Is there a way to change the Source IP / Source Interface for packets generated by the firewall
-
First time posting; please forgive me if this is not posted in correct place.
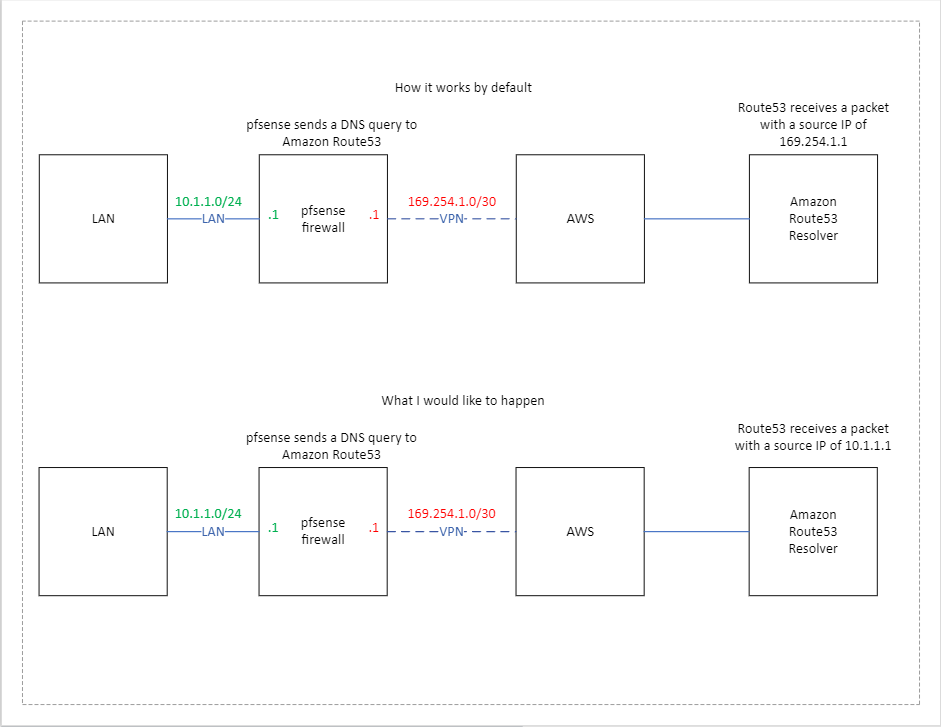
We have a pfsense firewall with a IPsec VPN built to AWS. We have a requirement that we send pfsense DNS traffic to our DNS servers sitting in AWS.
What we have found is, when we send traffic the firewall generates (such as DNS traffic) over the VPN, the source IP of the packet is the tunnel IP. This is the normal default behavior. My question is, can we change it? So for example, instead of utilizing the tunnel IP as the source IP, could we use the LAN IP?
I've included a quick diagram which, hopefully, clarifies my question.
Thank you for any assistance given, in advance!
-
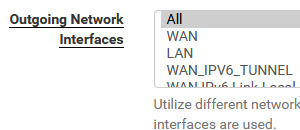
@dlrqdm On the DNS Resolver page there is an Outgoing Network Interfaces section. Not sure if it can send out to the Internet from LAN though.
-
@dlrqdm and would this amazon route53 know how to get back to your 10.1.1 address?
-
@steveits Thanks for the response Steve! Out of curiousity, where would the Outgoing Network Interfaces section be located? We're on version 01.00.00.11 if it helps. I did check out the "System > DNS Server Settings" section. Unfortunately, changing the gateway per DNS server doesn't resolve our issue. We could change the gateway - this would change the source IP, but it also forces the packet out of the wrong interface.
-
@johnpoz Yup it does. We have other resources behind the firewall (on the 10.1.1.x subnet) that work perfectly.
-
@dlrqdm Not sure what version number you're talking about...pfSense is at 2.5.2 or 21.05.
Services/DNS Resolver/General Settings
7th item down:
-
@dlrqdm said in Is there a way to change the Source IP / Source Interface for packets generated by the firewall:
on version 01.00.00.11
huh - what is that version of? That is not a pfsense version, or a unbound version..
-
@steveits Sorry, our version is 21.0.5.1. I posted the incorrect thing earlier. Unfortunately, the "outgoing network interfaces" section didn't appear to make any change to the issue. Traffic was still sent utilizing the tunnel IP. I think the "Outgoing Network Interfaces" section under DNS Resolvers only applies if a client was sending DNS queries to pfense (ie: pfesnse was acting as a DNS server). That's only a guess though.
Thank you for the assistance so far!
-
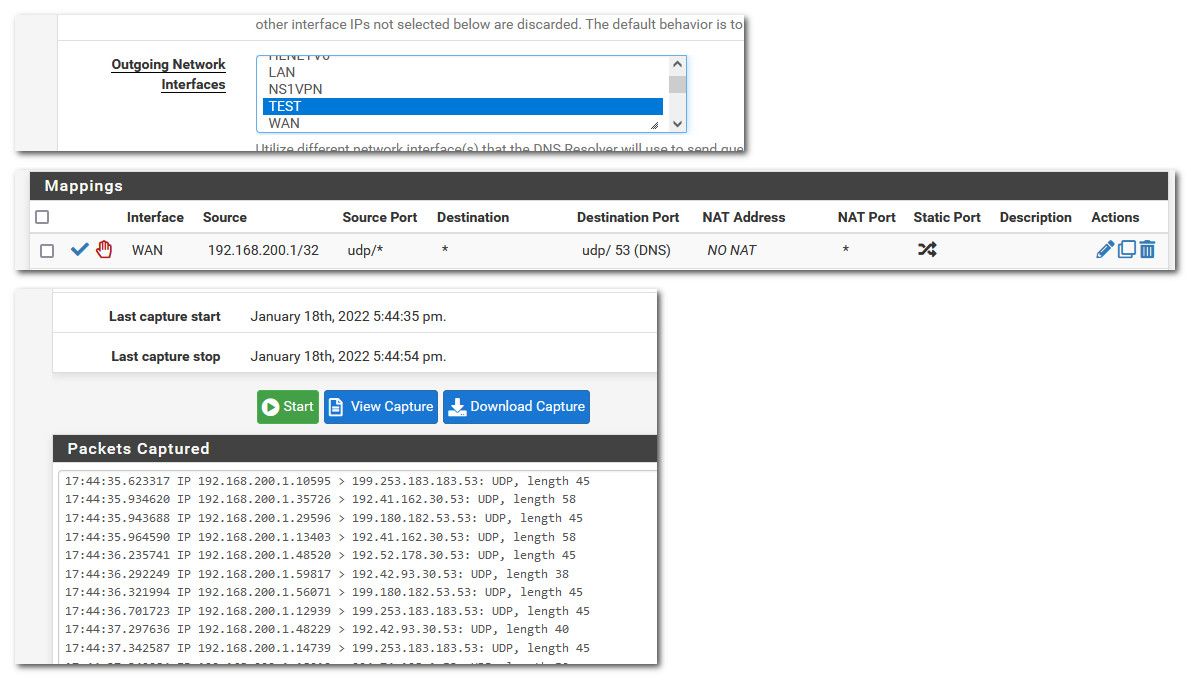
@dlrqdm You would have to adjust your outbound nat to not nat..
Here to do an example... I created a special outbound rule for my test interface to not be used for nat outbound using hybrid mode.. With my test interface IP 192.168.200.1, set unbound to only use the test interface for outbound.
Sniffing on wan while I do a dns query, which never get answered of course you can see the traffic going out with my 192.168.200.1 address.
You would have to adjust to use your vpn interface, etc..