Netgate 7100 multiple VLANS on one discrete switch lan port?
-
@stephenw10 I have tried to setup my Lan VLANs and the DMZ VLANs. However, none of my DMZ hosts have internet access. I can access them via SSH on LAN but they can't reach the internet.
Any idea of what I have made wrong?
-
If you can access them from LAN then the switch and VLAN settings must be correct, you have two way routed traffic.
You probably don't have a required firewall rules on those VLAN interfaces to allow the DMZ hosts to connect out.
Or the hosts may not have a route. That's unlikely though since they are able to reply to LAN.
Possibly they have no DNS for some reason. Unbound may not be configured to listen on those VLANs. It listens on all interfaces by default though.Steve
-
@stephenw10 - Yes, I though as well that it has something to do with my firewall rules. However, all the settings have been imported from my previous pfSense system, including firewall rules from the restore config. (of cause I edited the interfaces and VLANs in the config.xml file)
My firewall rules for my Wireguard DMZ looks like this. It should be fine... i guess?
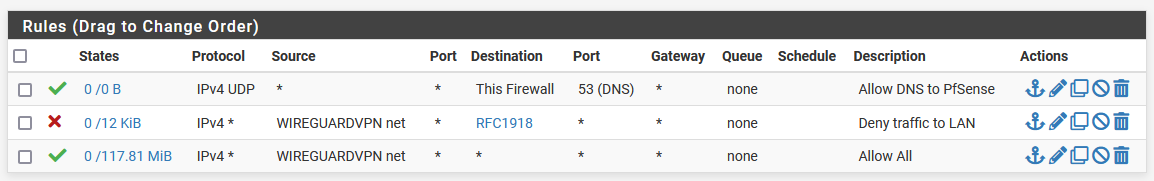
You mention that Unbound DNS might not listen on the DMZ VLANs. Sorry for asking, where can I check this?
-
@runevn said in Netgate 7100 multiple VLANS on one discrete switch lan port?:
where can I check this?
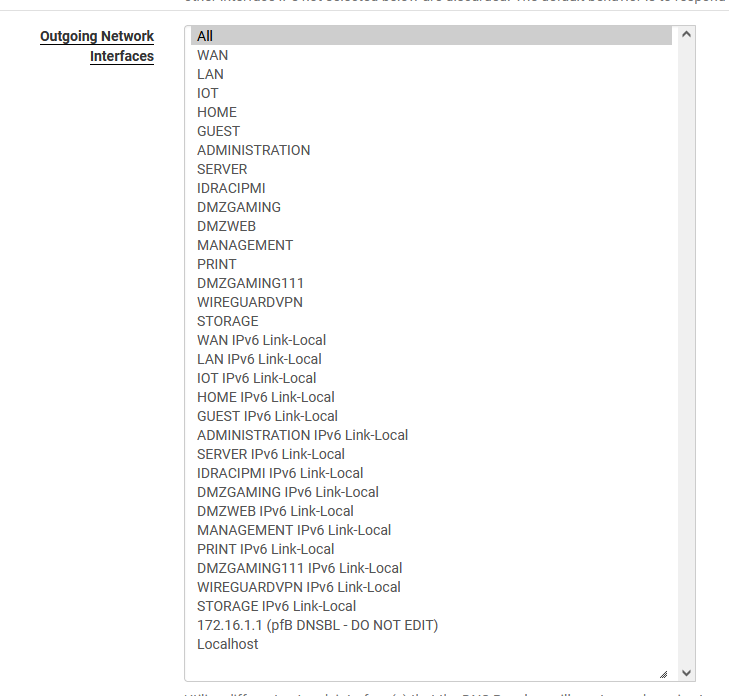
In Services > DNS Resolver. By default 'All' would be selected for Network Interfaces.
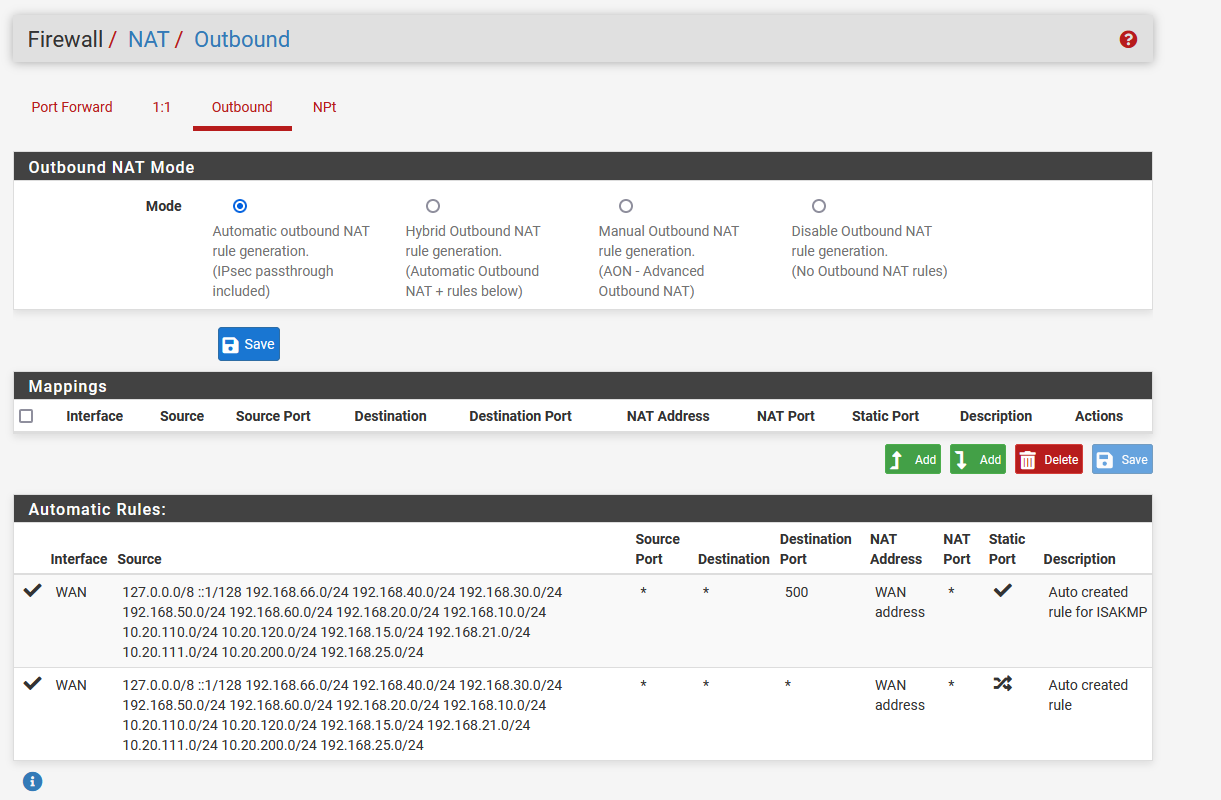
Another possibility is that there are no Outbound NAT rules for the new interfaces. If the outbound NAT has been changed to manual you would have to add them after creating new subnets.
See: Firewall > NAT > OutboundSteve
-
@stephenw10 In the DNS Resolver all interfaces are selected and the outbound NAT rules is set to automatic.
However, DNS resolver has a IPv6 Link-Local version. I have not enabled IPv6. Could that cause a conflict?
-
@runevn said in Netgate 7100 multiple VLANS on one discrete switch lan port?:
I have not enabled IPv6. Could that cause a conflict?
No, that's expected.
Is the subnet you are testing from shown in the automatically added outbound NAT rules?
How are you testing? What error do you see?
Steve
-
@stephenw10 - first of all thank you so much with your patience, I think I found the error.
In my previous pfsense system I had three physical ethernet ports:
- WAN (igb0)
- LAN (igb1)
- DMZ (igb2)
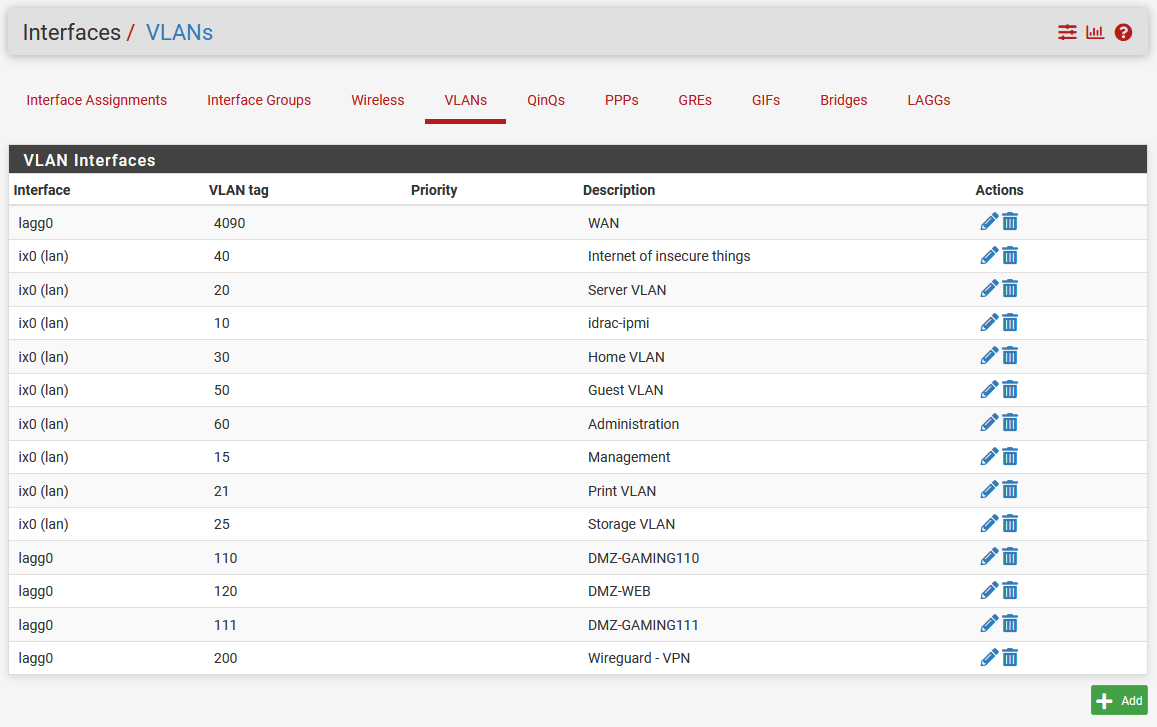
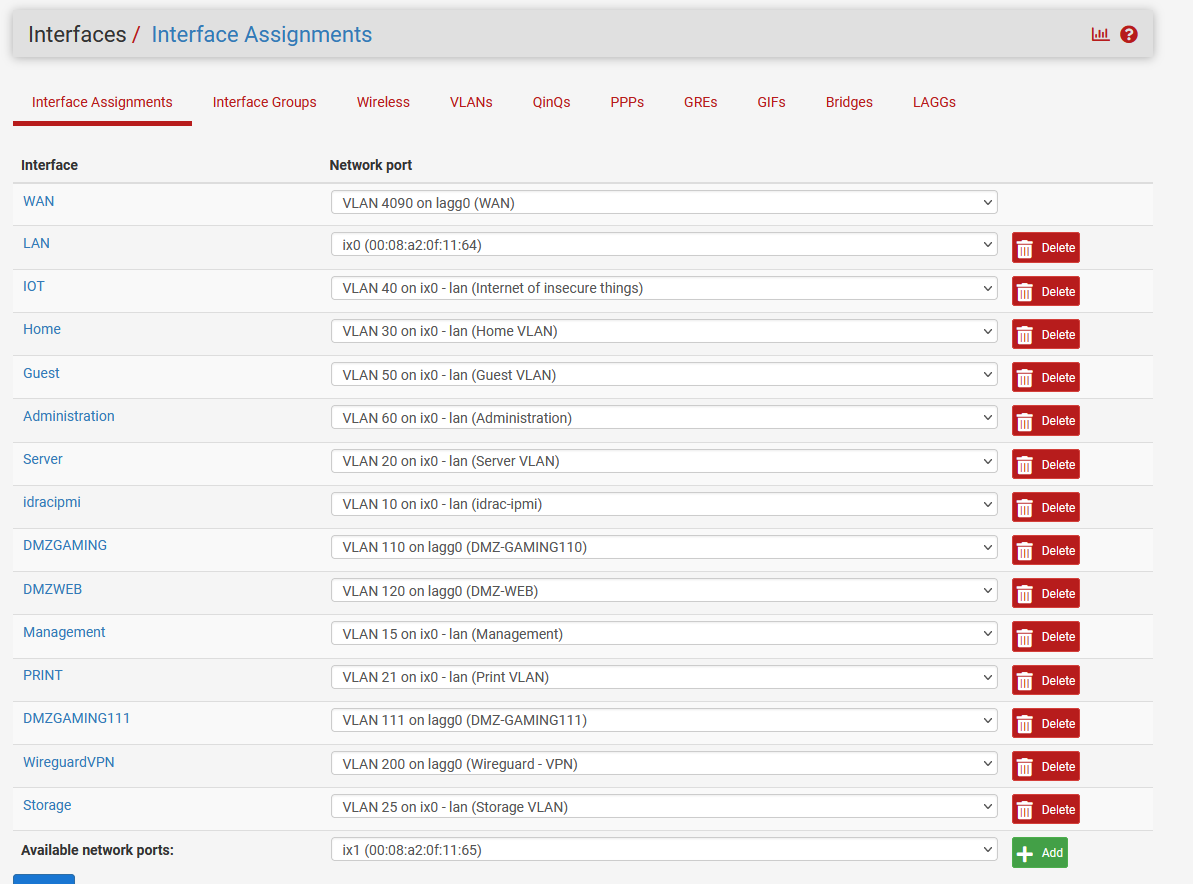
In my VMs I had the parent DMZ interface igb2 set as the DNS nameserver in resolv.conf and not the VLAN.
After I restored the old config at the new 7100 (with no discrete port and parent interface for the DMZ VLANs) it could of cause not resolve the DNS.
But again, thank you for your help and support.
-
Sorry for the intrusion but i feel like this is such a confusing topic, including for me and i would like to express my understanding in my own words , and maybe somebody from Netgate/pfSense to confirm or infirm.
I'm trying to migrate my VLANs from the switch ports to the discrete ports since we have 10Gbps switches/servers
How i think about this, is just separate the Switch from the router itself when thinking about configuration options, just like you'd have 2 devices
- a 4 x discrete port router ( 2 x 10Gi ports , 2 x 2.5Gi ports)
- a 10 x port switch ( 2 x 2.5Gi ports, 8 x 1Gi ports)
-
The router is connected to the switch (be default) through the 2.5Gi ports which are in a LAGG (Lagg0) on the router. The integrated switch does not support LACP , so the LAGG on the router side is set to LOADBALABCED mode so there's nothing to configure on the switch side for this.
-
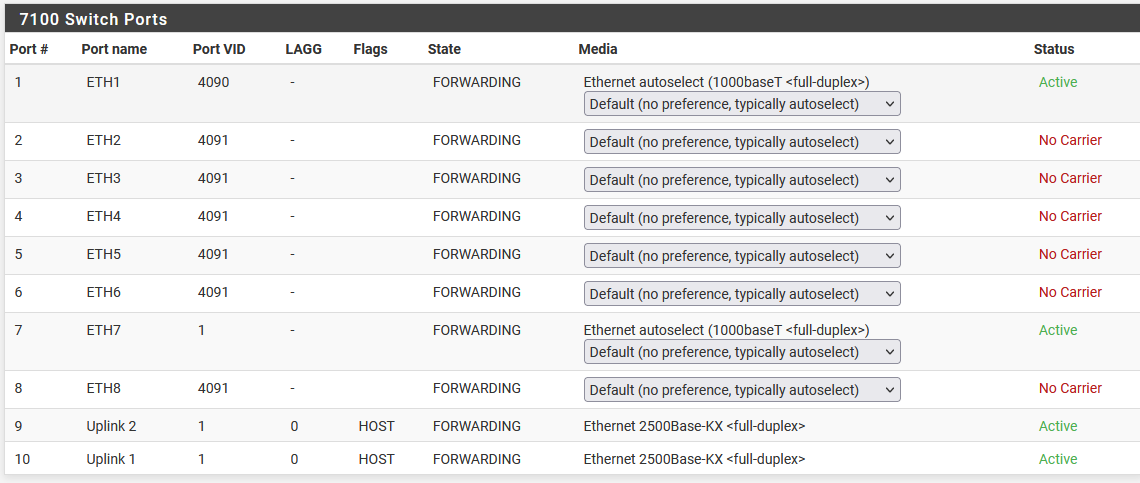
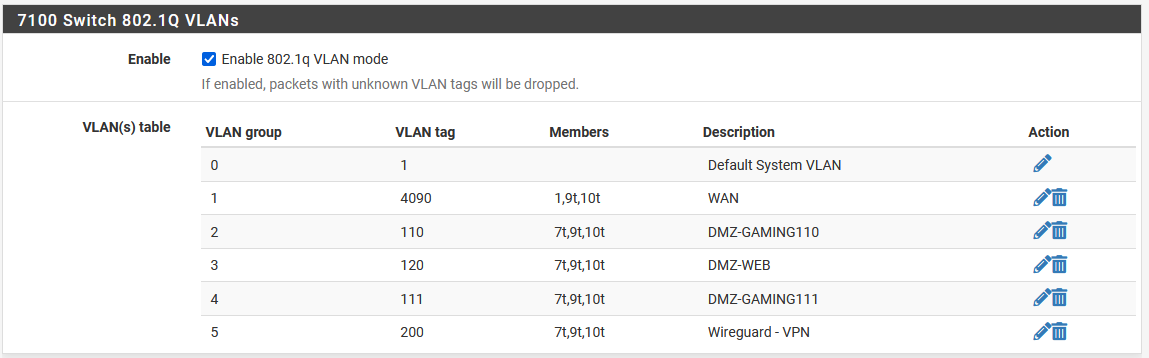
Trunking is done on the switch , where in 802.1q VLAN mode you add each port to the desired VLAN, making ports 9,10 tagged for that VLAN if you have a corresponding VLAN interface on the router LAGG0 as parrent (LAGG0.10 interface on the router would expect traffic tagged with VLAN ID 10 from the switch) , otherwise the traffic will not reach the router SoC
-
If you so desire the integrated switch ports can also be used just as on a regular stand-alone switch, leaving out ports 9,10 when creating VLANs on it so traffic is only sent to the other switch/device but not to the router
- for example (somebody correct me if i'm wrong):
- VLAN15 is configured on discrete port ix0 as parent on the router
- the port is connected to a 10 port stand-alone switch and you run out of
ports
- you could (i think) , create a new trunk port on the stand-alone switch , connect it to a swtichport on the router , tag the port with the required VLAN , add other ports to the VLAN , leaving out ports 9,10 ... to extend your stand-alone switch.
-
On the integrated switch, the port PVID should be the same as the un-tagged/native VLAN
-
There's no STP on the integrated switch , so watch out for loops
-
@aduzsardi said in Netgate 7100 multiple VLANS on one discrete switch lan port?:
The integrated switch does not support LACP , so the LAGG on the router side is set to LOADBALABCED mode so there's nothing to configure on the switch side for this.
Actually the internal switch ports, 9 & 10, are configured in a lagg group in the swith config.
@aduzsardi said in Netgate 7100 multiple VLANS on one discrete switch lan port?:
If you so desire the integrated switch ports can also be used just as on a regular stand-alone switch
Yes you can do that. Though it would probably confuse some other sysadmin at a later date!
Other fun things you can do include:
Separating the internal lagg and configuring the switch as two discrete switches with one internal link to each.
Using port VLAN mode to to connect a single external port to each internal NIC. Then you can pass any traffic including QinQ or LACP.Steve
-
@stephenw10 thank you for the clarification, i just migrated all my VLANs to the 10Gi ports , worked out flawlessly
ix0,ix1 => LAGG1 => LAGG1.vlanXI have just the (3) WAN ports on the integrated switch now
I think this setup is far better utilizing the two 10Gi ports on the internal network , having
them as uplinks for the VLANs