Chrony, PTP, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd)
-
@sergei_shablovsky
Even though Chrony is "Shining Brand New" , i would .. As it is the industry standard.
Still prefer NTP to be the timeserver on pfSenseChrony would be something i'd play with on a separate host , if i wanted to.
/Bingo
-
@bingo600 said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Even though Chrony is "Shining Brand New" , i would .. As it is the industry standard.
Still prefer NTP to be the timeserver on pfSenseImo Chrony is just plan better and can see no reason not to use it on pfsense
- Time synchronisation is better (faster and more accurate synchronisation)
- Better reporting via the combination of
chronyc tracking chronyc sources chronyc sourcestats chronyc clientsSo I would like to see chrony on pfsense. For me it would be cleaner than using my Proxmox host for chrony / site time.
-
@patch Even more:
chrony vs ntp
Things chrony can do better than ntp:chrony can perform usefully in an environment where access to the time reference is intermittent. ntp needs regular polling of the reference to work well.
chrony can usually synchronise the clock faster and with better time accuracy.
chrony quickly adapts to sudden changes in the rate of the clock (e.g. due to changes in the temperature of the crystal oscillator). ntp may need a long time to settle down again.
chrony can perform well even when the network is congested for longer periods of time.
chrony in the default configuration never steps the time to not upset other running programs. ntp can be configured to never step the time too, but in that case it has to use a different means of adjusting the clock (daemon loop instead of kernel discipline), which may have a negative effect on accuracy of the clock.
chrony can adjust the rate of the clock in a larger range, which allows it to operate even on machines with broken or unstable clock (e.g. in some virtual machines).
chrony is smaller, it uses less memory and it wakes up the CPU only when necessary, which is better for power saving.
Things chrony can do that ntp can’t:
chrony supports the Network Time Security (NTS) authentication mechanism.
chrony supports hardware timestamping on Linux, which allows an extremely stable and accurate synchronisation in local network.
chrony provides support for isolated networks whether the only method of time correction is manual entry (e.g. by the administrator looking at a clock). chrony can look at the errors corrected at different updates to work out the rate at which the computer gains or loses time, and use this estimate to trim the computer clock subsequently.
chrony provides support to work out the gain or loss rate of the real-time clock, i.e. the clock that maintains the time when the computer is turned off. It can use this data when the system boots to set the system time from a corrected version of the real-time clock. These real-time clock facilities are only available on Linux, so far.
Things ntp can do that chrony can’t:
ntp supports all operating modes from RFC 5905, including broadcast, multicast, and manycast server/client. However, the broadcast and multicast modes are inherently less accurate and less secure (even with authentication) than the ordinary server/client mode, and should generally be avoided.
ntp supports the Autokey protocol (RFC 5906) to authenticate servers with public-key cryptography. Note that the protocol has been shown to be insecure and has been obsoleted by NTS (RFC 8915).
ntp has been ported to more operating systems.
ntp includes a large number of drivers for various hardware reference clocks. chrony requires other programs (e.g. gpsd or ntp-refclock) to provide reference time via the SHM or SOCK interface.
-
Please describe step-by-step how to properly installing Chrony on pfSense.
Thank You so much!
-
@patch said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
So I would like to see chrony on pfsense. For me it would be cleaner than using my Proxmox host for chrony / site time.
How to ask (with a positive result, of course), the pfSense dev team about including Chrony as package ?
Because in comparison “Chrony vs ntpd”, the Chrony are the winner no doubt.
-
@sergei_shablovsky said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Please describe step-by-step how to properly installing Chrony on pfSense.
Thank You so much!
As I wrote , i would do it on a separate host.
And my preferred target would be a linux (Debian 10)/Bingo
-
@bingo600 said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
would do it on a separate host.
Yeah I am agreement here - while pfsense can do many amazing things, and can run quite a few different services for your network from just a home setup to enterprise level.
Doesn't always mean its the best thing for every job.. If the ntp features do not fit into your wants/needs for your network. Then run ntp on something else..
There could be many reasons why your pfsense box is not the best fit for your networks stable ntp source. For starters - its load will fluctuate as your network runs traffic through it at vary levels throughout the day, other services you might be running on it already can and will effect its temp as loads on those fluctuate.. Depending on what hardware your running it on - might not be suited for say PPS input, etc. This sort of stuff does not make for the most accurate and stable time source - if what your looking for is dead nuts time within a few ms or even nanoseconds :)
If your goal is highly reliable highly accurate ntp source.. Running it on something else is prob going to be best bang for the buck here. Not saying you can not provide ntp from pfsense - but its not all that costly or involved to provide a much better source for your network on something else.. This will give you wide choice in actual time software used, better hardware for time, if all it does provide time, is overall load and temp can be better controlled for more accurate time keeping.. etc..
-
@johnpoz said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
@bingo600 said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
would do it on a separate host.
Yeah I am agreement here - while pfsense can do many amazing things, and can run quite a few different services for your network from just a home setup to enterprise level.
We all love pfSense software, because this we all are here. :)
Doesn't always mean its the best thing for every job.. If the ntp features do not fit into your wants/needs for your network. Then run ntp on something else..
Let’s note, the ACCURATE TIMESTAMP is one of the core things in processing on fw/main gate. This is not something we may name “extra” or “additional”. This is core.
There could be many reasons why your pfsense box is not the best fit for your networks stable ntp source. For starters - its load will fluctuate as your network runs traffic through it at vary levels throughout the day, other services you might be running on it already can and will effect its temp as loads on those fluctuate.. Depending on what hardware your running it on - might not be suited for say PPS input, etc. This sort of stuff does not make for the most accurate and stable time source - if what your looking for is dead nuts time within a few ms or even nanoseconds :)
At this point Let me to be disagreeing with You: in most cases pfSense running on separate server, powerful, with 2 PSU and several WANs to avoid outage.
And of course, FreeBSD daemon to work with PPS source like GPS receiver thru the COM port - eating only smallest fraction of total CPU power and interrupts. So, running You this NTP service + GPS on COM port or not - not making impact on whole system.If your goal is highly reliable highly accurate ntp source.. Running it on something else is prob going to be best bang for the buck here.
As I note several post before, there are several BIG disadvantages of this:- round trip to other node and back (thru the switch, other system drivers, etc..) impact on accuracy of timestamp. Because the are measurement in milliseconds / nanoseconds;
- you need care about extra one server (time server), this mean double PSU, double Eth connection, best available servers hardware, memory, enterprise (mean big MTBF hours), etc...
Not saying you can not provide ntp from pfsense - but its not all that costly or involved to provide a much better source for your network on something else.. This will give you wide choice in actual time software used, better hardware for time, if all it does provide time, is overall load and temp can be better controlled for more accurate time keeping.. etc..
Another time not agree: now are quite little a choice, ntpd or Chrony. Please look at the comparison table.
-
@sergei_shablovsky said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
now are quite little a choice
What about openntpd, ntpsec and if windows shop just windows way of doing it, and there is also just sntp - my point was more to what ntp implementations are primary choice for your OS your wanting to run.. And how it integrates with the hardware your wanting to run it on.
this mean double PSU, double Eth connection, best available servers hardware, memory, enterprise (mean big MTBF hours), etc...
If your worried about NTP in the enterprise.. I highly doubt you would be doing it on pfsense to be honest.. More than likely you would have some ntp appliance or multiple ones most likely, etc.
Sorry but if your goal is ntp.. In an enterprise I sure wouldn't be running it on my firewall/router ;) And more likely than not I wouldn't be setting up any hardware - what would be done is get a box that is designed to provide NTP to the enterprise..
-
@johnpoz said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
@sergei_shablovsky said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
this mean double PSU, double Eth connection, best available servers hardware, memory, enterprise (mean big MTBF hours), etc...
If your worried about NTP in the enterprise.. I highly doubt you would be doing it on pfsense to be honest.. More than likely you would have some ntp appliance or multiple ones most likely, etc.
Sorry but if your goal is ntp.. In an enterprise I sure wouldn't be running it on my firewall/router ;) And more likely than not I wouldn't be setting up any hardware - what would be done is get a box that is designed to provide NTP to the enterprise..
I clearly understand Your point.
But anyway, the so-called “NTP Server” (in case that they cannot obtain PPS thru the radio waves, but only thru the GPS receiver) - is no more than the same 'nix system for embedded platforms, that running inside the device.
This is exactly the same as having separate x86_64 server, but less flexible and more dependent on a yearly payment for device developer for firmware upgrade.Am I wrong here?
-
@sergei_shablovsky said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Sorry my misstyping, I mean that’s phrase made by myself. :)

Furthermore...
Everything you need to know about NTP at enterprise and industrial level can be found here:
https://www.meinbergglobal.com/
Doing NTP well is not easy, because, say, one temperature dependency of crystal can throw the whole thing in the trash.
(Not to mention the delay of the NTP distribution network)That's why this hardware costs so damn much, stability - stability - compensation and stability again.
on pfSense is not worth thinking about it...
(if you want to have close to exact time on your network, choose something like this:
https://nguvu.org/pfsense/network%20time%20protocol%20(ntp)/ntp-server/)More for, say, data centre switches or audio systems, bank App, stock exchange, credit card schemes, NASA :)) - ......it's a big question really...
or PTP (AES67, DANTE, digital audio word clock, etc:
https://en.wikipedia.org/wiki/Precision_Time_Protocol -
@daddygo said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Doing NTP well is not easy, because, say, one temperature dependency of crystal can throw the whole thing in the trash.
(Not to mention the delay of the NTP distribution network)
That's why this hardware costs so damn much, stability - stability - compensation and stability again.
on pfSense is not worth thinking about it...
(if you want to have close to exact time on your network, choose something like this:
https://nguvu.org/pfsense/network%20time%20protocol%20(ntp)/ntp-server/)Please read whole docs carefully.
Here we discuss scheme “pfSense driver receive PPS from local connected GPS device thru COM port”, and nothing about linking to the hardware (CPU frq generator, etc) on which exactly pfSense working.
You may connect pfSense to small Garmin marine GPS with 8-12 channels, or more complicated debice like listed several posts above,- anyway the results (PPS signal) come to COM port of pfSense server.
Let’s to note when You have the “Ethernet” port on Your stand-alone Time-Source device, this mean inside of this device are some firmware that realise ... the same NTP server. And in this case You have another one point of delay because need time for converting PPS signal to answers from NTP server inside the device.This “stand-alone time sync devices” born a lot of years ago, and still live now only because certification system for health, financial, military industry exist. They are not much more than specialized computer device with an GPS and RF receivers modules.
The extremely accurate GPS/radio receiver and robust bullet-proof engineered construction and a bunch of output connectors, - there are only one advantage of this devices.Cheers ;)
-
@daddygo said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
@sergei_shablovsky said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Doing NTP well is not easy, because, say, one temperature dependency of crystal can throw the whole thing in the trash.
(Not to mention the delay of the NTP distribution network)That's why this hardware costs so damn much, stability - stability - compensation and stability again.
on pfSense is not worth thinking about it...
(if you want to have close to exact time on your network, choose something like this:
https://nguvu.org/pfsense/network%20time%20protocol%20(ntp)/ntp-server/)The device here are just for lab using or experiment: the GPS receiver are for hobbyist, and the computing module have no chances to compare with even old 10+ years IBM, Dell, HP servers ;)
-
@sergei_shablovsky said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Please read whole docs carefully.

I don't have a problem with what you've written, but thanks the call for attention.
I have been working on timing theme (PTP stuffs) for years and I thought I would share with you the tools we use in our own radio station network.
https://www.meinbergglobal.com/english/products/ptp-ieee-1588.htm
https://dev.audinate.com/GA/dante-controller/userguide/webhelp/content/clock_synchronization.htm
-
I don’t doubt hardware optimised for time keeping will do better than hardware optimised for firewall functionality.
I don’t think that’s relevant though. The issue is chrony provides better functionality on whatever hardware it runs on. It’s simply better at it’s job, so given the choice, it is the preferred option.
But then again both of the above are answer to the the wrong question. A more relevant question is: is improving the time functionality of high enough priority to actually be done by a company who sells expertises in firewalls. I suspect the answer to this question is no, it will be upgraded when added upstream.
So unless someone outside of Netgate is willing and able to implement and test a chrony port, I can’t see it happening.
-
@daddygo said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Doing NTP well is not easy, because, say, one temperature dependency of crystal can throw the whole thing in the trash.
If you're relying on a crystal, you're doing it wrong. NTP servers are supposed to be traceable back to something called International Atomic Time, which is the average of several atomic clocks around the world. The NTP software averages out the variations and if you have multiple sources (you should have at least 3), your time will actually be better than a single source. That said, however, hardware quality may affect jitter.
-
@patch said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
I don’t doubt hardware optimised for time keeping will do better than hardware optimised for firewall functionality.
Totally agree. In previous replies I just note that most of the modern devices are just “PPS signal source (GPS, RF) + embedded SoC that realize NTP server”
I don’t think that’s relevant though. The issue is chrony provides better functionality on whatever hardware it runs on. It’s simply better at it’s job, so given the choice, it is the preferred option.
But then again both of the above are answer to the the wrong question. A more relevant question is: is improving the time functionality of high enough priority to actually be done by a company who sells expertises in firewalls. I suspect the answer to this question is no, it will be upgraded when added upstream.
Thank You for most relevant reply here ;)
So unless someone outside of Netgate is willing and able to implement and test a chrony port, I can’t see it happening.
May be I have time in this wintertime ;)
P.S. Chrony able to using NTS/NTPsec.
P.P.S.
From Netgate Official docs:
Time and clock issues are relatively common on hardware, but on firewalls they are critical, especially if the firewall is performing tasks involving validating certificates as part of a PKI infrastructure.
...
Not only will getting this all in line help with critical system tasks, but it also ensures that the log files on the firewall are properly timestamped, which aids with troubleshooting, record keeping, and general system management.
-
@jknott said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
If you're relying on a crystal, you're doing it wrong.
Yup,

I did not mean that I produce the time source itself with a crystal, say a VCO
unless I was referring to the fact that all computing devices follow some basic clock, e.g. CPU, BUS, RAM cycles, etc.
So there are a thousand points where time can be lost...
Of course, what you describe is the right approach, but it is also pointed out wherever time is involved, for example here:
(this is one of the behaviors of the NTPd and what would be good) + so this should not be news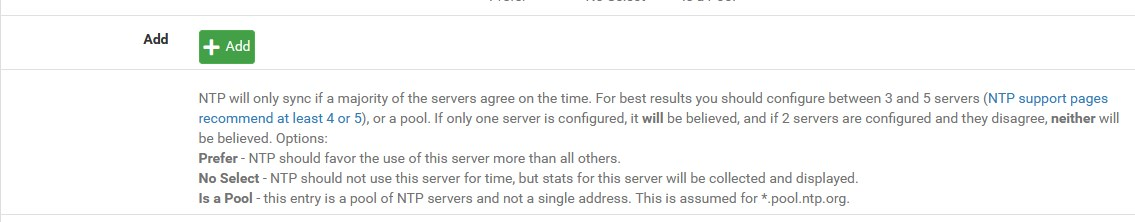
++++edit:
BTW:
https://www.microsemi.com/product-directory/3425-timing-synchronizationHSO with Rubidium, OCXO, TCXO, Quartz = crystal :)
https://timetoolsltd.com/atomic-clocks/high-stability-oscillators/ -
I have 5 sources, 3 stratum 1 and 2 stratum 2. One thing some people don't realize is the math that goes on to calculate the transit delay and then the error from the source. They're described in this article. I had to show that to a co-worker a couple of years ago. He thought each hop was delay from the one it connected to.
GPS is an excellent source as it traces back to IAT, through atomic clocks on the satellite. There's also WWVB. There were a couple of other methods that are pretty much gone now. One was the old 2G CDMA cell network, which used extremely precise time on the phones and the NTSC analog TV signal, where the colour burst frequency was tied to an atomic clock and some stations (PBS) provided the time of day in the vertical blanking interval. Even short wave radio broadcasts from WWV or CHU can be used, though their short term stability is not as good as WWVB. An NTP server that's not traceable back to IAT is supposed to be stratum 15.
BTW, here's a free book from the NIST about time.
From Sundials To Atomic Clocks -
@daddygo said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
HSO with Rubidium, OCXO, TCXO, Quartz = crystal :)
Yep, the crystal will be synced to the source and provide the correct time should you lose the connection to the source.