Azure VPN > Head Office > OpenVPN - No Access
-
To give some idea of the network architecture;
Head Office has a Pfsense firewall with a site-to-site IPSec VPN connection to some virtual machines in Azure. When on site (192.168.1.1/22) I have no issues communicating to the Azure VNET (10.0.0.0/16) or its VM's.
Remote users connect to head office using OpenVPN on Pfsense (10.8.0.0/24) and can access site resources but can't see the Azure VNET.
I tried adding the route to the OpenVPN server config (push "route 10.0.0.0 255.255.0.0"), but that made no difference.
Any direction on how to make the AZ VNET visible to remote users would be appreciated.
-
The IPSec tunnel, assuming it's policy based, must carry that traffic. So you would need an additional P2 for: 10.8.0.0/24 <-> 10.0.0.0/16
Steve
-
Thanks for that. Makes sense. I've added the P2, but still not seeing the AZVNET though.
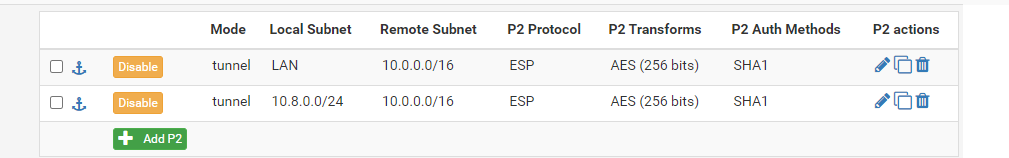
Anything else I could be missing?
-
Did the P2 establish? Do you see traffic on it on the state counters in the IPSec status?
You can try to ping across it from pfSense itself by setting the source IP to the OpenVPN server.
To use it from an OpenVPN client you need a route, which it looks like you added, and firewall rules on the OpenVPN in pfSense and in Azure.
Steve
-
That was it!
I had everything set up on pfSense after adding the P2, but the Azure VNET wasn't aware of the 10.8.0.0/24 address space.
Thanks Stephen.