Rules not respected?
-
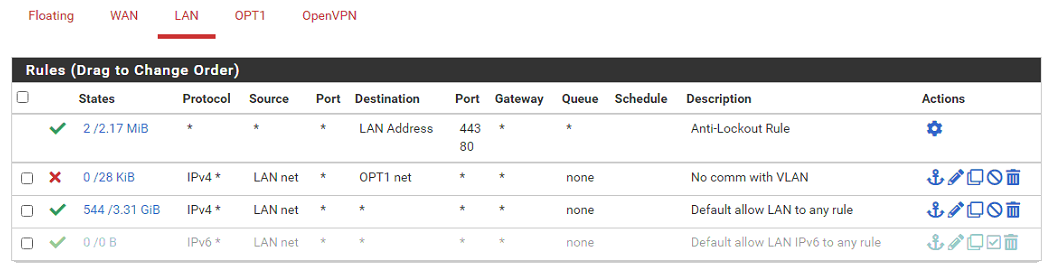
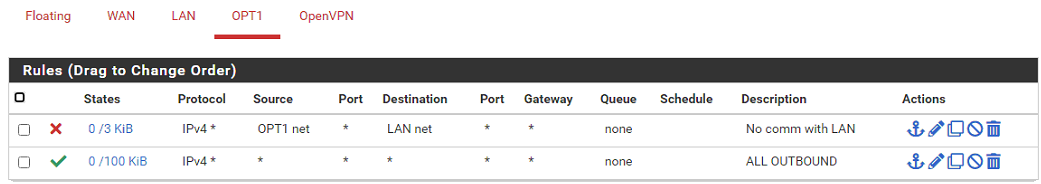
Traffic from LAN to OPT1 blocked
Traffic from OPT1 to LAN blocked
But yet I can ping from a host on LAN to a host on OPT1 and it returns.
What am I missing?
-
@peterlecki Was there a firewall state open when you added the block rules, maybe?
-
@steveits
It's been restarted -
@peterlecki if you log blocks, it is pfSense blocking it? Not a firewall on the server?
-
@steveits
The problem is that it's NOT blocking while it should. -
@peterlecki
Interface rules are "into" the interface.
Your LAN rule should have source from OPT1Net, OPT1 rule should have source from LANNet.The way you have them written it would block the returns, but since there is outbound state for the return, the return is not blocked. That's why it doesn't appear to work.
ping lanhost from opt1host creates outbound state on OPT1 interface.
icmp reply from lanhost gets evaluated against OPT1 rules, there is state because of the outbound from opt1host. -
@mer said in Rules not respected?:
@peterlecki
Interface rules are "into" the interface.
Your LAN rule should have source from OPT1Net, OPT1 rule should have source from LANNet.The way you have them written it would block the returns, but since there is outbound state for the return, the return is not blocked. That's why it doesn't appear to work.
ping lanhost from opt1host creates outbound state on OPT1 interface.
icmp reply from lanhost gets evaluated against OPT1 rules, there is state because of the outbound from opt1host.normal rules for interface 'lan' can never have source 'opt1' ... this is wrong
-
@heper Of course. Unless a packet were spoofed.
But the other point about interface rules being applied on the in direction still holds.So the rules as shown are not going to prevent a packet from opt1host from getting sent because that's an "out" on OPT1.
If the rules were made into Floating rules, and the direction was defined as "out" then OP should get the desired result.
-
@mer
Even though I'm not at all understanding how the LAN interface should have a OPT1net as incoming source, I made it both ways, but as I expected, it made no difference.On the LAN interface there is a default rule to "allow LAN to any" - I didn't create this, it was automatically made during initial setup. As you can see the source is LANnet which is how I made the rule to block traffic to OPT1net. Hence my confusion about your comment to use OPT1net as the source.
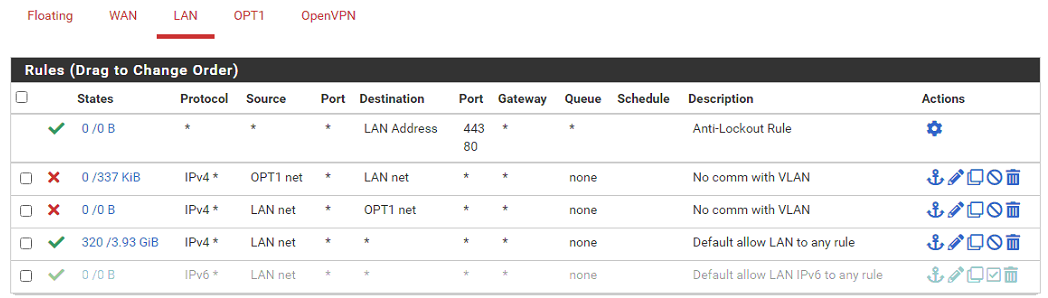
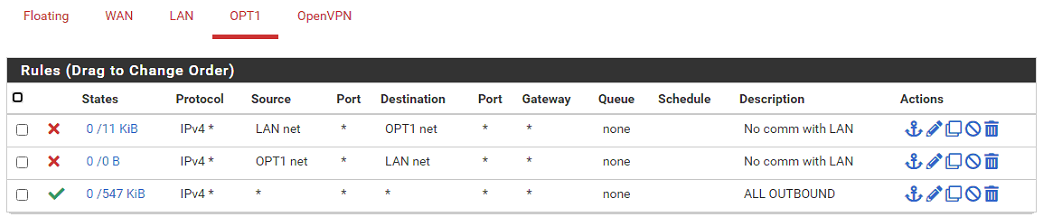
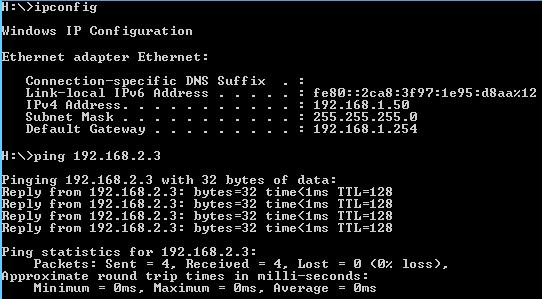
-
@peterlecki I was wrong about that.
-
@peterlecki said in Rules not respected?:
The problem is that it's NOT blocking while it should.
Yeah sorry, I answered late at night and apparently was misremembering. The device firewall comes up here every month or two.
A restart would definitely clear states of course. Have you looked at Diagnostics/States after you ping to see what is open?
-
do you have any floating rules? Your rules are correct for blocking
you sure your actually isolated.. I do see evaluation on your rules - that that sure looks like traffic is flowing through pfsense.
Floating rule would be my guess..
But since you got hits when you put up the wrong source for the interface.. That screams your not actually isolated at Layer 2.
How is lan and opt actually connected to pfsense - if those flow into the same dumb switch you are not actually isolated at layer 2.
-
This was a user error. All is well.