Random one way communication from LAN to DMZ issues
-
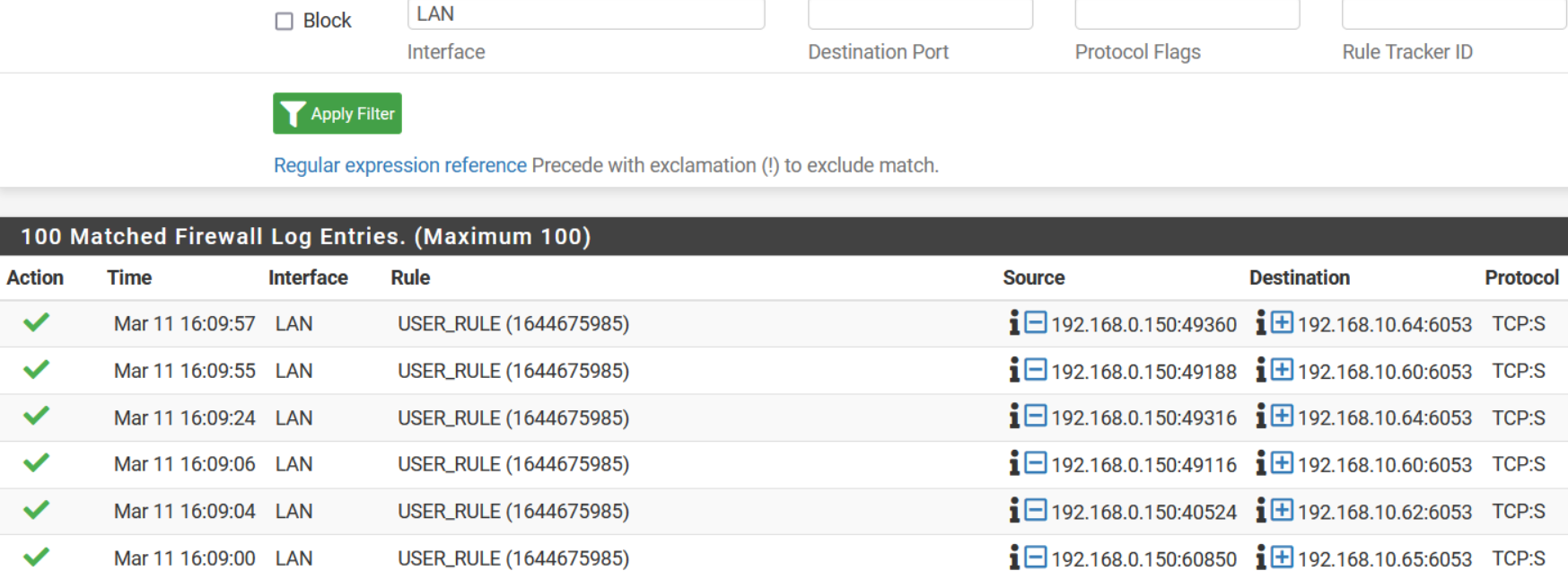
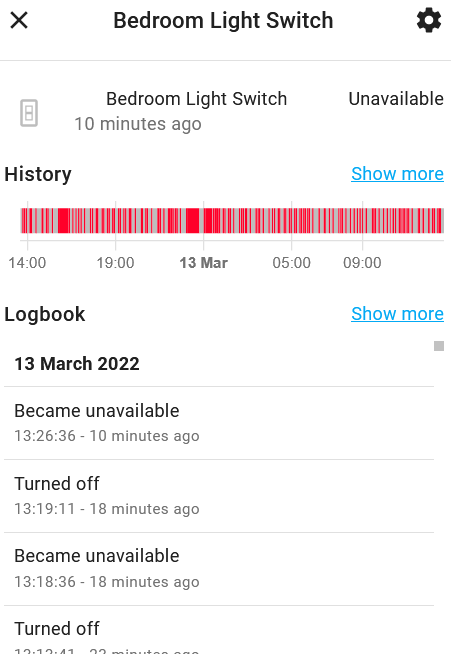
Something weird and interesting is happening. I have a home-automation server that is residing on my LAN and I have a couple of smart light switches residing on my IoT (or DMZ) interface side. In order to get online status displayed in my automation server, it sends communication ACK port 6053 to my swtiches on the DMZ. This I can see through packet captures. But for some reason there is a random drop in states for these switches on the DMZ.
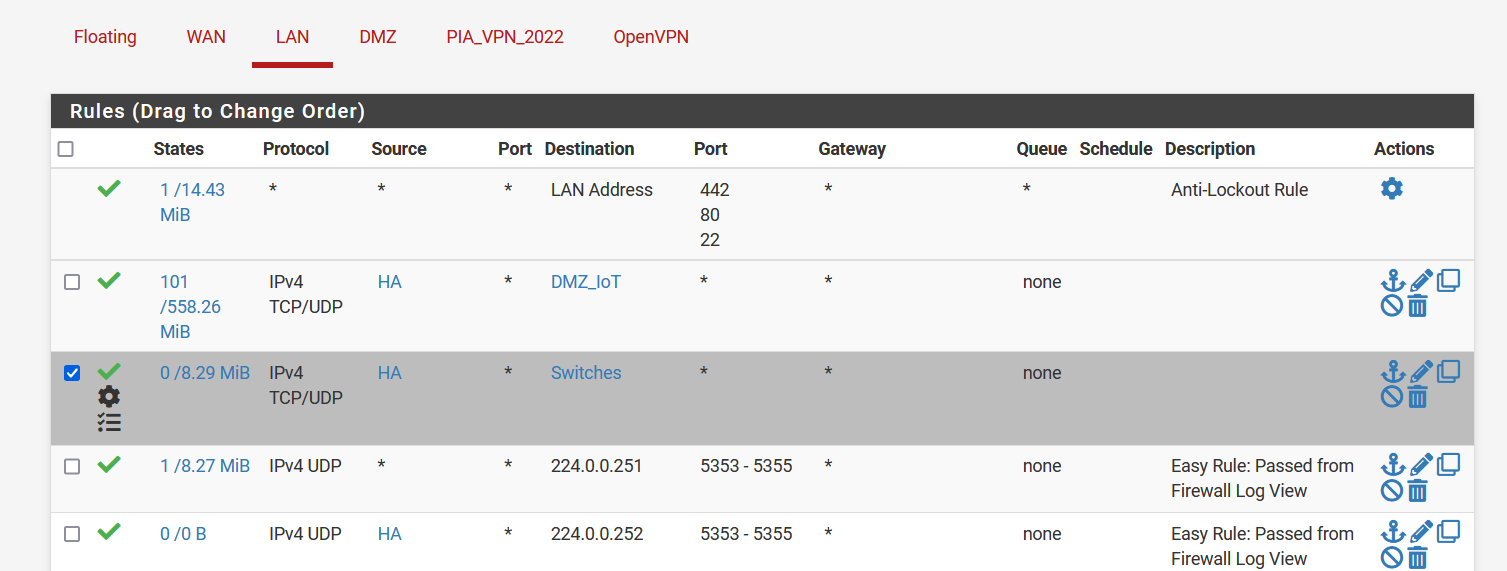
I've configured a LAN FW Rule allowing TCP with the source being my server and the destination being the switches with port any just for troubleshooting to see if anything other thatn port 6053 is needed but no changes.
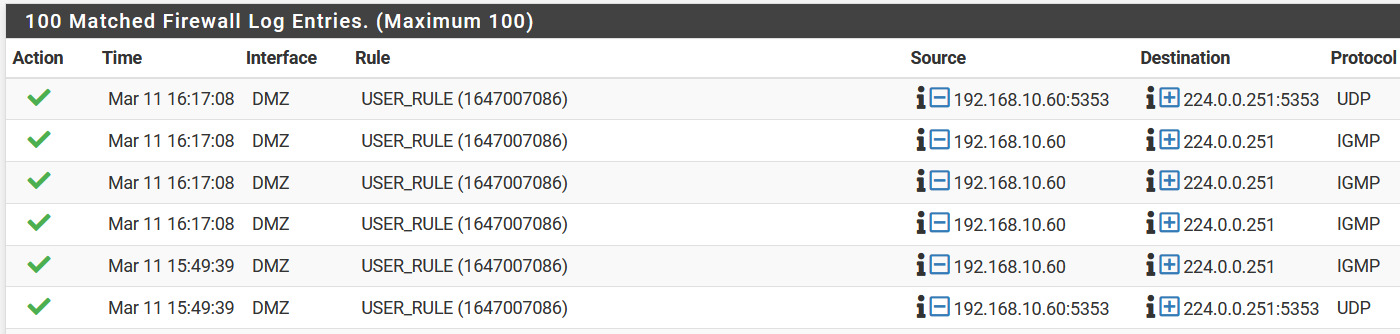
I've even configured a rule in DMZ Allowing the switches any any on any port while logging activity to see what happens and although I see it trying to get IGMP and 224.0.0.251:5353 nothing else shows up. So I'm a bit stumped.
Additonal notes, traffic from the DMZ to the internet is going over the OpenVPN internface. I would assume this wouldn't affect it since the FW should know to redirect the traffic appropriately.
Edit. Adding logs from the LAN side and DMZ side to the below.
-
I forgot to add packet capture from pfSense on the LAN side communicating to DMZ of one of the switches that is online then status becomes unknown.
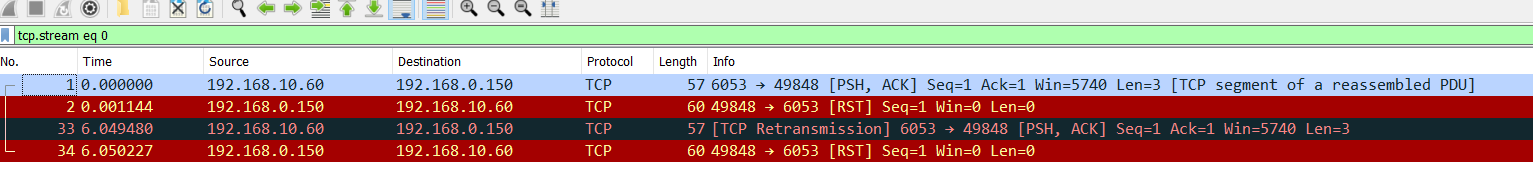
-
tcpdump from the local server with filter of port 6053