IKEv2 IPSEC VPN - Randomly stopped working
-
@brswattt said in IKEv2 IPSEC VPN - Randomly stopped working:
@mamawe What is the benefit with and without? I'm not sure if I do need it exactly, I just want the client to connect after the lifetime expires, thats all.
The benefit depends on what your situation is.
Basically rekeying means replacing only the session keys while reauthentication means tearing down the IKE session and creating a new one from scratch. With IKEv2, rekeying can be done for Child SAs (ESP) as well as for the IKE SAs (IKE itself) by exchanging CREATE_CHILD_SA messages. IKEv1 supports only reauthentication of the IKE SA.
I personally haven't been in a situation where I needed reauthentication with IKEv2.
This page from the Strongswan Wiki may explain the topic better than I can do it.
-
@mamawe Regarding rekeying, if you follow the link to interoperability issues with Windows on the Strongswan Wiki page, you can find that at least with Windows 7 clients rekeying of the IKE SA does only work with DH group modp1024.
I don't know if that applies to your client.
-
@mamawe it's a Windows 10 machine. Definitely a Windows issue as my Android phone had no problem rekeying both phases.
-
@brswattt Looks like that bug reaches out to windows 10 as well. I triggered a manual rekey with
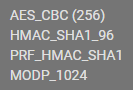 these algorithim settings (windows default), and I can rekey just fine.
these algorithim settings (windows default), and I can rekey just fine.go back to this:
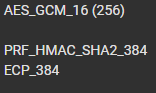 and rekey fails 100% of the time.
and rekey fails 100% of the time.I dont understand how in 2022 windows 10 is still forcing you to use less secure parameters
Even setting the Group to DH2 with the AESGCM256, it still doesn't work, so I'm forced to use AES/SHA1/DH2 which isn't secure at all. Thanks Microsoft.That algorithm works on Android though. Very stupid.
-
I added/changed it to AES/SHA256/DH14 in my router and client settings and rekey works! Way better than SHA1/DH2. I can live with this..