat would never be actually used.. .In the future if you want to allow say 1 IP on the network to access something on the internet, your nat is already in place, and you just need to add a rule to allow.
- Vlan 1 is never really tagged.. Many low end switches might not even allow that.. Vlan 1 on a switch is just the default "untagged" vlan - while it "can" sometimes be tagged.. But no generally speaking vlan 1 is never tagged.
by having the allow any/all LAN rule, does that allow that vlan to ping all through the different LAN subnets?
Yes if you allow any specific vlan/network it would be able to talk to any other vlan on pfsense, even if the destination vlan has no rules.. The return traffic would be allowed by state. If you want to block lan from talking to something, then put rule on LAN to stop it.
I knew all incoming was blocked by default, but all outgoing too?
Huh? Rules are evaluated as traffic enters an interface.. Outgoing is not really a thing - unless you specifically put in a block egress rule on the floating tab.. Outgoing can only happen if the inbound into pfsense was allowed..
If your setup correctly - isolation of vlans be tagged or untagged doesn't really matter. As long as you only run 1 untagged vlan on any trunk connection. Where untagged might come into play is just being able to plug into a port and get on whatever that untagged vlan is. Normally the default vlan is disabled or changed or not used in enterprise just to help with mistakes.. Its not specifically a security issue, its just the default untagged vlan.
-
@johnpoz Thank you so much again. Understand all.
Couple of clarifications:
- Yes, understood, I was looking to be able to access pfsense and the LAN, but not the internet, in this instance. Either way, everything you said helped clarify it for me and I both understand it and got it configured and working. :))
2a. Mine is manual, but yes, great points and idea.
The allow rule you are referring to, would be an allow any and the gateway or default gateway correct?- Correction: Vlan 1 includes all ports as members, then port 1 (trunk) is tagged in every vlan. Is that correct configuration?
Also, on one of the switches I am looking at (all are good, one is high-end) I noticed that VLAN 1 (under its VLAN ID tab in membership), is an untagged member in every port as well. This includes ports with the assigned untagged VLAN also. That is incorrect?
Should only be the vlan assigned to that port untagged, correct?Okay, and if a block egress rule in floating, that would go on the WAN or other gateway as previously discussed, correct?
edit: 1 neither tagged nor untagged now in ports with other vlans untagged on them. All seems to be working, so thinking that is the correct config. :)
Therefore, now not all ports are members on vlan 1, but port 1 (trunk) is tagged on each vlan on other ports.
ex: VLAN ID. ** Port Member
1 ** 1 17 27 (not a member of ports with vlans assigned untagged)
10 ** 1 2 (vlan 10 U on port 2)
Port 1 tagged on every vlan
(formatting issue so had to use * to separate rather than columns)