SOLVED: Can only NAT to interface IP. Why?
-
I have successfully set up port forwarding from my WAN interface IP to my LAN interface IP.
I can even get it to work with a virtual IP on the WAN interface, but NAT fails any time i change the destination to an IP inside my LAN net other than my interface.WAN has a firewall rule to allow traffic to each NAT destination, but only NATing to the LAN interface works. LAN allows free access to anything. I have enabled logging. When I NAT to a non-interface IP, I see the rule pass the traffic to its destination but cannot connect to my SSH server behind the firewall. When I do the same thing for the interface IP I see nothing in the packet capture, but i am able to connect.
It seems like something fishy is going on here. Any help would be greatly appreciated.
-
Your description doesnt make much sense to me ^^".
Can you show sceenshots of your firewall rules and your NAT rules? -
I have worked on this for so long that it no longer makes sense to me either. Sorry if I didn't quite communicate the problem.
Here are some pictures to do the talking.First off here is a simple diagram of my network.
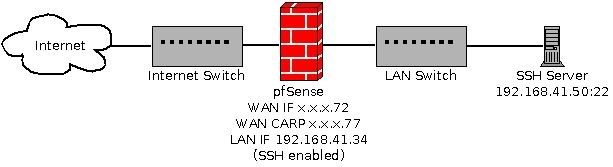
My CARP address
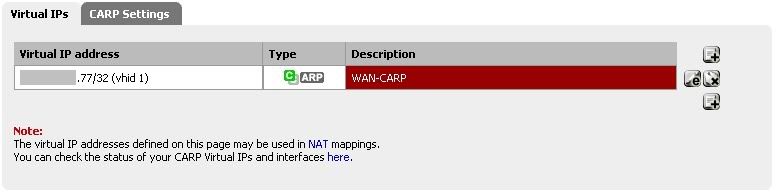
NAT Port Forwarding
Note, it is only like this for the screen shot's sake. I do not expect it to work this way.
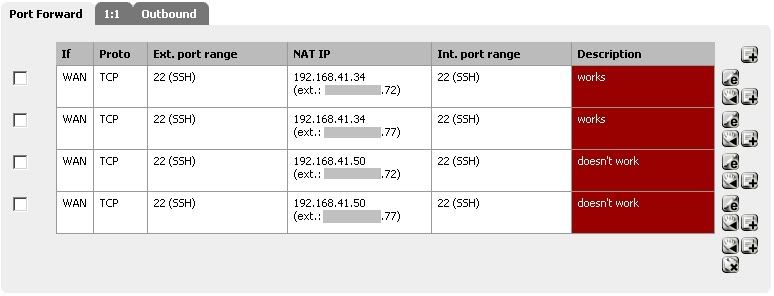
LAN Rule
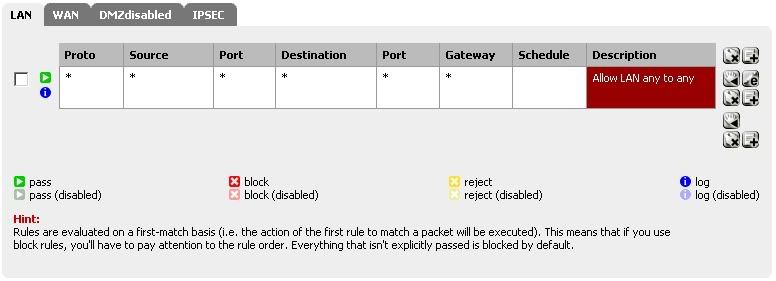
WAN Rules
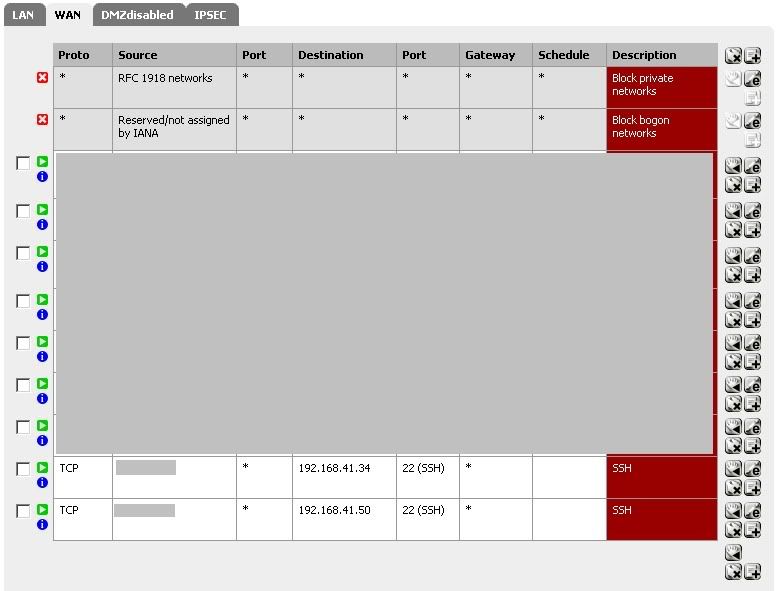
When NAT is set up properly and terminates to the .34 address I can reach a shell from the internet. When it terminates at a PC inside the LAN I cannot reach a shell as I should. There are no iptables or anything else obstructing the SSH server, and I am able to connect to it directly from the LAN.
-
Your VIP is a CARP type VIP with a subnet of /32.
This will not work. Read the notes on the page where you can configure a CARP VIP.This is the network's subnet mask. It does not specify a CIDR
-
Actually, I think this still belongs under NAT. Forget I ever mentioned CARP.
The problem is that I can NAT to 192.168.41.34 my interface address, but not 192.168.41.50 a server inside the LAN.
My point with mentioning CARP was that I could make it work with either the WAN interface or a CARP address. So, please disregard my misconfiguration CARP and focus on the NAT issue.And thanks. I appreciate any help I can get.
-
Your NAT rules appear to be forwarding from both .72 and .77 to .34, which is probably why your SSH server isn't receiving the traffic.
Your probably want to forward .72 -> .34 and .77 -> .50 (or the other way round).
-
Your NAT rules appear to be forwarding from both .72 and .77 to .34, which is probably why your SSH server isn't receiving the traffic.
Your probably want to forward .72 -> .34 and .77 -> .50 (or the other way round).
You apparently missed the note about those settings being there for the sake of the screen shot, but thanks for trying.
-
OK. how about posting your EXACT configuration, without bogus/misleading configuration?
-
Thanks for the offer, but I just figured out where I messed things up. I had a bad route to my .50 address.
-
You have way too smart network -)
Static route with two interfaces! I can't think of any other static route than default gateway… -
The picture did not show the entire network. pfSense shares a LAN with a SonicWall that we are trying to replace and the SonicWall has more VPNs to more networks. Trust me, I wouldn't just add static routes for the fun of it.