Moving LAN from ETH2 to ix1 on XG-7100-1U
-
You should only need to change the LAN assignment from lagg0.4091 to ix1 directly.
There's no need to use VLAN 4091 at all since it's not going through the on board switch. LAN is untagged at Eth2 currently.
You can leave the other config in place too. lagg0.4091 will just be ignored since it's unassigned.
All other VLANs will remain on the existing ports.Unless you need all the VLANs to be available at the Unifi switch.
Steve
-
@stephenw10 - I do need VLAN's 5, 75, and 69 to be available at the Unifi Switch.
So it sounds like I need to do the following
- Unplug the cable from ETH2
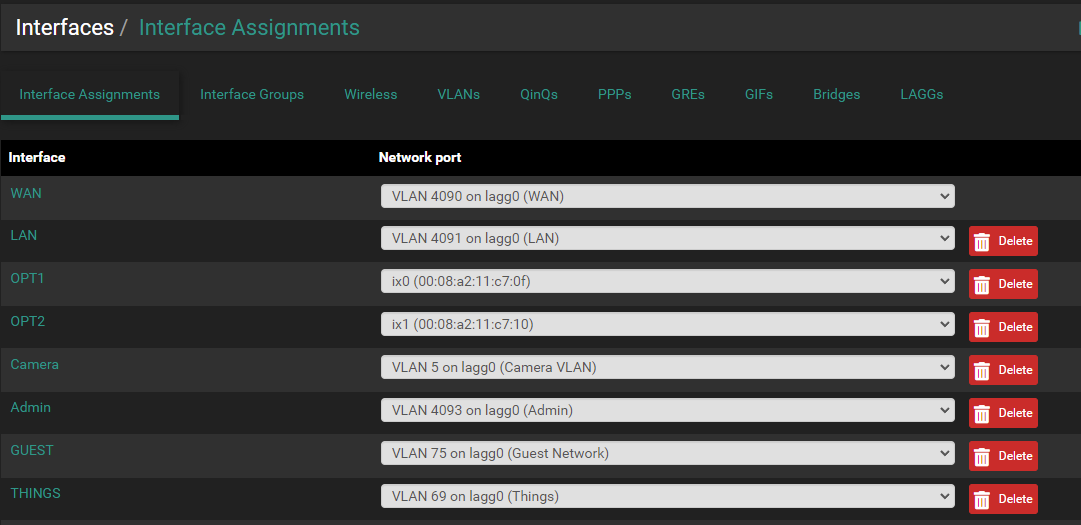
- Delete the OPT2 Interface under Interfaces --> Interface Assignments
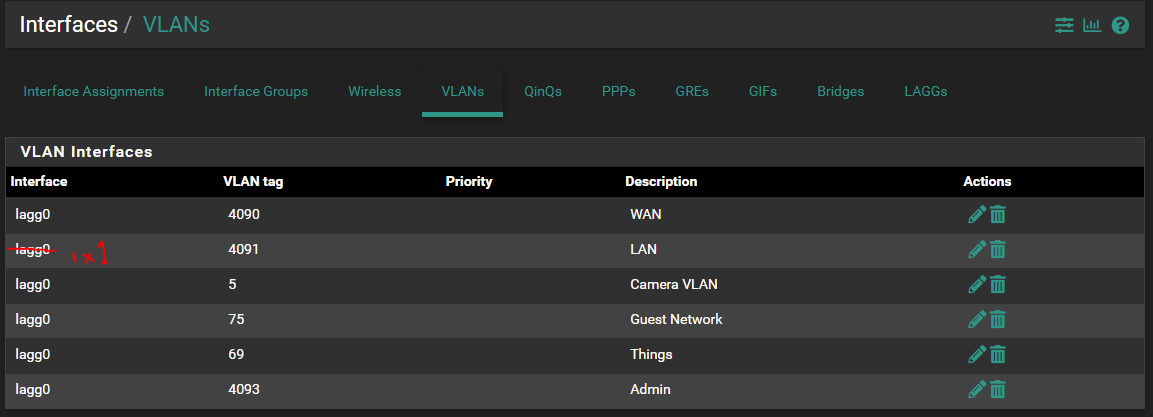
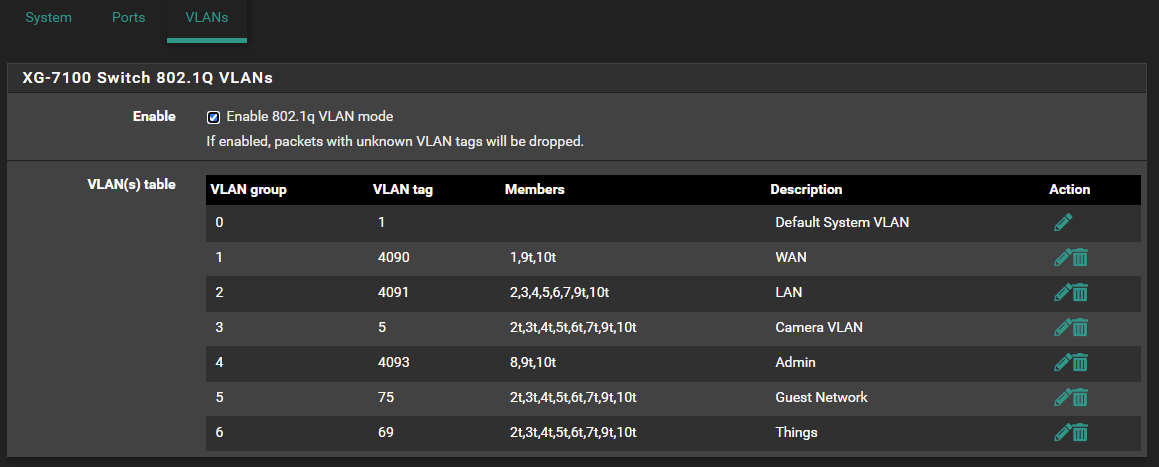
- Remove VLAN's 5, 75, and 69 from the internal switch
- Change all the parent interfaces to be ix1 for VLANs 5, 75, and 69 under Interfaces --> VLANS
- Change the LAN Interface to use ix1 under Interfaces --> Interface Assignments
Does this look correct?
-
Technically you don't need to remove the VLANs from the internal switch but I would do so to makes things less confusing.
You can send the LAN untagged to the Unifi switch or have it tagged as 4091, either will work.
It would just require a different config at the switch.Steve
-
@stephenw10 - Thank you for all your help. I was able to successfully move the LAN interface from ETH2 to ix1. All my VLAN's are also functioning as expected. One note, I did end up having to reboot the XG-7100 after running though my above steps to get the other clients on the various network segments to be able route properly.
-
@stephenw10 This is a topic from 3 years ago but I am going through this same thing.
My question is, when I make the LAN assignment the ix1 port directly everything seems to be working on the firewall side. When I make the LAN assignment (VLAN (Number) on ix1 port) it does not work and I lose connection entirely to the firewall. Before when I make LAN (VLAN (Number) on lagg0) I would not lose connection.
-
If you set LAN to be a VLAN on ix1 then that VLAN has to be configured correctly on whatever is connected to ix1. I assume a switch?
Whenever doing something like this I strongly recommend enabling some other way to access the webgui so you don't get locked out. That might be via the WAN (with limitations) or enabling a management interface on the Eth ports for example.
-
@stephenw10 Stephen thanks for the quick reply. How come I am able to connect to the firewall on ETH2 when its on a vlan tied to lagg without putting the VLAN tag on my device and not when its on a vlan tied to ix1?
-
Because the built-in switch is configured to handle that VLAN. By default VLAN 4091 is tagged on the internal lagg0 link and untagged on Eth ports 2-8. That allows a client to connect to those ports withiut needing to be aware of the VLAN tagging.
-
@stephenw10 Understood. Let me mess around with my switch now and I'll update the thread.
-
@stephenw10 Hey Stephen, so for my case using the ix1 port, my clients must always be tagged. I just want to make sure I'm thinking about it correctly. I changed the VLAN ID from 4091 so its more organized and got my switches/clients connected.
Now I have another question. If I want to use ix1 and ix0 both to carry the same VLANs can I make this happen? I want to have ix1 connected to switch 1 and ix0 connected to switch 2.
-
The clients themselves would not normally have to be tagged because the switch would be untagged on the VLAN on the port it's connected to.
You can create the VLAN interface on ix1 and ix0 but that would be two separate interfaces in pfSense. ix0.100 and ix1.100 for example. They would not be in the same network segment.
If you want them to be in the same segment you would be better off connecting sw2 to sw1 directly. If they are stacking switches you may be able to do a split lagg between them from ix0 and ix1.
-
@stephenw10 Hi Stephen, thanks for you help! I am configuring an MLAG between the switches, not a stack so I wanted to see if this was possible with the ix0 and ix1 ports to somehow combine them. I have ix1 already configured with the VLANs and they are working. The ix1 port only sends out tagged VLANs correct? Because when I connect directly I get nothing unless I specify the VLAN tag which sounds like the correct method.
-
The ix ports don't have to be tagged. You can assign the port directly without any VLAN tagging.
If the switches can do mlag then I would expect that to work with the ix0/1 ports. I'm not sure I've ever seen that on non 'stacked' switches though. You would certainly need some sort of sync connection between the switches.
-
@stephenw10 Interesting, I seem to not be getting anything unless I specify a VLAN tag. I am running a Hyperv testing environment, on the VSwitch I specify the VLANID and I'm up and running and then on the VM level as well. If I do not do this I am not getting any IP from pfsense coming from the ix1 port and I have DHCP enabled.
So in regards to my switches, yes I have an IPL link so they are connected to each other, but each config is configured independently since they are not using the traditional stacking method.
Is it suggested to not use the ix0 and ix1 ports this way? I just did not want to go from switch to switch since there is a point of failure. I wanted to go from firewall, one cable to each switch.
-
How do you have the port assigned? How does the interface show in Interfaces > Assignment?
-
@stephenw10
See below, the reason I have LAN on 4091 is because I used it to connect so I didn't lose connection when messing with the other ports.Interface || Network port
WAN || VLAN4090 on lagg0 (WAN)
LAN || VLAN4091 on lagg0 (LAN)
OPT1 || 1x0 (00:08:a2:12:ca:50)
LANix1 || VLAN 5 on ix1 (LANix1)
Fin || VLAN 20 on ix1 (Fin)
AP || VLAN 21 on ix1 (AP)
UP || VLAN 22 on ix1 (UP)
TESTING || VLAN 23 on ix1 (TESTING) -
Ok so you don't have the untagged ix1 NIC assigned. It's only assigned as VLAN tagged. Thus you can only connect to it using traffic tagged with one of those VLANs.
If you assign ix1 as an interface you could connect a host to that directly without any VLAN tagging.
I would expect to be able to get mlag working to ix0/1 if the switches support it.
-
@stephenw10 So since ix0 and ix1 are on different interfaces, and VLANs can only have one parent interface, I don't see a way to do this on pfsense unless somehow we can create a bridge between both interfaces. I was reading this forum post, https://forum.netgate.com/topic/170174/same-vlans-on-both-ix0-and-ix1/13
-
You can bridge the VLANs across the two interfaces but you really shouldn't!

If you can configure an mlag with one link on each switch then you can just add the VLANs on to the lagg and they should be available in both switches.
-
@stephenw10 Stephen, thanks for all your help!