Firewall UDP ? Attack !! Or Normal ?
-
Is this normal?
Should I accept this traffic?
What is this behavior due to?
-
@silence
You should consider silencing that rule.
Ask the person who created that rule if it needs to 'log' every hit.
Askk him also : what will happen when I receive a lot of UDP WAN hits ? Like a real 'full pipe' DOS ?
Or, as you control pfBlokerNG-devel, have all WAN rules not to log.
Better : it is actually counter productive to log block rules on a WAN interface - or even place block rules - see below.If you want to control traffic that comes in to your WAN interface, go see your ISP, and place a firewall on their side, as only they can control what's send to you - over your WAN wire.
and here it comes : not you (using pfSense).You should know that you can not be a part of the Internet (your WAN IP) and not being part at the same time.
As soon as you plug in that "WAN wire", others, the other 255255255*255 - 1 IP addresses, can try to connect to your IP .... just like a phone : as soon as you have a number, and you connect to the public phone network, yeah, you can call some one, and the other xxxx billion can call you.
And yes, their are many that actually try to do just that. Scanning for every known exploit.So, now you know there is something as an "Internet back ground noise" and that's why there is, by default, just one final, hidden firewall rule on every interface : block everything, and don't tell ( don't log).
See for yourself this section
#--------------------------------------------------------------------------- # default deny rules #---------------------------------------------------------------------------in the /tmp/rules.debug file.
edit : and don't post your mail in the footer.
That's not very 'cyber Security' aware. -
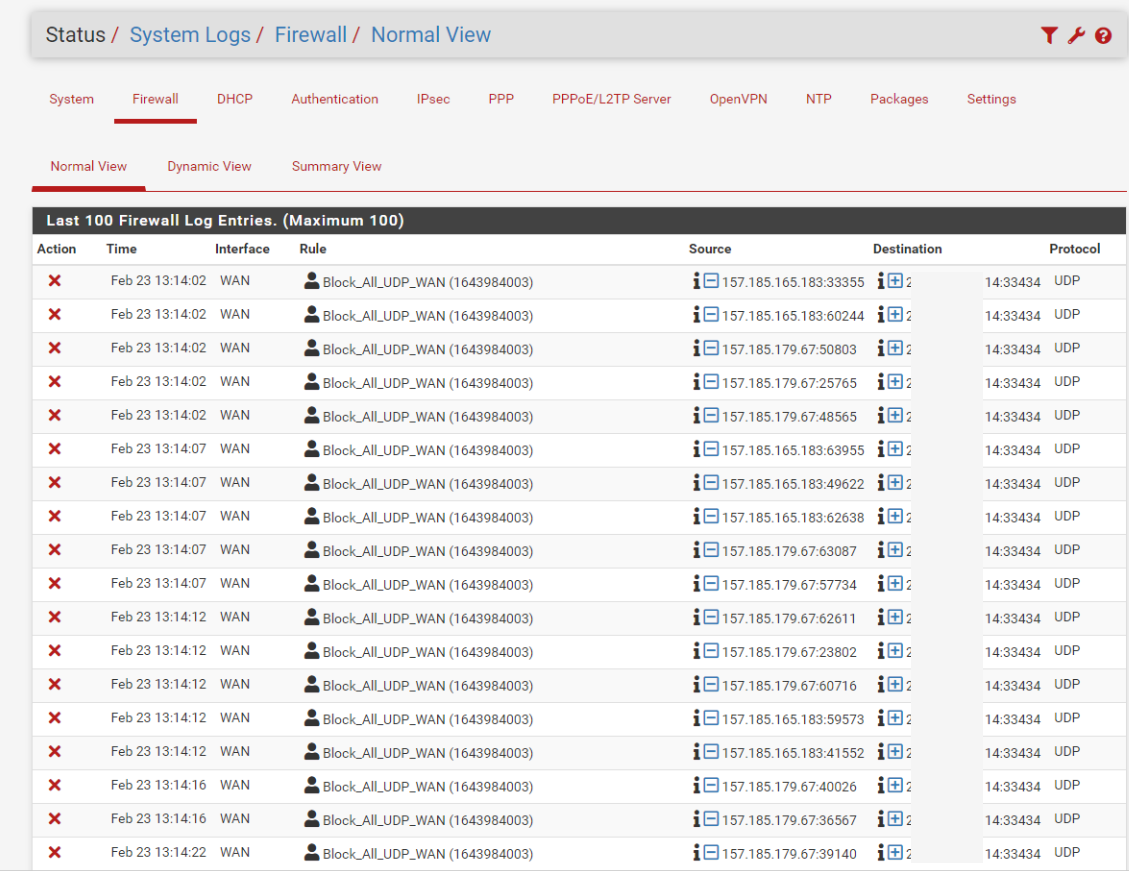
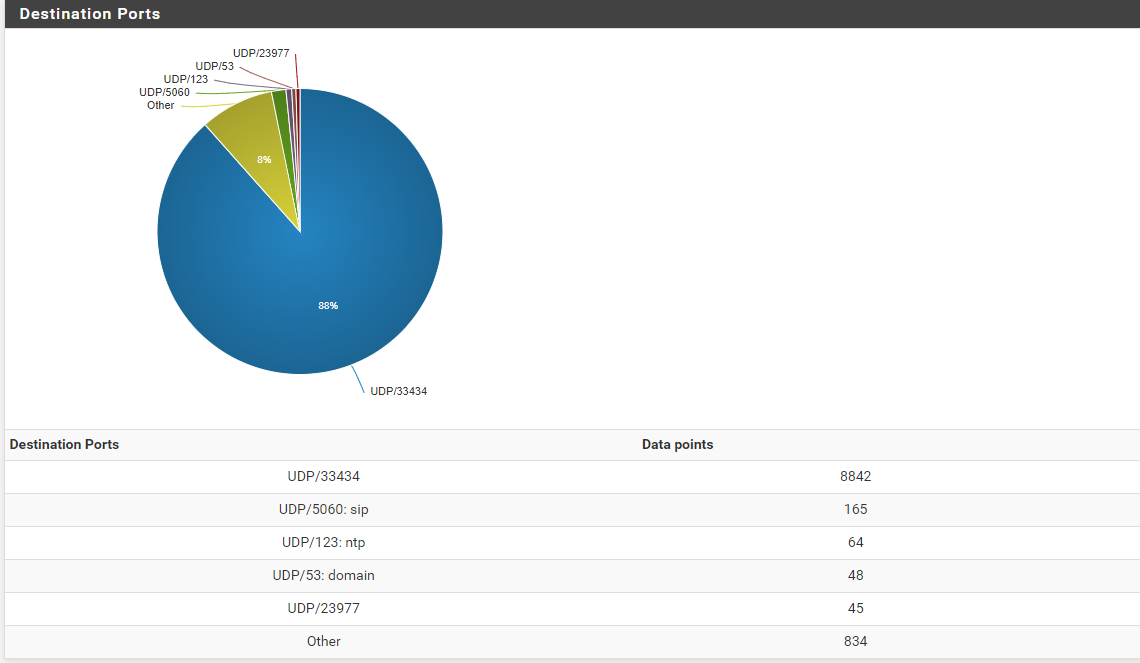
@silence 33434 is first port of the traceroute range
33434-33523
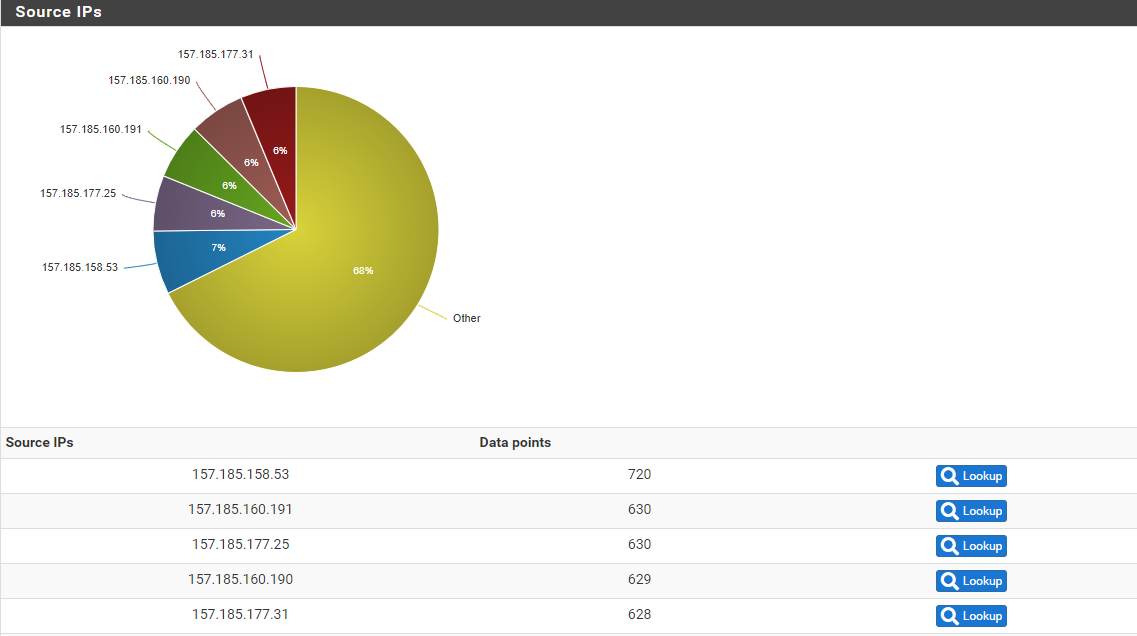
Those IP are both from Quantil, they are global cdn - don't see them much they out of CA..
It is curious traffic.. Could be p2p traffic.. that is normally what high range UDP traffic is.. I would sniff it and see if its just traceroute traffic..
Do you see the port go up to 435, 436, etc..
Why would you accept traffic that you did not instigate? Or that your hosting - are you running anything that listens on 33434? p2p maybe? Simple packet capture and open in wireshark should give you some more clues to that the traffic is..
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
Do you see the port go up to 435, 436, etc..
8842 ON Port 33434 /UDP

-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
are you running anything that listens on 33434?
NO
-My Wan Rules
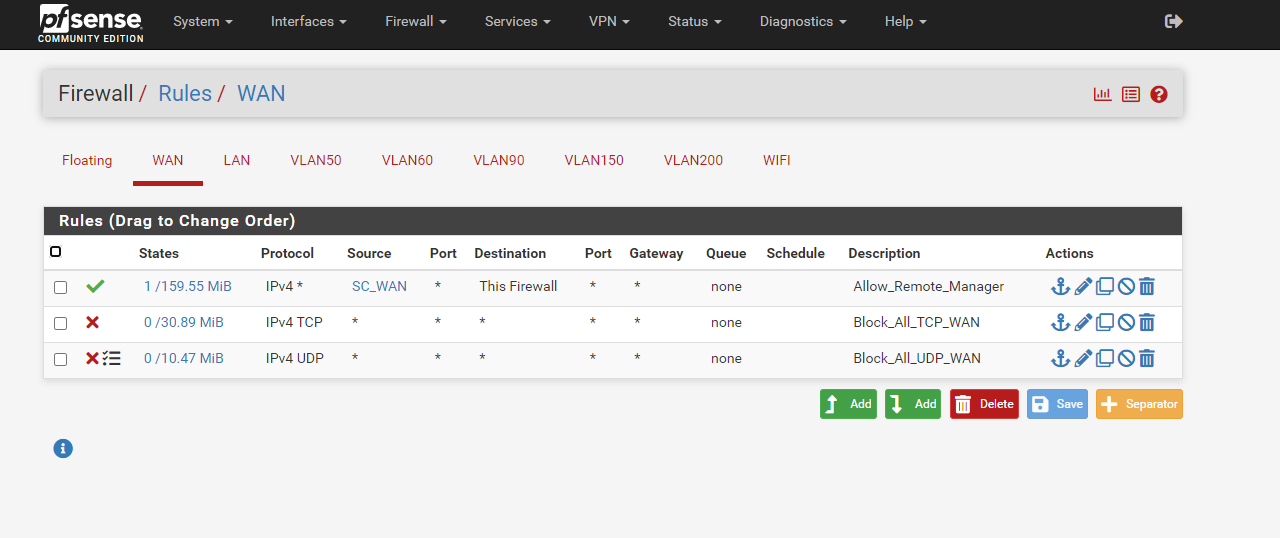
-NO NAT
-
@johnpoz
Yeah, could be anything.
Maybe @Silence forgot to tell us he is using a VPN. So he sees the side effect of what the previous WAN IP owner was doing ;)Something I normally did, in the past, when (phone line modem) 'POTS connections was the only option available:
I got an new IP from my ISP.
I actually activated logging of any non solicited traffic. If the incoming rubbish traffic was just a killobit/sec or so, I kept the IP, as it was 'clean'.
If not, I took another IP.
And as always : I had to control my LANs - the devices connected to it. When some local idiot installed that utorrent again, my WAN IP would get bombard (polluted) over time. So, some local "cyber awareness training" was needed.
And so on.These days, with multiple Mbits/sec on my WAN, I don't care any more. The last time I changed my WAN IPv4 and IPv6, was back in 2017 (I guess).
edit :
You don't need the last two rules. Because ... see my post above.
True, you might want to know "who" or "how much" is hitting your WAN. If it's 'to much, it hinders you, change your WAN IP - if possible.
The stop logging again. Apply the "what you can't see doesn't exist" rule ^^ -
@gertjan said in Firewall UDP ? Attack !! Or Normal ?:
And as always : I had to control my LANs - the devices connected to it. When some local idiot installed that utorrent again, my WAN IP would get bombard (polluted) over time. So, some local "cyber awareness training" was needed.
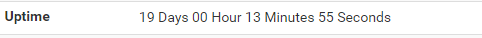
As you can see, this pfsense has been on for 19 days using the same static public IP.
on dhcp it has some 200 clients now.
I don't know if what you are trying to tell me is that someone within these 200 clients is using malicious software
-
@silence I would sniff the traffic via diagnostic packet capture.. What is in it.. From that you should be able to gleen more info..
Post up the pcap, you can change your IP in the pcap.. Simple way to do that would be with https://www.tracewrangler.com/
-
@johnpoz Right now, I have the same behavior...
this is annoying.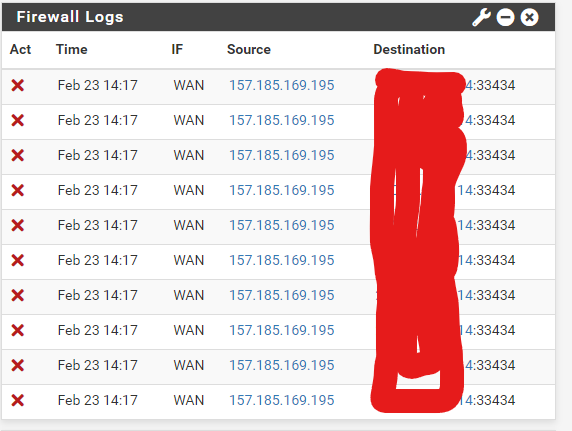
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
@silence I would sniff the traffic via diagnostic packet capture.. What is in it.. From that you should be able to gleen more info..
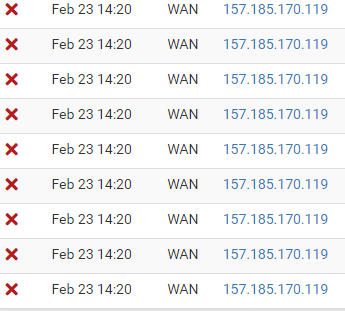
change the ip and return to the same port.
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
@silence I would sniff the traffic via diagnostic packet capture.. What is in it.. From that you should be able to gleen more info..
Running....
-
@silence huh? Do a packet capture, and open it up in wireshark.. From that can most likely gleen some more info..
Post up this packet capture if you don't understand what its telling you. You can change the dest IP of the traffic (your public ip)..
Here I did a simple packet capture of udp, ntp is what I normally see because I run ntp server in the ntp pool... Anyway here is sniff of a few of those packets - clearly my public IP is not 1.2.3.4 because I replaced my real one with the tool linked too..
I would prob have set the packet capture to be more zoned in on the specific - say UDP only, etc.. or just that port your seeing as well..
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
say UDP only, etc.. or just that port your seeing as well..
I keep capturing only port 33434
but for some reason I am no longer receiving this traffic, I will leave the capture open in case I receive any...! in 15 minutes update
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
Here I did a simple packet capture of udp, ntp is what I normally see because I run ntp server in the ntp pool... Anyway here is sniff of a few of those packets - clearly my public IP is not 1.2.3.4 because I replaced my real one with the tool linked too..
-
@silence As Gertjan alluded to, why do you care? There's going to be a constant stream of traffic coming at every IP from the Internet as IPs get probed. Logging that traffic just going to take CPU cycles, fill your logs, and waste disk write cycles.
-
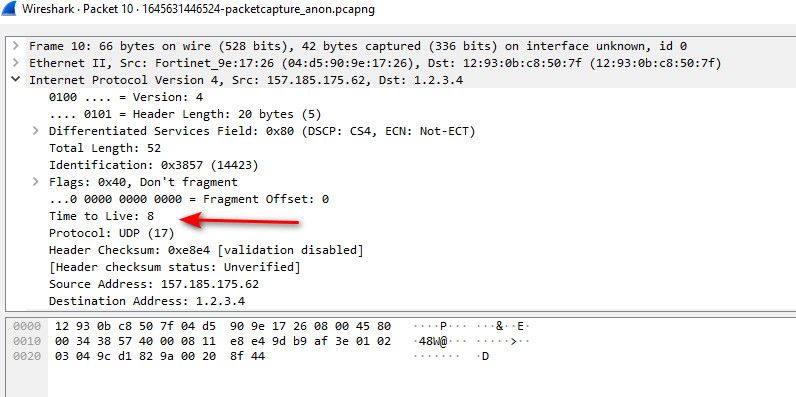
@silence why did you truncate the capture.. can not see full payload - so really hard to tell what that is.. But from the ttl on the packets, they are very low, and seem to increment - but they also seem out of order? when a traceroute would count down, or up etc.. depending on where your capturing etc..
On the tracewrangler make sure you uncheck everything other than changing the IP..
So either these are after many many hops.. Or what is sending them is changing the ttl, like in traceroute..
But as mentioned - other than a curiosity, you can't really stop someone from sending you traffic.. Unless you control the sender.. So while trying to figure out what this is - not much you can do about it.. So you could just drop it without logging it if its causing you grief in seeing it in the logs..
Normally traceroute - see how the ttl is changing..
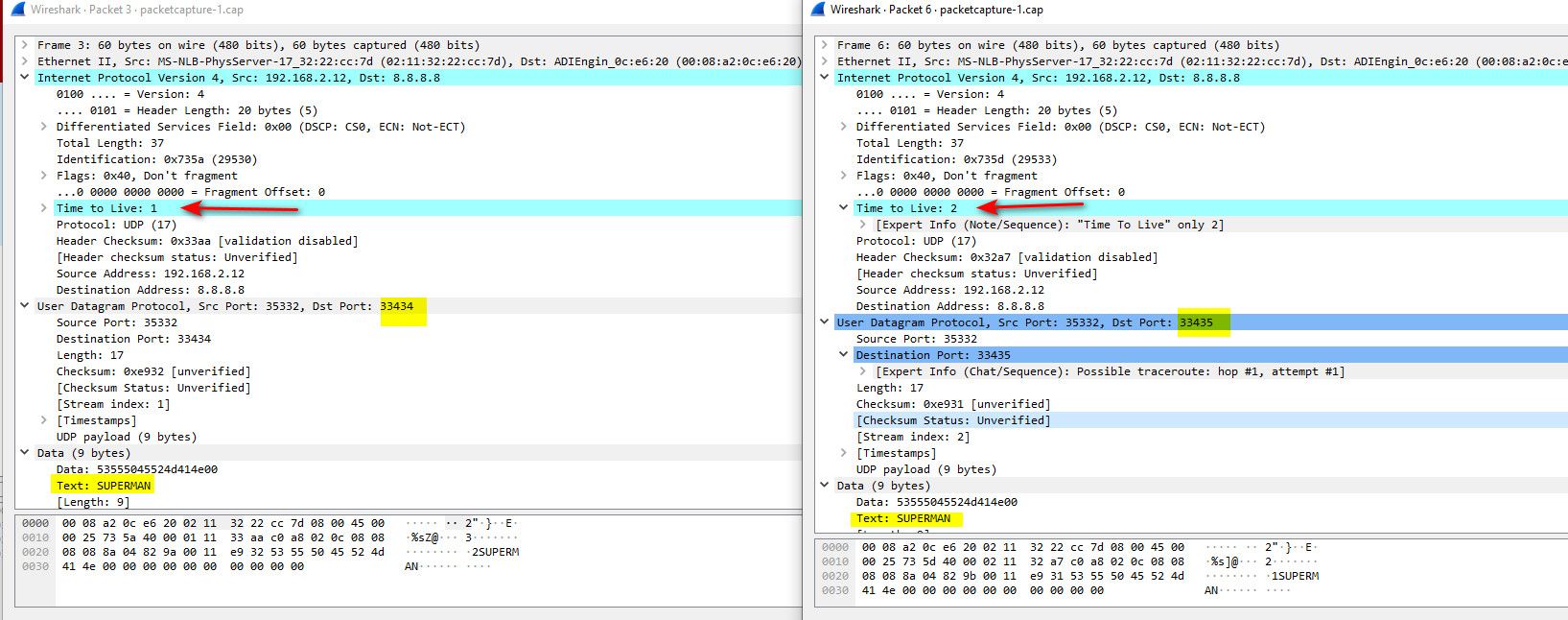
See how the data is specific.. different traceroute programs might send different text.. Also normally the source port would be same
see how source port is the same, and the port is increasing..
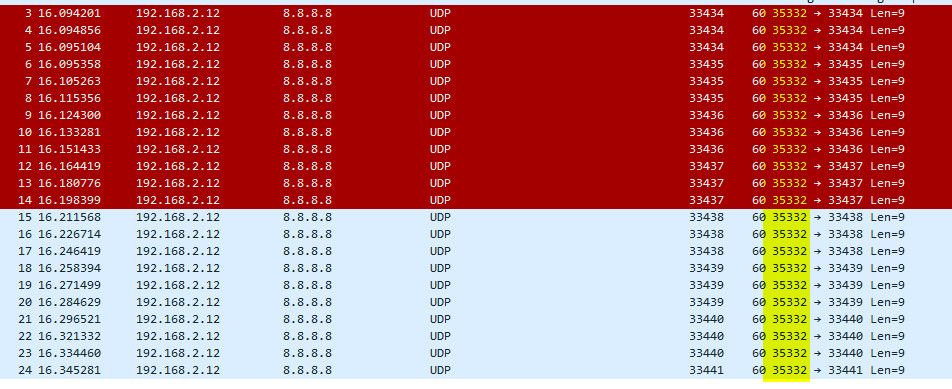
And sent in groups of 3..
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
@silence why did you truncate the capture.. can not see full payload - so really hard to tell what that is.. But from the ttl on the packets, they are very low, and seem to increment - but they also seem out of order? when a traceroute would count down, or up etc.. depending on where your capturing etc..
On the tracewrangler make sure you uncheck everything other than changing the IP..
So either these are after many many hops.. Or what is sending them is changing the ttl, like in traceroute..

But as mentioned - other than a curiosity, you can't really stop someone from sending you traffic.. Unless you control the sender.. So while trying to figure out what this is - not much you can do about it.. So you could just drop it without logging it if its causing you grief in seeing it in the logs..
Normally traceroute - see how the ttl is changing..

See how the data is specific.. different traceroute programs might send different text.. Also normally the source port would be same
see how source port is the same, and the port is increasing..

And sent in groups of 3..
update
-
@silence said in Firewall UDP ? Attack !! Or Normal ?:
Normally traceroute - see how the ttl is changing..
So, should I just ignore that a Network 0/16 is sending traffic to port 33434 to my wan?
simply because you can not determine your goal ?
Also the port is always 33434 I don't think it's a simple traceroute.
rather it seems to me that someone with access to this entire /16 network tries to execute something against my wan
-
@johnpoz said in Firewall UDP ? Attack !! Or Normal ?:
@silence why did you truncate the capture.. can not see full payload - so really hard to tell what that is.. But from the ttl on the packets, they are very low, and seem to increment - but they also seem out of order? when a traceroute would count down, or up etc.. depending on where your capturing etc..
On the tracewrangler make sure you uncheck everything other than changing the IP..
So either these are after many many hops.. Or what is sending them is changing the ttl, like in traceroute..

But as mentioned - other than a curiosity, you can't really stop someone from sending you traffic.. Unless you control the sender.. So while trying to figure out what this is - not much you can do about it.. So you could just drop it without logging it if its causing you grief in seeing it in the logs..
Normally traceroute - see how the ttl is changing..

See how the data is specific.. different traceroute programs might send different text.. Also normally the source port would be same
see how source port is the same, and the port is increasing..

And sent in groups of 3..
@johnpoz I think I found something that could be the error, but I need a little of your help to determine or confirm my theory.
-
@silence said in Firewall UDP ? Attack !! Or Normal ?:
rather it seems to me that someone with access to this entire /16 network tries to execute something against my wan
That seems to be a bit tight on the tinfoil hat ;)
Now that port range could also be older SIP calls 33434-33598
Many of the packets are sending the same data.. But can not make out what it is exactly
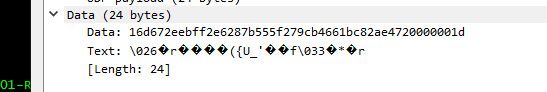
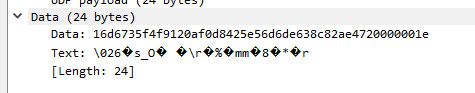
There are some others that are duplicated as well.
It just a guess of mine that 33434 UDP was traceroute - doesn't mean it actually is that.. Other stuff could use that port.. webex teams, Noction version of bgp I think..