SG-3100: No trunking on LAN ports
-
So what is the trick on this device to perform trunking on port LAN 1-4? I'm trying to trunk to 2 Cisco switches and I'm following the details in this doc article: https://docs.netgate.com/pfsense/en/latest/solutions/sg-3100/switch-overview.html
I've been trying every possible combination I can think of for a day now and no matter what, nothing is working. I've tried changing my native vlan (untagged) on the Cisco side, tagging, etc. The only way I can get VLANs to be recognized and pass traffic on the SG-3100 is to remove 802.1q on the LAN ports and then I'm trunking all my stuff through a single LAN port. I don't want this - I want specific vlans on specific ports and I need trunking on all ports so I can set my lab up properly.
I've searched around quite a bit on other forums; seems a number of people have had this problem, but no one has posted a full solution to how to get it working.
Does this firewall support trunking multiple and distinct VLANs on each of the LAN ports?????
-
Interface / Assignments / VLANs
Create your VLANs for mvneta1 interface
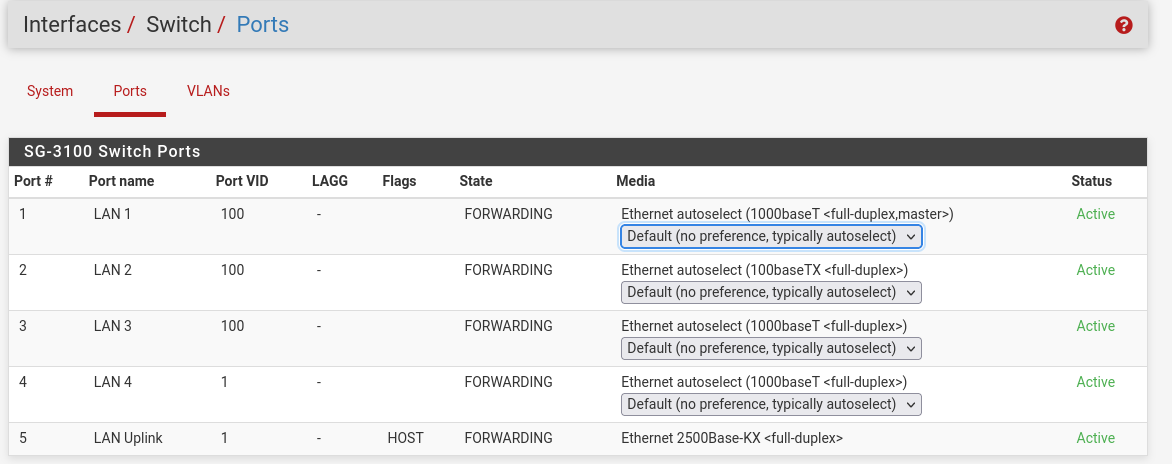
Interface / Switch / VLANs
Create VLAN groups, for an example VLAN10 and VLAN20, port 4 will be trunk in this example:
trunk ports carrying VLAN10 and VLAN20 ports will be 4t,5t and PVID for that interface in Interface / Switch / Ports will be 1.
Access ports won't have the t (tagged) and you will need to set the PVID for that specific VLAN in Interface / Switch / PortsNative VLAN will be anything that reaches port 4 untagged, you can't change native VLAN in pfsense as far as I'm aware of..
-
Thank you for the response. Coming from a Cisco background, I think I've determined how the SG-3100 should work, but I cannot get it to actually pass traffic anything other than my default vlan (vlan 1).
Here are screenshots of my setup. VLAN 1 being native, I'm trying to establish port 1 as a trunk carrying 3 VLANs and port 3 as having a different untagged (native) VLAN. Port 3 will end up carrying two vlans, so it also needs to be a trunk interface. If I understand your last comment, I may not be able to change the "native" on port 3, meaning I would have to tag native on the Cisco side so that the sg-3100 receives a tagged port.
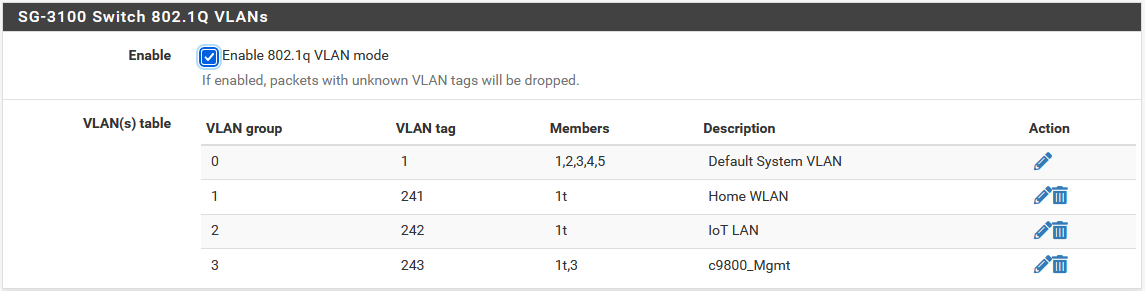
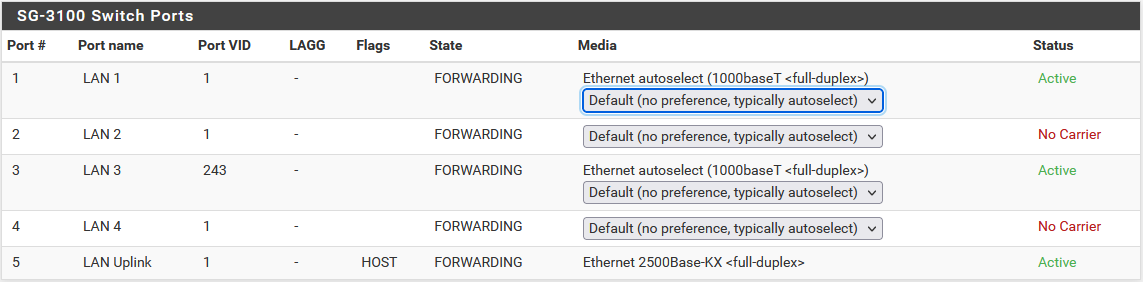
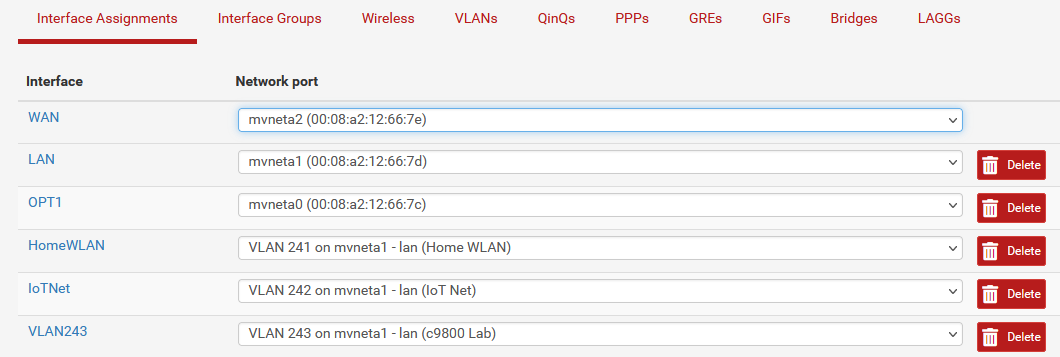
-
You have to Tagged Port 5 to, this is the Switch Uplink to the Firewall CPU. If there is no Tagged, you stuck at this point.
-
In the example below, ports:
1 , 2 , 3 are access ports for VLAN100
4 is a trunk port for VLAN100, VLAN10 and VLAN20.Note that you need to tag port 5 (uplink).
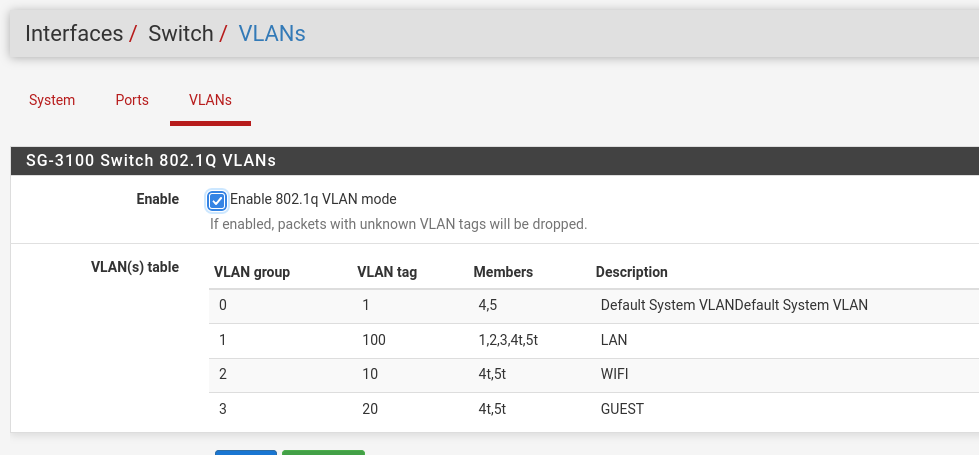
-
@mcury This helped a lot; my trunks are working correctly now.
Thank you very much!
-
I somehow managed to figure out by myself most of what's in this thread - phew. But I do still have a question:
I'd like physical port LAN1 to be an access port for the system default VLAN, VLAN1. I ask this because I have other devices on that same VLAN, also using that VLAN for mgmt.
Most of those devices I am able to change, but one, an AP, I can not. So I'm trying to figure out how to leverage VLAN1 to support it.
Thoughts?
-
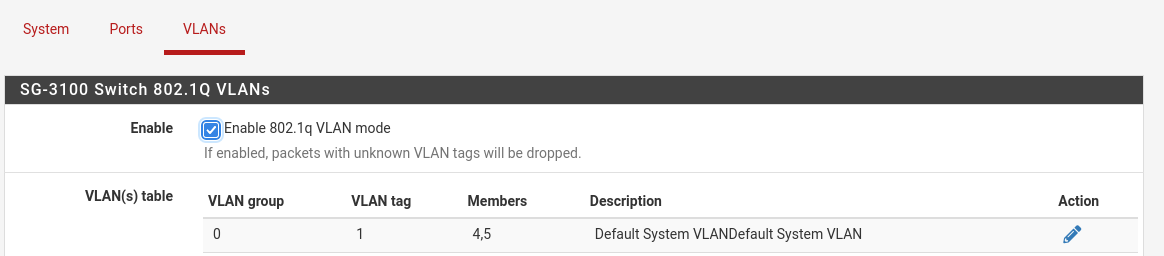
Include port 1 there, it would be port 1,5 (disregard port 4 in the picture above).
Then, in ports, port 1 would be PVID 1
mvneta1 interface would also to have an IP address. -
@mcury
Thank you.I did this... and it appears to work. I say appears because I left it as Members being 1,5. Not 1,5t.
I'm not entirely certain I understand what it means for the 5t being the uplink. Is there an explanation/documentation of this somewhere that I can read to understand what that means? Everything else said I need to do 5t. But in this specific case, when I put 5t (instead of the 5 I have), it doesn't give me an IP on that interface. Which makes me believe it "isn't working"... conversely when I just just 5 (eg, 1,5), I am able to get a response from DHCP on that interface on the correct network.
Does this make sense?
-
@jd3 Port 5 doesn't physically exist, its the uplink to the switch.
Port LAN are the 4 switch ports.
So, to VLAN to work as you intended, you need to leave VLAN1 untagged to the uplink and set the PVID 1 in that specific port (port 1 in your case).You only use TAG when you are connecting to another switch vlan capable, and you want to trunk other vlans to it.
-
@mcury said in SG-3100: No trunking on LAN ports:
You only use TAG when you are connecting to another switch vlan capable, and you want to trunk other vlans to it.
I do intend to connect the SG3100 directly to a switch. My plan is to have ports 1-4 as access on the SG3100 (and then trunk them out of that 2nd switch to other things as needed). And use OPT1 to trunk out of the SG3100 a couple other networks so that the SG3100 is doing routing/firewalling between those networks (in addition to the access ports mentioned above).
I setup something very much the same on a vanilla PC running PFS with 2 NICs: 1 WAN and 1 port that was effectively 100% a trunk (basically a one-armed router/fw).
I bought the SG3100 do to logically the same, but with the physical difference being the integrated switch. So that I could get the full throughput of the switching for ports LAN1-LAN4. And then use OPT1 to manage 2 less bandwidth intensive VLANs in a trunk config.
So far I'm happy with it. And I think it's doing as I'm intending, but I want to make sure I'm not shooting myself in the foot mixing/matching traffic that shouldn't be.
Cheers,
JD -
full throughput of the switching for ports LAN1-LAN4
Ports 1 to 4, in case they are members of the same VLAN, then they would be using the switch bandwidth.
In case ports are members of different VLANs, they would share the 2.5Gbps uplink to the SOC.
It's not a Layer 3 switch, so Inter-Vlan connections would still go to the SOC limited to a 2.5Gbps.
Edit:
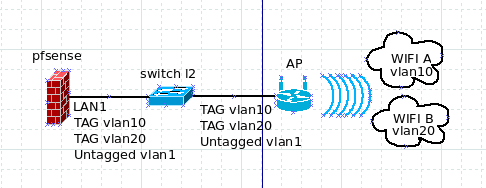
For that AP that you can't change the management VLAN, you can do like the image below and use the VLAN1 for MGMT.. Some cheap switches can't change MGMT vlan too, so this is how I do it.
In this scenario, you would use VLAN1 for MGMT for both the switch and the AP:
-
@jd3 said in SG-3100: No trunking on LAN ports:
My plan is to have ports 1-4 as access on the SG3100 (and then trunk them out of that 2nd switch to other things as needed). And use OPT1 to trunk out of the SG3100 a couple other networks so that the SG3100 is doing routing/firewalling between those networks (in addition to the access ports mentioned above).
Then you don't need to do anything with the 3100 switch config. That is it's default config.
Just add VLANs on OPT1 (mvneta0) like you would with your existing pfSense install.Steve
-
Thanks to you both for the input. Greatly appreciated.