SSL error for 3x IP blocklist updates all three from letsencrypt
-
I have three IP list updates failing in PFBlockerNG but I think this is a configuration issue in PFSense. All failed since 30th sept, all three are letsencrypt sites.
https://kriskintel.com/feeds/ktip_ransomware_feeds.txt
https://www.darklist.de/raw.php
https://cybercrime-tracker.net/all.phpTaking kriskintel.com as a test I ran "openssl s_client -showcerts -connect kriskintel.com:443" from shell to see what the OS is going to give me. Low and behold:
CONNECTED(00000003)
depth=3 O = Digital Signature Trust Co., CN = DST Root CA X3
verify error:num=10:certificate has expired
notAfter=Sep 30 14:01:15 2021 GMTSo there is my answer apparently. However. If I run the website through "https://www.ssllabs.com/ssltest/analyze.html?d=kriskintel.com"
Then I get a different story, the root cert is a totally different cert in the chain. On a completely different machine I run openssl again but get this response:
CONNECTED(00000005)
depth=2 C = US, O = Internet Security Research Group, CN = ISRG Root X1
verify return:1
depth=1 C = US, O = Let's Encrypt, CN = R3
verify return:1
depth=0 CN = kriskintel.com
verify return:1Which matches the ssllabs test and my own browser. I have no idea how to correct this on my pfsense box.
-
@jimmychoosshoes said in SSL error for 3x IP blocklist updates all three from letsencrypt:
https://kriskintel.com/feeds/ktip_ransomware_feeds.txt
I saw that domain name yesterday :
Here :
=>
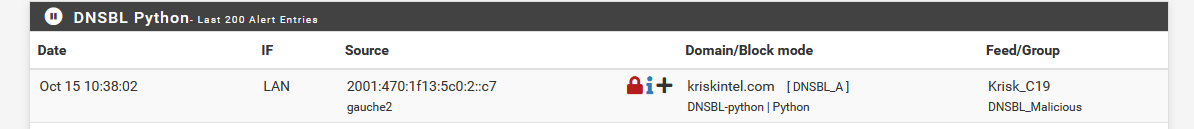
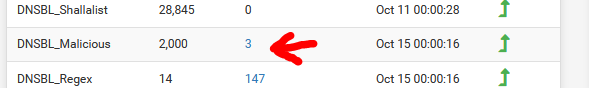
Nice : the "DNSBL_Malicious" has "kriskintel.com" blacklisted : one list blocks another.
About the "certificate has expired" message : see the acme package thread and you'll discover what happened.
The owner of the list, the one that takes care of the certs, missed the important Letenscrypt singing cert change message.@jimmychoosshoes said in SSL error for 3x IP blocklist updates all three from letsencrypt:
I have no idea how to correct this on my pfsense box
Read https://forum.netgate.com/category/72/acme ;)
edit : wait .....
Krisk_C19 -- DNSBL_Malisious is blocking itself ?
-
Found it. I will now hunt for an ca-root-nss.crt (/usr/local/share/certs/ca-root-nss.crt does not exist) as I cannot upgrade to 2.4.5> due to stability issues I found in 2.5.2
thank you for your help.
-
Mmm, you should just be able to delete the expired CA cert from the Certificate Manager as shown here: https://forum.netgate.com/post/999878
-
It isnt in the certificate manager. I have 4 certs in the certificate manager, 1 self cert from when it was installed. Two of our domain subCAs and a test cert.
I wasnt using ACME but my /etc/ssl/cert.pem or /usr/local/share/certs/ca-root-nss.crt was out of date due to me using 2.4.5 I updated the ca-root-nss.crt manually from nss package but also needed to remove the old DST Root CA X3 from ca-root-nss.crt after this openssl retrieved the correct cert CA from the external website and all it well again with list updating.
Incidentally my https://kriskintel.com/feeds/ktip_malicious_domains.txt feed doesnt have "kriskintel.com" in it so they must have refreshed it.
-
@jimmychoosshoes said in SSL error for 3x IP blocklist updates all three from letsencrypt:
Incidentally my https://kriskintel.com/feeds/ktip_malicious_domains.txt feed doesnt have "kriskintel.com" in it so they must have refreshed it.
Here it is :
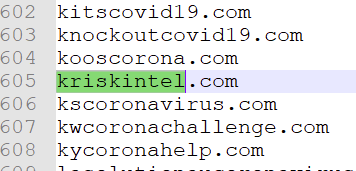
Found it in :
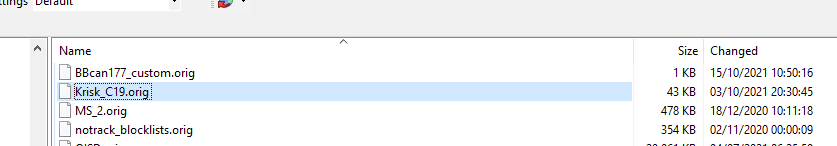
What a joke ;)
-
@gertjan said in SSL error for 3x IP blocklist updates all three from letsencrypt:
https://kriskintel.com/feeds/ktip_malicious_domains.tx
Stranger and stranger. Ive just checked again, not only is kriskintel.com not in my ktip_malicious_domains but NONE of the others in your screenshot are either. This is my "K" list:
(hah it wont let me post all the domins, the board thinks it is spam - suffice to say there are about 30 to 40 "K" domains and none of yours are in there)
Granted, I dont use lots of lists. What lists are you pulling from? Im only pulling from the malicious DNSBL and ransomware IP.