2.5.2 Update has broken Mobile Client IPSec
-
Hi
We've been running a config. that has been working literally flawlessly. I've just upgraded to 2.5.2 and now we get "IKE authentication credentials are unacceptable" in the native Windows 10 VPN client.
We use EAP-TLS with certs. All certs are still valid. Nothing else has changed other than updating to 2.5.2.
Site-to-Site tunnels are OK still.
IKE_AUTH N AUTH_FAILED
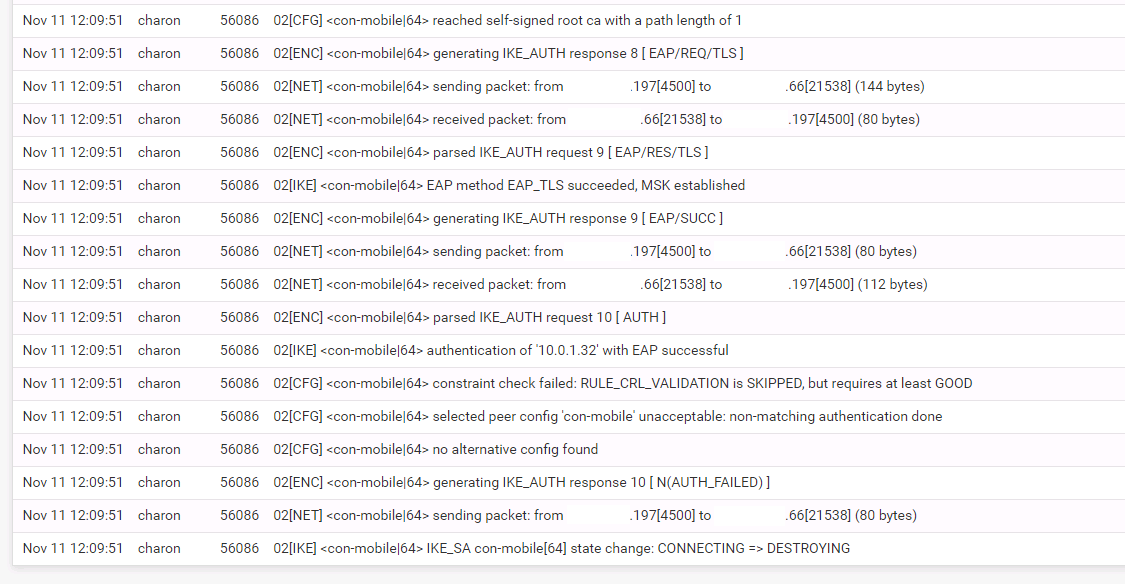
-
PS: The certs are all provided by pfSense Cert Manager
-
If I disable Strict Cert checking it works ok again.
Not sure how to refresh the CRL without completely generating a new one?
-
https://forum.netgate.com/topic/163221/constraint-check-failed-rule_crl_validation-is-stale-but-requires-at-least-good/3
Same issue as this one, which had no responses.
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.