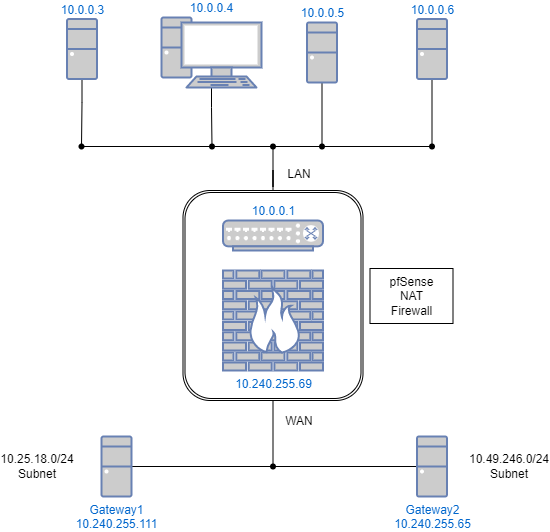
One WAN Interface Two Gateways With NAT
-
The original configuration had one gateway (Gateway1), and was working great. Due to network expansion and other constraints, a second gateway (Gateway2) is needed for the WAN interface to connect to a different subnet (10.49.246.0/24). I can ping and ssh to the pfSense machine WAN ip address from the 10.49.246.0/24 subnet, but haven't been able to get NAT/Port Forward to work when trying to connect to the LAN from the new subnet. I suspect NAT is not possible to do?
It may be possible to add another WAN interface, maybe this would be a better option?
-
@sdockter said in One WAN Interface Two Gateways With NAT:
I can ping and ssh to the pfSense machine WAN ip address from the 10.49.246.0/24 subnet, but haven't been able to get NAT/Port Forward to work when trying to connect to the LAN from the new subnet.
That's not different to a single WAN gateway in this case. You can simply forward the WAN address behind pfSense. By stating the source network you can also forward both to different destinations.
However, if the gateway 2 does not NAT the traffic you need to add a static route for the subnet 10.49.246.0/24 and point it to gateway 2.It may be possible to add another WAN interface, maybe this would be a better option?
This would be necessary if access from public IP range is coming in from the second gateway.
-
@viragomann Yes, I added a second gateway, and a WAN rule that checks the source IP subnet and changes the gateway.
Gateway2 does not NAT. A packet capture on the WAN shows the source from 10.49.246.110. I've tried a static route (System->Routing->Static Routes) from the 10.49.246.0/24 network to Gateway2 on the WAN interface, but it doesn't seem to help with NAT.
-
@sdockter said in One WAN Interface Two Gateways With NAT:
and changes the gateway.
What does that mean?
That is quite simple. 10.49.246.0/24 is already able to access the pfSense WAN IP. So forwarding should word as well and the static route care that respond packets are routed back to the correct gateway.
Sniff the traffic on pfSense WAN and LAN to see what's really going on there.
-
@viragomann In the advance options on the firewall rules, you can change the gateway or gateway group.
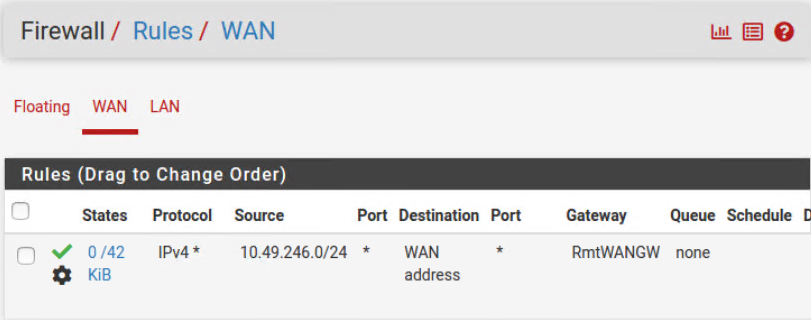
I think what's happening is that the NAT happens before the firewall rules. Since ssh is not NATTed, it triggers the above rule and goes to the right gateway. A packet capture on the pfSense WAN while connecting with ssh shows the 10.49.246.xx ip address in both the source and destination as expected.
It seems that NATTing changes the source so that it bypasses this firewall rule. I've tried the NAT/Port Forwarding with the pfSense web configurator, and packet capture on the pfSense WAN shows the 10.29.246.xx as a source, but not as a destination (no reply out of the WAN).
-
@sdockter
Setting a gateway in the WAN rule is really a bad idea.
The gateway option in firewall rules is meant for policy routing of outbound connections and instructs pfSense to pass all matching traffic to this gateway.
So this rule will pass no packets behind pfSense in your setup.