Routing issue between two LANs on same box
-
Hi,
I'm having issues routing between my management LAN (10.0.1.0/29) and my regular wireless/wired LAN (10.0.0.0/24). I cannot ping anything on the 10.0.0.0/24 network from my MGMT LAN and I cannot ping anything on the 10.0.1.0/29 network from my LAN. I can ping both gateways (10.0.0.1 and 10.0.1.1) but cannot ping devices. These are networks that are on the same pfSense box so I figured it would establish the routes? I have opened all traffic on all of the interfaces (LAN, WLAN, WLAN_LAN_BRIDGE, and MGMT_LAN). Any help would be appreciated!
The network topology is as follows:
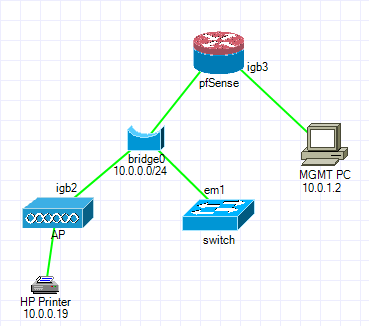
-
@loststatetable can you actually show your rules - common issue is rules default to tcp, and ping is icmp not tcp.
Another common issue is host firewalls blocking traffic. Another common problem is device has no actual gateway set or gateway other than pfsense, your printer is the reason I bring that up since its common for printer to not have gateways at all sometimes.
I figured it would establish the routes?
You are correct, pfsense would have routes automatic to any networks it is directly connected to. But this brings up another common issue - users forcing traffic out a gateway via policy routing in their rules. Which is again why a screenshot of your actual rules would be helpful.
-
This post is deleted! -
@johnpoz sure thing! Do you need LAN and WLAN as well? I'm still confused if the bridge actually controls the rules to the individual interfaces? I have both allowed all from all sources to all destinations. I can ping from the LAN network obviously. I haven't added or changed any routes or gateways in pfSense either. Both devices are getting configs from DHCP via pfSense. Sorry for the messy and contradicting rules...
Here's the printer network config page:
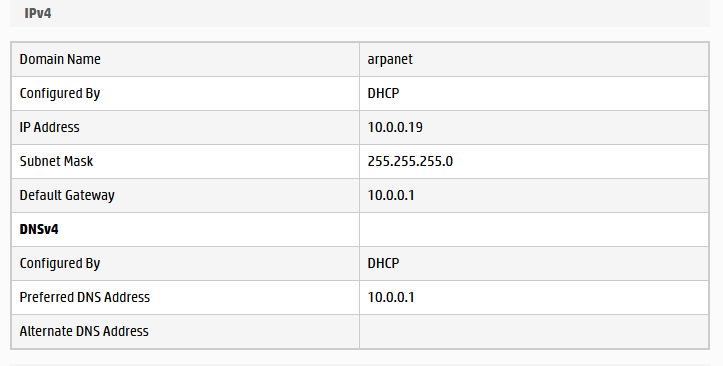
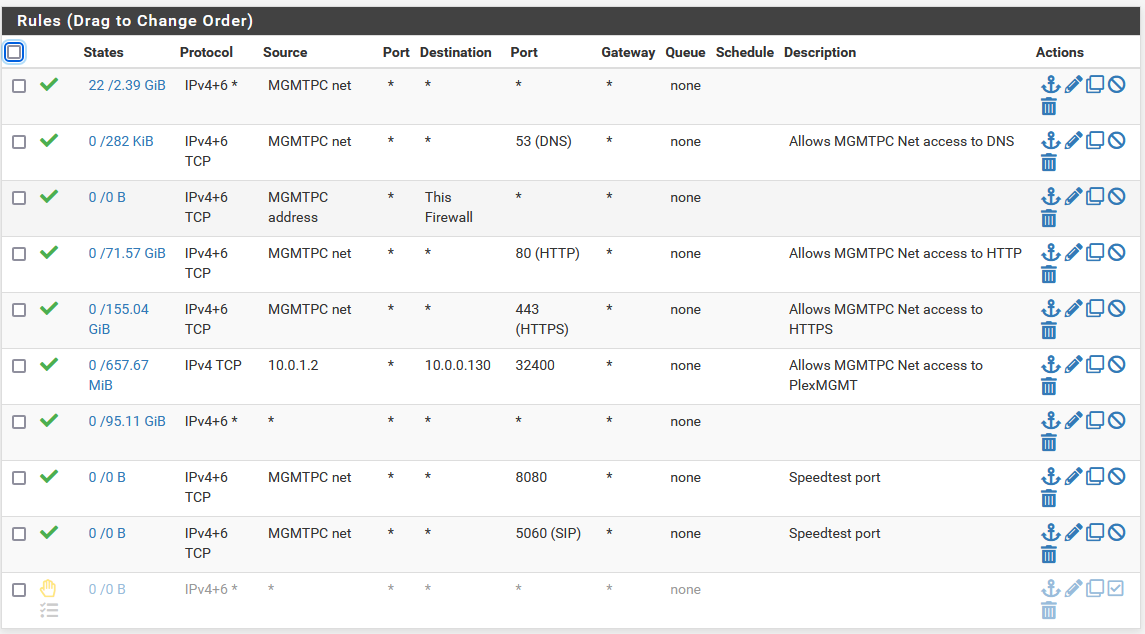
MGMT_LAN:
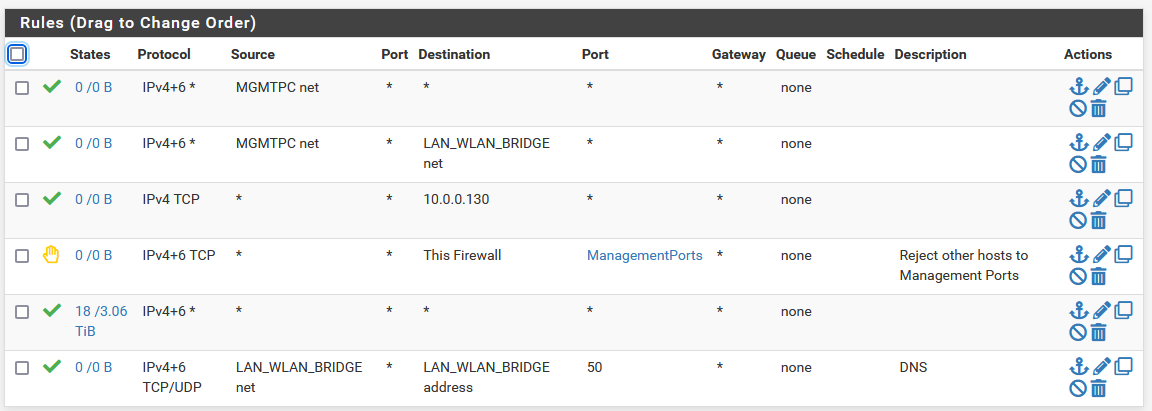
WLAN_LAN_BRIDGE:
-
@loststatetable those rule make no sense.. On your mgmt every below that top rule is pretty pointless.. Sinc eyou allow all there, all your other rules would never be evaluated.
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
On your wlan rules.. mgmt net could never be a source of traffic into this interface.
Traffic is evaluated as it enters an interface from the network its attached to.. In what scenario would source traffic into wlan interface be mgmt?
device traffic ----> interface pfsense
So on your wlan rules.. trying to ping those first 2 would never be evaluated - where exactly is 10.0.0.130? Then you block all traffic to whatever management ports are. Then allow all, but then that last rule pointless because its below a any any rule.
I'm still confused if the bridge actually controls the rules to the individual interfaces?
How did you set it up?
But I really don't get the point of even having the bridge? Why not just plug your AP into your switch, and switch into pfsense? I could see if your AP was network A, and your switch and its devices where network B.. But your bridge is just creating complexity because why? Your out of switch ports?
Do you have anything in floating? I do not see anything there what would block icmp on either of those interfaces even if the rules are not really correct.
If you can not ping something in network B from network A, is there a firewall on network B device? Are you filtering on the bridge or the interfaces?
https://docs.netgate.com/pfsense/en/latest/bridges/firewall.html#bridging-and-firewalling
I would just get rid of the bridge, and just use your switch. If you are short on ports, get another switch, or a bigger switch.. Really would suggest a "smart" switch that can do vlans.. A 8 port get switch that can do vlans can be had for like $40 price point..
-
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
I know, I have been using the pass all to just bypass any possibility that the firewall was stopping it.
But I really don't get the point of even having the bridge? Why not just plug your AP into your switch, and switch into pfsense? I could see if your AP was network A, and your switch and its devices where network B.. But your bridge is just creating complexity because why? Your out of switch ports?
These interfaces are bridged because I have it going directly into ports on the firewall. I currently don't have a managed switch, that is in the works of being purchased but I was hoping to figure out this routing/rules issue first. My reason for plugging it directly in was to allow VLAN to be passed directly from the firewall to the AP to segregate IOT's and normal traffic.
Do you have anything in floating? I do not see anything there what would block icmp on either of those interfaces even if the rules are not really correct.
I don't and this is what's bothering me, I have no clue why it's getting blocked and traffic isn't being passed over.
If you can not ping something in network B from network A, is there a firewall on network B device? Are you filtering on the bridge or the interfaces?
There is only a single firewall, nothing is between the printer and the PC besides the firewall and AP. Unless the AP or printer is somehow blocking it?
-
@loststatetable said in Routing issue between two LANs on same box:
These interfaces are bridged because I have it going directly into ports on the firewall
But why? Since from your drawing everything on the AP and the switch are on the same network.. Since you bridged the interface.. Why not just plug the AP into the switch and remove the bridge from pfsense.
The mgmt rules clearly allow for icmp, since the first top rule there is any any.. And so do your wlan rules - no matter if there are unneeded/used rules.. There are any any rules that would trigger.
So from your wlan interface get a constant ping going to something on your mgmt.. Now sniff does pfsense (diagnostic menu packet capture) see the traffic, does it send it on..
edit: other thing maybe to check since you seem to be running not so common /29 mask there.. You sure your mask is correct on the device.. If you had the mask wrong, where it included your other 10 network, say a /23 or larger - traffic would never get sent to pfsense to go to your wlan network.
You also need to validate where your doing the filtering when you created the bridge - see the link I posted.
Again I would suggest just removing the bridge on pfsense, doing such a thing is almost always the wrong choice.. And trying to leverage a port is not a good enough reason to need to bridge. Just get another switch.. If your out of switch ports, a bridge on pfsense does not a switch make..
-
@johnpoz Thanks for the guidance! I will remove the bridge and put another dummy switch in its place until I get a managed switch. I'll reply back if it works.
-
@loststatetable you show a switch, is it out of ports?
Are you really using an AP, or a wifi router with switch ports as AP?
edit: Also please don't take my comments the wrong way, there are valid use cases for using a bridge.. But it does create more complexity, and its not a switch..
From your drawing I don't see why it would make sense, other than just trying to leverage what is perceived as a port on pfsense, but an interface is not a switch port.
If your in need of switch ports, its almost always going to be a better choice to just get a bigger switch, or add another switch to your network than trying to create a switch via bridging..
If it was me, and wanted to leverage the port on pfsense for my AP.. I would do that - but the wifi would just be another network than stuff that is plugged into the switch.. Unless you had some need of wired and wireless to be on the same network for some sort of discovery or broadcast/multicast traffic?
This is where smart switch come in handy because then its simple to put wireless and wired devices all on the same L2..
-
@johnpoz I am using a legit AP, Aruba 303.
edit: Also please don't take my comments the wrong way, there are valid use cases for using a bridge.. But it does create more complexity, and its not a switch..
I am not, I just genuinely thought it would handle the traffic better than joining with a dummy switch. Like I said I also had dreams to create some VLANs and the dummy switch couldn't support that.
Totally understand now and I will be updating from utilizing the ports on my homemade pfSense box to utilizing a managed switch to handle it a bit better. I was just trying to delay installing the switch because I'm pretty busy and didn't have the time to configure it at the time. Looking back now, it might have saved time to just do it when I switched over to pfSense! Thanks again.
-
@loststatetable said in Routing issue between two LANs on same box:
I just genuinely thought it would handle the traffic better than joining with a dummy switch
no - A switch, even the dumbest of the dumbest ones would be better. Unless it was like 10/100 only and you needed/wanted more than 100 bandwidth. And you had gig interface on your router.
But having that dumb 10/100 switch downstream would limit you anyway, etc.
To be honest the only time I would leverage a bridge on my router would be for media conversion - say I had a fiber interface on my router, and needed that to be on the same L2 as copper.. But that would only be for length of time it took me to order a media converter and or switch with fiber connection (sfp or sfp+) etc..
-
@johnpoz Just ordered an HP 1920-24G for 60 bucks shipped. Took a lot of internal deliberating, but excited I moved forward finally.
-
@loststatetable said in Routing issue between two LANs on same box:
@johnpoz Just ordered an HP 1920-24G for 60 bucks shipped. Took a lot of internal deliberating, but excited I moved forward finally.
This did not resolve the issue. The entire network topology is through the managed switch and the firewall/router only has 2 ethernet cables going in and coming out. WAN from modem and LAN to switch. I'm not sure what's causing this.
-
@loststatetable said in Routing issue between two LANs on same box:
LAN to switch
devices on the same network have ZERO to do with pfsense.. Pfsense has nothing to do with communication between devices on the same network.
If your trying to route at a 1920 between vlans, did you set that up? Again that would have nothing to do with pfsense..
If your trying to route on pfsense - already went over in great detail on how to see if pfsense is routing the traffic and sending the traffic on to where your trying to go.
But with your latest comment.. Where lan goes to your switch, and zero mention of any vlans or routing setup on the switch. Have to assume all devices on the same network. So pfsense has zero to do with communication between these devices.
How exactly do you have device A connected, How is device B connected. What is the IP and mask of A, same for B, etc..
-
@johnpoz said in Routing issue between two LANs on same box:
devices on the same network have ZERO to do with pfsense.. Pfsense has nothing to do with communication between devices on the same network.
If your trying to route at a 1920 between vlans, did you set that up? Again that would have nothing to do with pfsense..Routing is occurring at pfSense. VLAN tagging is on and my PC is on VLAN 5, the printer is not being tagged.
If your trying to route on pfsense - already went over in great detail on how to see if pfsense is routing the traffic and sending the traffic on to where your trying to go.
I know I may have to look into greater detail, I was hoping it was a common error. (Being lazy)
But with your latest comment.. Where lan goes to your switch, and zero mention of any vlans or routing setup on the switch. Have to assume all devices on the same network. So pfsense has zero to do with communication between these devices.
PC is on VLAN5 (10.0.1.0/28) printer is not on a VLAN (10.0.0.0/24). PC can access other devices outside of the VLAN such as servers.
How exactly do you have device A connected, How is device B c
These are all ethernet connections.
I have tried disabling all firewall rules and still see issues, I do not see issues when the PC is on the same network though.Printer --> HP Switch --> pfSense
PC --> HP Switch (VLAN5) --> pfSense -
@loststatetable Ok common problem with printers that I see is they have not gateway set.. If you can not talk to it from vlan5 pc.. Validate the printer has a gateway, that points back to pfsense.
As long as your vlan 5 rules allow access to printer IP or that network, or any any, etc. then what rules are on the printer network would not come into play.
Can you post up the rules of this vlan 5..
But 2 directly connected networks/vlans would automatically pfsense would route between these network. Unless you were forcing traffic out a gateway via policy routing? If you could post your vlan 5 rules we could see.
But if you sniff on the printer network interface, while you say try and ping the printer IP from the vlan 5 PC you could validate that pfsense is sending the traffic to the printer.