Host OverRide for UnFi APs
-
@magikmark so you run all your rules in floating.. So there is really no way to know even what direction they are in? Other than your description there saying outgoing or incoming
So in what possible scenario would wirelesslan be an outgoing interface towards whatever is in firehol level 1?
First thing I would suggest is get rid of ALL of those... You understand use of "this firewall" is every IP of the firewall right? But in what scenario would these interfaces be used in the out direction htpc and wirelesslan? Or how would these what I assume are external sources in your aliases be inbound into those interfaces?
What are the rules on your actual interfaces.. Please delete all those rules and show us the rules on your actual interfaces.. You can put your whatever those are suppose to be and do back after you actual have stuff working..
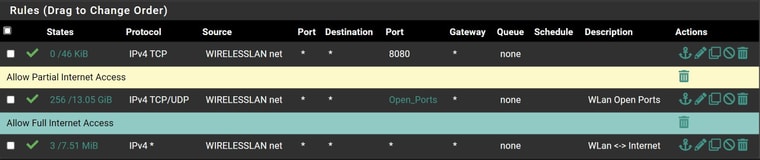
Most of those rules don't even have any hits.. they are all 0/0
Value: 01:04:0a:00:01:01 (10.0.1.1)
01:04:7f:00:00:01 (127.0.0.1)Those are not how you do option 43.. For option 43 you put in the IP of your controller..
-
Ok Will delete those
-
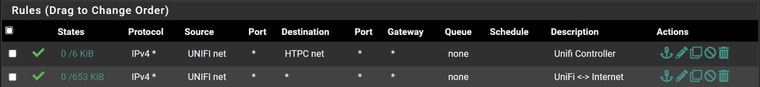
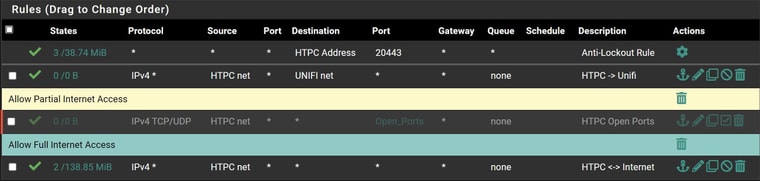
@magikmark what interfaces are those rules on? I can guess that the antilock out is your lan, but you have it named htpc ?
-
Ethernet 1 Wan 192.168.1.2 (ISP)
Ethernet 2 Lan (HTPC) 10.0.1.1
Ethernet 3 Asus 10.0.2.1
Ethernet 4 Unfi 10.0.3.1. -
Floating Rule
Host Override
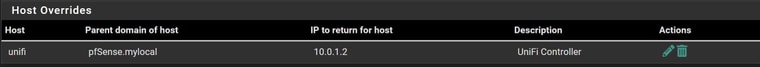
DhcP Option 43 under the Unifi IP 10.0.3.2
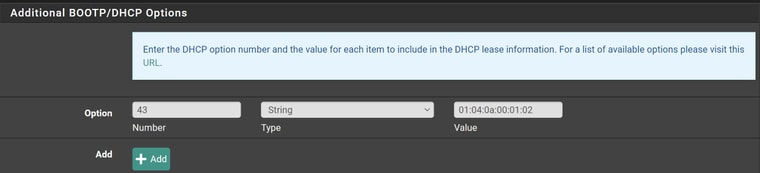
-
@magikmark where did you come up with that hex? I show that converting to 0.0.0.1
That should be the IP of your controller..
-
From
https://www.browserling.com/tools/ip-to-hexUnifi Controller Ip:
10.1.2 -> 0a.00.01.02According to
https://network.unifi.ui.com/
my Controller IP is 10.0.1.2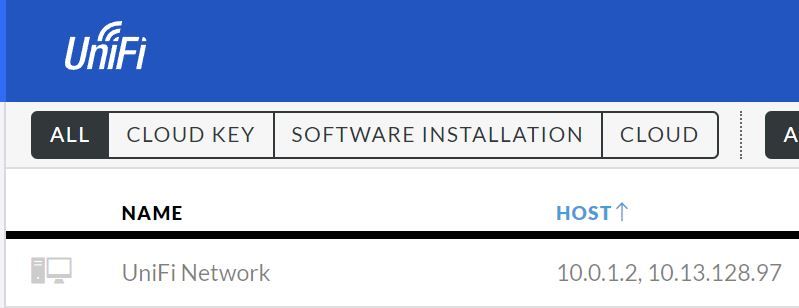
-
where is that 10.13.128.97 coming from - you make no mention of this 10 network..
-
I have no idea. Unifi just included that,.
Maybe when I was installing the controller I was using the VPN? -
@magikmark regardless - can you ssh to your AP yet? Can you ping it even?
You were using a vpn on the actual unifi controller host, or is this some VM that your natting on the host..
-
- No vm. Not using any
- Last time I checked Ssh timed out. No ping either
- Vpn on my desktop only not in pfsense
Will try again later. Will be calling the night off shortly
If it's OK can you pm me where to send the config file?Thanks
-
@magikmark again I have no real desire to comb through your config file.. Just show your rules in a manner that can be understood..
What interface they are on.. etc..
Remove ALL your floating nonsense.. That are almost impossible to interpret, since you can not tell if they are inbound or outbound or both.. What description you put on the rule, doesn't mean you correctly put in the description for what direction the rules are being evaluated.
Post up the rules for your interfaces, listing the interface they are on..
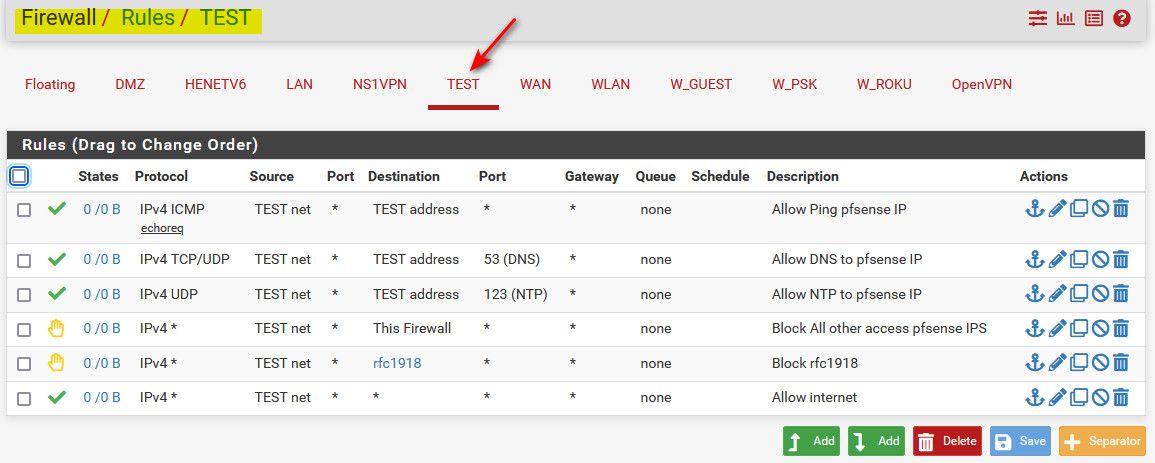
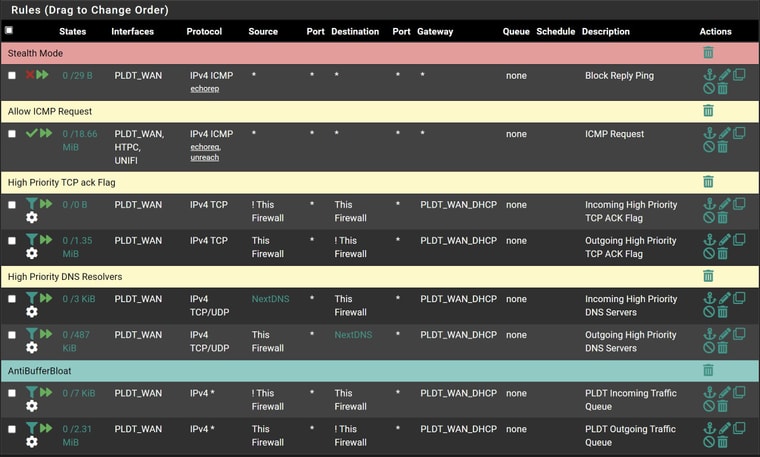
See how easy that is to see that is on my TEST interface ;) See how easy you can see that is ALL my rules on that interface..
Now look at what you posted..
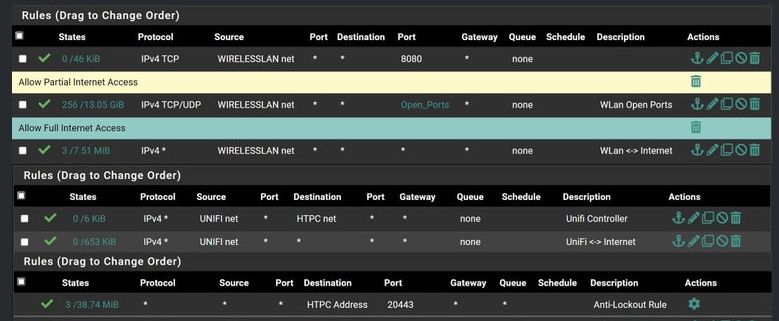
what interfaces are those on, are they all the rules on the interface? I assume those are the top rules? But really can not tell since do not see the top or the bottom.. I assume the rules are the top rules if they also show the column headers.. But are they actually on the correct interface? See all the time were users have source as some network that is not the interface the rule is on..
These rules unless you were logging specific access don't make a lot of sense. What is the point of allow specific rules above a any any rule, without any block rules between, etc.
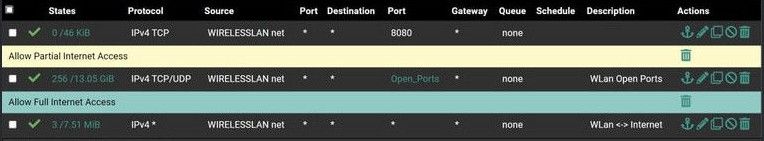
Those rules above the any any are there why, you have an any any that would allow what you have above it. So unless you specific wanted to log traffic to those ports, but you don't have those rules set to log? So why do you have them split like that?
If the source interface has a rule that allows ssh or ping, doesn't matter what the rules on the other destination network interface are.. You would be able to ssh and ping to stuff on that dest network.. As long as what your trying to access is not running some firewall, or not using some other gateway than pfsense.
-
Mmm, you have a rule to allow access to the AP specifically between HTPCnet and UNIFInet but it shows 0/0. It has never matched any traffic.
So either not traffic has tried to use it sicne the counters were last reset or you have a floating rule blocking it. It doesn't look like you do have a rule that would block it though.Can you ping the AP from the firewall itself?
Steve
-
@stephenw10 said in Host OverRide for UnFi APs:
allow access to the AP specifically between HTPCnet and UNIFInet but it shows 0/0
But that is not where his AP and controller are..
Unifi controller is located in my LAN (10.0.1.1:8443) and my U6 is located in another interface "Wireless" (10.0.2.1)
He lan is called HTPC, but he says his AP is on the wireless, So really not sure what is on unifi net?
The inform default port is 8080, and he has some hits on that rule from wireless net..
Then in another post he calls what I assume is he wireless network asus.. But then he calls out lan and htpc
LAN: 10.0.1.1
HTPC: 10.0.1.2But from his rules posted lan is clearly the htpc net - since that is where the the antilock rule is listed..
So to be honest I have no idea how to make heads or tails of this.. Then his controller shows some 10.13 address..
Its a mess to be honest.. All kinds of floating rules and not sure what interfaces those other rules are on..
he states
DhcP Option 43 under the Unifi IP 10.0.3.2
But thought his AP was on the wireless 10.0.2 network..
Post up some a diagram showing what is where, and what your calling what.. And post up the rules on the interfaces so they can be easily read.. etc..
-
Mmm, I had assumed that's where the host is he it trying to ssh to the AP from.
But has allow all rules there he should be able to connect to the AP anywhere. The 'feels' more like the AP cannot reply because it has no default route for example.
-
@stephenw10 said in Host OverRide for UnFi APs:
able to connect to the AP anywhere.
Concur - if there is a any any rule from where his ssh client is, then doesn't matter what rules are on the AP interface.. Unless he has some outbound rule in floating. But since his AP should be getting an IP from dhcp, its not really possible to have it use anything other than dhcp until its adopted..
So unless he also dicked with the default dhcpd setting, the AP would be pointing back to pfsense as it gateway.
But since this forest is so overgrown with weed trees, its hard to pick out the specific oak your looking for.
-
Guys,
Thank you for your patience. I cleaned my Floating Rules and Reset the state table.
Everything now is working. FireHol was giving a lot of false positive. So I removed them all
-
@magikmark said in Host OverRide for UnFi APs:
FireHol was giving a lot of false positive
Its not false if the IP range is included... A simple look to that firehol level 1, and it includes all the bogons, which would include rfc1918.
So yeah with those rules you wouldn't be talking between your rfc1918 vlans ;)
-
Just found out you need to disable your vpn when configuring APs. You will get disconnected status if you don't at least for Layer 3 adoptions.
-
A VPN in pfSense? If you are policy routing traffic across it then, yeah, it could well prevent local connections. You should probably have rules to allow it above policy routing though if that is the case.
Steve