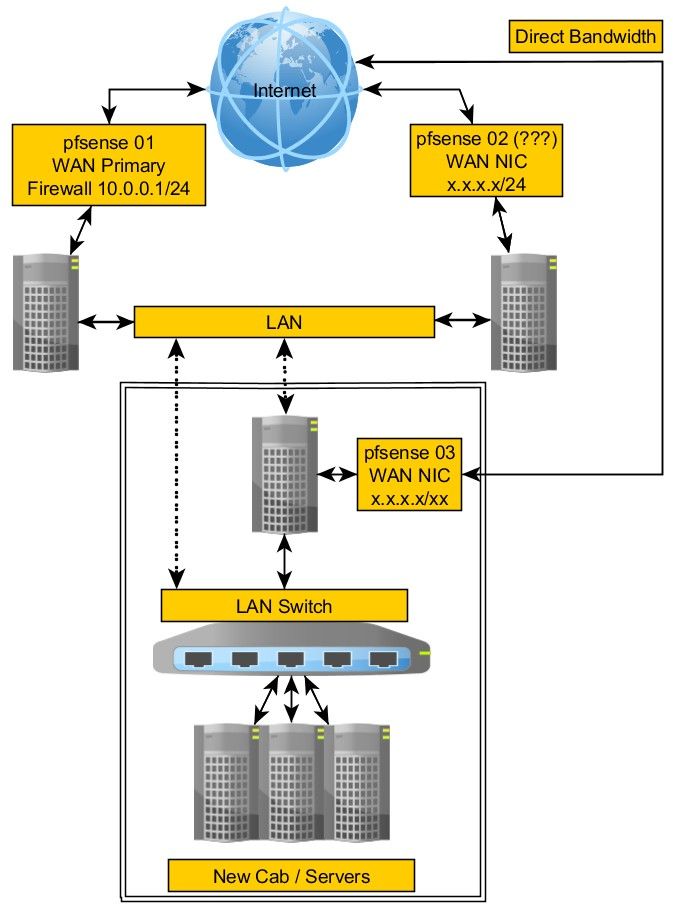
Using pfsense with multiple WANs
-
So far, so good. I've got a windows-7 vm running on the same hardware. I think it's time to try this transport link.
-
Can anyone offer a url/link/article on how I can go about testing this transport method? I don't want to mess up what I've done to date.
-
You have a diagram of exactly what it is you're planning to do?
-
@stephenw10 Yes, the very first message.
In that image, I show how it's going to be connected at the DC but right now, it's still at my home. I am hoping to get this into the DC over the weekend if I can figure out this transport.
-
I'm sorry I can only hold so many threads at the front of my mind at once.

I'm unsure now exactly what you have configured and what you are going to configure.
Reading back it looks like you added the DCLAN interface to the pf3 device setup on your home network and are now able to access it via port forwards?Steve
-
@stephenw10 LOL, no problem, I don't expect anyone to remember this long thread :).
Yes, my LAN is 192.168.1.1/24 so I gave DCLAN on pfsense-03 the IP of 192.168.1.3/32 so I could reach it.
On my network, I also have a 10.0.0.1/24 and the pfsense-03 has its own 10.0.0.24. I have a laptop connected directly to the LAN Switch.All this hardware needs to go to the DC this weekend so I'm at the point where I'd like to understand how to set up this transport. Because there will be other pfsense firewalls sending traffic to pfsense-03, the idea was to use tiny transport networks so I could add more as needed.
-
What I would consider a transport subnet would be something without other devices on it that you can route traffic across. You can't really do that here because you need the NAT to allow both firewalls to use 10.0.0.0/24.
What you're doing is simply port forwarding twice in order to reach the servers behind the second firewall. That can be across a separate subnet. So, yes, you should set that up and make sure you can reach the servers from the outside.
I mentioned before that for that to work you will relying on reply-to tagging since pf3 has a separate default WAN connection. So that definitely needs to be verified.Steve
-
Ok, I think the best way to work on this will be after the gear is installed at the DC tomorrow.
I'll give myself remote access via the new WAN connection and that will give me access to this new network and the old one. At that point, it'll be easier because it'll be the real setup instead of trying to simulate it from here.Hope it all goes well and I'll be in touch when I'm back on Monday.
Thanks so much for sticking with me on this. It's been a great learning experience. I'm always floored at what I can do with pfsense and recommend it to many companies that ask me about routing/firewalls. -
Alright, got everything into the data center and it's all working.
The new rack has its own pfsense fw now called 'pfsense 01' since it must become the main firewall. The WAN connection is working and I can see some traffic on the DCLAN interface or (OPT1).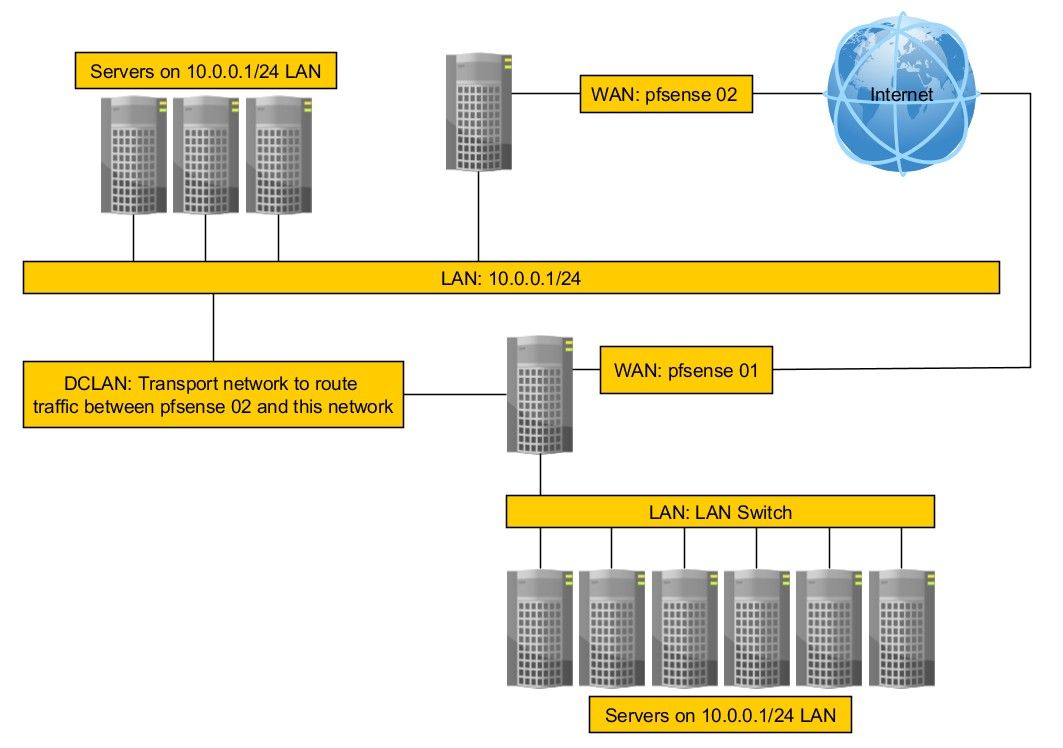
Hopefully, this updated image better explains. Also, I wonder if I should start a new question to benefit someone else who might be interested in learning about transport networks since this will be lost in this long thread.
-
Good to hear. Let us know if you see any issues moving stuff to the new location.
-
(I changed the pfsense numbers to make it simpler and more updated)
It was done over the weekend. The image reflects how things are right now and what I need to do next which is this transport :).
As a refresher, I need to move some of the 10.0.0.x hosts from the pfsense 02 over to a new network behind pfsense 01.
I also need to keep pfsense 02 online, with its own Internet connection, sending/receiving traffic from hosts on the LAN side of pfsense 01.
In addition, there are other pfsense devices in the mix which I need to forward their traffic to pfsense 01. However, I've not shown those to try and keep the question simpler. I figure once I have a way of doing this with what I show, then it's only a matter of duplicating with new transport networks.
-
Ok, so pfSense01 cannot have an IP address on it's interface in the DCLAN in the 10.0.0.0/24 subnet because it's already using that as it's LAN.
So you need to create a new subnet there that it can use and assign the pfSense01 DCLAN interface an IP from it. Then you need to add a VIP to pfSense02 in that subnet on it's DCLAN interface so it can route traffic to pf01.
Then you can simply change the port forwards of pf02 to point to pf01 in the new subnet as you move them across.What won't work is servers in the existing DCLAN will be unable to connect to servers behind pf01. The source IP will conflict with the pf01 LAN.
The reply-to tags on traffic coming into the DCLAN interface on pf01 will allow replies to go back out of the gateway defined on that interface. However that means if you have multiple routers forwarding traffic to pf01 on the interface only the one defined as the gateway will get replies as expected.
If you have multiple pfSense boxes doing that you might need to use tunneling of some sort to avoid asymmetric routing.Steve
-
This post is deleted! -
This post is deleted! -
I had a couple of replies but I deleted them to prevent confusion so I can continue from your last comment.
What won't work is servers in the existing DCLAN will be unable to >connect to servers behind pf01. The source IP will conflict with the >pf01 LAN.
I think the answer to importing vms will be to do it over the WAN. This way, I can simply open firewall ports on pfsense 02 that allow me to reach the vmware hosts I need to import from. Once imported, I can then change the forwarding on pfsense 02.
So you need to create a new subnet there that it can use and assign >the pfSense01 DCLAN interface an IP from it. Then you need to add >a VIP to pfSense02 in that subnet on it's DCLAN interface so it can >route traffic to pf01.
Alright, we're at the point of this transport then :).
So pf01 will become the main firewall and this is where things get interesting. I have to read and re-read what you say above because it's over my head at the moment.
If I understand where I'm at, I'm just wanting to create a network inside my own network using private IPs. The pf01 would know about a whole class C for example and pf02 would be assigned one IP or a /30 subnet from that class C.
Sorry, brain twisting for me since this is probably fairly simple but typing it all out is much more complex sounding maybe.
-
It just needs to be any currently unused subnet. So, no, it can't be a /30 from inside the existing DCLAN /24 because that will still conflict with the pf01 LAN which is using that same subnet.
So it could be 10.100.0.0/24 for example. With pf01 using 10.100.0.10/24 is it's DCLAN IP and pf02 using 10.100.0.1/24 as a VIP on the DCLAN.Steve
-
Yes, I understood that and was thinking of using the 192.168.x.x or 172.16.x.x network but your suggestion works too.
You said create a network like 10.100.0.0/24 on pf01 DCLAN, use 10.100.0.10/24 on the interface and a VIP on pf02 of 10.100.0.1/24.
Trying to understand this, I'm not really creating a network where there is typically a gateway? In other words, pf01 is not going to become the gateway for pf02, pf03, etc. Instead, the pf01 DCLAN is simply in the same network space as the other pfxx are?
Hope I'm explaining this right.
-
The VIP on pf02 will be the gateway for pf01 on the DCLAN interface.
pf01 mist treat the DCLAN interface like a second WAN. It needs to be able to send replies to forwarded traffic back via pf02.Steve
-
This post is deleted! -
The VIP on pf02 will be the gateway for pf01 on the DCLAN interface.
pf01 mist treat the DCLAN interface like a second WAN. It needs to be >able to send replies to forwarded traffic back via pf02.Oh gee, I'm seeing all this backwards. I see the pf01 as being the gateway for external pfxx once this is set up.
Once I understand this, it's going to be a powerful thing.