Newbie port forwarding problem
-
First time trying to do this... forward a port to my internal Emby server.
I read the manual, and think I followed the instructions properly. On remote systems (testing via my phone's browser, not on my local wifi) the connection times out.
As I test it, I can see the connection attempt being blocked on my pfSense firewall log (default deny rule).
Here's my entry in the port forward table:
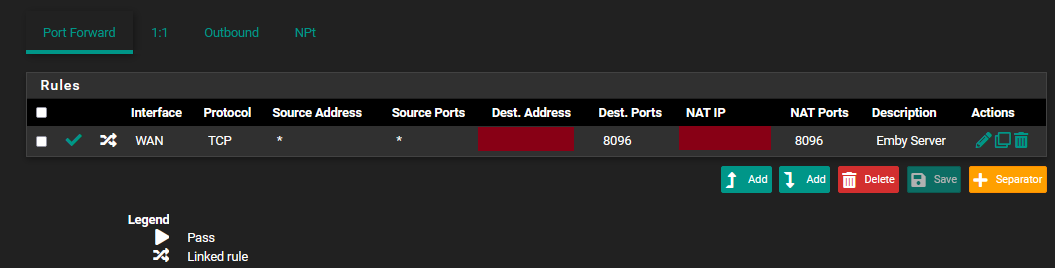
When on my internal network, I get to the server fine (using it's internal IP).
In the port forward setup, the Destination Address and Redirect Target IP address are the same (set to the external Emby server's address). Is this correct?
What am I missing? Thanks.
-
@nguser6947 if your being blocked by the default deny rule, then you didn't create your wan firewall rule. This would of been done for you automatic unless you told it not too.
Why are you hiding your dest address, this should just be wan address. And why are you hiding your rfc1918 address your nat IP? 192.168.x.x, 10.x.x.x, 172.16-31.x.x nobody can get to those other than if on their own network.. They are not accessible via the public internet.. So hiding them does nothing.. It akin to hiding that your carpet is red in your living room - because someone might be able to pick out your house from knowing that.
Post up your wan rules, and your full port forward
https://docs.netgate.com/pfsense/en/latest/troubleshooting/nat.html#port-forward-troubleshooting
-
@johnpoz Here's my wan rule:
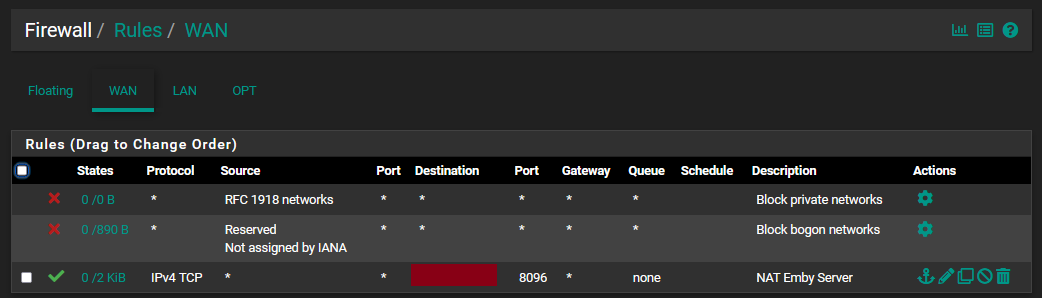
and the full port forward screen:
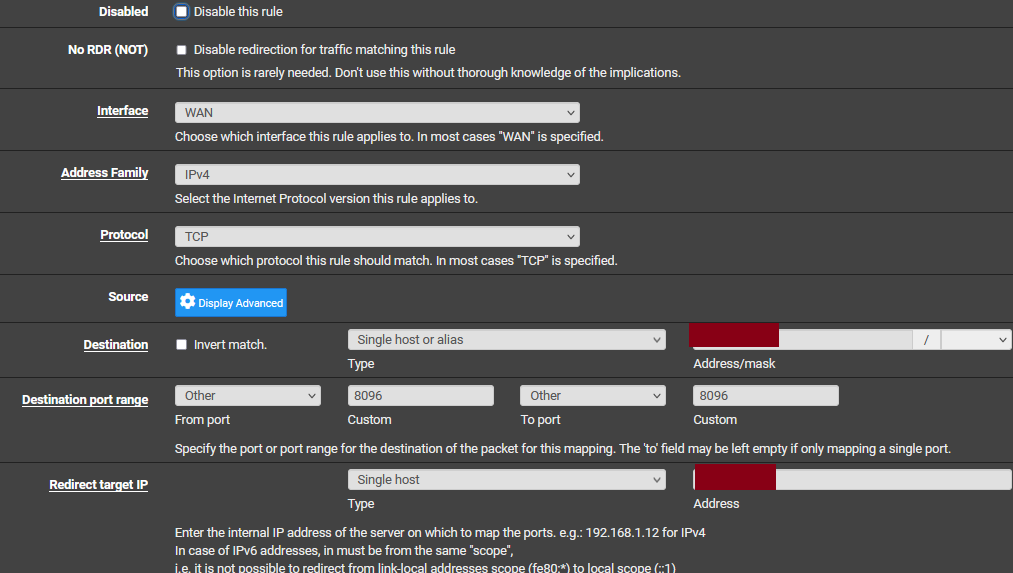
I've masked what Emby reports is my server's external IP. The brown boxes contain that external IP (both are the same values).
-
@nguser6947 said in Newbie port forwarding problem:
The brown boxes contain that external IP (both are the same values).
well that would never work!
That target IP should be your servers local IP.. 192.168.1.100 for example.. How would it work with some public IP?
example - here are forwards and wan rules for my plex, which is 192.168.9.10 on my local network..
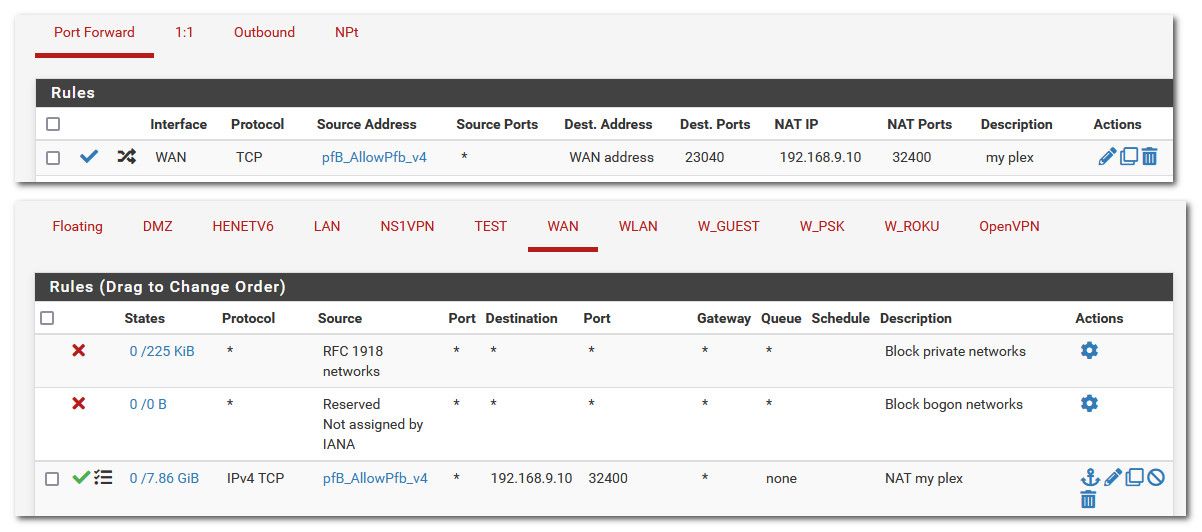
So you want to hit your server from the internet on port xyz... But your server is not on a public IP its on a rfc1918 address, 192.168.x.x as example.
So you hit your WAN Address (your public ip) on pfsense, its says oh you want to talk to port xyz.. I will send you to 192.168.1.100 on port xyz, or could be even a different port like in my setup..
How could it forward to some public IP? Which I assume is your wan IP.. So it would just forward to itself?
In my example traffic that hits my pfsense wan address (my public IP) on port 23040 gets sent to my plex server that is 192.168.9.10 on my network to port 32400 (the plex port)..
I use pfblocker alias (that contains US IPs, etc) as restriction... So if the source of the traffic hitting my wan IP on that port is from one of those IPs its allowed, if not say its a China IP or something than it would not be forwarded.
-
@johnpoz Ok. Yes, I have updated my configuration:
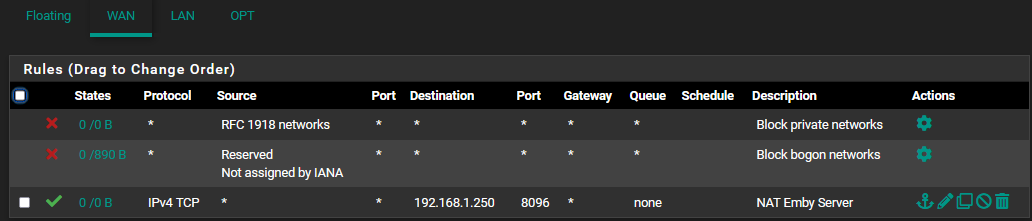
I've verified that the destination IP and port are correct and the device is online. Firewall log still indicates it is failing due to the default rule.
-
@nguser6947 Solved! I realized that I was mistakenly entering my local server's IP address in the Destination field which smacks head wouldn't work.
Cleared that, and now I have remote access.
Thanks for your help!
-
@nguser6947 said in Newbie port forwarding problem:
it is failing due to the default rule
You say this because you've looked at the firewall logs and you saw the incoming (WAN) traffic - with the correct (8096) port and correct "protocol TCP" being flagged as 'blocked' ?
I give you an example :
I have a Synology Diskstation in my LAN, it has IPv4 192.168.1.33 (RFC1918 of course).
I've created an alias for the device name "diskstation2", it resolves to 192.168.1.33.
I want to access my Diskstation using https://diskatation2.my-domain.tld:8080I created a NAT rule :
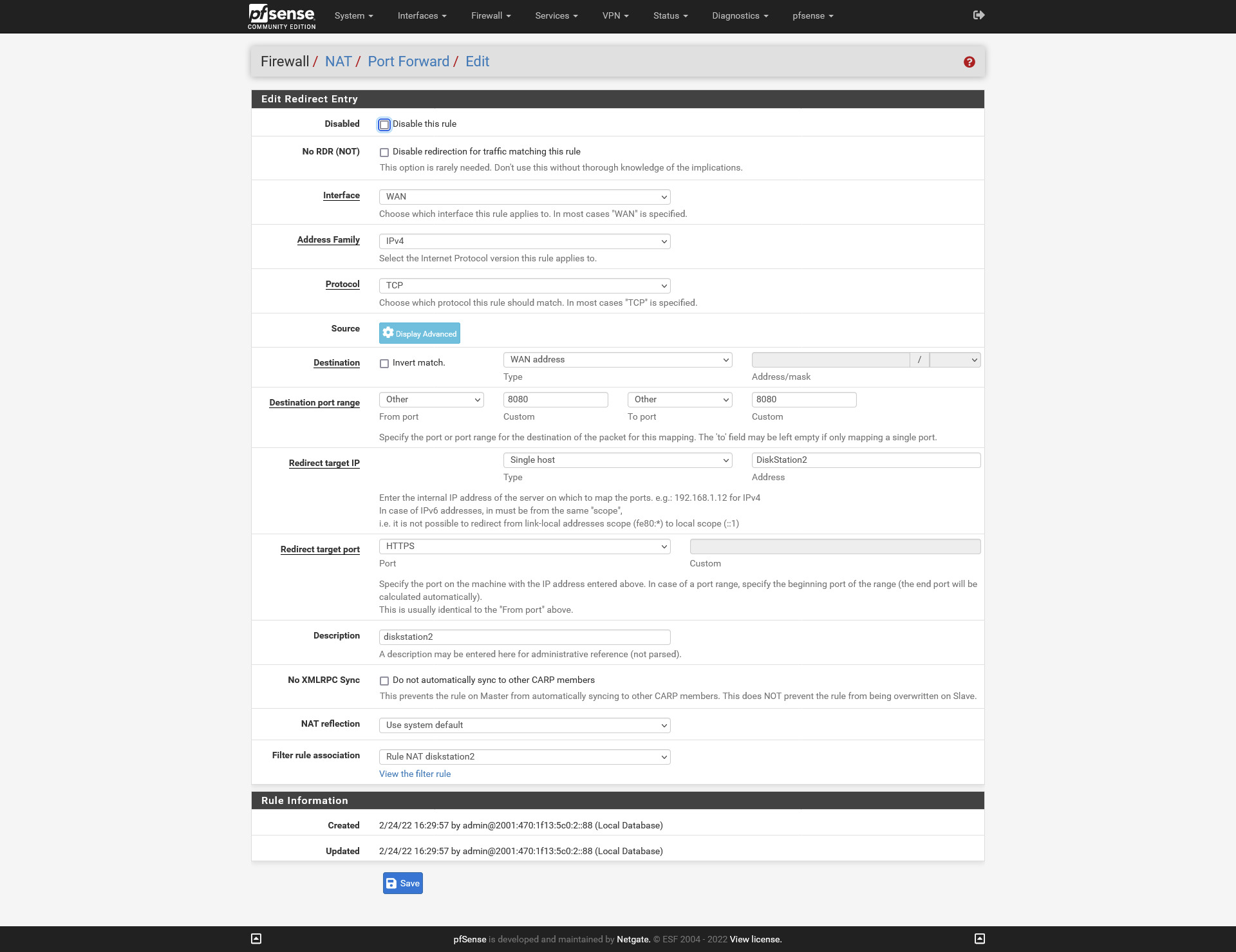
The 'destination' is the firewall macro WAN Address, as my WAN is is always part of WAN address. The day my WAN IP changes, my rule still works.
I want to reach my diskskation on port 8080, so "Destination port range" is set to 8080.
The traffic that comes in and matches WAN Address & port 8080 should go to :
Redirect target IP : I entered the Alias "diskstation2", I could also enter "192.168.1.30".
And the destination port : my diskstation web server listens on "443", it's using TLS.I Save.
I have a NAT rule :
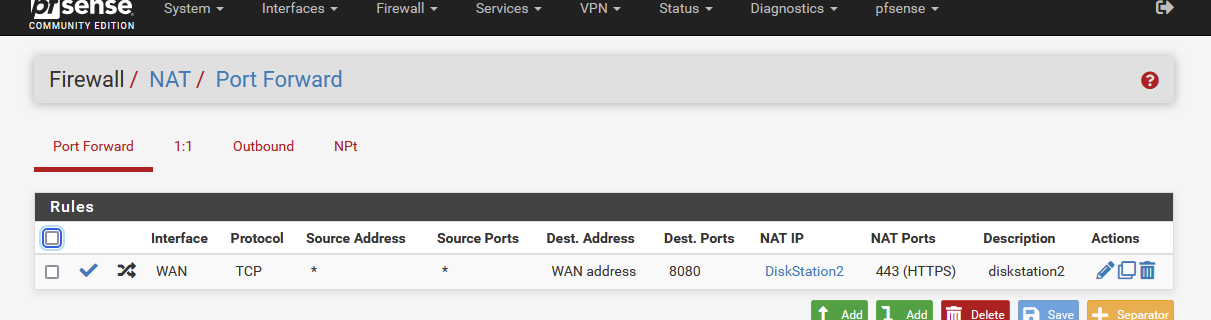
I checked the auto created WAN firewall rule :
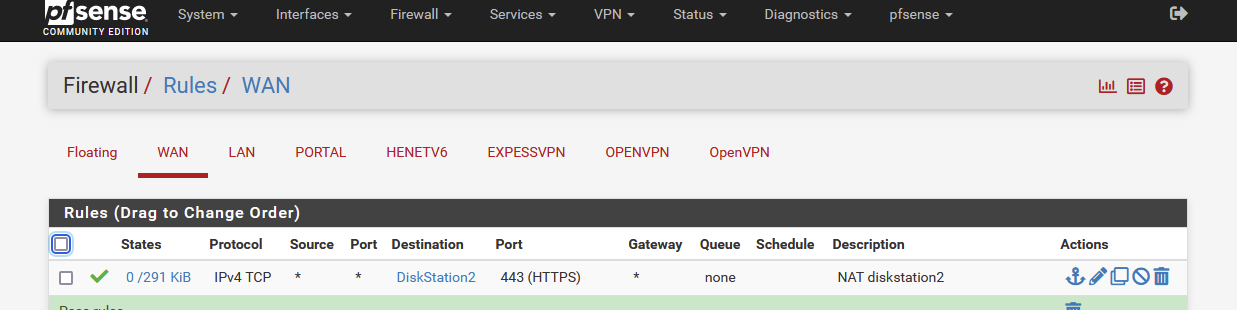
I tested with my phone ( with Wifi shut down !! ) , and entered :
https://diskatation2.my-domain.tld:8080I saw the main web page of the web server of my diskstation2.
I also saw :
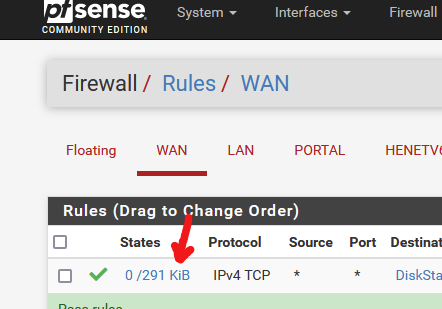
which means that the WAN rule was used / matches incoming traffic. That was me testing the access with my phone..
If needed, abuse the pfSense documentation, like Port Forwards. Port forwarding or port NATting or, more correct, PATting, hasn't changed since 1995. Every Home/business router/firewall needs the same inputs. pfSEnse seems to be diffrent but check for yourself : you have to enter 4 things, and your good. The rest of the option are 'special cases'. The day you need them, you'll know they are there.
Also : I copied all the images without the need of masking something. The correct use of aliases and firewall macros make rules maintenance easy : It becomes a "set it and forget it" which means I had to look up the pfSense NAT doc, as I tend to forget things. I do not use NAT rules any more, only a VPN access which is just a firewall rule, no NAT). Exposing internal devices in a company network is a big no no (imho). This said : this is also valid for you : now your 192.168.1.250 becomes part of your network security. Keep that in mind.