-
@viragomann said in Configuring APCUPSD:
@panzerscope
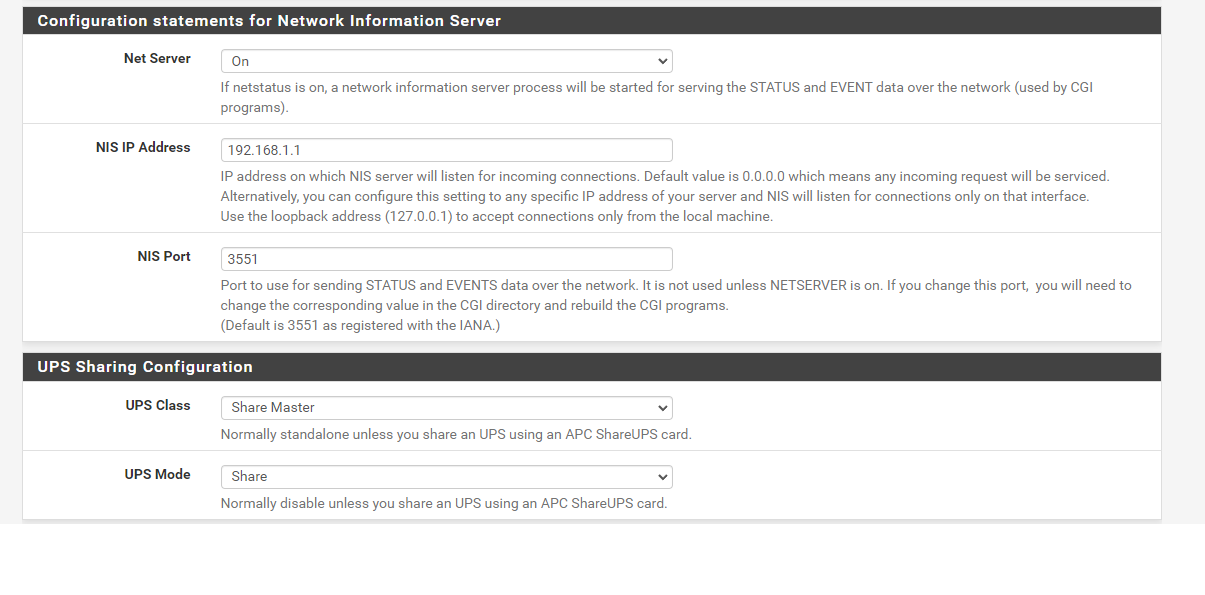
Yes, NIS access should work with that. But you can also enter "0.0.0.0" for the NIS server, which means, it will listen on any interface IPs.Thanks. I Have also tried setting the NIS to 0.0.0.0, with my NAS still looking at 192.168.1.1 to detect the UPS, unfortunately nothing still. Perhaps I need to try a reboot later.
-
@panzerscope
I think, you should better find out, what your NAS is needing.If you get no other info you can sniff its traffic on pfSense using Diagnostic > Packet Capture.
Possibly it tries to access via SNMP. -
@viragomann said in Configuring APCUPSD:
@panzerscope
I think, you should better find out, what your NAS is needing.If you get no other info you can sniff its traffic on pfSense using Diagnostic > Packet Capture.
Possibly it tries to access via SNMP.Ok,
So I sniffed the packets at host 192.168.1.25 (NAS). While sniffing I configured the NAS to lookup 192.168.1.1 (PfSense) for the UPS. The Log I got was:
13:25:45.986770 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.986774 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.987326 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.987740 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.987742 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.988463 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.988704 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.988707 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.989677 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.989679 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.990055 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.990651 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.990653 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.991423 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.991616 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.991619 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.991875 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.992559 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.993235 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.993237 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.993469 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.994378 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.994862 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.994865 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.995292 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.995971 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.996487 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.997110 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.997298 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.997300 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.997384 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.998703 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:45.998943 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.998945 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:45.999840 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.000596 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.000598 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.000979 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.002215 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.002217 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.002799 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.003708 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.003850 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.003853 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.004619 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.005071 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.005073 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.005757 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.006292 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.006295 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.007518 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.007521 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.007607 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.008492 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.008751 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.008754 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.009967 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.009969 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.010312 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.011194 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.011196 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.011673 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.012420 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.012422 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.012811 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.013495 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.013643 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.013645 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.014868 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.014870 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.015086 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.016097 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.016100 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.016236 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.017323 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.017325 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.017591 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.018500 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.018562 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.018564 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.019774 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.019776 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.019861 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.020550 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.021001 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.021003 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.021458 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.022226 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.022229 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.022371 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.023280 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.023451 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.023453 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.023962 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.024680 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.024682 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.024872 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.025554 IP 162.125.64.14.443 > 192.168.1.25.55952: tcp 0
13:25:46.025901 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428
13:25:46.026514 IP 192.168.1.25.55952 > 162.125.64.14.443: tcp 1428Any clues ? I note that nothing to do with SNMP comes up. My NAS does have a a function to use SNMP to search for a UPS but I am guessing that will not work with APCUPSD.
-
@panzerscope
Also absolutely no access to 192.168.1.1.Set the IP filter to
192.168.1.1,192.168.1.25
to only catch the traffic between NAS and pfSense.Consider that the pull interval on the NAS is 2 minutes. So you need to run the capture for at least this period of time.
-
@viragomann said in Configuring APCUPSD:
@panzerscope
Also absolutely no access to 192.168.1.1.Set the IP filter to
192.168.1.1,192.168.1.25
to only catch the traffic between NAS and pfSense.Consider that the pull interval on the NAS is 2 minutes. So you need to run the capture for at least this period of time.
Ok thanks for that. So I re-ran it and we have the below .
13:51:18.648530 IP 192.168.1.25.40356 > 192.168.1.1.3493: tcp 0
13:51:19.352556 IP 192.168.1.25.40364 > 192.168.1.1.3493: tcp 0
13:51:20.500358 IP 192.168.1.25.40394 > 192.168.1.1.3493: tcp 0
13:51:21.528643 IP 192.168.1.25.40394 > 192.168.1.1.3493: tcp 0
13:51:23.577727 IP 192.168.1.25.40394 > 192.168.1.1.3493: tcp 0
13:51:24.550890 IP 192.168.1.25.40430 > 192.168.1.1.3493: tcp 0
13:51:25.171361 IP 192.168.1.25.40442 > 192.168.1.1.3493: tcp 0
13:51:25.561816 IP 192.168.1.25.40430 > 192.168.1.1.3493: tcp 0
13:51:26.200847 IP 192.168.1.25.40442 > 192.168.1.1.3493: tcp 0
13:51:27.577455 IP 192.168.1.25.40464 > 192.168.1.1.3493: tcp 0
13:51:27.608900 IP 192.168.1.25.40430 > 192.168.1.1.3493: tcp 0
13:51:28.248938 IP 192.168.1.25.40442 > 192.168.1.1.3493: tcp 0
13:51:28.632940 IP 192.168.1.25.40464 > 192.168.1.1.3493: tcp 0
13:51:29.559620 IP 192.168.1.25.40484 > 192.168.1.1.3493: tcp 0
13:51:30.306889 IP 192.168.1.25.40496 > 192.168.1.1.3493: tcp 0
13:51:30.617032 IP 192.168.1.25.40484 > 192.168.1.1.3493: tcp 0
13:51:30.681025 IP 192.168.1.25.40464 > 192.168.1.1.3493: tcp 0
13:51:31.321062 IP 192.168.1.25.40496 > 192.168.1.1.3493: tcp 0
13:51:32.666124 IP 192.168.1.25.40484 > 192.168.1.1.3493: tcp 0
13:51:33.369171 IP 192.168.1.25.40496 > 192.168.1.1.3493: tcp 0
13:51:34.628748 IP 192.168.1.25.40558 > 192.168.1.1.3493: tcp 0
13:51:35.673249 IP 192.168.1.25.40558 > 192.168.1.1.3493: tcp 0
13:51:37.721331 IP 192.168.1.25.40558 > 192.168.1.1.3493: tcp 0
13:51:40.463451 IP 192.168.1.25.40584 > 192.168.1.1.3493: tcp 0
13:51:41.497497 IP 192.168.1.25.40584 > 192.168.1.1.3493: tcp 0
13:51:43.545579 IP 192.168.1.25.40584 > 192.168.1.1.3493: tcp 0
13:51:47.526853 IP 192.168.1.25.40626 > 192.168.1.1.3493: tcp 0
13:51:48.538789 IP 192.168.1.25.40626 > 192.168.1.1.3493: tcp 0
13:51:49.568545 IP 192.168.1.25.40630 > 192.168.1.1.3493: tcp 0
13:51:50.585867 IP 192.168.1.25.40630 > 192.168.1.1.3493: tcp 0
13:51:50.585869 IP 192.168.1.25.40626 > 192.168.1.1.3493: tcp 0
13:51:52.634975 IP 192.168.1.25.40630 > 192.168.1.1.3493: tcp 0
13:51:53.483821 IP 192.168.1.25.40650 > 192.168.1.1.3493: tcp 0
13:51:54.490035 IP 192.168.1.25.40650 > 192.168.1.1.3493: tcp 0
13:51:54.576649 IP 192.168.1.25.40652 > 192.168.1.1.3493: tcp 0
13:51:55.578078 IP 192.168.1.25.40652 > 192.168.1.1.3493: tcp 0
13:51:56.538130 IP 192.168.1.25.40650 > 192.168.1.1.3493: tcp 0
13:51:57.626178 IP 192.168.1.25.40652 > 192.168.1.1.3493: tcp 0
13:52:00.458712 IP 192.168.1.25.40722 > 192.168.1.1.3493: tcp 0
13:52:01.466346 IP 192.168.1.25.40722 > 192.168.1.1.3493: tcp 0
13:52:03.514424 IP 192.168.1.25.40722 > 192.168.1.1.3493: tcp 0
13:52:07.542379 IP 192.168.1.25.40782 > 192.168.1.1.3493: tcp 0
13:52:08.570635 IP 192.168.1.25.40782 > 192.168.1.1.3493: tcp 0
13:52:08.932667 IP 192.168.1.25.40790 > 192.168.1.1.3493: tcp 0
13:52:09.978697 IP 192.168.1.25.40790 > 192.168.1.1.3493: tcp 0
13:52:10.618726 IP 192.168.1.25.40782 > 192.168.1.1.3493: tcp 0
13:52:12.026785 IP 192.168.1.25.40790 > 192.168.1.1.3493: tcp 0
13:52:13.067170 IP 192.168.1.25 > 192.168.1.1: ICMP echo request, id 58135, seq 0, length 64
13:52:13.067181 IP 192.168.1.1 > 192.168.1.25: ICMP echo reply, id 58135, seq 0, length 64
13:52:13.578544 IP 192.168.1.25.40848 > 192.168.1.1.3493: tcp 0
13:52:13.725799 IP 192.168.1.25.40854 > 192.168.1.1.3493: tcp 0
13:52:14.587886 IP 192.168.1.25.40848 > 192.168.1.1.3493: tcp 0
13:52:14.778897 IP 192.168.1.25.40854 > 192.168.1.1.3493: tcp 0
13:52:16.455410 IP 192.168.1.25.40866 > 192.168.1.1.3493: tcp 0
13:52:16.634985 IP 192.168.1.25.40848 > 192.168.1.1.3493: tcp 0
13:52:16.826991 IP 192.168.1.25.40854 > 192.168.1.1.3493: tcp 0
13:52:17.467010 IP 192.168.1.25.40866 > 192.168.1.1.3493: tcp 0
13:52:18.787706 IP 192.168.1.25.40906 > 192.168.1.1.3493: tcp 0
13:52:19.515118 IP 192.168.1.25.40866 > 192.168.1.1.3493: tcp 0
13:52:19.836109 IP 192.168.1.25.40906 > 192.168.1.1.3493: tcp 0
13:52:20.490753 IP 192.168.1.25.40918 > 192.168.1.1.3493: tcp 0
13:52:21.499190 IP 192.168.1.25.40918 > 192.168.1.1.3493: tcp 0
13:52:21.883199 IP 192.168.1.25.40906 > 192.168.1.1.3493: tcp 0
13:52:23.547269 IP 192.168.1.25.40918 > 192.168.1.1.3493: tcp 0
13:52:26.459238 IP 192.168.1.25.40942 > 192.168.1.1.3493: tcp 0
13:52:27.516455 IP 192.168.1.25.40942 > 192.168.1.1.3493: tcp 0
13:52:29.563532 IP 192.168.1.25.40942 > 192.168.1.1.3493: tcp 0
13:52:33.614177 IP 192.168.1.25.41030 > 192.168.1.1.3493: tcp 0
13:52:34.619762 IP 192.168.1.25.41030 > 192.168.1.1.3493: tcp 0
13:52:36.464868 IP 192.168.1.25.41034 > 192.168.1.1.3493: tcp 0
13:52:36.668816 IP 192.168.1.25.41030 > 192.168.1.1.3493: tcp 0
13:52:37.499873 IP 192.168.1.25.41034 > 192.168.1.1.3493: tcp 0
13:52:39.547946 IP 192.168.1.25.41034 > 192.168.1.1.3493: tcp 0
13:52:39.595106 IP 192.168.1.25.41052 > 192.168.1.1.3493: tcp 0
13:52:40.635998 IP 192.168.1.25.41052 > 192.168.1.1.3493: tcp 0
13:52:41.472938 IP 192.168.1.25.41060 > 192.168.1.1.3493: tcp 0
13:52:42.492073 IP 192.168.1.25.41060 > 192.168.1.1.3493: tcp 0
13:52:42.684084 IP 192.168.1.25.41052 > 192.168.1.1.3493: tcp 0
13:52:44.540157 IP 192.168.1.25.41060 > 192.168.1.1.3493: tcp 0
13:52:45.457453 IP 192.168.1.25.41094 > 192.168.1.1.3493: tcp 0
13:52:46.460241 IP 192.168.1.25.41094 > 192.168.1.1.3493: tcp 0
13:52:48.508327 IP 192.168.1.25.41094 > 192.168.1.1.3493: tcp 0
13:52:51.457379 IP 192.168.1.25.41142 > 192.168.1.1.3493: tcp 0
13:52:52.476493 IP 192.168.1.25.41142 > 192.168.1.1.3493: tcp 0
13:52:54.524576 IP 192.168.1.25.41142 > 192.168.1.1.3493: tcp 0
13:52:57.545088 IP 192.168.1.25.41182 > 192.168.1.1.3493: tcp 0
13:52:58.556746 IP 192.168.1.25.41182 > 192.168.1.1.3493: tcp 0
13:53:00.604831 IP 192.168.1.25.41182 > 192.168.1.1.3493: tcp 0
13:53:01.482274 IP 192.168.1.25.41222 > 192.168.1.1.3493: tcp 0
13:53:02.525924 IP 192.168.1.25.41222 > 192.168.1.1.3493: tcp 0
13:53:04.573031 IP 192.168.1.25.41222 > 192.168.1.1.3493: tcp 0
13:53:04.614521 IP 192.168.1.25.41264 > 192.168.1.1.3493: tcp 0
13:53:05.661052 IP 192.168.1.25.41264 > 192.168.1.1.3493: tcp 0
13:53:06.491011 IP 192.168.1.25.41270 > 192.168.1.1.3493: tcp 0
13:53:07.517125 IP 192.168.1.25.41270 > 192.168.1.1.3493: tcp 0
13:53:07.709137 IP 192.168.1.25.41264 > 192.168.1.1.3493: tcp 0
13:53:09.566226 IP 192.168.1.25.41270 > 192.168.1.1.3493: tcp 0
13:53:10.496894 IP 192.168.1.25.41290 > 192.168.1.1.3493: tcp 0
13:53:11.549311 IP 192.168.1.25.41290 > 192.168.1.1.3493: tcp 0
13:53:13.597391 IP 192.168.1.25.41290 > 192.168.1.1.3493: tcp 0 -
@panzerscope said in Configuring APCUPSD:
3493
This seems to be the NUT protocol.
So you may rather succeed with the NUT package, I assume.
-
@viragomann said in Configuring APCUPSD:
@panzerscope said in Configuring APCUPSD:
3493
This seems to be the NUT protocol.
So you may rather succeed with the NUT package, I assume.
As it happens I did install NUT to try but it looks like my UPS (APC SMT 1500) is possibly not supported as I could not get it to work. I think PfSense will not work for what I am trying to achieve, based on the QNAP not using NIS and NUT not wanting to work with my UPS. It was worth a go !
Thanks for all your help.
-
If NUT does not recognise your UPS then you can run both apcupsd and NUT. But I wonder if you configured NUT wrong as I am using an SMT750i fine with it.
So two options:-
Run apcupsd on pfsense machine as you are already. Then ALSO run NUT but configured as type "remote apcupsd" pointing to the apcupsd service on the same machine. Then point QNAP to NUT. Note QNAP requires that the NUT machine name is "QNAPUPS".
-
Try to get NUT working with your SMT1500, and point QNAP to that. Note the same UPS machine requirement.
-
-
@panzerscope said in Configuring APCUPSD:
I did install NUT to try but it looks like my UPS (APC SMT 1500) is possibly not supported
Network UPS Tools has support reports for Smart-UPS 1500 back through NUT 2.2.
-
@occamsrazor said in Configuring APCUPSD:
you can run both apcupsd and NUT
FWIW, I would not recommend this. While this might appear to work fine initially, you would likely run into an issue when it came to forced shutdown as both would be trying to manage the UPS.
-
@dennypage said in Configuring APCUPSD:
@occamsrazor said in Configuring APCUPSD:
you can run both apcupsd and NUT
FWIW, I would not recommend this. While this might appear to work fine initially, you would likely run into an issue when it came to forced shutdown as both would be trying to manage the UPS.
@dennypage Thank you, that's interesting. I was only using NUT as a kind of bridge for monitoring via an IOS app that only supports NUT, not for any shutdown purposes.
The apcupsd is used for shutdown purposes set to halt pfsense if either remaining minutes or battery level conditions are met. I guess I'd assumed that with no specific instructions, NUT running on pfsense wouldn't shut it down at all, but perhaps there is some kind of default shutdown behaviour that is not visible in the interface? I wish the NUT interface had some more GUI options like apcupsd does.
I thought both of these softwares just "pulled" info from the UPS and then reacted to it based on user settings. But seems you are saying in NUT's case the UPS itself somehow "pushes" a shutdown, is that right?Re: @panzerscope 's machine, it would help to know what kind of connection you are using between the SMT1500 and pfsense - USB, network management card, etc? Did you set the UPS name in pfSense NUT settings to exactly "QNAPUPS" like below? If it is not exactly that then your QNAP will not recognize it.
Below are my pfSense NUT settings connected via USB to an SMT750i and that's the same series UPS as yours, so I think you must be able to get it to work...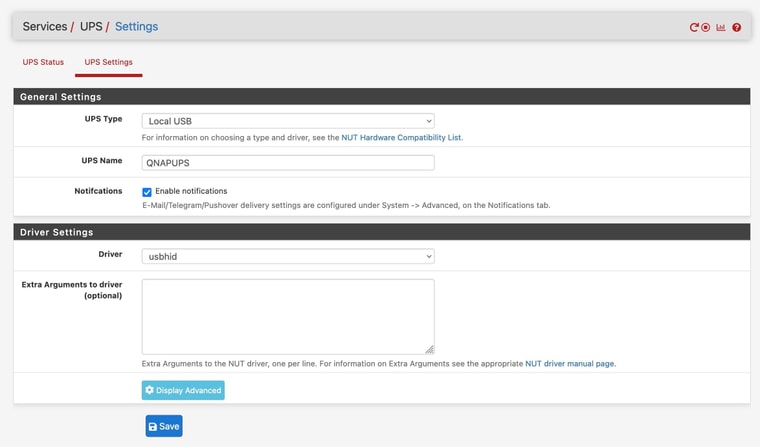
And here are my QNAP settings:
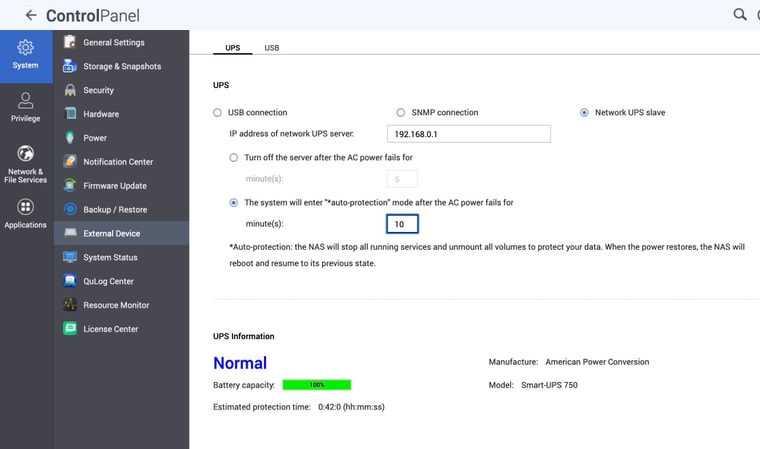
-
@occamsrazor said in Configuring APCUPSD:
I guess I'd assumed that with no specific instructions, NUT running on pfsense wouldn't shut it down at all, but perhaps there is some kind of default shutdown behaviour that is not visible in the interface?
With no specific instructions, NUT "does the right thing." The right thing is to perform a shutdown when the UPS declares a low battery condition. I haven't used it in a while, but this is still the default behavior of apcupsd as well.
I always tell people... don't futz with UPS settings unless you have a very good reason--I.E. something does not actually work. NUT and the UPS will generally work together to do the right thing. About the only pseudo common situation people run into is when the UPS power off delay isn't long enough to allow full system shutdown (some UPSs have really short off delays).
-
@occamsrazor said in Configuring APCUPSD:
Did you set the UPS name in pfSense NUT settings to exactly "QNAPUPS" like below? If it is not exactly that then your QNAP will not recognize it.
The most likely issue is that you have not configured remote access to the NUT server. Read post #2 in the NUT package thread.
-
@occamsrazor One other thing you are going to run into... the QNAP uses a hard coded value for username and password (admin/123456).
These hard coded values will be in conflict with the generated admin settings for NUT on pfSense. To get around this, you will need to change the configuration on the QNAP by hand to use the values you add on pfSense (post 2 referenced above). You will likely need to repeat this change whenever the OS on the QNAP is updated.
-
 S stephenw10 moved this topic from pfSense Packages on
S stephenw10 moved this topic from pfSense Packages on
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.