PfSense AWS not passing traffic
-
I have installed PfSense from the AWS market place.
I have wan and a lan subnets. I created a new network interface and attached it to the lan subnet and then the PfSense EC2.
I have created a openVPN server and a IPSEC tunnel to my other VPCs.
I can connect to all instances on the lan subnet and in all my vpcs. However I cannot connect to anything from the lan instances behind pfsense. If I ping 8.8.8.8 I get no response but the icmp is logged as allowed traffic. The same happens if I try to connect to other vpc instances. It gets logged as allowed on pfsense but I fail to connect.
The pfsense can ping 8.8.8.8 from the diagnostics menu.Can anyone help me with this?
Thanks,
Paddy -
 J jimp moved this topic from Problems Installing or Upgrading pfSense Software on
J jimp moved this topic from Problems Installing or Upgrading pfSense Software on
-
Do you see anything logged as blocked?
Are trying to route that outbound traffic over either VPN?
Can we see your LAN side rules and the logs showing it passed?
Steve
-
@stephenw10
Hi Stephen thanks for replying.
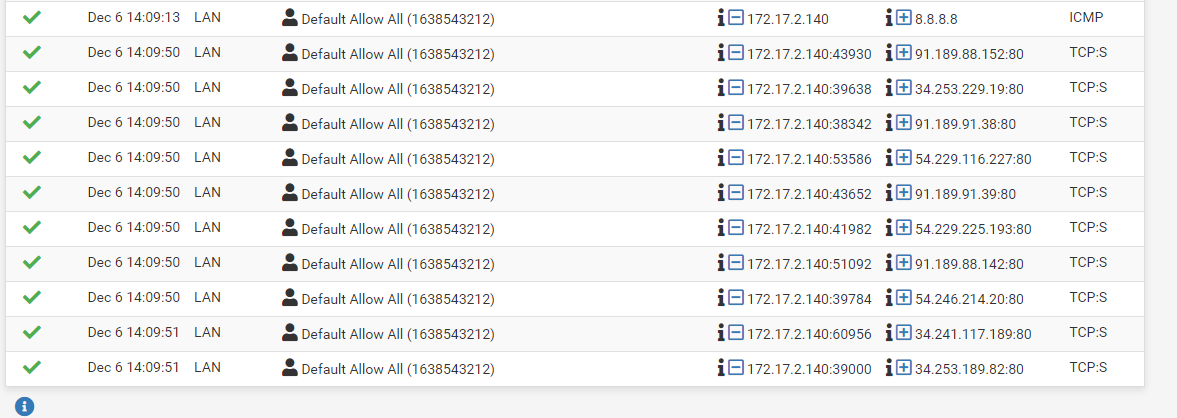
Below are the logs for a ping to google and a apt update on a host on the lan.
Currently there is a single allow all rule on the lan interface.
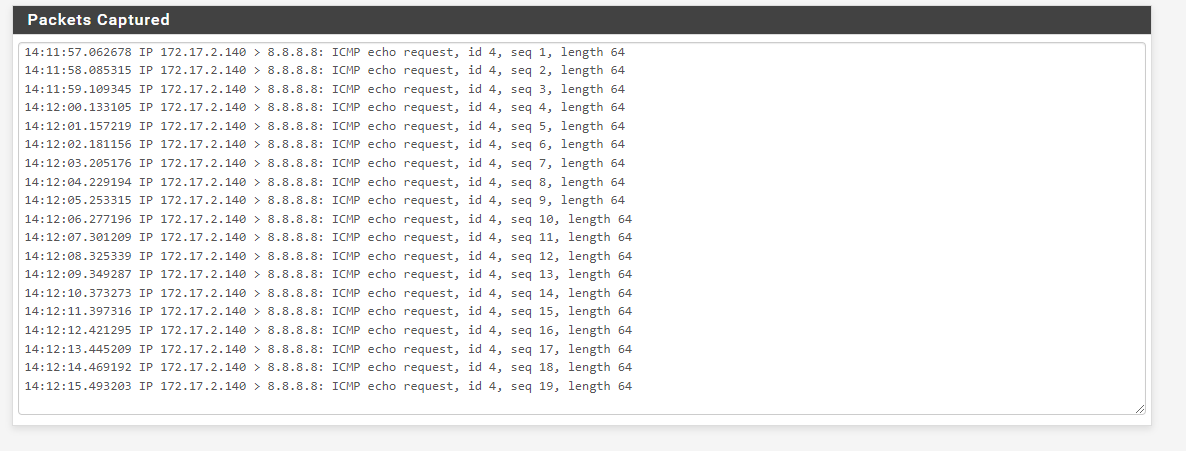
Finally there is a capture of a ping to 8.8.8.8 from a host on the lan.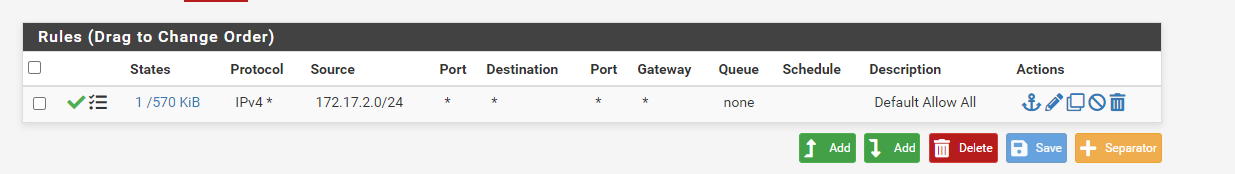
-
@stephenw10
Just to add I do see the ping on the WAN interface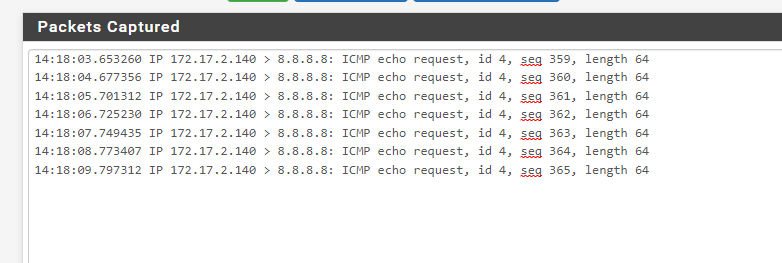
-
Ah, OK. On the WAN interface you should usually see that leaving as translated to the WAN IP by the outbound NAT rules.
If it's not translated there it would need to be added to AWS to translate at the external elastic IP. However that's probably not what you want sine the AWS would know about both subnets and you could easily end up with an asymmetric route.Steve
-
That got it - many thanks Stephen.