Issues reaching end devices across subnets
-
My topology is shown in the image at this link
This is the topology I would like to stick with for now, until I am able to carve out time to mess with our home network overall (wife and I both work from home and have a kid).
I have a dedicated PC running pfsense, and the attached image shows the overall network. I am connected to ExpressVPN, and the end devices' traffic is indeed going through the VPN as desired.
I can ping from:
- Laptop to 192.168.0.152
- Laptop to 192.168.1.1
- PC to 192.168.1.1
- PC to 192.168.0.1
But I cannot ping from:
- Laptop to PC/PC to Laptop
I have network drives that I share from the PC when it is on 192.168.0.0/24, but the drives are not accessible when it is on 192.168.1.0/24.
I have tried the following as troubleshooting:
- Static route from 192.168.1.0/24 to 192.168.0.1
- Any combination and reordering of rules, as well as specifying to allow certain traffic to traverse certain ports
- Last ditch effort I allowed all traffic ipv4+ipv6 from all interfaces (fully open the firewall)
None of these worked. There must be something I'm missing, as the pinging is only having problems between end devices on other subnets, which would lead me to believe a static route would be necessary.
Please let me know what other information I can provide (like config xml), if anyone has some advice for getting this to work. And again I know the topology is not desirable, but I'll be surprised if that is the only reason this is having problems.
Alternatively, I'm open to making the pfsense box a wired AP so everything is on the same subnet. But I am not sure how to get that to work while also directing certain traffic to the VPN and the rest to my LAN. I also don't necessarily want all devices routed to the VPN anyway.
Thanks in advance.
-
@rsherga asymmetrical nightmare.. Your hosts are on your transit network.
Use pfsense as your primary router, and use that wifi router as just an AP..
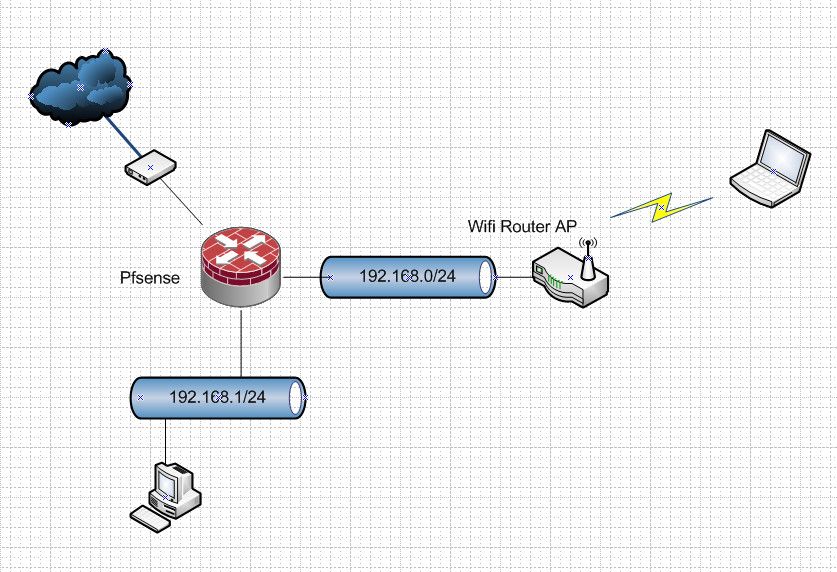
This is the correct way to set it up.. Your soho wifi router is not capable of actual routing and creating another network/vlan to use as a transit network.. It makes no sense to try and put a vpn connection downstream etc.
Put pfsense as your edge/primary router and you can do whatever you want with multiple network or vlans and having wireless on its own network via just a AP, etc..
Trying to do it any other way is just a waste of time and effort and going to cause you nothing but grief. This setup should take you all of 5 minutes to get up and running..
If your going to setup pfsense as a downstream router, did you disable its nat? Did you setup your upstream router to nat the downstream network?
If you want to use it as just downstream natting firewall/router then there is no need for routing, etc..
-
Parsing...
Parsing...Wishing I had a different Internet connection to test all this out on....
Bummer.
I actually have no desire for multiple domains, I only had the two because of the pfsense box being set inside my existing network.
So would it be a reasonable expectation that I could set firewall and routing rules for only my PC's TCP 80 and 443 traffic (or other specified ports) to go through my VPN virtual interface, and the rest of it and all other devices' traffic to go through the ISP? Could that be achieved via static routing + firewall rules?
I very much appreciate your advice so far btw.
-
@rsherga if you put pfsense at the edge then pretty much sure you can do anything you want for devices to use a vpn or not use a vpn.. This is simple policy routing.
If your going to use it as you drew it - there is not routing and just use pfsense downstream natting.. To your soho router its just another client on its 192.168.0 network..
If you want to access stuff behind pfsense from stuff on your soho routers network, this would be done via port forwards on pfsense, and your clients on the soho network would access pfsense wan IP and be forwarded depending on what port, etc.
You could then have stuff behind pfsense use some vpn or not as well. If you want to access stuff on your soho network from client behind pfsense just access them, but you would have to have rules to allow it that don't policy route your traffic out some vpn you setup, etc.
If you want to set it up how it actually should be setup then my drawing is how it would be done.. This gives you the most control the most flexibility and the best ability to grow.. Adding a vlan capable switch, and actual AP that can do vlans and you really could do anything you could ever think of wanting to do..
-
HA! Oh man I did try forwarding ports along with the rest, maybe I just didn't forward what was needed. At least I know I was on the right track at some point.
I do aim to have it more like you drew, as it is intended. I just have limited time to get it running appropriately without the house exploding from internet being down for a bit.
Thank you so much again. This is pretty badass software yall distribute, and I'm happy I finally pulled the trigger on it.
-
@rsherga To get your network working just setup pfsense natting. NO routing nothing on your soho router. To it pfsense is just another client, you could put as many clients behind pfsense as you want, and to your soho router its all just coming from some IP it handed to pfsense wan.
Just like your isp sees all your stuff as the router wan IP..
You can then get stuff working via port forward. Off the top your port forwarding wouldn't of worked unless you also turned off the default block rfc1918 rule on pfsense wan, because all your stuff on soho network is rfc1918 and would of been blocked from any port forwards your setup anyway.,