Upping home security with first pfSense build
-
Hi everyone,
After silently reading for a few weeks, it is time for my first post on the forum.
Background:
I have been running a TrueNAS home server for 5 years. My family and I use it as file server with some addons (Nextcloud, Plex, and lately also Bitwarden server, all of them in separate iocage jails). Especially this last addition made me rethink my security architecture.Security today:
At the moment, I have a standard modem/router (the one provided by my ISP), forwarding ports 80 and 443 to my nginx reverse proxy jail on TrueNAS, as well as a higher port to my openVPN jail.
The reverse proxy handles SSL encryption with a letsencrypt certificate and with IPFW dropping all requests with IPs from outside of my small country. All jails have as tight IPFW rules as possible to the best of my knowledge, blocked port 22 and disabled sshd (I access them via host system).
OpenVPN allows me to access the host system remotely, and all my services when I am abroad.I hadn't had any (detected) intrusions in this past 5 years of operation. In my non-professional opinion, the geoblocking and not listening on port 22 already adds a lot to overall security and keeps 99% of bots and low-skilled intruders out.
However, I am a bit anxious of some exploit of any one of my services or infection of my more exposed devices, which endangers the rest of my network (e.g Bitwarden or personal laptops). Because, and this I don't like, it still is a very basic home network without any subnets/vlans, etc. In the lower IP range, all smartphones, laptops, printer etc can be found, and the higher IP range is used for the NAS host system and all the jails. And if root access in a jail is compromised any outbound rules on IPFW are of course moot.
Plan for the future:
First, I was thinking about a managed switch, allowing for separating personal devices and the host system from the exposed jails. But more and more I think a pfsense box may be the better, more secure and more versatile choice. Reverse proxy and OpenVPN would sit on pfSense (?), the rest stays on TrueNAS. I was imagining something like this:
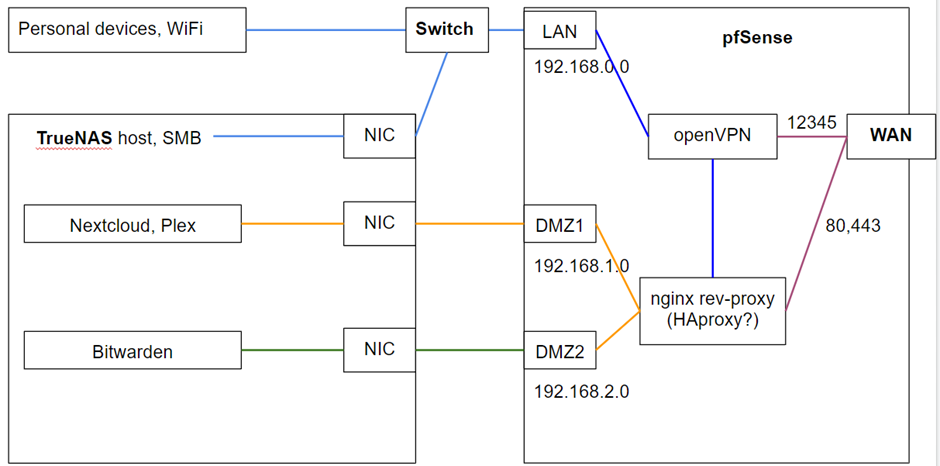
What do you guys think about this strategy?
- Reasonable?
- Does it add to the security or need I do better?
- Realistic? I don’t know pfSense yet, can I deploy plugins in jails?
o Reverse proxy
o OpenVPN
o Geoblocking?
EDIT: after reading this article, it may not be the best idea to keep all personal devices in the same VLAN as the TrueNAS host. How would you guys tackle this? Would I need a firewall AND a managed switch?
Hardware
For pfSense, I was thinking about getting one of those small Protectli/Qotom/etc boxes with 4-5 Intel NICS and maybe a i5-5200U and 8GB of RAM? It seems like most of the CPUs in those mini PCs are 6+ years old. But this one seems more recent: 5 Intel i225 NICS and a Celeron J4105 (J4125 seems unavailable).Would this be enough for downloading from Nextcloud with let’s say 500 Mbit/s to 1 Gbps and 1Gpbs LAN traffic (few users, maybe 1-3). I read that OpenVPN tends to be a lot slower due to single core performance only, but this I don’t mind. But does this mean in general, that if I have a passmark score of 2000 of a 2 core (2x1000) and a 4 core (4*500) CPU, I should rather pick the 2 core CPU?
Thank you already in advance, I’d also be happy for some pointers of reading up on the topic, anything else than filling up IPs form 0 to 255 is new to me : )
Cheers,
Weingeist -
Well obviously I'd rather you used our hardware....
I would definitely consider separating your internal devices into different VLANs. IoT devices should not be on a general subnet with other hosts IMO.
I would question why you are forwarding http/s traffic at all. That's inherently insecure.
It would be far better to access those services over a VPN if you need to access them externally.Steve
-
I would still consider the managed switch, this will allow you to add devices to a VLAN easier.
That system is more than enough to handle 1Gb, although I cannot say how fast it will run a VPN. -
Thank you already for your fast answers. I appreciate it a lot.
@stephenw10 said in Upping home security with first pfSense build:
I would question why you are forwarding http/s traffic at all. That's inherently insecure.
It would be far better to access those services over a VPN if you need to access them externally.Well, since I use Nextcloud a lot for sharing and requesting files with/from various people, VPN alone is not really an option.
For clarification, port 80 is only forwarded for being redirected to 443 by the reverse proxy. There is no unencrypted traffic to the internet, only behind the reverse proxy to the backends, which does not seem uncommon to me. And chances for a MITM attack in a wired home network should be slim : )
But could you please elaborate? Are you saying SSL itself is inherently insecure? How would you make such services accessible for multiple people in a secure way?@andyrh said in Upping home security with first pfSense build:
I would still consider the managed switch, this will allow you to add devices to a VLAN easier.
That system is more than enough to handle 1Gb, although I cannot say how fast it will run a VPN.I am a bit confused about some distinctions:
- where would I want a managed switch for managing my Vlans, where do I need the firewall?
- Do I need a physical port for each vlan (in the blog example linked above, there were about 10 Vlans)? Or can I also setup logical Vlans?
- If yes, where should I use physical Vlans, and where are logical Vlans sufficient? Is it just a question of priority, more critical devices should rather be physically separated?
-
SSL itself is relatively secure it's more a question of what you are connecting to. So you could imagine a new exploit discovered in nextcloud that would immediately start being actively probed for and used. If the NC container is compromised what would that imply? Hopefully nothing if it's sufficiently isolated but....
You would usually have a single connection between the firewall and a managed switch that carries all the VLANs. That could be lagg of two ports. Then have the VLANs brought to access ports at the switch. That way you don't need 10 NICs in the firewall.
Steve
-
@stephenw10 ok, agreed. Thats why I want to put those services in DMZs and setting rules that prevent them from being able to connect to one another.
Aah, now I understand much better regarding Vlans and switches. I will rethink my network architecture based on the new insights
Thank you Steve (and Andy)
-
DMZ2 Layer2 Switch ------ Server 2 | | pfSense-------LAN----Layer3 Switch-------VLANs | | DMZ1 Layer2 Switch ----- Server1pfSense-------LAN----Layer3 Switch-------VLANs | | DMZ Layer2 Switch -------- 2 ServersFor big concerns (large files) and routing much traffic
and on top what installed packets will be there in game too! Do you plan using IDS or IPS (inline mode) and if so
where you are want to use it. Is there one or more radius servers in game too? Is there another ids instance inside
this setup, like OSSec or so?