OpenVPN and SG-3100 crypto support
-
Hi,
I am having relatively poor performance with my pfsense 3100 when using openvpn client. When I checked for support it seems to be there:
: kldstat -v | grep cesa 340 simplebus/cesa: dmesg | grep cesa cesa0: <Marvell Cryptographic Engine and Security Accelerator> mem 0x90000-0x9ffff irq 30,31 on simplebus1 cesa1: <Marvell Cryptographic Engine and Security Accelerator> mem 0x90000-0x9ffff irq 39,40 on simplebus1However
vmstat -i | grep cesais not showing any result
and below is showing it is unavailable: /usr/bin/openssl engine -t -c (dynamic) Dynamic engine loading support [ unavailable ]The option to pick a crypto devicehas also disappeared. However, if I understood correctly, this already had no effect on the SG-3100.
I am running PfSense +.So I am wondering, am I having any hardware support for my openvpn connection?
I am using AES-256-GCM and SHA512 -
https://forum.netgate.com/topic/152195/sg-3100-crypto-config?_=1648899454000 answers the question of it missing on the page, but I am still looking for an answer if it is even working. Because it does not seem to be.
btw, I based my queries on this document
https://docs.netgate.com/pfsense/en/latest/hardware/cryptographic-accelerators.html -
@nokkief said in OpenVPN and SG-3100 crypto support:
I am using AES-256-GCM and SHA512
Does the CESA crypto support AES-GCM? I thought it was just CBC.
-
@bigsy This is very true, I amended this (I had been playing with the cipher suite). Alas the results are still the same for me.
using:
Mode: Peer to Peer ( SSL/TLS )
Data Ciphers: AES-256-CBC
Digest: SHA512 -
@bigsy Based on the post you referenced, it does not support sha512. Which is sad, because I can not control that part. Guess I am out of luck on this then.
-
Yes it only supports AES-CBC and only up to 256bit SHA2. But it can be used for one or both of those.
However since pfSense 2.5 (21.02+) it only accelerates IPSec. That's because OpenSSL no longer supports the cryptodev engine which is required to use the BSD crypto framework:
https://www.mail-archive.com/freebsd-stable@freebsd.org/msg136970.html -
@stephenw10 Kind of negates the use of the crypto capabilities though, as ipsec only support aes-gcm and not aes-cbc when I try to set it up through the front end. But I guess I should be looking for some newer hardware if I want better openvpn crypto support. Sad, because I like this little machine on it self.
-
IPSec supports AES-CBC. I use that on a 3100 here:
Apr 6 19:41:25 charon 5290 12[CFG] <con1|2> selected proposal: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ Apr 6 19:41:25 charon 5290 12[IKE] <con1|2> CHILD_SA con1{2} established with SPIs c02b6914_i ca2dbfab_o and TS 172.21.16.0/24|/0 === 172.27.0.0/18|/0 172.30.0.0/21|/0 -
@stephenw10 I only have these options? I must admit I have not used IPSec before though.
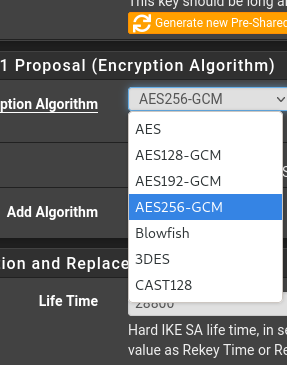
-
'AES' there is aes-cbc.
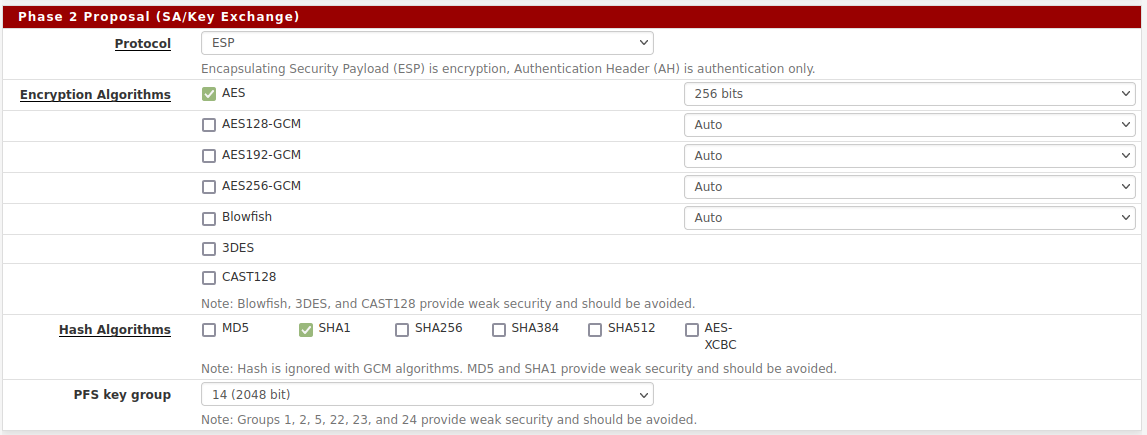
Also the Phase2 is where is counts for speed.
-
@stephenw10 Thanks! I will give it a try then :)
-
M mcury referenced this topic on
-
M mcury referenced this topic on
-
M mcury referenced this topic on
-
M mcury referenced this topic on
-
M mcury referenced this topic on