Remote Code Execution in pfSense <= 2.5.2
-
Remediation
Upgrade pfSense CE to version 2.6.0 or pfSense Plus to version 22.01.
or
If you can't update to 2.6.0 at the Moment, you still can apply the security fix to 2.5.2 with the Patches package.
- Install Patches package via System > Package Manager > Available Packages 1. (set Update Branch to 2.5.2!)
- or via Command line: "pkg add -f https://firmware.netgate.com/pkg/pfSense_plus-v21_05_1_amd64-pfSense_plus_v21_05_1/All/pfSense-pkg-System_Patches-1.2_6.txz"
- Go to System > Patches > "+ Add New Patch"
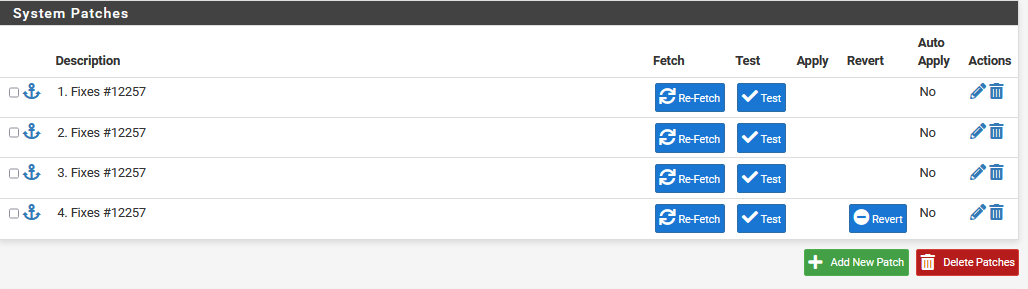
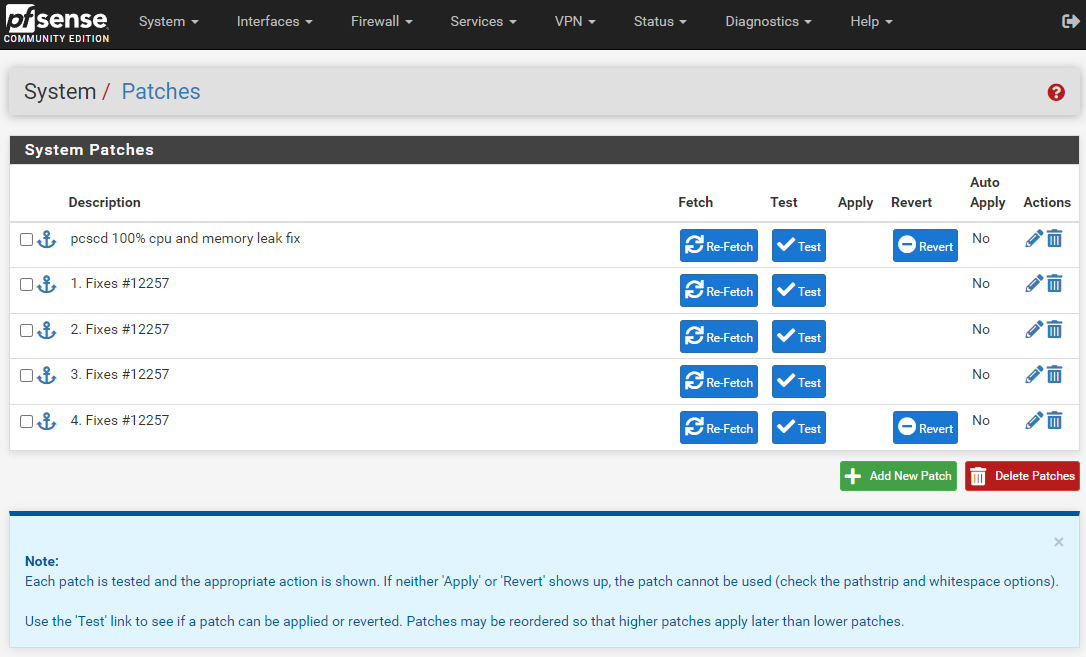
- Description = 1. Fixes #12257
- URL/Commit ID = https://github.com/pfsense/pfsense/commit/72ea2b69cc111d4bc8ebf1ccf1e1529923c5b88a
- Save
- "+ Add New Patch"
- Description = 2. Fixes #12257
- URL/Commit ID = https://github.com/pfsense/pfsense/commit/57a737f172b7baaa6ae0f23e8aef2f93ad851054
- Save
- "+ Add New Patch"
- Description = 3. Fixes #12257
- URL/Commit ID = https://github.com/pfsense/pfsense/commit/8cd3f92f2443a6f0e4b7964a9532f761f808a0c6
- Save
- "+ Add New Patch"
- Description = 4. Fixes #12257
- URL/Commit ID = https://github.com/pfsense/pfsense/commit/cf757a8094762ede47861fc073eaba06355c6bfc
- Save
- It should look like this https://imgur.com/a/1wsSjwV
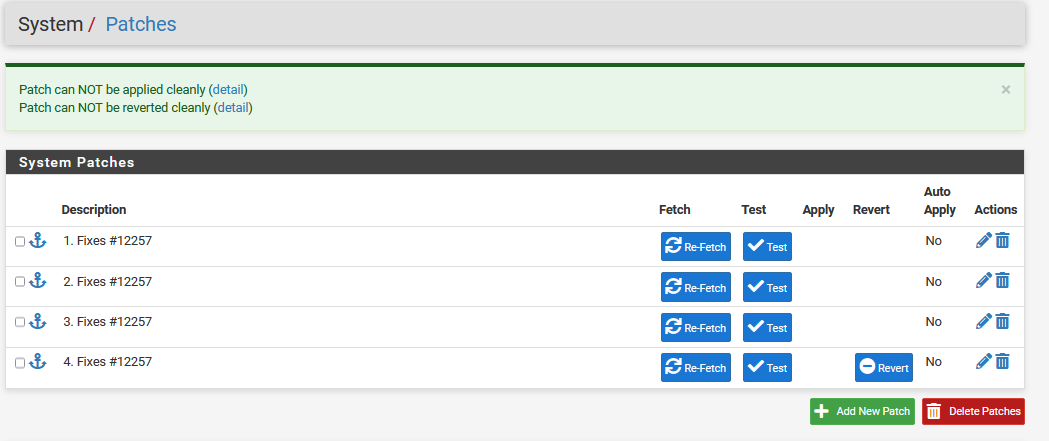
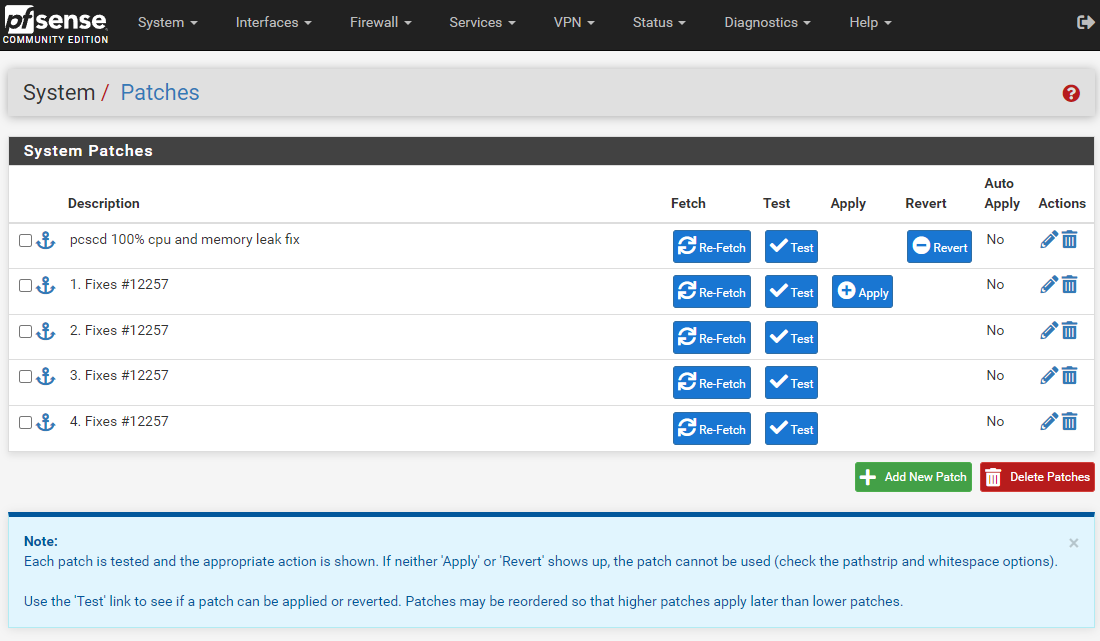
- Now you can Apply the patches one by one in chronically order beginning with 1. Fixes #12257
- If needed you can reverse the patche the same beginning with 4. Fixes #12257
Good luck.
before
after
-
You cant do that since the 2.5.2 package repository doesnt exist anymore.
-
You can try:
pkg add -f https://firmware.netgate.com/pkg/pfSense_plus-v21_05_1_amd64-pfSense_plus_v21_05_1/All/pfSense-pkg-System_Patches-1.2_6.txz(this is for amd64!)
Or make your own from here
https://github.com/pfsense/FreeBSD-ports/tree/devel/sysutils/pfSense-pkg-System_Patches
@cool_corona said in Remote Code Execution in pfSense <= 2.5.2:
You cant do that since the 2.5.2 package repository doesnt exist anymore.
-
@bismarck That worked. Thanks.
-
Getting this error...
/usr/bin/patch --directory=/ -t -p2 -i /var/patches/621750e928b24.patch --check --forward --ignore-whitespace
Hmm... Looks like a unified diff to me...
The text leading up to this was:|From cf757a8094762ede47861fc073eaba06355c6bfc Mon Sep 17 00:00:00 2001
|From: jim-p
|Date: Wed, 18 Aug 2021 16:11:11 -0400
|Subject: [PATCH] Regex cleanup should also kill {}. Fixes #12257
|
|It's not used often (and less in the GUI) and can be a source of
|problems with large numbers of repetitions even outside of groupedexpressions. src/etc/inc/util.inc 1 file changed, 3 insertions(+), 2 deletions(-) diff --git a/src/etc/inc/util.inc b/src/etc/inc/util.inc index f419e265d5b..2f63b7298e2 100644 --- a/src/etc/inc/util.inc +++ b/src/etc/inc/util.inc
Patching file etc/inc/util.inc using Plan A...
No such line 3843 in input file, ignoring
Ignoring previously applied (or reversed) patch.
Hunk #1 ignored at 3817.
1 out of 1 hunks ignored while patching etc/inc/util.inc
done -
So this ist patch no. 4? It should look like here and apply as the last one!
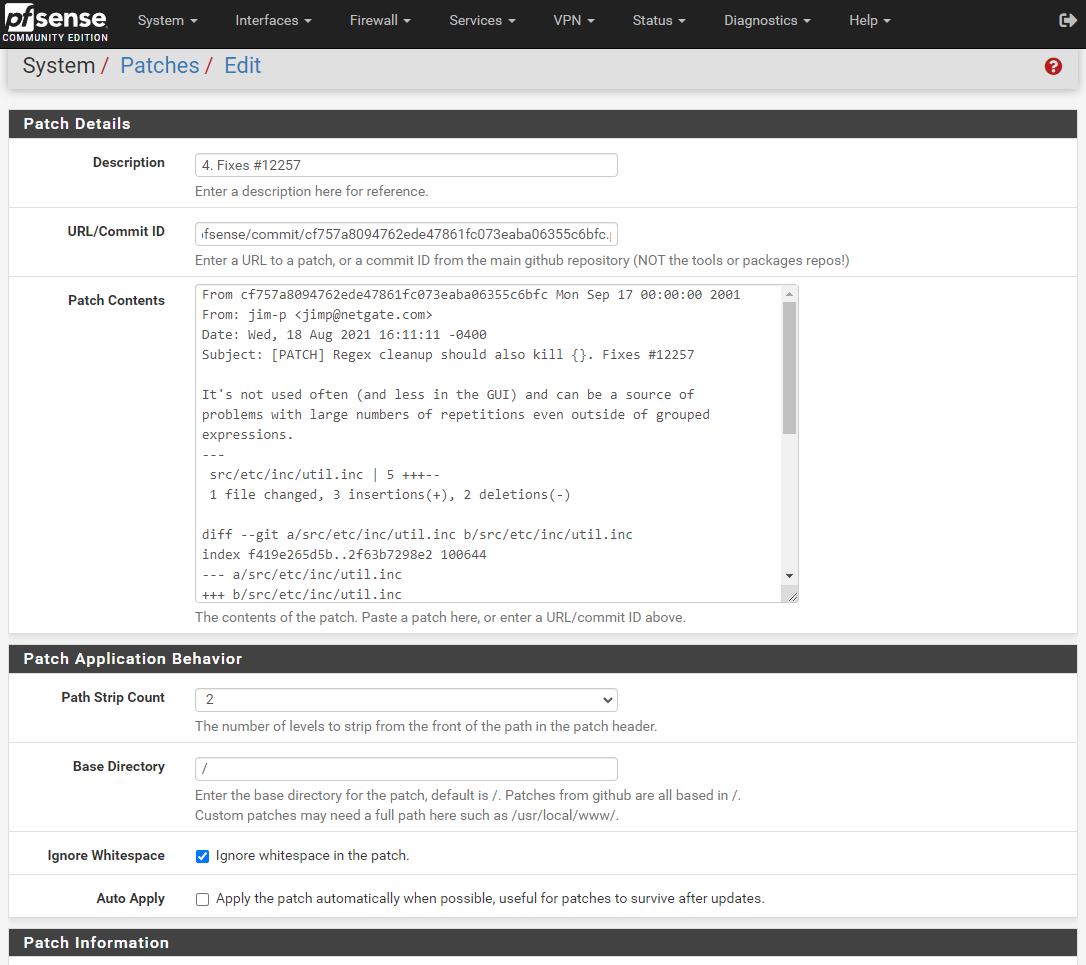
Do always a Test before applying.
-
#1
/usr/bin/patch --directory=/ -t -p2 -i /var/patches/62174f216a692.patch --check --forward --ignore-whitespace
Hmm... Looks like a unified diff to me...
The text leading up to this was:|From 72ea2b69cc111d4bc8ebf1ccf1e1529923c5b88a Mon Sep 17 00:00:00 2001
|From: jim-p
|Date: Fri, 13 Aug 2021 13:46:12 -0400
|Subject: [PATCH] Change route collection and output. Fixes #12257
|
|All changes are on src/usr/local/www/diag_routes.php
|
|* Change problematic use of sed for an equivalent and safer use of tail
| (to remove headers) and grep (to filter output).
|* Restrict AJAX request to POST only
|* Increase update period from 5 to 15 seconds
|* Hardcode output headers, use gettext() and fix some column names
| and formatting
|* Fix route table sorting* If the GET request has a value for "filter", pre-fill that in the form src/usr/local/www/diag_routes.php 1 file changed, 33 insertions(+), 36 deletions(-) diff --git a/src/usr/local/www/diag_routes.php b/src/usr/local/www/diag_routes.php index 40eff33b43e..c0d059c6d79 100644 --- a/src/usr/local/www/diag_routes.php +++ b/src/usr/local/www/diag_routes.php
Patching file usr/local/www/diag_routes.php using Plan A...
Ignoring previously applied (or reversed) patch.
Hunk #1 ignored at 35.
Hunk #2 ignored at 47.
Hunk #3 ignored at 101.
Hunk #4 ignored at 134.
Hunk #5 ignored at 141.
Hunk #6 ignored at 149.
Hunk #7 ignored at 166.
Hunk #8 ignored at 181.
Hunk #9 ignored at 205.
9 out of 9 hunks ignored while patching usr/local/www/diag_routes.php
done#2
/usr/bin/patch --directory=/ -t -p2 -i /var/patches/62174f48d0b24.patch --check --forward --ignore-whitespace
Hmm... Looks like a unified diff to me...
The text leading up to this was:|From 57a737f172b7baaa6ae0f23e8aef2f93ad851054 Mon Sep 17 00:00:00 2001
|From: jim-p
|Date: Mon, 16 Aug 2021 13:42:51 -0400
|Subject: [PATCH] More route display changes. Fixes #12257
|
|* Move escape_filter_regex() from syslog.inc to util.inc since it will
| be used by things other than syslog.
|* Add some basic regex sanity and consistency check functions
|* Cleanup diag_routes.php route filter before use
|* Ensure diag_routes.php route filter is not misinterpreted as grep command line
| paramters
|* Add warning to diag_routes.php that invalid filters will be ignored.* Ensure diag_routes.php AJAX gets CSRF protection src/etc/inc/syslog.inc src/etc/inc/util.inc src/usr/local/www/diag_routes.php 3 files changed, 71 insertions(+), 10 deletions(-) diff --git a/src/etc/inc/syslog.inc b/src/etc/inc/syslog.inc index 1a9a83e4e37..2e5d0818023 100644 --- a/src/etc/inc/syslog.inc +++ b/src/etc/inc/syslog.inc
Patching file etc/inc/syslog.inc using Plan A...
Ignoring previously applied (or reversed) patch.
Hunk #1 ignored at 26.
Hunk #2 ignored at 864.
2 out of 2 hunks ignored while patching etc/inc/syslog.inc
Hmm... The next patch looks like a unified diff to me...
The text leading up to this was:|diff --git a/src/etc/inc/util.inc b/src/etc/inc/util.inc
|index 332b690b80e..83ad1dc6336 100644
|--- a/src/etc/inc/util.inc+++ b/src/etc/inc/util.inc Patching file etc/inc/util.inc using Plan A... Hunk #1 succeeded at 3779 with fuzz 1 (offset -2 lines). Hmm... The next patch looks like a unified diff to me... The text leading up to this was:
|diff --git a/src/usr/local/www/diag_routes.php b/src/usr/local/www/diag_routes.php
|index c0d059c6d79..409343046c2 100644
|--- a/src/usr/local/www/diag_routes.php+++ b/src/usr/local/www/diag_routes.php Patching file usr/local/www/diag_routes.php using Plan A... Ignoring previously applied (or reversed) patch. Hunk #1 ignored at 32. Hunk #2 ignored at 53. Hunk #3 ignored at 70. Hunk #4 ignored at 106. 4 out of 4 hunks ignored while patching usr/local/www/diag_routes.php done #3
/usr/bin/patch --directory=/ -t -p2 -i /var/patches/62174f8677d3e.patch --check --forward --ignore-whitespace
Hmm... Looks like a unified diff to me...
The text leading up to this was:|From 8cd3f92f2443a6f0e4b7964a9532f761f808a0c6 Mon Sep 17 00:00:00 2001
|From: jim-p
|Date: Tue, 17 Aug 2021 09:09:45 -0400
|Subject: [PATCH] Regex cleanup change. Fixes #12257
|
|Rather than attempting to cleanup group repetition, just discard theunwanted pattern. src/etc/inc/util.inc 1 file changed, 7 insertions(+), 11 deletions(-) diff --git a/src/etc/inc/util.inc b/src/etc/inc/util.inc index 8571399928c..f419e265d5b 100644 --- a/src/etc/inc/util.inc +++ b/src/etc/inc/util.inc
Patching file etc/inc/util.inc using Plan A...
No such line 3837 in input file, ignoring
Hunk #1 failed at 3838.
1 out of 1 hunks failed while patching etc/inc/util.inc
done#4
/usr/bin/patch --directory=/ -t -p2 -i /var/patches/62174f9b62b9c.patch --check --forward --ignore-whitespace
Hmm... Looks like a unified diff to me...
The text leading up to this was:|From cf757a8094762ede47861fc073eaba06355c6bfc Mon Sep 17 00:00:00 2001
|From: jim-p
|Date: Wed, 18 Aug 2021 16:11:11 -0400
|Subject: [PATCH] Regex cleanup should also kill {}. Fixes #12257
|
|It's not used often (and less in the GUI) and can be a source of
|problems with large numbers of repetitions even outside of groupedexpressions. src/etc/inc/util.inc 1 file changed, 3 insertions(+), 2 deletions(-) diff --git a/src/etc/inc/util.inc b/src/etc/inc/util.inc index f419e265d5b..2f63b7298e2 100644 --- a/src/etc/inc/util.inc +++ b/src/etc/inc/util.inc
Patching file etc/inc/util.inc using Plan A...
No such line 3843 in input file, ignoring
Ignoring previously applied (or reversed) patch.
Hunk #1 ignored at 3817.
1 out of 1 hunks ignored while patching etc/inc/util.inc
done -
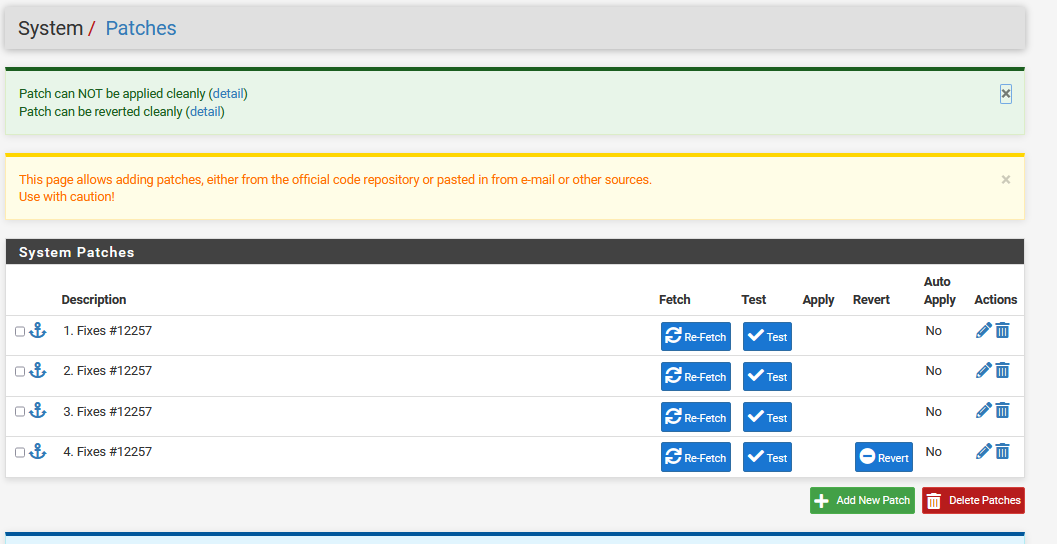
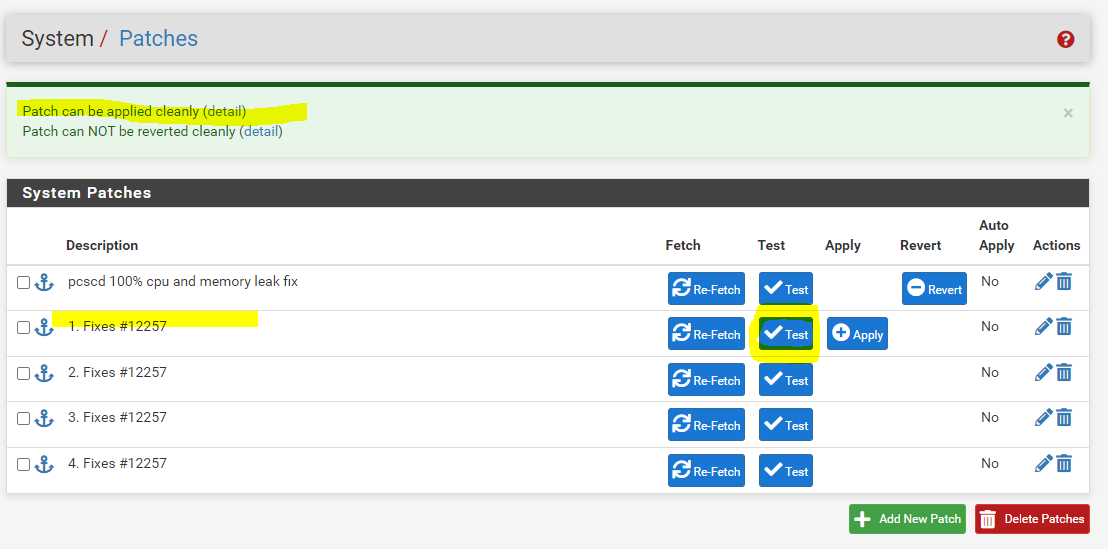
Can you please post a screenshot with a list all patches like the once I posted above, thanks.
example
-
-
That looks okay to me, you have successfully patched it.


-
-
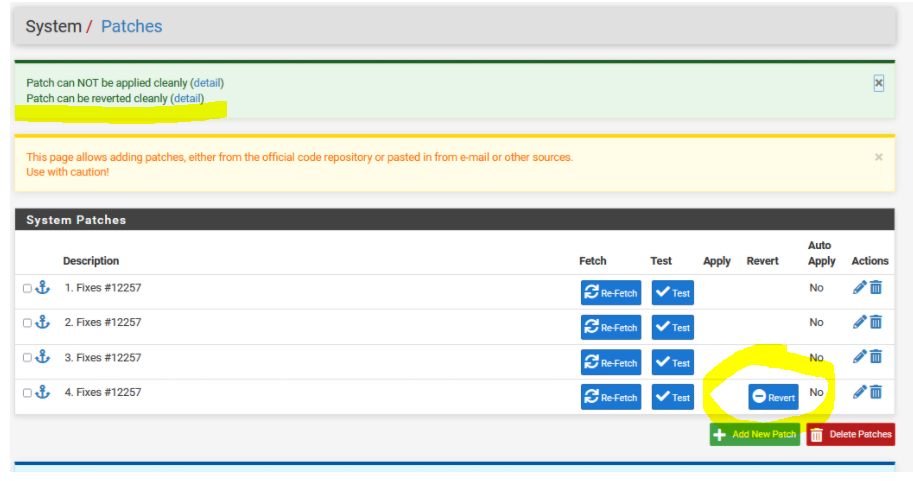
all good, you can't patch it anymore because it is already patched, you only can revert it from there.
-
@cool_corona said in Remote Code Execution in pfSense <= 2.5.2:
You cant do that since the 2.5.2 package repository doesnt exist anymore.
I just installed System_patches on a 2.5.2 machine
It was pointing at 2.5.2 deprecated (by me) , as soon as they released 2.6.0
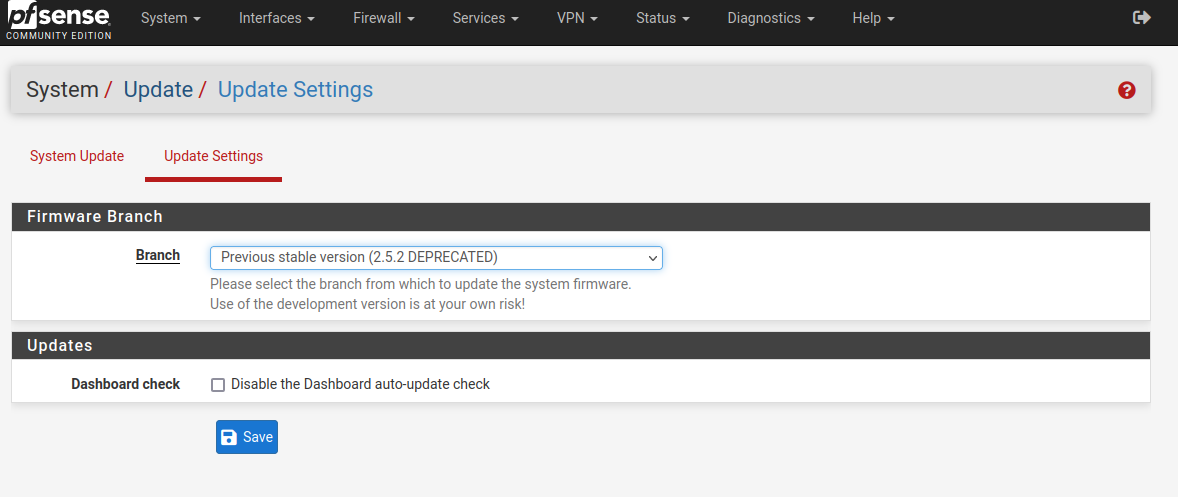
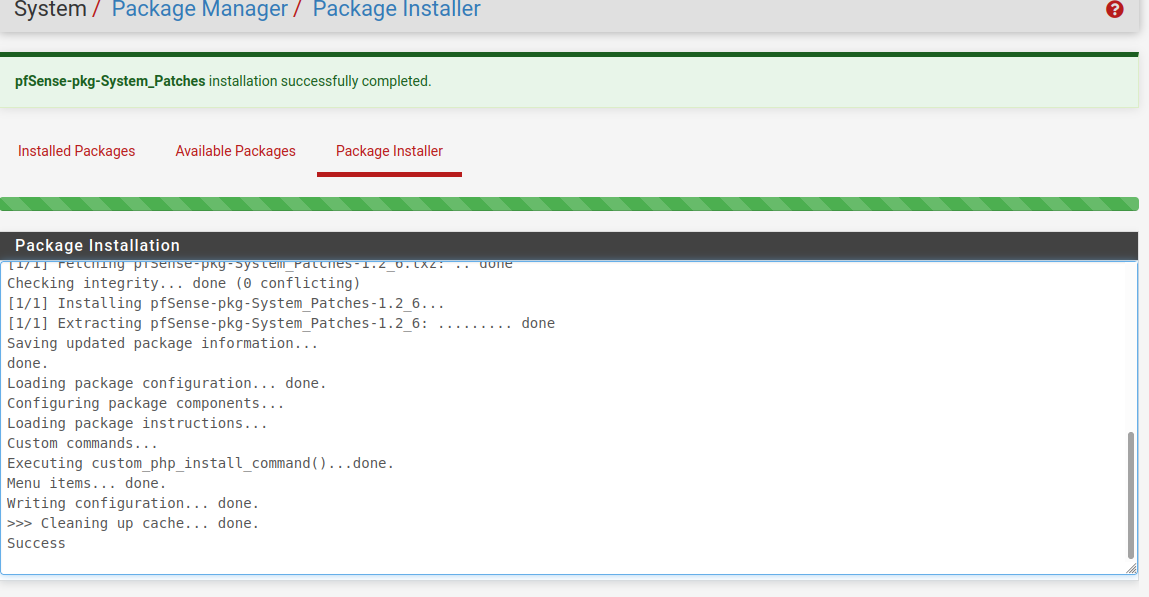
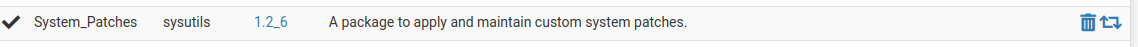
-
A few notes:
- As has been pointed out, you can (and should) install the package using the GUI by setting the update branch to the "Previous stable version" branch for 2.5.2 or 21.05.2. Do not do it at the CLI with a direct repo URL.
- The advisory exaggerates things a bit. There is nothing "pre-authentication" about this. An admin must already be logged in for it to happen, if it's triggered via CSRF or similar it must be in the same browser session where the admin is already logged in. tl;dr don't browse the web from the same session you admin your firewall.
- All of the relevant commits and so on are also published in advisories from Netgate at https://docs.netgate.com/advisories/index.html -- This one is pfSense-SA-22_02.webgui
- If you are concerned about this, you should also patch the others fixed in 22.01/2.6.0:
Each advisory has a list of relevant commit IDs.
-
- ...tl;dr don't browse the web from the same session you admin your firewall.
And also: run the browser for administering pfSense under a different OS account than the one you use for browsing, and add an OS firewall rule to prevent inadvertent general browsing from the pfSense browser.