how to bulk import netblocks into an alias?
-
How to bulk import a list of IP netblocks into firewall aliases, and then automate it -- akin to how pfblockerng does it?
Short story: I want to block facebook in/out. FB tells how to get a list of their networks on their developers page, which is:
/usr/bin/whois -h whois.radb.net -- '-i origin AS32934' | /usr/bin/grep ^route | /usr/bin/tr -s ' ' '\t' | /usr/bin/cut -f2 | /usr/bin/uniq
This pipeline could be put into a shell script in pfSense and updated via cron, but what is an easy to pull it into the network aliases list via shell command?
If I put php code into /usr/local/www/mydir in order to pull the list in via an alias URL, eg https://127.0.0.1:443/mydir/mycode.php will this work? Do I risk breaking the pfSense web interface? Will it survive an upgrade? Is there an easier way to do this?
-
I forgot to mention, I am using Netgate pfSense 22.01.
-
Just use the ASN in pfBlocker directly and it does it all for you.

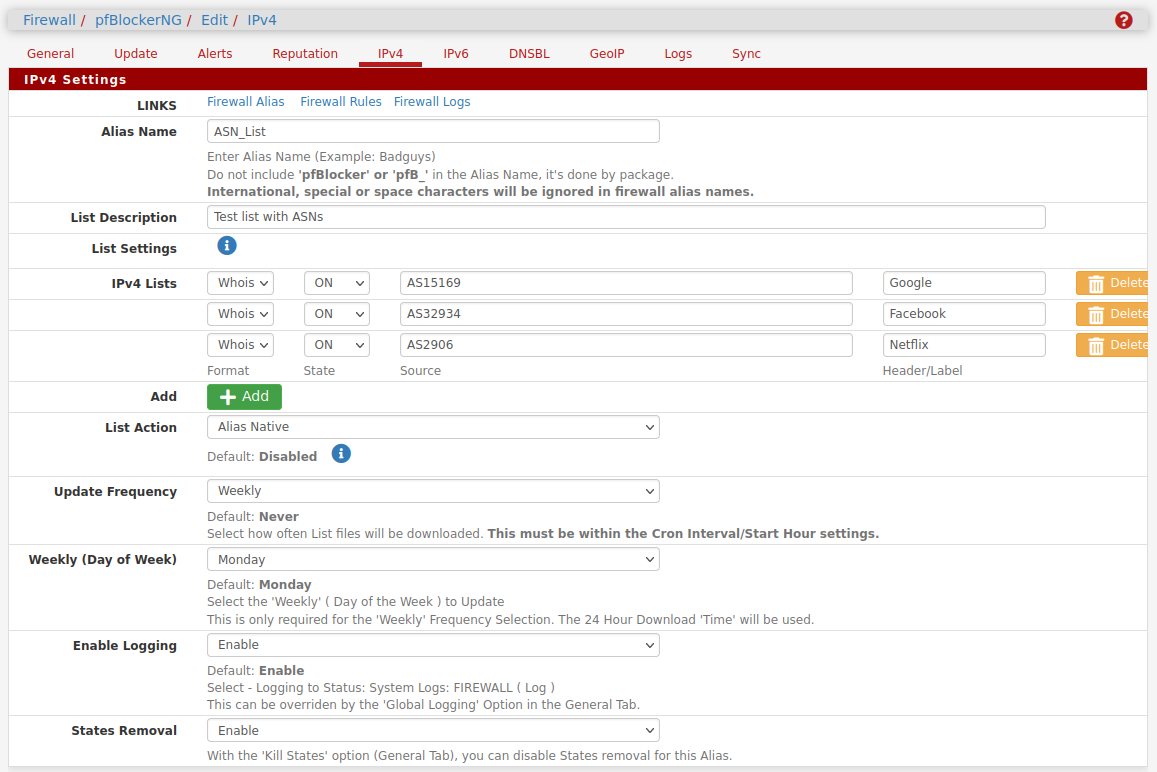
Steve
-
Thank you, thank you!! After getting the whois ASN list pulled into pfblockerng, and doing a force update to get the alias list built, I got my anti-Facebook rules going in floating rules, akin to the other pfBlockerng rules. This is a beautiful thing! It is amazing how much outbound crap to FB I am now blocking -- them stalking me around the Internet that I don't want.
-
While this system of keeping an active list of a company's netblocks works great -- beware. It can suck up memory and result in "cannot allocate memory" errors. Example: building a list for Apple (AS6185) will give you a large list of small netblocks in 17.x.x.x. However, "whois 17.0.0.0" shows that 17.0.0.0/8 is a direct allocation to Apple, so specifying a network alias with a /8 takes a lot less memory. Google is even worse with 7400+ IPv4 netblocks from the whois ASN output.