Netgate XG-1541 VPN Configuration
-
To configure our remote access VPN our company provided us a public IP address that is mapped (NAT?) to an address on our local network. Our 1541 is configured with this as its network address, with the Ethernet cable plugged into the WAN port. Nothing is plugged into the LAN port since it's already on the network with the servers that clients need to remotely access. For example, say our network is 192.168.30.0/24. the pfSense VPN device has IP address 192.168.30.252, mapped to public address 100.100.100.25. Client config files connect to 100.100.100.25, authenticate via OpenLDAP, then access their desired server(s), also on the 192.168.30.0/24 network. Is this the best way to configure the VPN - with only the WAN connected?
-
That's fine, you should have no problems doing that.
By configuring it like that you are relying on pfSense to outbound NAT the traffic from VPN clients to it's WAN address. That's needed so that the resources they are connected to have a route back. However that does mean that local resources will see all connections as coming from the pfSense WAN IP and not the actual VPN client IPs. That might be better for logging.
A better setup in my opinion would be to have the 1541 connected to the upstream router on a separate transport subnet with routes in place to allow traffic without NAT. However that may not be practical.
Steve
-
@stephenw10 Thank you Steve, that's good to know. The only problem I have with this configuration is that I have to manually change the "remote" line of client configuration files automatically generated by the pfSense, since the WAN interface IP is the local one and not the public one. That is not a big deal at all though. Just good to know that I didn't configure it totally wrong :)
-
You can change that in the exporter before creating the file. You save that as the default if you use that every time:
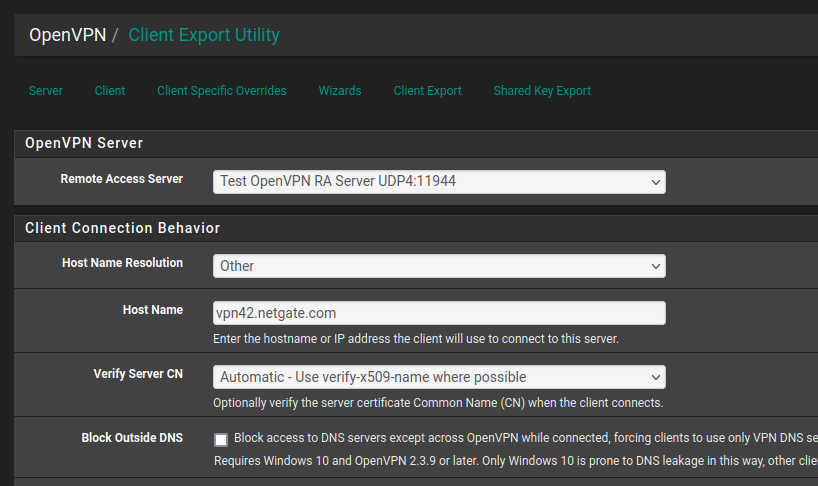
Steve
-
@stephenw10 Nice! Thank you again!