OpenVPN client cannot access second pfSense host
-
Hi all —
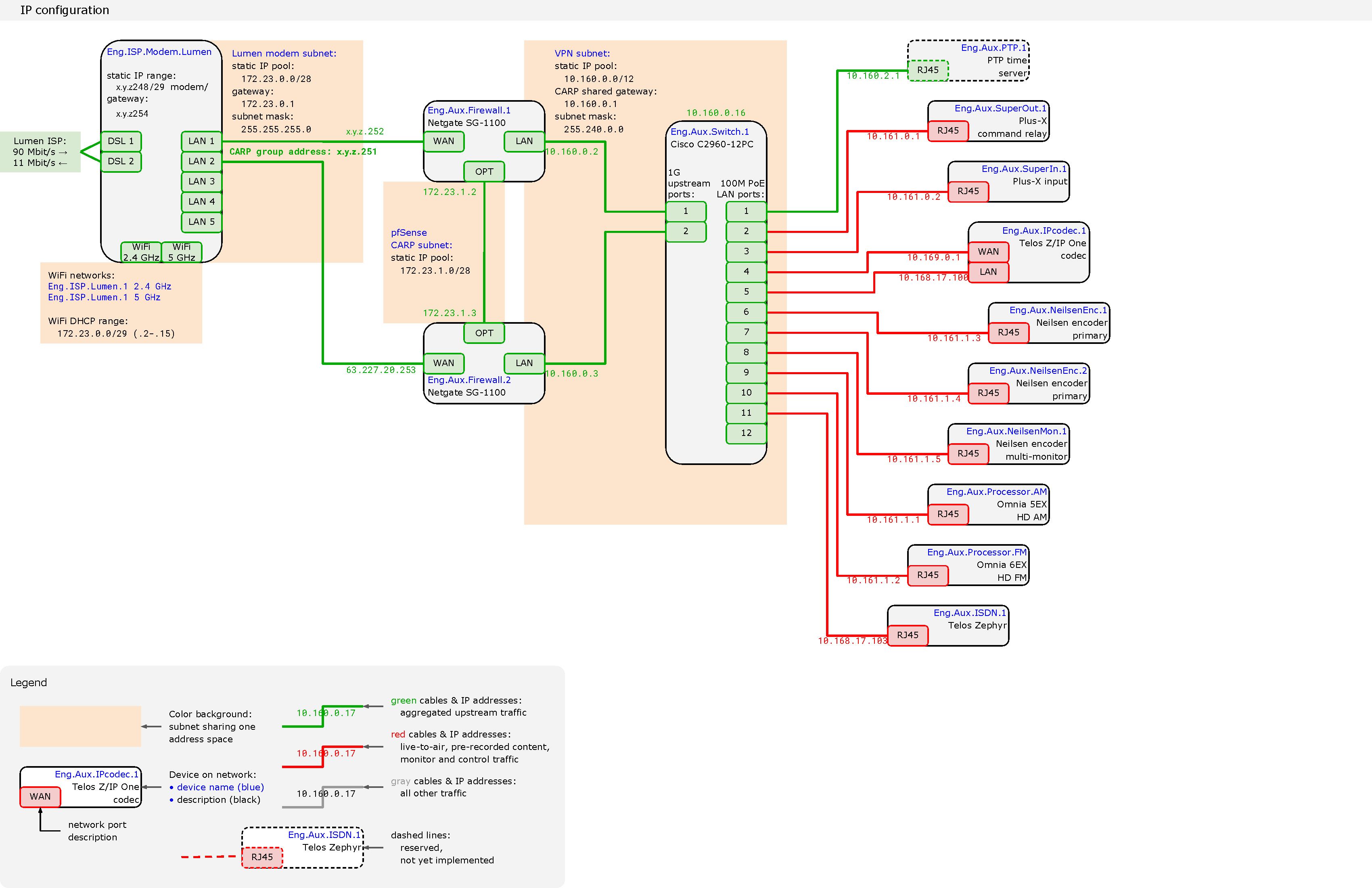
The attached configuration uses two Netgate appliances to implement High Availability.
(At the moment there is only one WAN. Later dual-WAN will be added.)OpenVPN provides remote access to clients.
This general works fine, but there is a minor, annoying, lingering problem: an OpenVPN client cannot access the second (standby) pfSense appliance with its assigned LAN address (e.g., 10.160.0.3 in this diagram).
The OpenVPN client can SSH into the console port of the Cisco switch. The switch can be instructed to ping the pfSense appliance at 10.160.0.3 successfully.
The OpenVPN client can ping the current primary pfSense appliance at the group address (10.160.0.1) and its individual address (10.160.0.2)... and can log-in to its web configurator at those addresses successfully.
However, the OpenVPN client cannot ping nor log-in to the second pfSense appliance (on standby).
A local on-site device behind the Cisco switch can access the pfSense appliance at 10.160.0.3 successfully with pings and log-ins.
There must be some peculiarity of how OpenVPN is working that precludes either routing to the second pfSense appliance or perhaps returning the response from that appliance.
Any suggestions?
— Eric
-
@eric-scace
This is an expected behavior, because the secondary has no route to the OpenVPN clients virtual IP.You can find how to workaround this by adding a masquerading rule in the docs: Troubleshooting VPN Connectivity to a High Availability Secondary Node
-
@viragomann Thank you! That's exactly what I needed to know — and it fits all my observations perfectly. (And I'm sorry to have overlooked that one troubleshooting article.)
-
Could someone post an example for the necessary NAT rule(s), please?
EDIT: got it already, at least I think so