WireGuard site to site tutorial
-
I know there are many tutorials already. This tutorial is based on this very good video tutorial
But, it took me a lot of time to get a working configuration, so I want to share my experience and also will be glad to get community feedback if I got something wrongThe WireGuard configured as the following
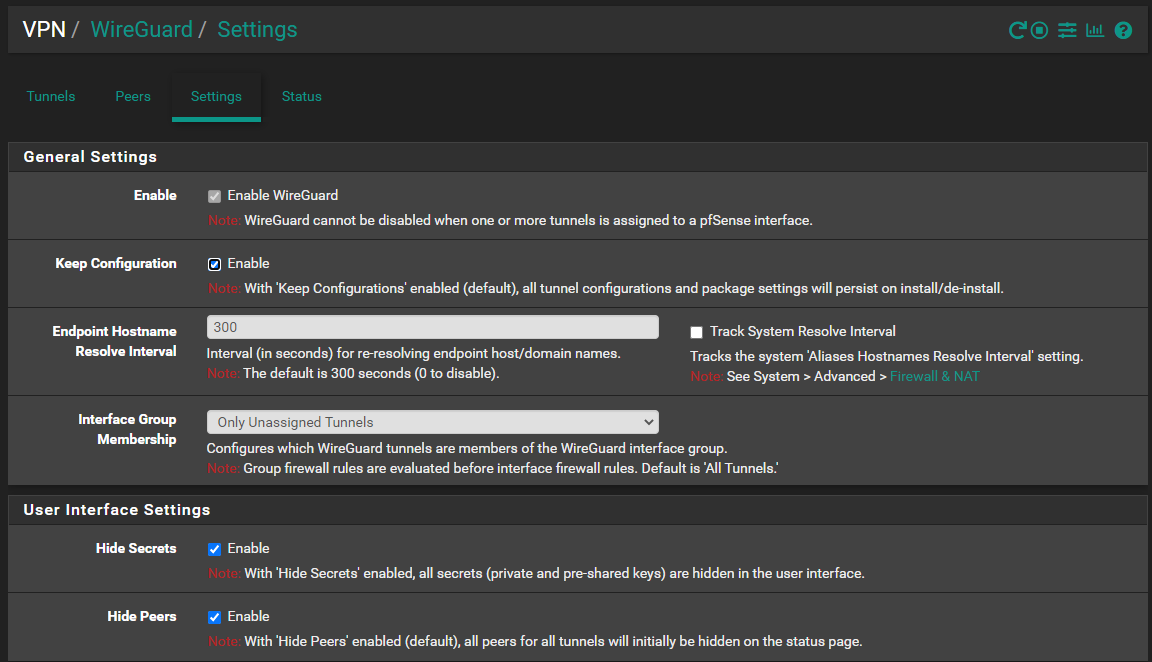
The tunnel network will be 10.0.20.0
Step 1 - Create the tunnel
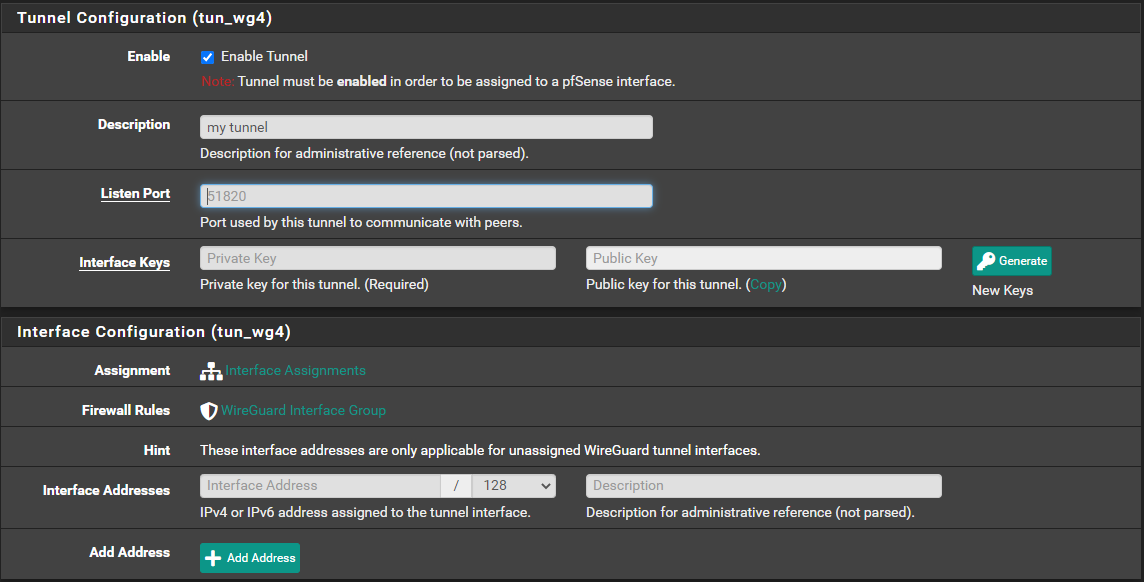
- Press "Generate" button to generate keys
- Leave interface address empty
- "Listen port" - any port but should be same for both ends
Step 2 - Add interface
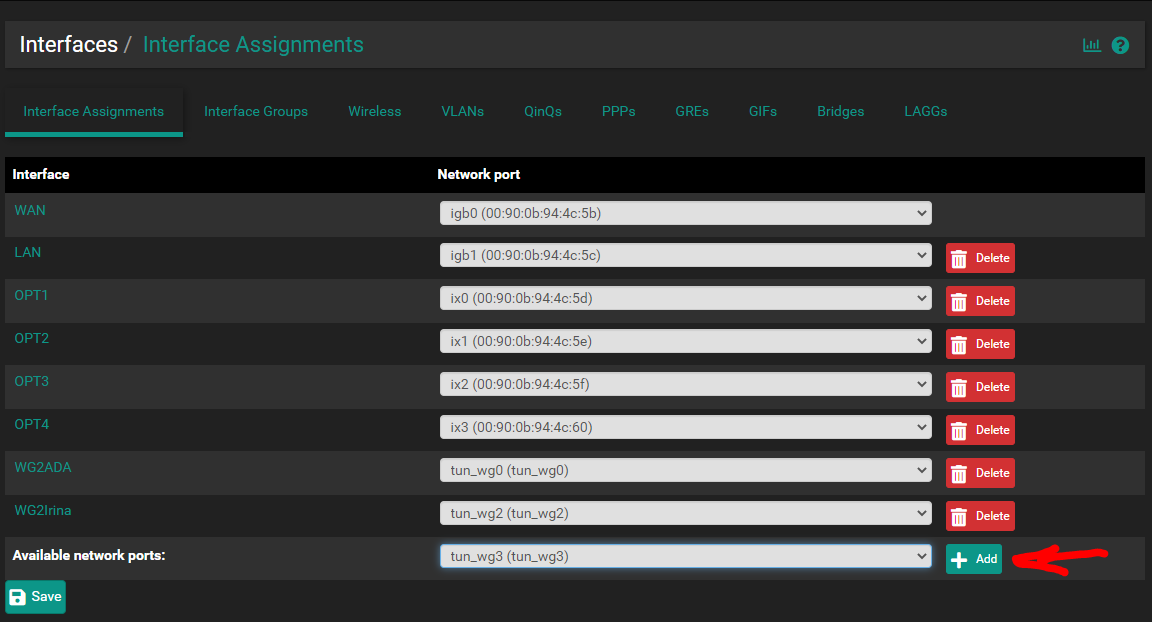
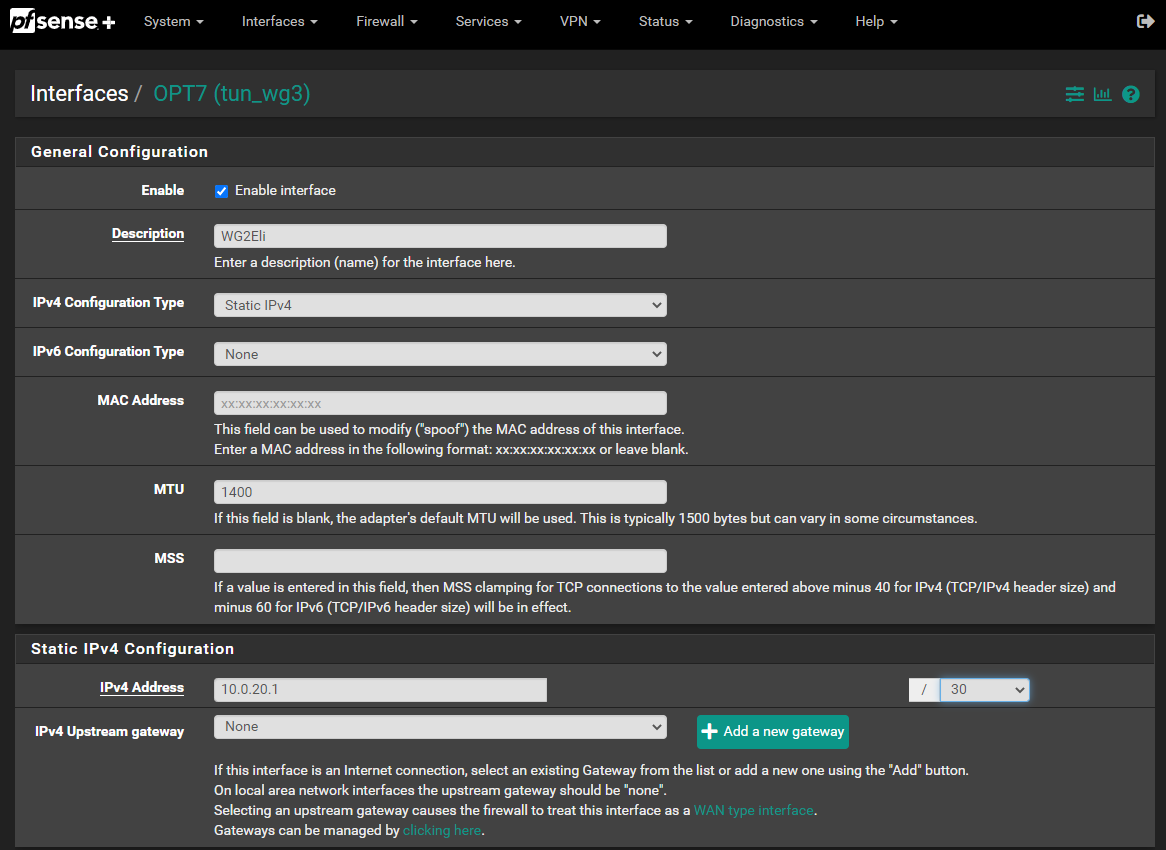
- The "IPv4 address" is what will be your side IP address for the tunnel network
- MTU 1400 for PPPoE connections (just approximation)
Step 3 - Add firewall rule for the created interface
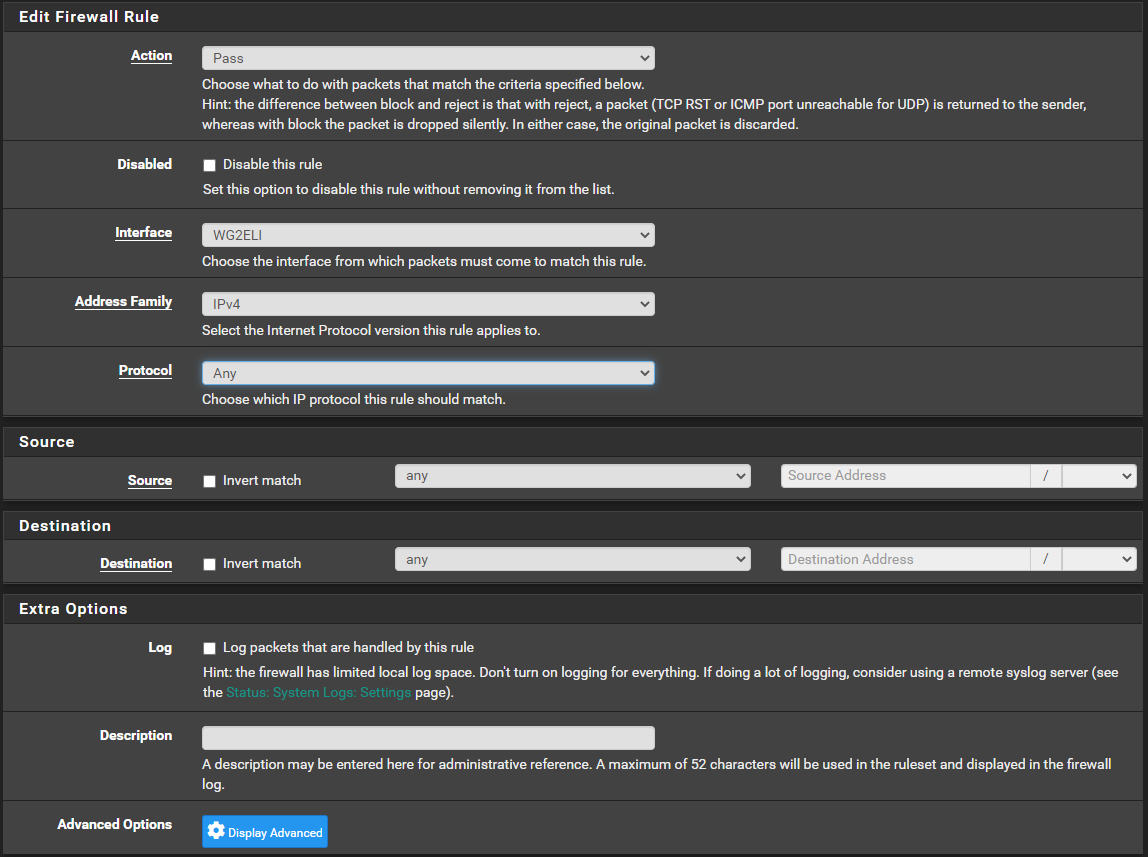
"Any Any" for the beginning. So will not complicate initial setupStep 4 - Add getaway
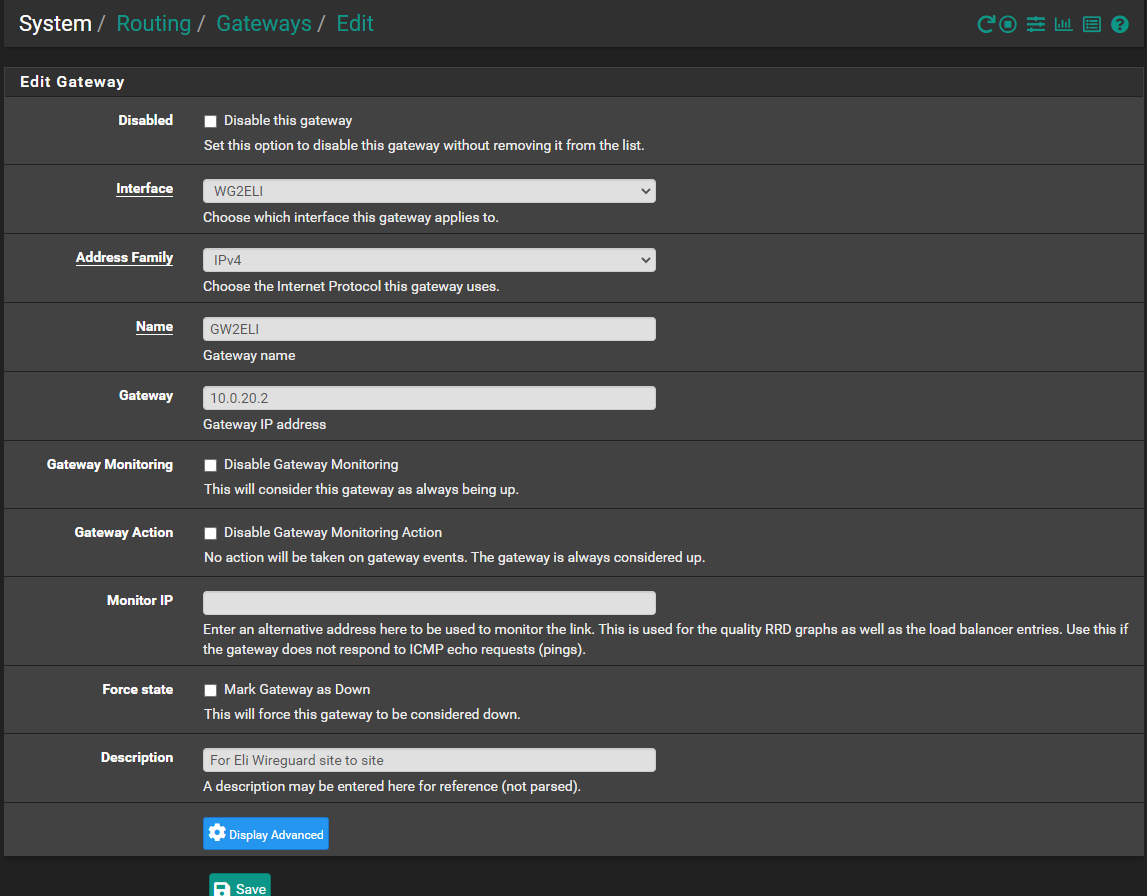
- The "Gateway" IP is the is other's side IP (inside tunnel network)
Step 5 - Add static route
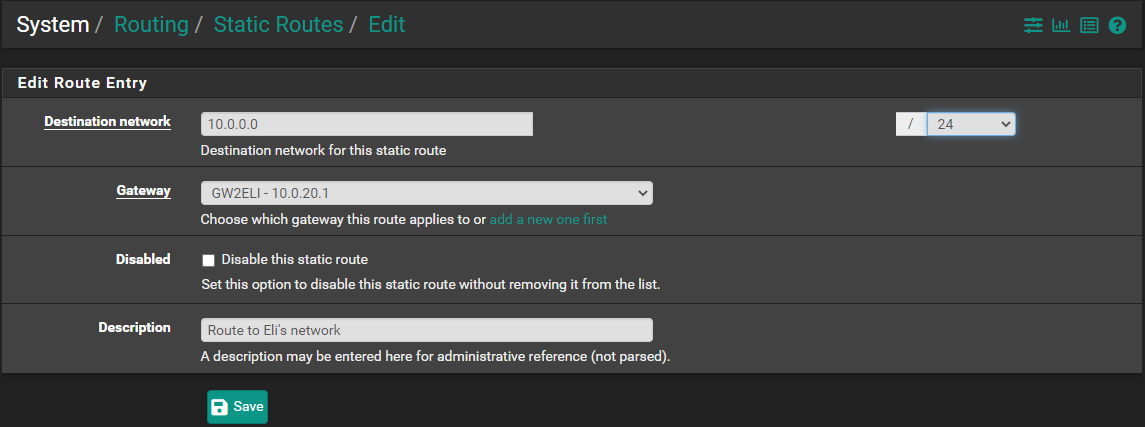
- "Destination network" is other's side network
Step 6 - Add firewall WAN rule
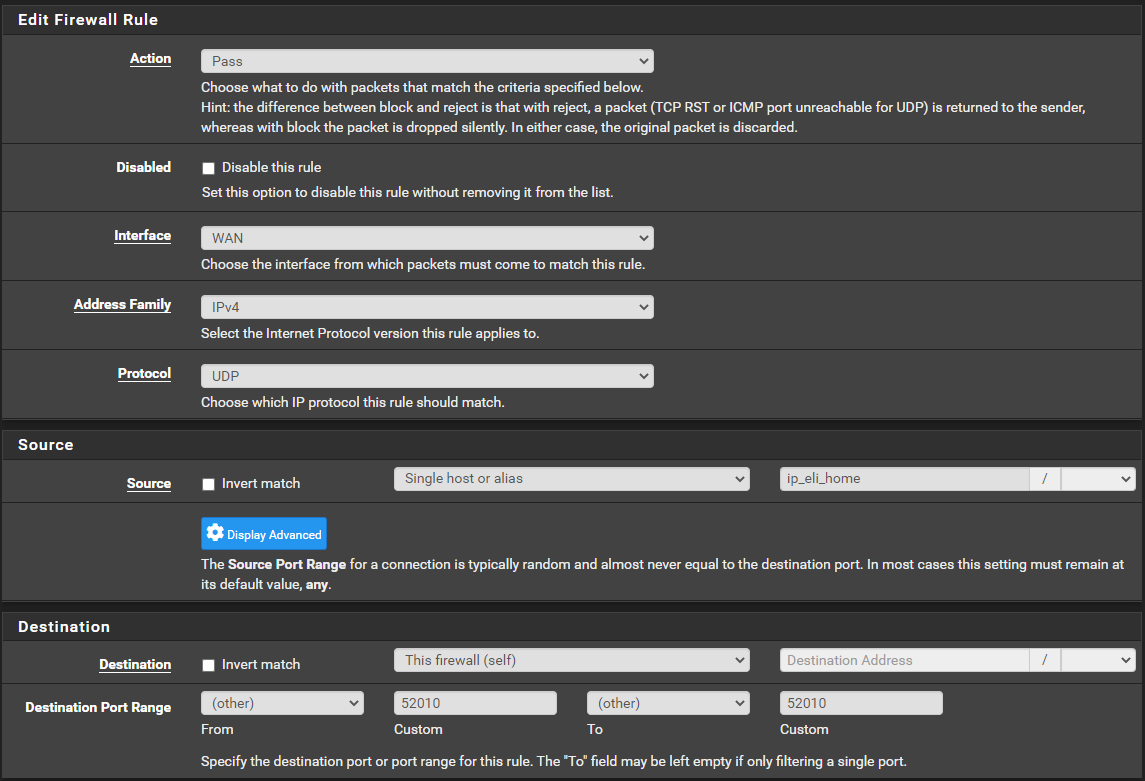
Step 7 - Add tunel peer
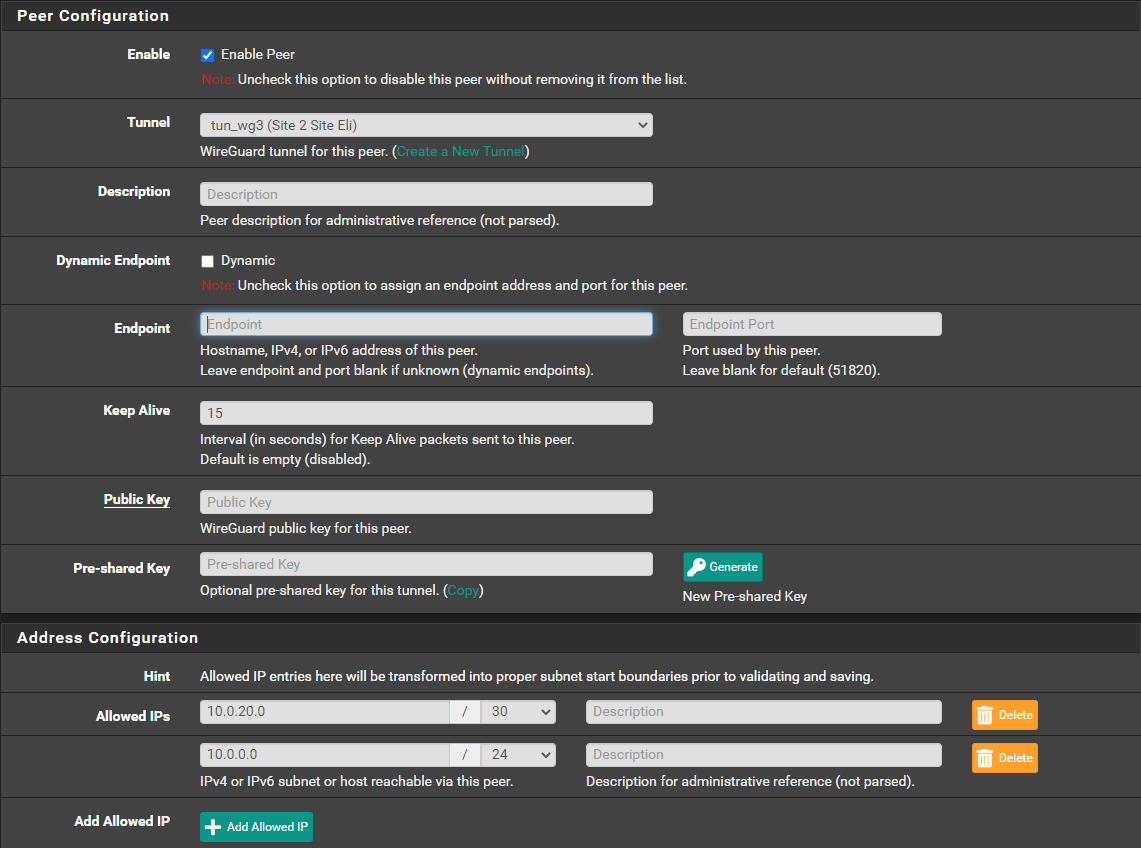
- Public key is the public key from the other side
- Both other's side network and tunnel network should be added to "Allowed IPs"
- "Endpoint" is IP or hostname of the other side
The other side is configured exactly the same way. The only difference is interface IP and gateway II should be swapped
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.