Issues with VPN and dual NIC
-
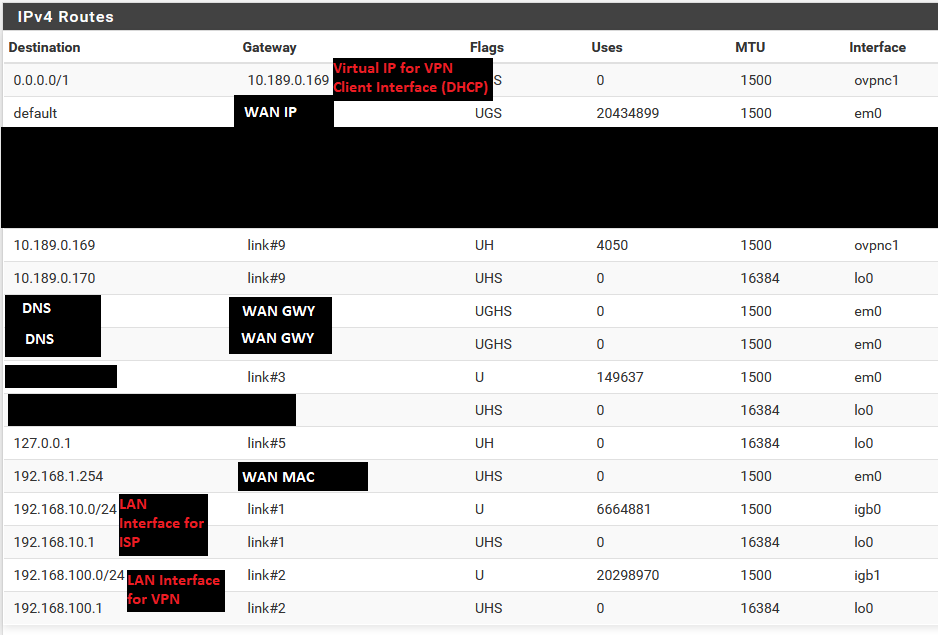
I am running bare metal pfsense, and the box is configured with one WAN interface and 2 LAN, each on their own /24 subnet as pictured here:
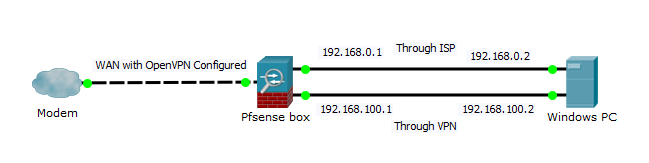
I am connected physically from one pc using two NICs to each eth port.
I want only one interface to use the VPN client, and I have all the policy rules in place how I believe they should be. However, it only works when I add a static route to my VPN interface. That'd be fine I guess, and it all seems hunky dory, except that when I use just the ISP interface on my computer (other unplugged), some websites report my public IP (which is what I expect) but others report the VPN IP address.
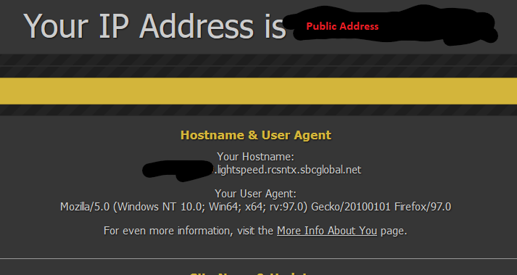
What's going on? And is there a better way than static routing like I'm having to do, because that seems to be the culprit.
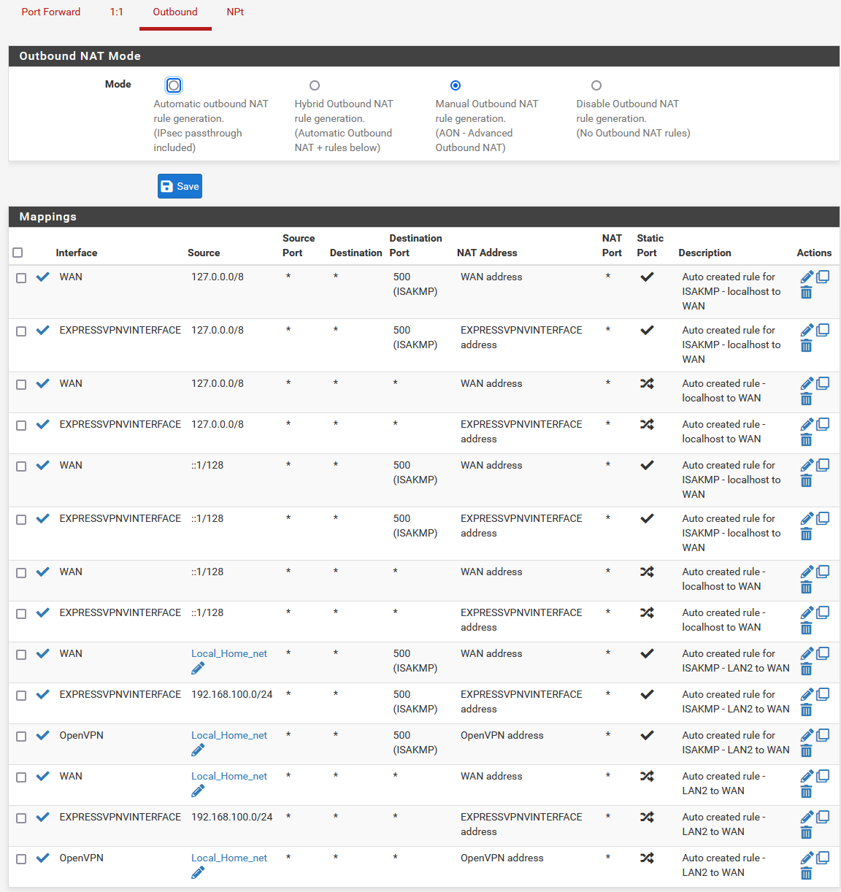
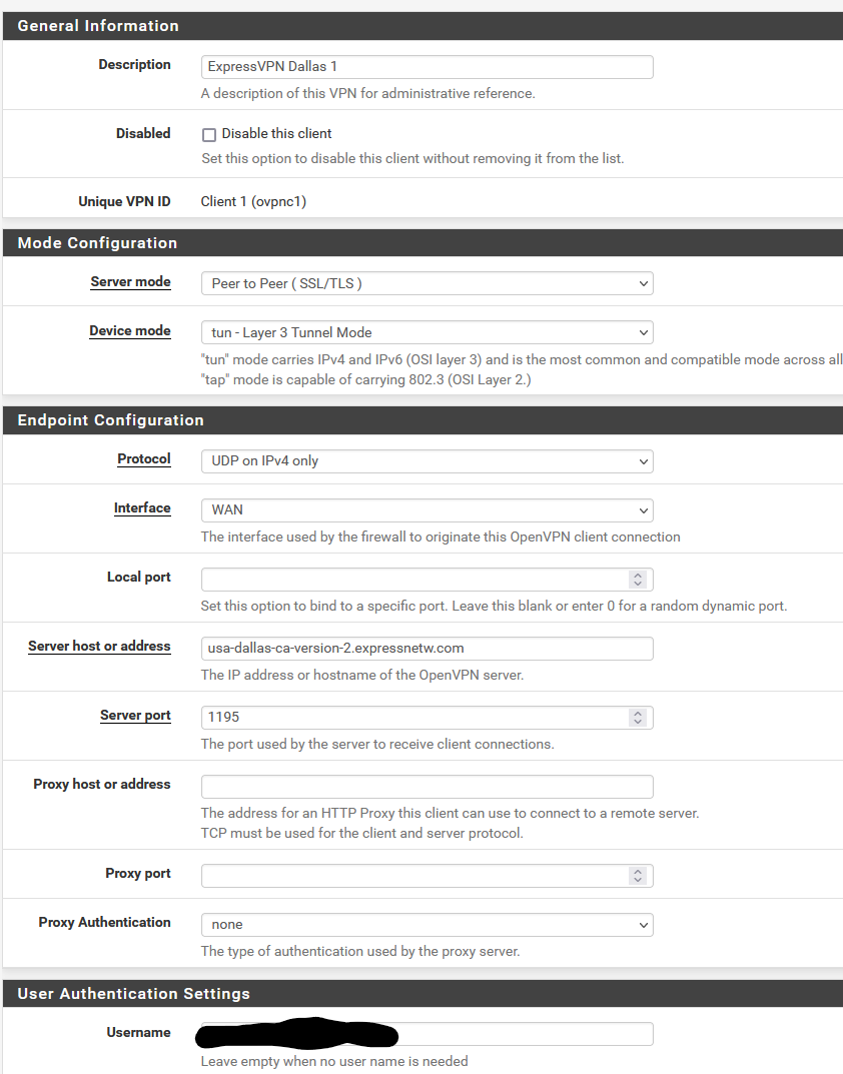
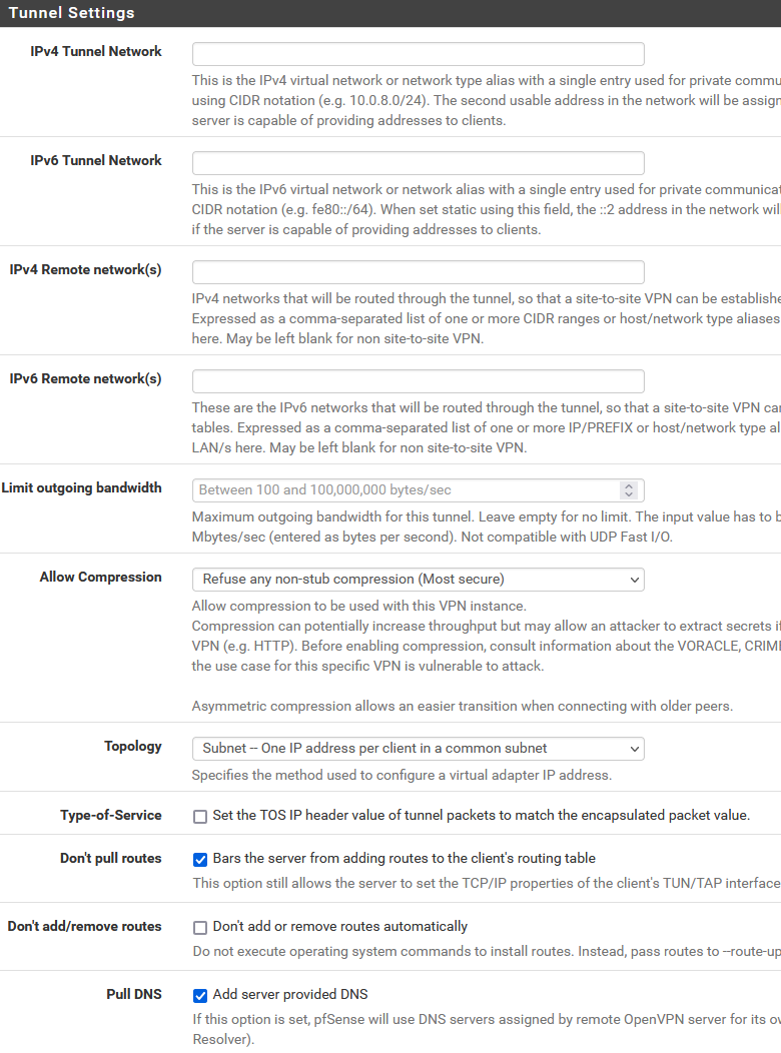
Here are all my settings.
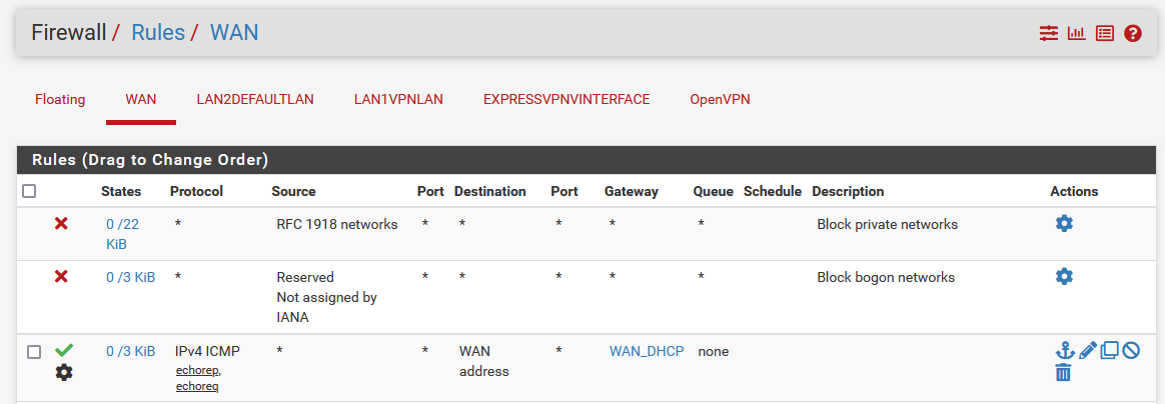
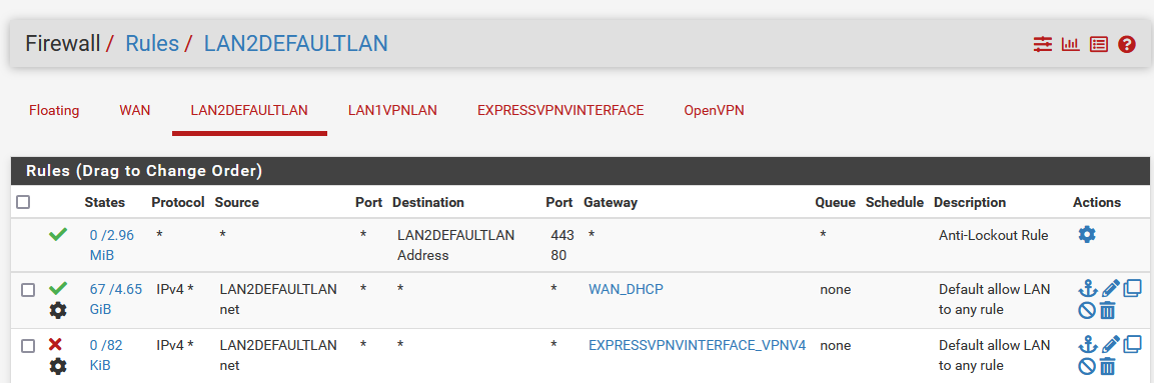
NOTE: If I put the block rule above the allow rule on LAN2DEFAULTLAN, all traffic stops on that interface.
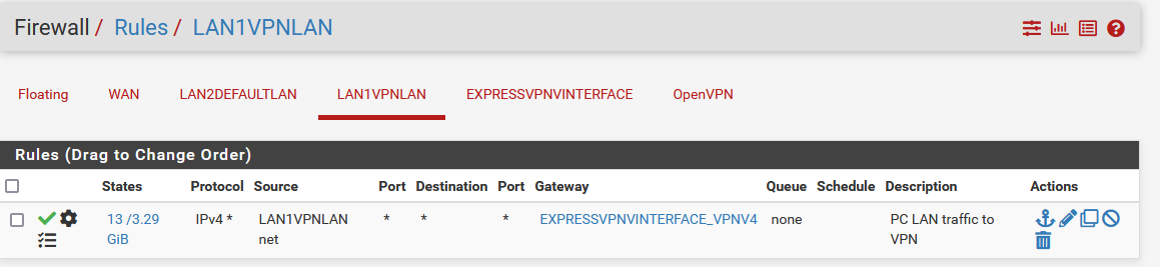
Thanks in advance
-
@rsherga You need to create a gateway based on the OpenVPN interface and then add a LAN rule that directs all traffic from your specific NIC's IP address to the OpenVPN gateway.
-
@kom thanks for the reply.. Take a look at the firewall rule for LAN1VPNLAN. I am already doing as you suggest. "Expressvpninterface_v4" is the gateway for the vpn.
-
@rsherga I don't know how I missed that.
How does the client PC know which NIC to send traffic out? Is it possible to bind an application to a specific network interface?
-
@kom man you rock for working with me here. I appreciate the input even if we can't end up figuring it out.
To answer your question, I just manually set the metric for each interface in windows so the one to ISP is at I think 2, while the one to VPN is at 35.
I have only one application I send over VPN interface, and it lets me bind it so it doesn't work unless I have it plugged in.
Also, the issue of seeing either of the public IPs using different websites still occurs if I have the interface to VPN LAN unplugged. And it happens on my laptop when I also connect under the ISP- routed subnet, and that doesn't even have another interface.
And this is all at once, so I can open 4 tabs at the same time and only certain ones report the public ISP IP address, and others the VPN. Each one is consistently the case though. So the same sites will always report the VPN IP in this situation. I am assuming maybe it is how they determine the information that differs. Like one uses ICMP, and another will use my DNS or something random. I know nothing really about how that could work aside from basic ICMP.
So anyway, it's gotta be an issue on the pfsense side, right?
-
@rsherga I've never worked with a multihomed client so I don't have a lot to add. I don't see anything that jumps out. Like you, I"m not sure why external sites sometimes see your VPN IP when you have that interface disabled.
-
@kom Hey I just wanted to follow up and let you know for posterity that I discovered the solution.
Simply setting each subnet/interface's allowed gateway on the firewall wasn't enough. The traffic MUST BE TAGGED in a floating rule.So basically here is a summary for anyone who might be searching for this:
Goal: Route different traffic to specific gateways, only allowing in/out on specific interfaces or subnets. I have one WAN interface and two LAN interfaces: one of which should ONLY be to VPN (can be single gateway or gateway group), and the other should ONLY be through ISP.
- Add firewall allow rules on each interface.
-
LAN to ISP only
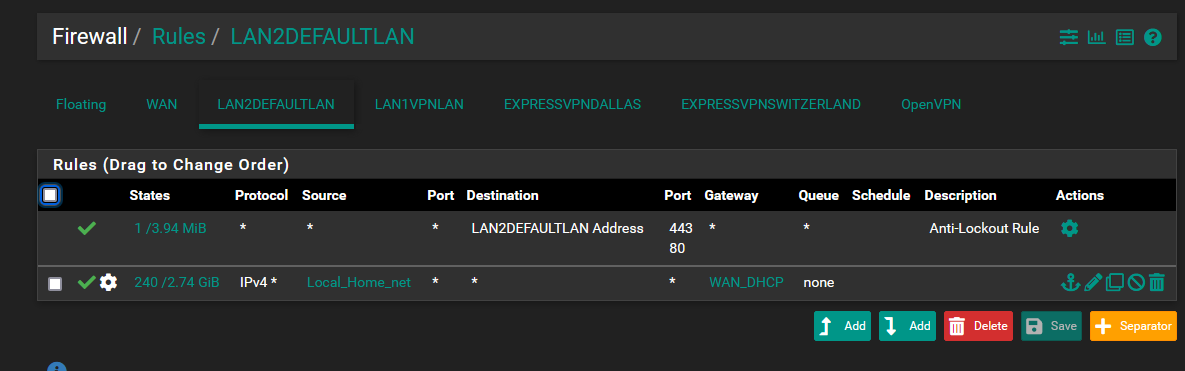
-
LAN to VPN gateways only
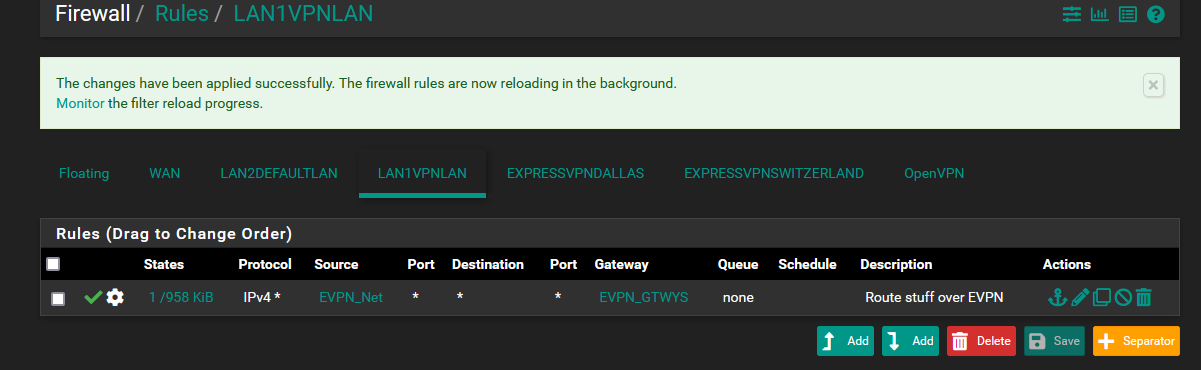
- In each rule, tag the traffic with a name you choose:
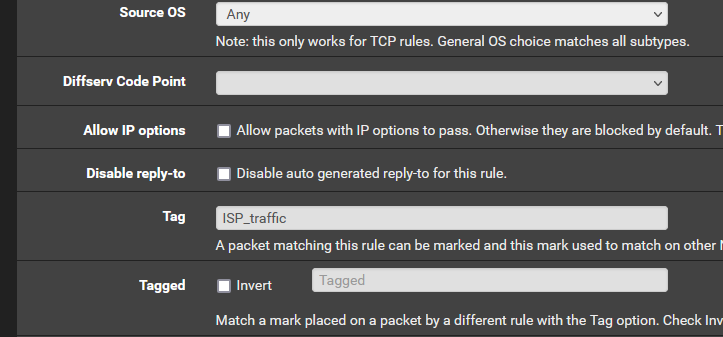
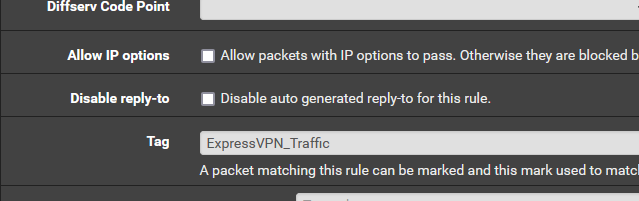
- Add two floating BLOCK rules.
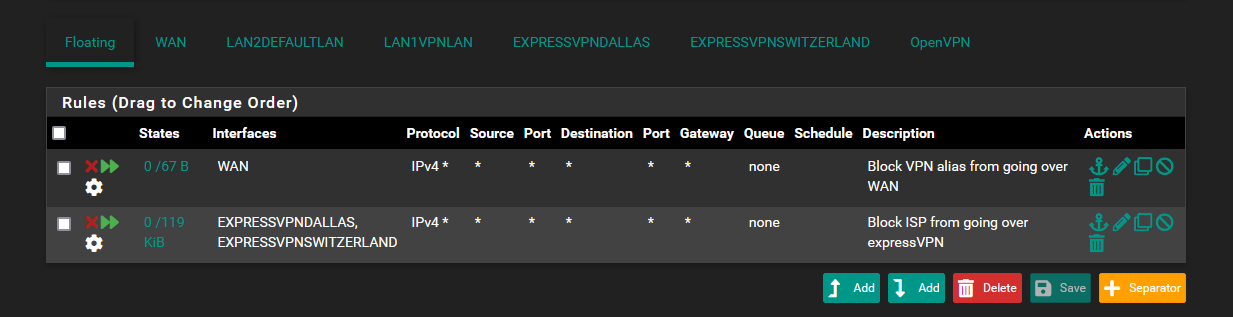
When you set the block rules for each inbound interface (WAN and VPN), set the opposite tag in the "tagged" field.
This will refuse any packets that have matching tags.This is what finally stopped any detection of incorrect traffic on either gateway.
Thanks for your help though.