DMZ 1 firewall vs DMZ 2 cascaded firewalls
-
Hello Everyone,
I'm thinking how to implement DMZ (exposed) network + Private LAN on same pfsense box, or with 2 different hardware firewalls.
I'm aware that in theory we can set rules on DMZ interface and LAN interface to have appropriate security and isolation, but i wanted to ask if there is any difference on implementation when 2 cascaded firewalls are used.
Does pfSense treat all interfaces the same ? What's the technical difference between WAN and LAN interfaces? WAN has all blocked by default, LAN has anti-lockout rule and allow all rule on LAN by default. It seems to me that some operations are not the same between WAN and LAN, so i'm wondering if there is any benefit of having the 2nd configuration setup.
Any suggestions appreciated.
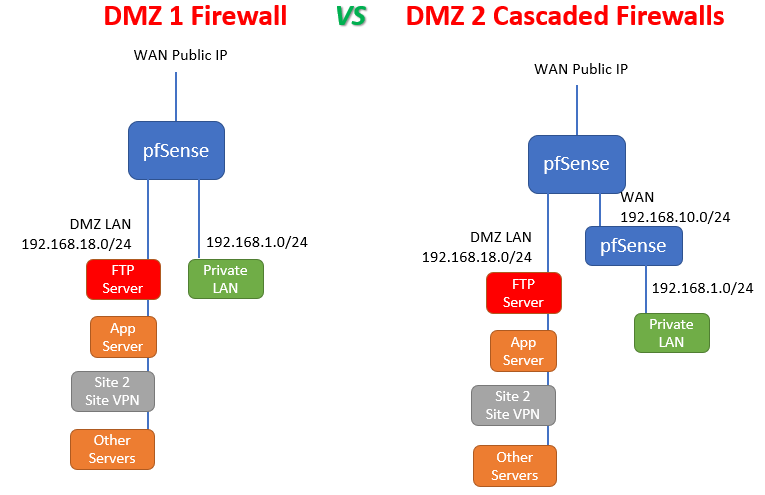
-
@bambos There is really zero reason to do 2 other than more complication, etc..
All interfaces are default deny, all!! of them - its just out of the box lan has a allow rule pre created is all. And yes an anti lockout rule - which both of which can be changed/disabled.
The really only difference with wan, is outbound nat is set to that interface.. And it blocks bogon and rfc1918 - again both of which could be turned off if so desired.
I see no reason to do with 2 what you can do with 1 device - more complication, more power, another thing that could fail, etc..
Reasons for downstream router/firewall are many - but creating a "dmz" wouldn't be a good one if you ask me..
-
@johnpoz thank you, is clear.
im expecting a 6 port device to arrive for this configuration. If i have any questions i will post again. Thank you.