Port forwarding problem (I did try following the troubleshooting guide)
-
Hi all,
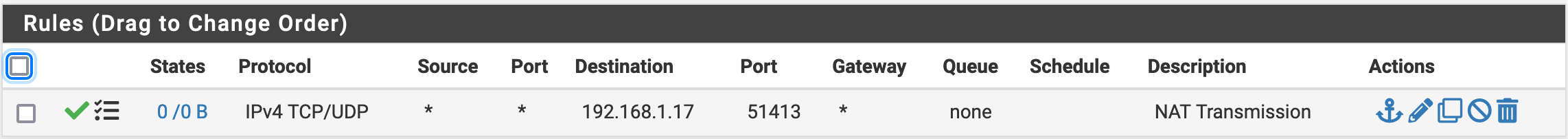
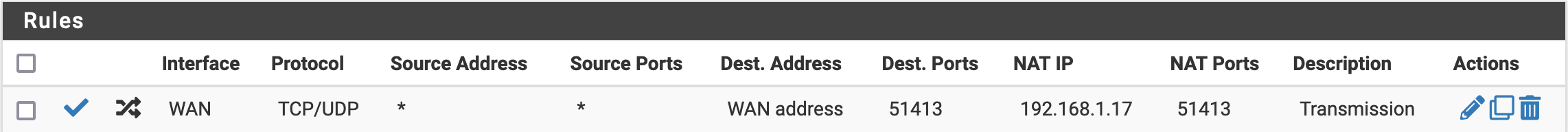
I have to use my ISP's router, and I have absolutely no control over it - I can't even see a status page. I have to email customer service if I want to make any changes to the router settings - even the Wi-Fi password! Anyway, they have set up a DMZ for 192.168.0.10. So, I've set up the pfsense WAN port to be 192.168.0.10, and the LAN port to be 192.168.1.1. The ISP is adamant that the DMZ is on and working. However, I seem to be having trouble with port forwarding. Specifically, I have Transmission on my server (IP 192.168.1.17), and it needs port 51413 forwarded. I have followed the troubleshooting guide and don't seem to be successful. Here are the port forward settings & firewall rules:
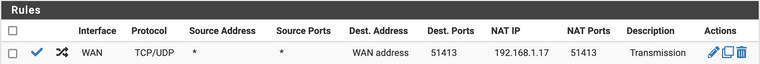
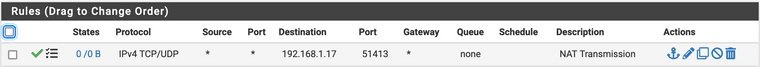
First, I checked the server port if it is enabled properly:
kit@Voyager ~ % sudo nmap -p 51413 192.168.1.17 Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-19 21:41 BST Nmap scan report for 192.168.1.17 Host is up (0.0039s latency). PORT STATE SERVICE 51413/tcp open unknown MAC Address: xxxxx (Dell) Nmap done: 1 IP address (1 host up) scanned in 0.16 seconds kit@Voyager ~ %So far, so good. I am not 100% certain the DMZ is working properly, so someone suggested looking at the firewall logs to check this, while there are a lot of LAN entries - mainly IPv6 - but very few WAN entries, so I am not sure if the DMZ is the problem.
I used a port checker to check port 51413, and it says it's closed, but I get nothing in the logs. I also ran ShieldsUP! while there were some log entries, it is not clear that it is related to ShieldsUP!.
Here are a few lines selected from the firewall log, all relating to the WAN:
Apr 19 21:29:47 WAN Default deny rule IPv4 (1000000103) 192.168.0.1 224.0.0.1 IGMP Apr 19 21:29:17 WAN Default deny rule IPv4 (1000000103) 192.168.0.1:44976 239.255.255.250:1900 UDP Apr 19 21:28:25 WAN Block snort2c hosts (1000000118) 17.253.35.210:80 192.168.0.10:35391 TCP:PADoes this mean the DMZ is working? Moving forward, looking at firewall states, there are a few lines relating to port 51413, for example:
LAN udp 192.168.1.17:51413 -> 54.194.137.170:6881 SINGLE:MULTIPLE 1 / 1 122 B / 95 B WAN udp 192.168.0.10:23220 (192.168.1.17:51413) -> 54.194.137.170:6881 MULTIPLE:SINGLE 1 / 1 122 B / 95 B LAN udp 192.168.1.17:51413 -> 31.133.127.112:6881 NO_TRAFFIC:SINGLE 1 / 0 122 B / 0 B WAN udp 192.168.0.10:53761 (192.168.1.17:51413) -> 31.133.127.112:6881 SINGLE:NO_TRAFFIC 1 / 0 122 B / 0 BAgain, I'm guessing that it's all related to the server trying to talk out on port 51413 but not being successful, but I'm not 100% sure.
I tried doing a nmap scan on pfsense itself, but I have no idea if doing this is a valid method of diagnosis:
[2.6.0-RELEASE][admin@pfSense.xx.intranet]/root: nmap 192.168.0.10 Starting Nmap 7.91 ( https://nmap.org ) at 2022-04-19 21:11 UTC Stats: 0:00:13 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan SYN Stealth Scan Timing: About 72.60% done; ETC: 21:11 (0:00:05 remaining) Nmap scan report for 192.168.0.10 Host is up (0.000043s latency). Not shown: 996 filtered ports PORT STATE SERVICE 22/tcp open ssh 53/tcp open domain 80/tcp open http 443/tcp open https Nmap done: 1 IP address (1 host up) scanned in 15.05 seconds [2.6.0-RELEASE][admin@pfSense.xx.intranet]/root: nmap -p 51413 192.168.0.10 Starting Nmap 7.91 ( https://nmap.org ) at 2022-04-19 21:12 UTC Nmap scan report for 192.168.0.10 Host is up. PORT STATE SERVICE 51413/tcp filtered unknown Nmap done: 1 IP address (1 host up) scanned in 2.20 seconds [2.6.0-RELEASE][admin@pfSense.xx.intranet]Note:
- I have unticked "Block private networks" in the WAN interface setup.
- I have unticked "Block bogon networks" in the WAN interface setup.
- Snort is installed & running. While, I've followed some tutorials on how to set up Snort, I'm inexperienced, so Snort might be blocking 51413 for all I know. That said, I tried turning off Snort and trying the port checker, but no difference.
I am certain I have made plenty of simple mistakes, that I can't figure out by reading the troubleshooting guide, so I would really appreciate your advice here! Thank you so much!
-
@eddles said in Port forwarding problem (I did try following the troubleshooting guide):
I am not 100% certain the DMZ is working properly
Run Diagnostic > Packet Capture on WAN and initiate an access from outside to check out, if the DMZ is working.
From what I see til now, I don't think so.Here are a few lines selected from the firewall log, all relating to the WAN:
Apr 19 21:28:25 WAN Block snort2c hosts (1000000118) 17.253.35.210:80 192.168.0.10:35391 TCP:PA
Does this mean the DMZ is working?This let me assume, outbound from pfSense is basically working. But this is a response packet from a webserver, which is blocked here. That needs further investigation.
However, I'm wondering why you have snort enabled while troubleshooting. You should disable it as well as pfBlockerNG for testing.
-
@viragomann said in Port forwarding problem (I did try following the troubleshooting guide):
Run Diagnostic > Packet Capture on WAN and initiate an access from outside to check out, if the DMZ is working.
From what I see til now, I don't think so.Problem solved, my ISP enabled DMZ on the wrong router (that I have an account for). Cleared up the router details, DMZ now working and port forwarding works perfect. Thank you for your time!