One tunnel multiple peers?
-
@f-meunier said in One tunnel multiple peers?:
@swemattias
I see on tunnel config : listen port 55120
but you set the other side's enpoint port as 58220
This should be the same portThat is just mistake from my side during preparing the post. Ofc I have the same port.
-
@f-meunier Here are those configs:
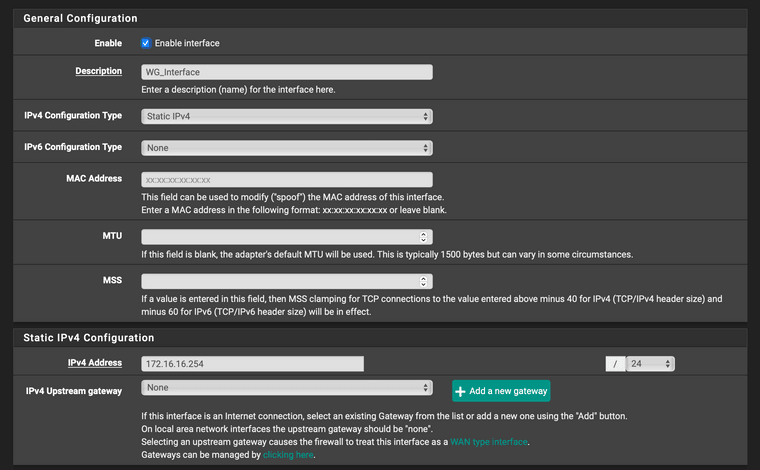

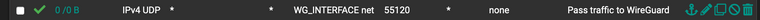
-
@swemattias
please try checking "dynamic"
Doing so, you only have to set parameters on the "fixed" side...
(client side will "use" these params in the [Peer] section) -
according to your screenshots, you should have :
[Interface] PrivateKey = <Device 1 private key> Address = 172.16.16.1/24 DNS = 172.16.16.254 [Peer] PublicKey = <Server/pfSense public key or in your words FWpubk> AllowedIPs = 172.16.16.0/24, 10.0.0.0/24 Endpoint = wg.domain.io:55120pinging 172.16.16.254 from client works ?
-
@f-meunier That didn't help, setting it to Dynamic, I can surf and write this through this tunnel, but I cannot reach the inside.
-
@swemattias
also confirm in pfSense' peer config that "Public Key : device 1 pkey" is the public key of the client(not the private key from [Interface] PrivateKey)
-
@swemattias
sorry, I did not understand the situation.
You have a computer connecting to the pfSense through the WG tunnel, you manage to surf through but can't access internal network 10.0.0.x /24 ?according to your config, it's not a "catch all" tunnel. Your computer access to the internet will not use the tunnel, but its local router/gateway directly...
-
@f-meunier Yes I am testing with my computer to see if it works.
First question - yes. Switching to 4G network activating the tunnel.
I cannot ping anything on either 172.16.16.0/24 or 10.0.0.0/24. -
let's summarize.
Your computer client should have 2 interfaces :
LAN interface (let's say 192.168.1.1/24)
wireguard interface : 172.16.16.1/24client config is
[Interface] PrivateKey = <Device 1 private key> Address = 172.16.16.1/24 DNS = 172.16.16.254 [Peer] PublicKey = <Server/pfSense public key or in your words FWpubk> AllowedIPs = 172.16.16.0/24, 10.0.0.0/24 Endpoint = wg.domain.io:55120pfsense has public IP wg.domain.io
LAN interface IP is 10.0.0.254/24
wireguard tunnel (tun_wg0) is bound to interface WG_INTERFACE
WG_INTERFACE has static IPv4 172.16.16.254/24
tunnel listen port = 55120 -
On the client computer side, what is the output of "route print -4" ?
-
@f-meunier route is available in OS X but not like that... :) No idea what do you want outputted? ;)
-
@swemattias
let me check the equivalent command in OSX... -
netstat -rn
-
the routes to 172.16.16.0/24 and 10.0.0.0/24 should appear in the list
-
@f-meunier This is what I get out cut out the lines with the right info in them:
10.0.0/24 link#16 UCS utun5 127 127.0.0.1 UCS lo0 127.0.0.1 127.0.0.1 UH lo0 172.16.16/24 172.16.16.1 UGSc utun5 172.16.16.1 172.16.16.1 UH utun5 -
@swemattias
well, your tunnel seems effectively up, and the routes are there.
what is the pfSense config of LAN interface ? 4th byte of 10.0.0.x address ? -
can you give the pfSense STATUS > Wireguard
(click on Show peers to see the details) -
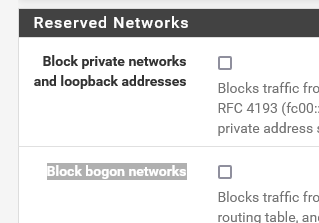
One last check on WG_INTERFACE
Verify that "Block private networks and loopback addresses" and "Block bogon networks" are UNCHECKED
-
nevertheless, ping 172.16.16.254 should work...
-
what is curious :
route 10.0.0.0/24 should be accessible through a gateway -> flag " G" missing.really need to know your macOSX LAN IP...
also can you explain "I can surf and write this through this tunnel, but I cannot reach the inside."