TCP:FA, TCP:FPA blocked is it Asymetric Routing?
-
Hi All,
I'm setting up a lab network behind pfsense 2.5.2 and am getting lots of log messages that seem to be... at least from what I've gathered by reading the forums... related to asymmetric routing. But, I'm new at this and am not quite sure.
Here's a diagram of my network:
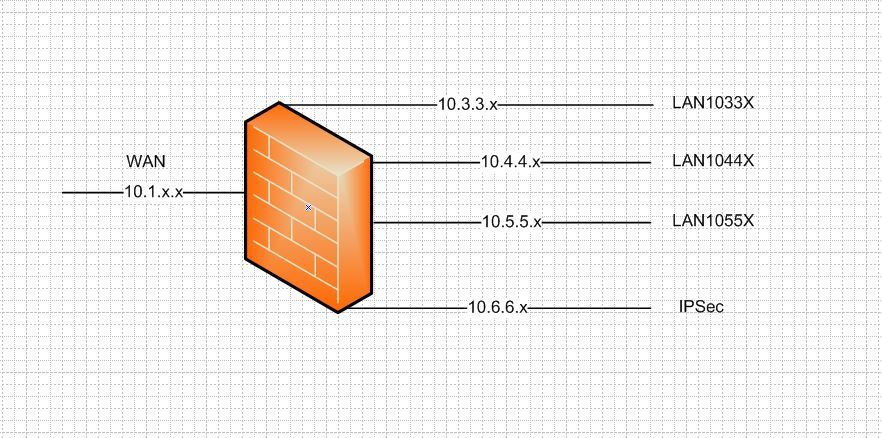
Routing between all of the segments works as I would expect. The only route I have defined is the default gateway on the WAN interface pointing out to my main firewall to the internet.
The log messages are from hosts on the 10.4.4.x, 10.5.5.x and 10.6.6.x subnets trying to reach hosts on the 10.3.3.x network.
The hosts on these segments simply have the corresponding firewall interface as their default route (ie. 10.5.5.1, 10.6.6.1, etc).
This doesn't seem like it should be anything special, but the logs show lots of valid passed traffic , with invalid entries thrown into the mix, but the source/destination/protocol/port are all the same and should work. I actually can't really see any failures when moving about the lab, which is another reason I'm suspecting a state problem somewhere.
My limited understanding of asymmetric routing is when packets take one path in one direction and another path in the other direction, but in this limited lab where the only path between them is pfsense, I'm not sure how I could be in such a situation.
The log entries look like this:
Mar 7 20:01:09 LAN1044X from client442 to server170 (1646116536) 10.4.4.2:51920 10.3.3.170:23400 UDP Mar 7 20:00:05 LAN1044X from client442 to server170 (1646116536) 10.4.4.2:40056 10.3.3.170:23400 TCP:S Mar 7 20:00:05 LAN1044X from client442 to server170 (1646116536) 10.4.4.2:44924 10.3.3.170:23400 UDP Mar 7 19:59:44 LAN1044X Default deny rule IPv4 (1000000103) 10.4.4.2:39874 10.3.3.170:23400 TCP:FPA Mar 7 19:59:16 LAN1044X Default deny rule IPv4 (1000000103) 10.4.4.2:39874 10.3.3.170:23400 TCP:FPA Mar 7 19:59:03 LAN1044X Default deny rule IPv4 (1000000103) 10.4.4.2:39874 10.3.3.170:23400 TCP:FPA Mar 7 19:58:56 LAN1044X Default deny rule IPv4 (1000000103) 10.4.4.2:39874 10.3.3.170:23400 TCP:FPA Mar 7 19:58:54 LAN1044X from client442 to server170 (1646116536) 10.4.4.2:40054 10.3.3.170:23400 TCP:S Mar 7 19:58:52 LAN1044X Default deny rule IPv4 (1000000103) 10.4.4.2:39874 10.3.3.170:23400 TCP:FPA Mar 7 19:58:51 LAN1044X Default deny rule IPv4 (1000000103) 10.4.4.2:39874 10.3.3.170:23400 TCP:FPA Mar 7 19:58:50 LAN1044X Default deny rule IPv4 (1000000103) 10.4.4.2:39874 10.3.3.170:23400 TCP:FPA Mar 7 19:58:49 LAN1044X Default deny rule IPv4 (1000000103) 10.4.4.2:39874 10.3.3.170:23400 TCP:FPA Mar 7 19:58:49 LAN1044X Default deny rule IPv4 (1000000103) 10.4.4.2:39874 10.3.3.170:23400 TCP:FPA Mar 7 19:58:49 LAN1044X Default deny rule IPv4 (1000000103) 10.4.4.2:39874 10.3.3.170:23400 TCP:FPA Mar 7 19:58:49 LAN1044X Default deny rule IPv4 (1000000103) 10.4.4.2:39874 10.3.3.170:23400 TCP:PA Mar 7 19:58:33 LAN1044X from client442 to server170 (1646116536) 10.4.4.2:40052 10.3.3.170:23400 TCP:S Mar 7 19:58:33 LAN1044X from client442 to server170 (1646116536) 10.4.4.2:36647 10.3.3.170:23400 UDP Mar 7 19:57:17 LAN1044X from client442 to server170 (1646116536) 10.4.4.2:40050 10.3.3.170:23400 TCP:SThe rule that applies is:
IPv4 TCP/UDP 10.4.4.2 * 10.3.3.170 23400 * none from client442 to server170Any help deciphering this would be much appreciated.
Thanks to you all in advance!
-
I see those "deny's" when ie. my laptop has been in sleep for a period.
My guess is that the laptop ie. has a tcp connection to my e-mail server , goes to sleep , and then wakes up and try to resume (continue) the "old" tcp connection.
But the firewall state has "timed out" , making the "old tcp" connection invalid.
And the firewall "barfs" loudly ....The laptop eventually just makes a new (valid) tcp connection.
I have no asymmetric routing possibilities in my internal pfSense lan connections. Well as long as i don't use WiFi and cabled network at the same time on the laptop.

/Bingo
-
Thanks for the reply. I would expect the stale states from hosts that went to sleep, etc., but in my case, the hosts are all 24x7.
It just seems odd to generate so many "deny" logs... they just add noise to the value of the logs.
Is there a way to determine exactly what is happening? ie. I'm guessing it's state problem, but how do I know if I'm right?
Thanks again!
-
@msmcknight said in TCP:FA, TCP:FPA blocked is it Asymetric Routing?:
but how do I know if I'm right?
Are you states resetting - I think they are set to do that on loss of wan out of the box, etc.
-
How can I tell if they are resetting? They don't have timestamps to compare to from one sample to another.
There has been no loss of WAN in this lab. Is the "loss-of'wan-reset" an option somewhere in the admin gui?
Thanks!
-
This is an Android TV Box (24/7 on time). That the wife uses in the summerhouse kitchen , connected to a 23" HDMI TouchScreen ... A "Giant Tablet" for recipes.
It loves to babble "Home to Google" , and is sometimes slower than the state timeout (or just silent). I have no worries ...
Except it's an old Android version .. Would love to update , but i have been bitten by "Stock boxes" not having the "touch driver" that recognize the Monitors USB touch interface. And wo. touch-if the Wife is not happy.
Well i confined it to the Phone Vlan , that is super restricted in the access to other vlans.
Would have loved to replace it with a Linux Box , but Linux & Touch .... sucks a lot.
/Bingo
-
@msmcknight said in TCP:FA, TCP:FPA blocked is it Asymetric Routing?:
How can I tell if they are resetting?
you should see an entry in the log.. Do you see any log entries for wan issues about response time for your monitor, action being taken, etc. Do you have them set to reset on wan issue?
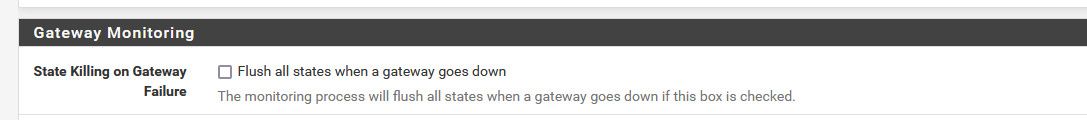
-
I don't have "State Killing" turned on. It looks like the default is "off" and I've never messed with it. I also don't see any log messages related to gateway loss.
One interesting thing I just noticed is that the blocked packets happen "on-the-clock"...
They are happening exactly at the top of the hour. Sometimes it's every hour, sometimes it's every two hours, but in every case it's at the top of the hour.
That seems a bit programmatic to me. Is there a setting somewhere that tells the firewall to do something every 60 minutes with respect to states?
-
@msmcknight said in TCP:FA, TCP:FPA blocked is it Asymetric Routing?:
every 60 minutes with respect to states?
not unless you have created a schedule to do that.
https://docs.netgate.com/pfsense/en/latest/firewall/time-based-rules.html#time-based-rules
By default, states are cleared for active connections permitted by a scheduled rule when the schedule expires. This shuts down access for anyone allowed by the rule while it was active. To allow these connections to remain open, check Do not kill connections when schedule expires under System > Advanced on the Miscellaneous tab.
-
No, I've not done anything like that. This is a fresh install with minimal setup.
I'm guessing that it has to do with states since the logs showing the blocked attempts seem to match those of a stale state, but happen like clock work. For example:
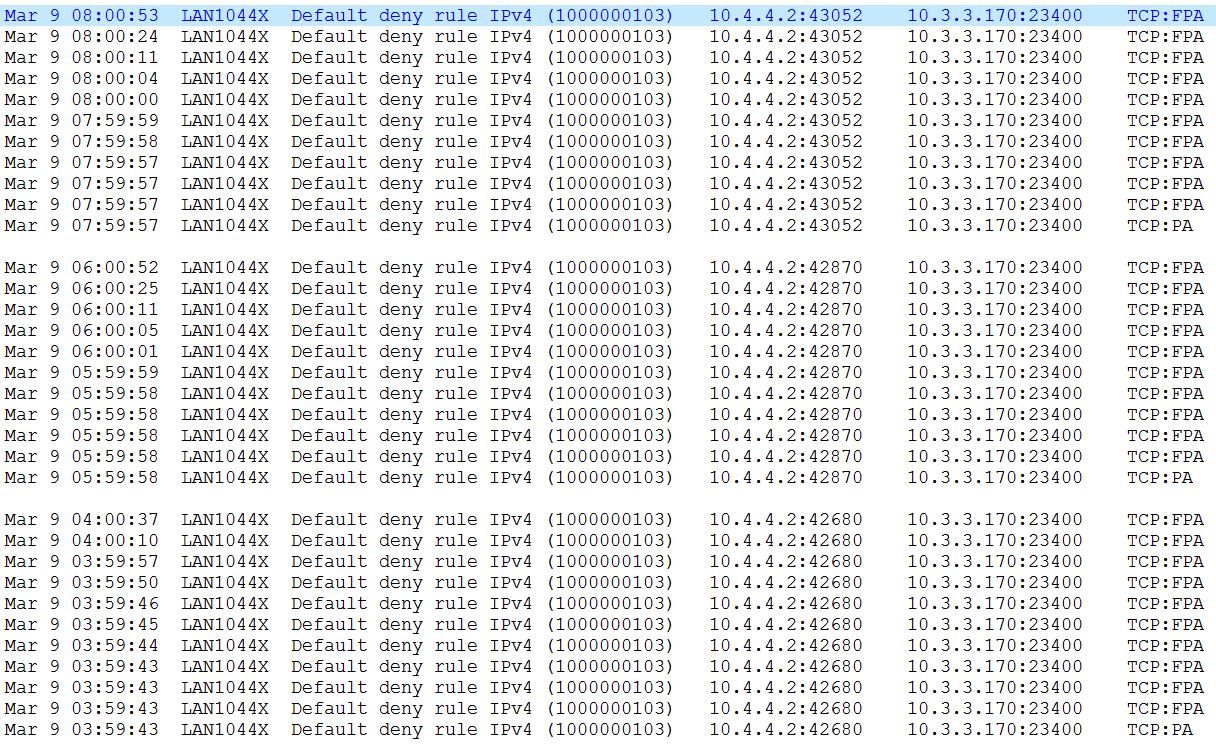
(Apologizes for the picture. The forum kept marking my log entries as spam and wouldn't let me post this reply with them)
Again, I'm only guessing these are state-related given the other messages in the forums showing similar logs and complaints. I wouldn't be so worried about them if they weren't cluttering up the logs with so much noise.
Thank you
-
Friendly bump here... anyone have any idea as to what would lead to the odd on-the-hour occurrence of these log entries?
Thank you