Resolver IP/Address?
-
I am not a network guy, so bear with me.
Let's say my domain pointing to my network storage is "abcd.1234.com" When I attempt to cast to my Google device, I get a certificate error that lists an address of "https://abcd". Now, this address is the last bit of text on the screen so it could be cut off, but it would be a big coincidence that it cut off right at the domain. Also, if I use http, it will show the error with "http://192.168.xx.xx", so it seems the full address is displayed which makes me wonder why the subdomain "abcd" is only shown when using HTTPS. I am curious if the resolver would be truncating or not providing the full address.
Thank you for any education.
-
@kn4thx does this abcd.1234.com point to your local file server?
I am trying to understand what your trying to do exactly?
A https cert will include common name (CN) and possible SAN (Subject Alternative Names)
This need to match to what you trying to access via your fqdn you used, or yes browsers will balk at the mismatch.
example if your trying to go to https://host.domainX.com and the cert has www.domainX.com as its CN or SAN - it would fail..
Your local dns should resolve whatever fully qualified name your using (fqdn) abcd.1234.com to your local IP say 192.168.1.100
The cert used on this device needs to have correct CN or SAN that matches up with the fqdn your using to resolve it.
Is this fqdn your using a public domain? You could be having issues with it resolving to some public IP, etc. Could you PM this actual fqdn your trying to use, and I can see what that resolves if it does on the public internet.
The resolver would not be truncating anything - what you ask for, would either resolve, or it would fail.. It would not truncate the IP address that your fqdn resolves too.
-
@johnpoz Thank you for the quick reply.
In regards to your first question, I am trying to resolve certificate errors that do not seem to occur inbound from the WAN, but from LAN to LAN. I have an entry for my Synology DDNS in the DNS Resolver to point towards a LAN IP, otherwise I get errors accessing the NAS from within the local network.
The fqdn is a DDNS from Synology which points towards my NAS. The NAS has a Let's Encrypt feature which adds or renews a certificate. I use the included Synology DDNS when creating the certificate. Accessing from the WAN yields no cert errors, only from the LAN.
In the Resolver I have set :
Host: xxxx
Parent: synology-nas.com
IP : 192.168.20.31It behaves as though the address being seen by the receiving LAN device is not what matches the certificate, but since this works great externally, I am not sure. This is why I was curious about the resolver. Also because one of the errors I saw on the Chromecast was referencing the "https://xxxx" address, which shows the host but not the parent domain. I would think it should have shown "https://xxxx.synolgy-nas.com" in the error message. I opened a ticket with Synology to check it out from the other side.
-
@kn4thx its possible your chromecast just resolved hostname via some local discovery method - which yeah would fail on cert since cert would have whatever fqdn, and not just hostname.
I don't have my nas open to the public ;) Unless you have that locked down to known source IPs that your only allowing - I would suggest against having your nas open to the public internet..
So I have never really looked into using acme with nas, etc. But I do have local cert I created and trust to access my dsm with.. And I use that internally.
-
@johnpoz Thank you for that good info. I read up on ACME and definitely need to learn more about that.
I wish I could disable external access, but not everyone is as comfortable with computers as I am for now.
Another question: When I look in the Resolver settings, it lists an SSL/Cert as WebConfigurator. Is this a certificate used when SSL is requested and possibly overriding the default Let's Encrypt certificate once the resolver redirects traffic?
Edit: I have been playing with this after work and have been getting the local 192.168.xx.xx address in the error message now. It seems that the IP is being passed along rather than the host/domain which would explain why the cert doesn't match. Is there a way to check if this is being done by the resolver or the Synology app/NAS?
-
@kn4thx said in Resolver IP/Address?:
I wish I could disable external access, but not everyone is as comfortable with computers as I am for now.
Not sure what that means? Exposing your DSM to the public internet is horrible idea.. Who is remote that would need to access your dsm?
What are they accessing - files? Some other package like web or plex or something?
When I look in the Resolver settings, it lists an SSL/Cert as WebConfigurator
That would be the cert the resolver would use if you were allowing for dot connections to your resolver.. Zero to do with any certs that would be presented by some fqdn you were resolving to an IP.
as to your error message about certs and CN or SAN not matching - that has zero to do with resolver.. DNS resolves a fqdn to an IP that is it..
Could you post up this exact error your seeing..
It seems that the IP is being passed along rather than the host/domain
Huh... if your browser wants to go to say https://host.domain.tld it resolves this to an IP.. It then does a connection to that IP sending the fqdn its trying to go to.. This would be seen in the http handshake via the client hello
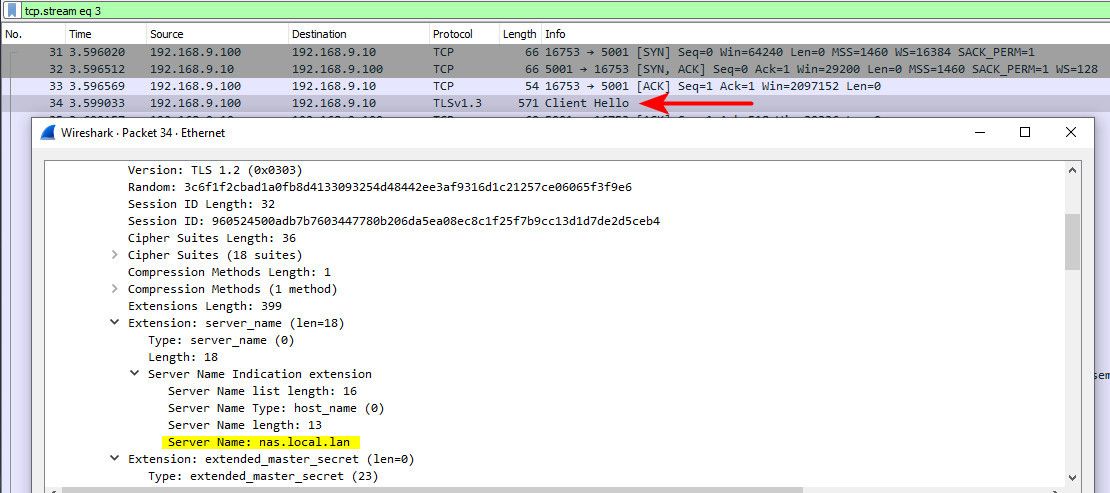
You can see where my client resolved nas.local.lan to my local IP here.

It could be very helpful if you show the error your seeing.. Is this is some browser, is this some app your running on a phone - what?
Are you maybe just going to your nas IP vs the IP:port.. notice in my connection it going to 5001 which is the dsm port.
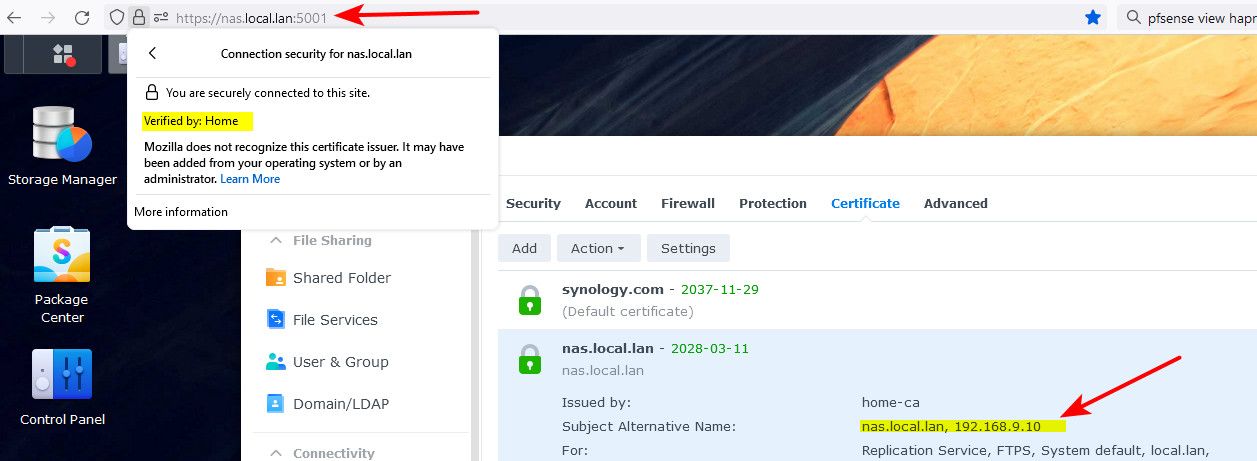
since the url I use to go there is https://nas.local.lan:5001/
The certs your nas uses for different things can be selected/edited.. Notice in my post of my certs the services that are selected for my nas.local.lan cert.
-
Not sure what that means? Exposing your DSM to the public internet is horrible idea.. Who is remote that would need to access your dsm?
What are they accessing - files? Some other package like web or plex or something?I use Plex, yes, though the server app itself is on a PC. I also use the casting feature in the Synology Photos/Video apps and am not familiar enough with split situationDNS but am slowly learning. The others would be using various apps such as the Synology Photos web app and accessing files. Asking them to use a VPN is going to be a fun challenge in the future and would like to go this way. I am still a little confused as to the difference of Quickconnect and the supplied DDNS but Quickconnect is disabled currently.
Huh... if your browser wants to go to say https://host.domain.tld it resolves this to an IP.. It then does a connection to that IP sending the fqdn its trying to go to.. This would be seen in the http handshake via the client hello
I assumed that the Resolver was sending the IP instead of the fqdn and if you look at the error that I took a photo of (Nvidia Shield and Nest Display) you will see where it shows the local IP. I was sometimes getting an error of just the DDNS host name without the parent instead (https://xxxxx instead of https://xxxx.synology-something.com) but lately only get the IP errors. Based on what you say, the resolver should direct to the local IP but send the fqdn which would then line up with the cert.
Hopefully this helps my explanation and I do thank you for your time.
EDIT:
Are you maybe just going to your nas IP vs the IP:port.
I am using the same DDNS host name and parent I enter into the resolver. It works for normal navigation and other uses, just not casting.
The certs your nas uses for different things can be selected/edited
The cert has all available applications selected but there is not one specifically for Photos so I assume that it is tied into the DSM since they use the same ports.
-
Here is the other address showing up in the error. You can see it does not end in a parent domain, only the host name.

-
@kn4thx said in Resolver IP/Address?:
just not casting.
Casting is quite often a multicast thing, and discovery is done via the L2 only.. So casting to something on another network, or if your doing any sort of filtering on your L2 network possible that could fail.
So does it work if you enable it over http? As the error suggest.
-
@kn4thx said in Resolver IP/Address?:
he resolver should direct to the local IP but send the fqdn which would then line up with the cert.
The resolver does not sending any fqdn.. The client would be responsible for that - all it gets from the resolver is the answer to its question, what is the IP (A record) for some fqdn.. It would send back the IP is 1.2.3.4
When the client wants to actually talk to 1.2.3.4 it would send the fqdn, resolver has nothing to do with that.
