How to put router before pfsense 22.01 firewall
-
This post is deleted! -
The most likely problem there is a subnet conflict. pfSense uses 192.168.1.0/24 as it's default LAN subnet. That's a very common subnet. If the upstream router is also using it that will break routing, one of them needs to be reconfigured not to use it.
But as we said in the other thread it would be much better to just connect to the OpenVPN service from pfSense directly. Troubleshooting that problem is what I would be doing here.
Steve
-
This post is deleted! -
Yes, the default configuration in pfSense should work fine in that situation.
The WAN will be DHCP so it will pull a lease from the VPN router in the 10.105.x.x subnet with the VPN router as it's gateway and default route.
A client connected to the pfSense LAN will get an IP from the DHCP server in pfSense. By default that will be in the 192.168.1.0/24 subnet.
Everything should work as long as the VPN router is routing traffic.How does it fail?
Can clients ping 8.8.8.8?
Can they ping google.comCan pfSense itself do either from Diag > Ping?
Steve
-
This post is deleted! -
This post is deleted! -
@rupocinski said in How to put router before pfsense 22.01 firewall:
I will set the VPN to DHCP towards the ISP and then Lan 10.105.17.1 and the firewall WAN DHCP connected to the LAN of the VPN and the LAN 10.105.17.2 will this work or no
No that would not work. You can't use 10.105.17.0/24 on both the WAN and LAN side of pfSense.
In that scenario pfSense will pull a DHCP lease from the VPN router in the 10.105.17.x subnet.
Then you must use a different subnet on the pfSense LAN. The default 192.168.1.1 would be fine.Steve
-
This post is deleted! -
Yes. The VPN router will be in the pfSense default route so traffic from LAN clients will be able to reach it.
-
This post is deleted! -
You can't screw it up too badly, you can just remove pfSense to get access to the VPN router again if you need to.
Basically:{Public WAN IP/VPN}--[WAN VPN_Router LAN]-10.105.17.1----10.105.17.2-[WAN pfSense LAN]-192.168.1.1----192.168.1.100-[client]
-
This post is deleted! -
Yes, you would need to change those statically configured devices to be in the same subnet.
Or you can use the 10.105.17.0/24 subnet on the pfSense LAN and change the VPN-router LAN to be some other subnet.
Clients in a 192.168.1.X subnet behind pfSense will be able to reach 10.105.17.X addresses because that is in the default route. pfSense will route between the subnets.
Of course it would still be better to just use the OpenVPN client in pfSense directly and not have two subnets at all.

Steve
-
This post is deleted! -
@rupocinski said in How to put router before pfsense 22.01 firewall:
I read forums and worked with ExpressVPN techs and still could not
Upfront, I use "2.6.0 CE", not "pfSnse Plus 22.0x".
I'm not working for ExpressVPN (support) but I'm in the 'assisting' : I work for a hotel.In the OpenVPN forum I've posted two ( ? ) step by step OpenVPN with Express setups.
I have the OpenVPN client still 'ready to go', let me start it up :
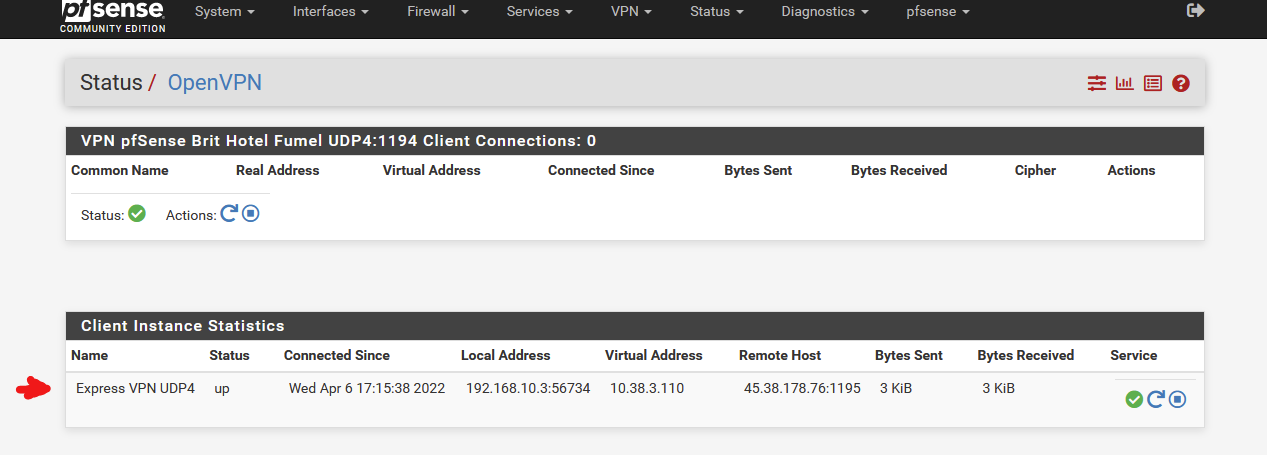
there. Connected. So pfSense 2.6.0 works with ExpressVPN.
And yes, I'm using "usa-sanfrancisco-ca-version-2.expressnetw.com:1195" as the ExpressVPN other side end point. I do pay ExpressVPN every month "just to have a VPN ISP for the day I need one". Never found the reason, but that's another story.I've not set up the other second half of the needed setup, the routing part.
Connecting, making the tunnel, to a VPN ISP is one thing.
Having traffic, like some LAN devices, or just one LAN, or all the LAN networks being routed over this tunnel instead of the default WAN interface needs some more setup.The somewhat outdated documentation on the ExpessVPN site uses an older version of pfSense and, more important, presumes older OpenVPN "2.4.x" version.
pfSense 2.6.0 (probably also 22.0x) uses OpenVPN 2.5.4.Go to to pfSense OpenVPN forum, use my name, look up all the posts that are ExpressVPN related, and you will find, I hope, useful information.
Also, I have a ISP router before my pfSense, and this is IMHO the most common setup. Not that this is important when you want to use the OpenVPN client. This only matters when you want to use the OpenVPN server, as the 1194 UDP port has to be natted to pfSense in the upstream router.
I'm not an ExpressVPN fan or so, and as said, I never actually used their services (yet I'm stupid enough to pay them ?!? - and they are not what I call cheap).
Express proclaims to use OpenVPN on their side as the server part. So OpenVPN on the pfSense client side should work.
Now you know it does. I hope I convinced you that, as you use the same software on your side as I do, pfSense, you can make it work.And yes, creating an OpenVPN connections is not easy. They never was, and never will be. It's a beast will a lot of options, as it is an open source thing and everybody (the entire planet by now ?) wanted options in it.
-
They don't need to be in the same subnet. pfSense routes between the subnets. The same way you can reach 8.8.8.8 or any other IP that is not in your subnet. You will be able to access the VPN-router from a client on the pfSense LAN.
There is no special work-around required to use pfSense as an OpenVPN client in 22.01. It just needs to be configured correctly. It will work if it is.
So far we have nothing to use to diagnose whatever issue you might have been having.
If you can post the OpenVPN logs with the connection error(s) then we can offer guidance.Steve
-
This post is deleted! -
Removed, as it clutters up the OP's topic
/Bingo
-
@rupocinski said in How to put router before pfsense 22.01 firewall:
I got the openVPN up and running
So Status > OpenVPN showed the client as UP with traffic passing?
but the interface would not connect
What interface? The assigned OpenVPN interface?
If the OpenVPN tunnel was up that interface would show as connected.Steve
-
@bingo600
Ok so what I want to do is have a vpn for encryption then my firewall then a the dhcp router. I just wanted to use the pfsense as the firewall so that means I would always be connected to VPN. I am worried about security. I know the firewall is good but would feel better with a vpn in place. Not really happy with expressvpn subscriptions up in sept so not renewing it. Would like another alternative to this whole configuration setup. So you use your VPN now and then not all the time. Sounds like a good setup. What advice do you have for me at this point you know what I want to do, firewall the DHCP firewall had issues dropping clients at times so I thought why not use it and put a router behind it to handle the DHCP which are all static routes anyway with MAC. Just want to be secure. I setup the pfsense as it was supposed to be and I did Pfblocker also. Will install Snort also.