Solved - Upgrading from 2.6.0 to Plus - Unable to check for updates
-
@traveller Guess at least I'm not alone...
-
@zachtywebb A post in another thread suggested checking Perfer IPv4 under System->Advanced->Networking.
This allowed me to proceed with my upgrade.
-
@traveller Thanks! Will give that a go next time I have a window where internet can be down.
-
@zachtywebb Good luck
I'm doing the upgrade now as I finally have time when I don't need to connect to work, and my wife is away for the weekend. -
@traveller Thanks for the tip - didn't resolve for me (prefer was already checked, disabled ipv6 temporarily to see if that would help, it didn't.)
-
The issue persists and @Traveller provided the temporary solution. Thank you!
-
I was able to successfully upgrade from 2.5.2 to 2.6.0 to 22.01 last night without needing to set the prefer IPv4 option. Looks like whatever was going on has been fixed.
-
I'm still seeing the problem. If the service side has changed/fixed is there a cache to clear somewhere?
Specifically - still seeing ntop repo SSL validation errors. Pasting the upgrade command output is causing spam errors here :(
-
@traveller Thanks for the advice about preferring IPv4 when IPv6 is enabled I think it is ews.netgate.com that only has an IPv4 address, I also got the following errors when IPv6 was preferred so it looks like a certificate issue as well.
Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.netgate.com
34369339392:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-build-release-tarballs/BUILD_NODE/pkg-amd64-ce/OS_MAJOR_VERSION/freebsd12/PLATFORM/aws/crypto/openssl/ssl/statem/statem_clnt.c:1916:
Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.netgate.com
34369339392:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-build-release-tarballs/BUILD_NODE/pkg-amd64-ce/OS_MAJOR_VERSION/freebsd12/PLATFORM/aws/crypto/openssl/ssl/statem/statem_clnt.c:1916: -
This fixes the issue if the cert errors are for the ntop repo: https://www.yinfor.com/2022/02/upgrade-pfsense-from-the-community-edition-to-pfsense-plus.html
-
I have checked my pfsense install and do not have ntop installed. I am however using IPv6 in a dual stack environment and when I checked my internal DNS server which is used for all DNS queries I noticed that while most DNS queries for A and AAAA records do succceed unfortunately some do not. So if Prefer IPv4 is not selected the upgrade checking process fails, enable it and the Upgrade check works. I have been using dual stack IPv6 for 7 years now, hopefully now this IPv6 issue is highlighted the supporting infrastructure can be updated so Upgrade Check/Upgrade it works correctly
-
Hi all
I have the same issue on a fresh 2.6.0 install, which was on 22.01 before. I've reinstalled to get the box to zfs.
I've started this thread thread
any suggestions?
-
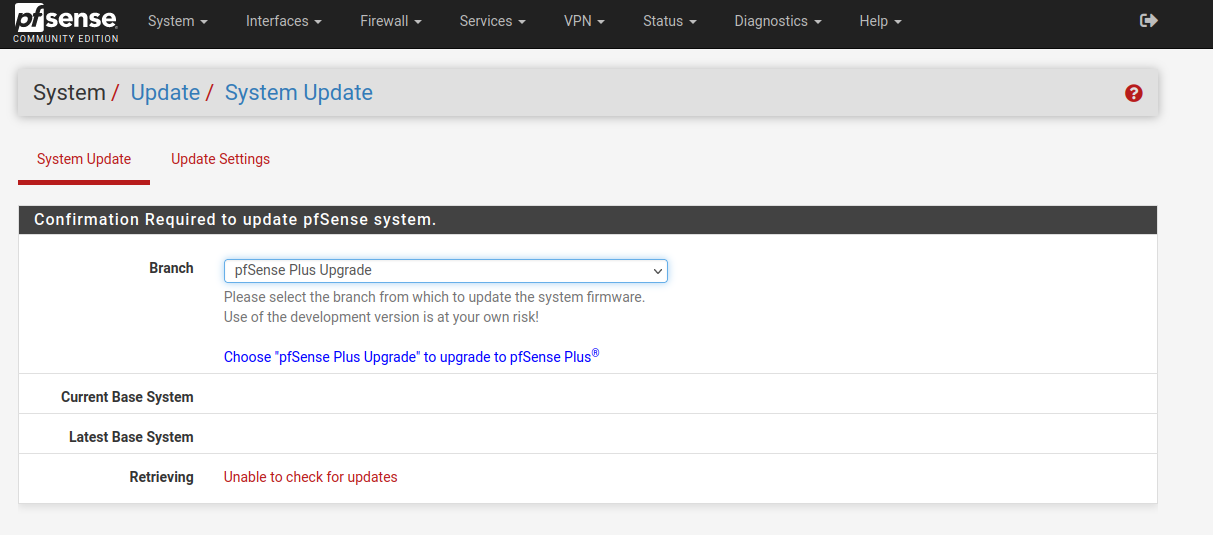
This worked yesterday (April 21) however was not able to run the upgrade from 2.6 to plus. today, getting error:
Retrieving Unable to check for updates
Tried all the suggestions above. No joy. Could someone look at the upgrade server endpoints if there was a change blocking?
Thanks!
-
@dpseattle
I had to copy cert files from a running box to the installation with issues and then it worked.../etc/ssl -rw-r--r-- 1 root wheel 7544 Feb 15 16:54 pfSense-repo-custom.cert -rw------- 1 root wheel 3242 Feb 15 16:54 pfSense-repo-custom.key -
This post is deleted! -
I am also getting update issue. I am getting bad request:
Updating pfSense-core repository catalogue... pkg-static: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v22_01_amd64-core/meta.txz: Bad Request repository pfSense-core has no meta file, using default settings pkg-static: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v22_01_amd64-core/packagesite.pkg: Bad Request pkg-static: https://pfsense-plus-pkg01.atx.netgate.com/pfSense_plus-v22_01_amd64-core/packagesite.txz: Bad Request Unable to update repository pfSense-core Updating pfSense repository catalogue... pkg-static: https://pfsense-plus-pkg00.atx.netgate.com/pfSense_plus-v22_01_amd64-pfSense_plus_v22_01//meta.txz: Bad Request repository pfSense has no meta file, using default settings pkg-static: https://pfsense-plus-pkg00.atx.netgate.com/pfSense_plus-v22_01_amd64-pfSense_plus_v22_01//packagesite.pkg: Bad Request pkg-static: https://pfsense-plus-pkg00.atx.netgate.com/pfSense_plus-v22_01_amd64-pfSense_plus_v22_01//packagesite.txz: Bad Request Unable to update repository pfSense -
Same here,
I this its SSL issue but not sure. -
I have open up a ticket with Netgate support and they made changes on their end to fix this issue. Try to update now and see if it works with you now but if it doesn't open up Netgate support ticket and they will you fix this for free.
-
@adelaide_guy Same blocker. Next, opened a support ticket. Appears they need a cert output from in-place upgraded CE system to correct their backend (asked if the system was in-place upgraded CE migrating to Plus or newly downloaded CE v2.6 upgrading to Plus - might be different fix routes). Anyways Netgate support was awesome! Migration from CE to Plus is complete.