Current firewall vulnerabilities CVE-2022-0934, CVE-2022-20698, CVE-2019-19906, CVE-2021-45079, CVE-2022-0547
-
Hello fellow netgate community members,
is there any quick fix for any of the following CVEs on the stable version of the firewall?
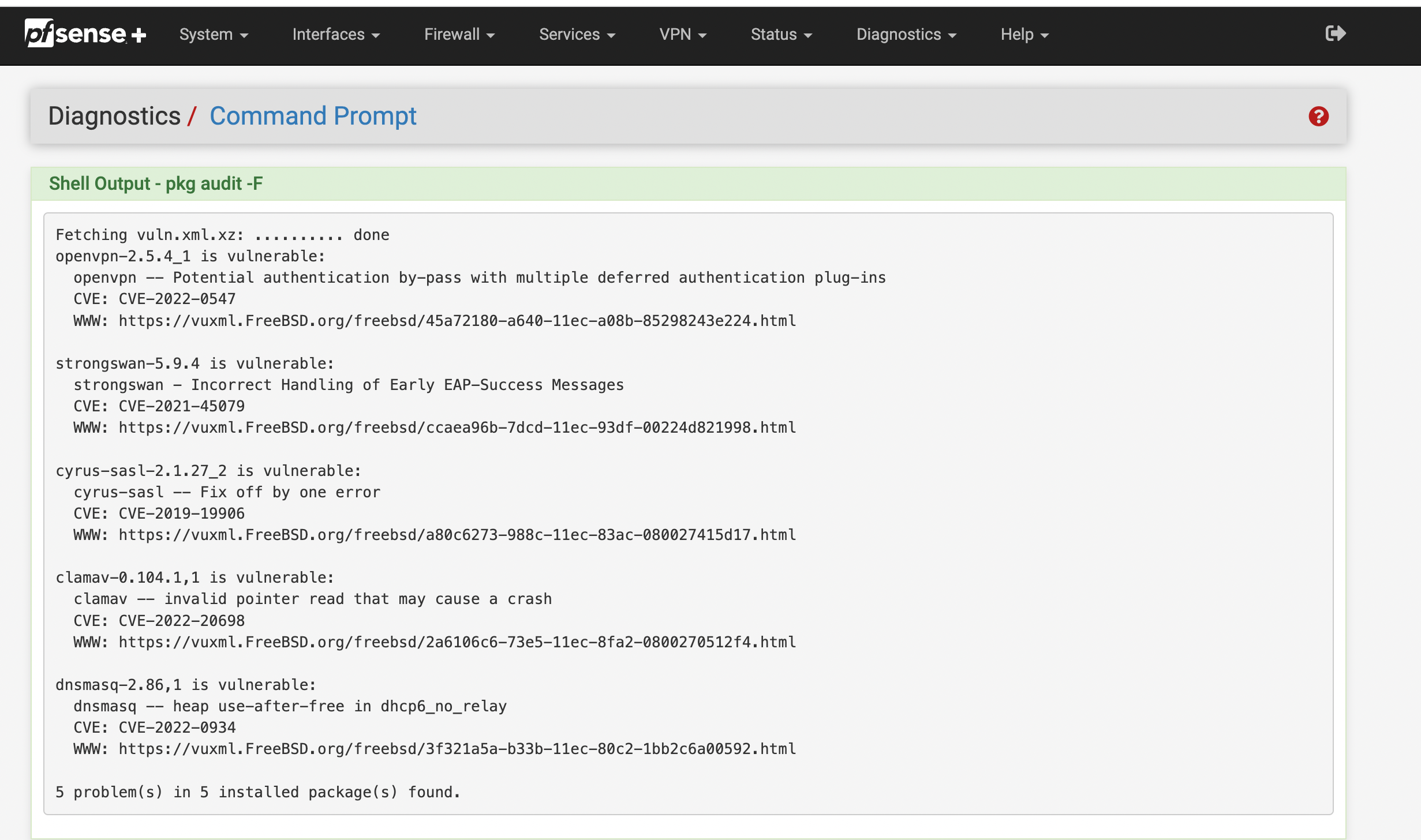
Fetching vuln.xml.xz: .......... done
openvpn-2.5.4_1 is vulnerable:
openvpn -- Potential authentication by-pass with multiple deferred authentication plug-ins
CVE: CVE-2022-0547
WWW: https://vuxml.FreeBSD.org/freebsd/45a72180-a640-11ec-a08b-85298243e224.htmlstrongswan-5.9.4 is vulnerable:
strongswan - Incorrect Handling of Early EAP-Success Messages
CVE: CVE-2021-45079
WWW: https://vuxml.FreeBSD.org/freebsd/ccaea96b-7dcd-11ec-93df-00224d821998.htmlcyrus-sasl-2.1.27_2 is vulnerable:
cyrus-sasl -- Fix off by one error
CVE: CVE-2019-19906
WWW: https://vuxml.FreeBSD.org/freebsd/a80c6273-988c-11ec-83ac-080027415d17.htmlclamav-0.104.1,1 is vulnerable:
clamav -- invalid pointer read that may cause a crash
CVE: CVE-2022-20698
WWW: https://vuxml.FreeBSD.org/freebsd/2a6106c6-73e5-11ec-8fa2-0800270512f4.htmldnsmasq-2.86,1 is vulnerable:
dnsmasq -- heap use-after-free in dhcp6_no_relay
CVE: CVE-2022-0934
WWW: https://vuxml.FreeBSD.org/freebsd/3f321a5a-b33b-11ec-80c2-1bb2c6a00592.html5 problem(s) in 5 installed package(s) found.
(Image: current CVEs listed on firewall) -
This post is deleted! -
This post is deleted! -
Getting this on 2.5.2
Fetching vuln.xml.xz: .......... done
curl-7.76.1 is vulnerable:
curl -- Multiple vulnerabilities
CVE: CVE-2022-30115
CVE: CVE-2022-27782
CVE: CVE-2022-27781
CVE: CVE-2022-27780
CVE: CVE-2022-27779
CVE: CVE-2022-27778
WWW: https://vuxml.FreeBSD.org/freebsd/11e36890-d28c-11ec-a06f-d4c9ef517024.htmlcURL -- Multiple vulnerabilities
CVE: CVE-2021-22926
CVE: CVE-2021-22925
CVE: CVE-2021-22924
CVE: CVE-2021-22923
CVE: CVE-2021-22922
WWW: https://vuxml.FreeBSD.org/freebsd/aa646c01-ea0d-11eb-9b84-d4c9ef517024.htmlcURL -- Multiple vulnerabilities
CVE: CVE-2021-22947
CVE: CVE-2021-22946
CVE: CVE-2021-22945
WWW: https://vuxml.FreeBSD.org/freebsd/c9221ec9-17a2-11ec-b335-d4c9ef517024.htmlcURL -- Multiple vulnerabilities
CVE: CVE-2022-27776
CVE: CVE-2022-27775
CVE: CVE-2022-27774
CVE: CVE-2022-22576
WWW: https://vuxml.FreeBSD.org/freebsd/92a4d881-c6cf-11ec-a06f-d4c9ef517024.htmlpython38-3.8.10 is vulnerable:
Python -- multiple vulnerabilities
WWW: https://vuxml.FreeBSD.org/freebsd/145ce848-1165-11ec-ac7e-08002789875b.htmlopenvpn-2.5.2_2 is vulnerable:
openvpn -- Potential authentication by-pass with multiple deferred authentication plug-ins
CVE: CVE-2022-0547
WWW: https://vuxml.FreeBSD.org/freebsd/45a72180-a640-11ec-a08b-85298243e224.htmlstrongswan-5.9.2_2 is vulnerable:
strongswan - Incorrect Handling of Early EAP-Success Messages
CVE: CVE-2021-45079
WWW: https://vuxml.FreeBSD.org/freebsd/ccaea96b-7dcd-11ec-93df-00224d821998.htmlstrongswan - denial-of-service vulnerability in the gmp plugin/denial-of-service vulnerability in the in-memory certificate cache
CVE: CVE-2021-41991
CVE: CVE-2021-41990
WWW: https://vuxml.FreeBSD.org/freebsd/58528a94-5100-4208-a04d-edc01598cf01.htmlcyrus-sasl-2.1.27_1 is vulnerable:
cyrus-sasl -- Fix off by one error
CVE: CVE-2019-19906
WWW: https://vuxml.FreeBSD.org/freebsd/a80c6273-988c-11ec-83ac-080027415d17.htmlhiredis-0.13.3 is vulnerable:
hiredis -- integer/buffer overflow
CVE: CVE-2021-32765
WWW: https://vuxml.FreeBSD.org/freebsd/2220827b-c732-11ec-b272-901b0e934d69.htmlmpd5-5.9 is vulnerable:
MPD5 PPPoE Server remotely exploitable crash
WWW: https://vuxml.FreeBSD.org/freebsd/f55921aa-10c9-11ec-8647-00e0670f2660.htmlnss-3.66 is vulnerable:
NSS -- Memory corruption
CVE: CVE-2021-43527
WWW: https://vuxml.FreeBSD.org/freebsd/47695a9c-5377-11ec-8be6-d4c9ef517024.htmlredis-6.0.14 is vulnerable:
redis -- multiple vulnerabilities
CVE: CVE-2021-32626
CVE: CVE-2021-32627
CVE: CVE-2021-32628
CVE: CVE-2021-32672
CVE: CVE-2021-32675
CVE: CVE-2021-32687
CVE: CVE-2021-32762
CVE: CVE-2021-41099
WWW: https://vuxml.FreeBSD.org/freebsd/9b4806c1-257f-11ec-9db5-0800270512f4.htmlredis -- Multiple vulnerabilities
CVE: CVE-2022-24736
CVE: CVE-2022-24735
WWW: https://vuxml.FreeBSD.org/freebsd/cc42db1c-c65f-11ec-ad96-0800270512f4.htmlredis -- Integer overflow issues with BITFIELD command on 32-bit systems
CVE: CVE-2021-32761
WWW: https://vuxml.FreeBSD.org/freebsd/c561ce49-eabc-11eb-9c3f-0800270512f4.htmldnsmasq-2.85_1,1 is vulnerable:
dnsmasq -- heap use-after-free in dhcp6_no_relay
CVE: CVE-2022-0934
WWW: https://vuxml.FreeBSD.org/freebsd/3f321a5a-b33b-11ec-80c2-1bb2c6a00592.html16 problem(s) in 10 installed package(s) found.
Would be nice to see patches to the stable versions.
-
[removed]
-
@woundeddog said in Current firewall vulnerabilities CVE-2022-0934, CVE-2022-20698, CVE-2019-19906, CVE-2021-45079, CVE-2022-0547:
thats nothing BUCH of command in dos, i created a script of you all want it funny
Um...wat?! This looks like a setup for spam. Justify it or it will removed.
Steve
-
@stephenw10 I agree

-
@cool_corona I had honestly couldn't believe they have a built in command that will check CVE numbers similar to Kali when you run pen tests. But it's built in to pfSense.
-
It's built into the FreeBSD package system. It would be silly for us not to carry that across.