Configuration example for dual firewall setup needed
-
I have a set of dedicated servers which I want to divide into a DMZ and an internal LAN with a dual-firewall setup, where the second firewall should use the first firewall as gate keeper. Firewall 2 should not route WAN to the internal network.
But I'm struggling at several places here, hoping to find help from you experts.I did not succeed to link both firewalls the way I want yet, e.g., I cannot reach the DMZ from the internal network, and I also cannot reach firewall 1 from the internal network or from firewall 2.
My setup is as follows:
- 2 x dedicated bare metal firewalls with 3 NIC ports each (6-Core AMD Ryzen)
- 4 x VM servers: 2 in the DMZ, two inside the internal network (32 Core Ryzen)
- 1 x 12 Port 10G Switch (to be divided into two network segments, first 6 ports used by DMZ, other 6 ports by internal network)
The firewalls are wired as follows:
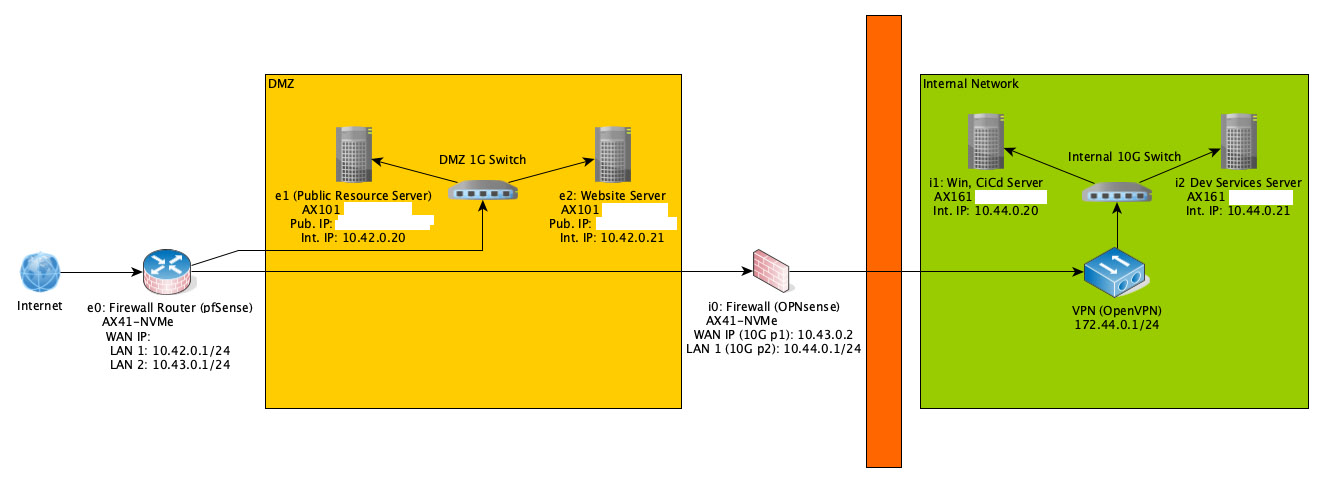
Internet -> FW1 (pfSense) -> WAN (NIC Port 1, 1Gbit) -> DMZ (NIC Port 2, 10Gbit) -> Switch
Internet -> FW1 (pfSense) -> NIC Port 3 (10Gbit) -> Crossover to NIC Port 2 of FW2Internet -> FW2 (OPNsense) -> WAN (NIC Port 1, 1Gbit) -> nowhere* (temporary, to be disabled)
FW1 -> FW2 (NIC Port 2, 10Gbit) via crossover as the link between FW1 and FW2
FW2 (NIC Port 3, 10Gbit) -> internal network (Switch)I have tried too many things to list, created gateways, NAT rules, firewall rules. The problem is likely behind the monitor, though I hope you can guide me a bit by example to do it the correct way. Also, do you think the wiring is any good? Or should it be changed? Currently nothing is running on those servers, thus I'm quite flexible to change things.
- The "WAN" is used only as a fallback and to actually be able to setup things. It will be disabled after the initial configuration has been done / figured out (e.g., I'd have to use a KVM to connect to the server remotely all the time until everything works - already used and paid for that for couple of hours already).
-
@budspencer said in Configuration example for dual firewall setup needed:
I have tried too many things to list,
Yet you can't seem to list the networks you used. Like how many cores matter??... There is zero reason to do this, hang your dmz off 1 firewall is all that is required.
But if your going to use a downstream router/firewall - what was the transit network?
There is nothing to do here other than create the transit network, and simple firewall rules to allow what you want or don't want.
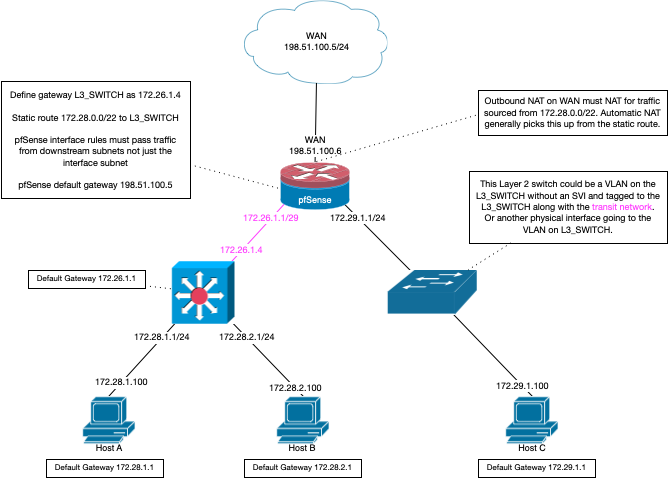
-
You're right, here it is.
The downstream network between firewall 1 and firewall 2 is the mentioned crossover cabling.
Could you provide me a few simpe steps how to correctly configure the transit network?
-
@budspencer well your lan 2 (10.43.0/24 would already be the transit... Do you have hosts on this network. Or is this just the network that connects your routers - if just routers then its transit. You put hosts on it and then yeah your going to have problems.
Are you natting at this downstream firewall? Or did you setup edge to nat the downstream networks? If your not natting did you setup the lan2 rules to allow for the downstream network 10.44? And no idea what your trying to do with that vpn box? Why would you not run that off either of your routers?
-
@johnpoz There are no hosts on 10.43.0.0/24. This network is just used for the link between FW1 and FW2 via crossover cable (FW1 NIC Port 3 (IP 10.43.0.1) to FW2 NIC Port 2 (IP 10.43.0.2)).
That VPN Box is eventually misplaced. OpenVPN is actually running on the OPNsense box.
... I may have just figured out what was missing in this very moment, after some more try & error and your response. I can ping FW1 from FW2. The reason seems to be that for the crossover cabling the option "This interface does not require an intermediate system to act as a gateway" needed to be enabled on the interface. I will give some further feedback after more testing.
Edit: My bad, That was just a terrible mistake when testing. I still cannot reach FW2 from FW1 or vice versa. Do I need to setup a gateway?