Acme adds out of date CA to cert manager
-
I am running pfSense 2.6 and Acme 0.6.10_1. When acme renews my cert from LetsEncrypt, it is adding a version of ISRG Root X1 as a CA in the certificate manager that was issued by DST Root CA X3 whose certificate expired on September 30, 2021. At https://letsencrypt.org/certificates/ it shows that the active root is a different version of ISRG Root X1, issued by ISRG Root X1 that does not expire until 2035. I have deleted the CA's added by Acme and manually renewed several times and this incorrect CA keeps coming back. This appears to be a problem. Am I missing something? Why is Acme not installing the current CA? How can I fix this?
-
@joelkolb - did you ever delete it like was mentioned?
https://forum.netgate.com/topic/166269/heads-up-dst-root-ca-x3-expiration-september-2021
I had deleted mine back when that was mentioned, and sure don't see it back...
-
@johnpoz Yes I did. But the older ISRG Root X1 that has DST Root CA X3 as its root keeps coming back.
-
Same issue here.
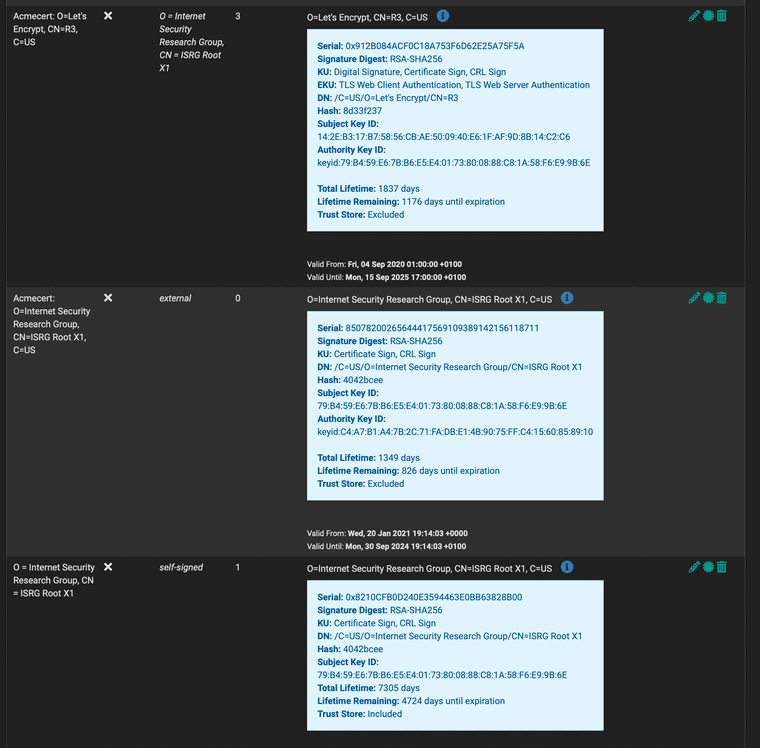
This is getting in the way for my OpenVPN server setup, as clients cannot validate the certificate chain.The solution was to manually remove the ISRG Root X1 installed by ACME package and add the self-signed version to cert manager.
See the attached screenshot. ISRG Root X1 installed by ACME package in cert manager is signed by DST Root CA X3, which is expired.
-
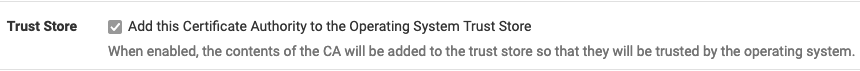
@dguerri You checked the box, that's why this problem is.

-
@nonick
Yep, but I think this is needed to let openVPN client export generate the correct ca bundle when exporting client configuration.After the manual operation described above, everything works fine, and I can uncheck that box to avoid it from happening again.
Nevertheless, the problem will come up again when/if certs are renewed/expired.EDIT: That box has no effect for my case (openVPN). I think the root cause is ACME package adding the wrong CA chain (as it ends with an expired cert)
-
This post is deleted! -
@nonick dug into the code a bit :)
Apparently, the problem is the chain provided by Let's Encrypt!
ACME scripts get that URL from Let's encrypt, and they just import all the CAs in there into the cert manager.
My theory is that all the certificates created before DST Root CA X3 expiration (regardless of their expiration or date of renewal), are still getting the CA chain that was valid at the time.
Maybe the solution would be to drop and recreate the configuration for these certs in pfSense...
-
We are getting this exact issue too.
I have tried a fresh PFSense install with fresh subdomain certificates and the same thing happens.
We get reported issues via SSLLabs and Nessus flagging that this additional chain, we do not need to support Android 7.
This can be recreated every single time so not sure how others have it working but hope there is a solution out there other than manually deleting the rogue CA.
-
Has anyone had any luck resolving this issue?
I'm also seeing this exact issue on 2.6.0 with the acme 0.7.1_1 package.
Deleting the CA doesn't seem to work as it just gets re-created.