router traffic from one IPsec tunnel thru another tunnel?
-
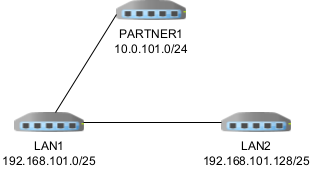
We have a working IPsec tunnel from our LAN1 to several partner sites (Tunnel ipv4).
Now we moved some servers to another location (LAN2) and connected them also thru IPsec (Tunnel ipv4).Is there a chance to get access from LAN2 to a partners IPSec tunnel via LAN1 without defining a direct tunnel between LAN2 and PARTNER1 (LAN2-->LAN1-->PARTNER1)? Is this something IPsec supports?
What I tried so far:
- I split the LAN1 from previously 192.168.101.0/24 into 2 subnets /25 and modified the P2 on LAN1 to PARTNER1 (10.0.101.0/24) to NAT on 192.168.101.0/24. This works as expected
- I modified LAN2 to use 192.168.101.128/25 and setup a tunnel between LAN1 and LAN2. This also works.
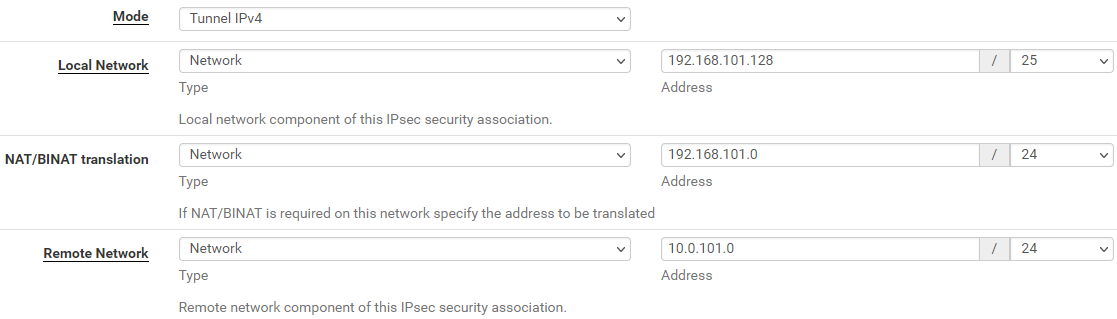
- I then added on LAN2 a P2 entry with remote 10.0.101.0/24 (PARTNER1) and on LAN1 a P2 with local 192.168.101.128/25 (which is actually the network of LAN2 accessable thru another tunnel). This does not work, but maybe I misunderstand how ipsec works?
-
I spent several hours in trial and error with Routed IPsec (VTI) but finally ended up in using (NATed) openVPN config behind the partner IPSec tunnel.
The main issues I had was with a endpoint using dynamic IPs and the leck of knowlege how to use vti config if the other side uses P2 config without vti. It looks like pfsense is mixing up P2 phases when using 0.0.0.0 on the other side due to dynamic IPs. Ubiquity (on one partner side) is not supporting dynamic IPs at all when using VTI.