Bug Pfblocker new NG 4100
-
Hmm, that would be true for using pfBlocker aliases inside the pfBlocker config. I'm not sure that's valid though. Making my head hurt thinking about how that would update....

-
Yes updated package, and i test in two diferents units of 4100 i check is the same version in 6100
-
Which pfBlocker package though exactly? I'll try to replicate it.
And this is in 22.01?
-
@stephenw10 said in Bug Pfblocker new NG 4100:
that would be true for using pfBlocker aliases inside the pfBlocker config
:) Maybe I'm not on the same page, but if I create a new IPv4 or IPv6 feed as Alias Native it isn't usable until I run an Update in pfBlocker.
@neoos So you are on the GeoIP page and edit a continent there? Did you change Action to Alias Native [edit: or something besides Disabled]? Like so:
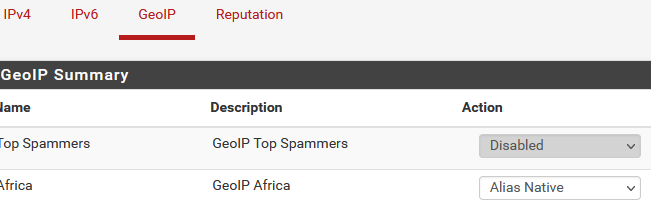
Is this pfBlockerNG-devel or pfBlockerNG? We could not get MaxMind to work with pfBlockerNG so have been using pfBlockerNG-devel for a couple years.
-
@steveits What is the correct use?
-
@neoos Alias Native just creates an alias that you can use in any NAT or firewall rule. The other options, like Deny Outbound, create a rule do what they say and by default put those rules at the top of the list of rules.
Using Deny can also have some unexpected results if deduplication is enabled, so I always just use Alias Native and create my own rules.
From the pfBlocker IPv4 rule page, under Action:
'Disabled' Rules: Disables selection and does nothing to selected Alias.
'Deny' Rules:
'Deny' rules create high priority 'block' or 'reject' rules on the stated interfaces. They don't change the 'pass' rules on other interfaces. Typical uses of 'Deny' rules are:- Deny Both - blocks all traffic in both directions, if the source or destination IP is in the block list
- Deny Inbound/Deny Outbound - blocks all traffic in one direction unless it is part of a session started by traffic sent in the other direction. Does not affect traffic in the other direction.
- One way 'Deny' rules can be used to selectively block unsolicited incoming (new session) packets in one direction, while still allowing deliberate outgoing sessions to be created in the other direction.
'Permit' Rules:
'Permit' rules create high priority 'pass' rules on the stated interfaces. They are the opposite of Deny rules, and don't create any 'blocking' effect anywhere. They have priority over all Deny rules. Typical uses of 'Permit' rules are:- To ensure that traffic to/from the listed IPs will always be allowed in the stated directions. They override almost all other Firewall rules on the stated interfaces.
- To act as a whitelist for Deny rule exceptions, for example if a large IP range or pre-created blocklist blocks a few IPs that should be accessible.
'Match' Rules:
'Match' or 'Log' only the traffic on the stated interfaces. This does not Block or Reject. It just Logs the traffic.Match Both - Matches all traffic in both directions, if the source or destination IP is in the list.
Match Inbound/Match Outbound - Matches all traffic in one direction only.'Alias' Rules:
'Alias' rules create an alias for the list (and do nothing else). This enables a pfBlockerNG list to be used by name, in any firewall rule or pfSense function, as desired.- Options - Alias Deny, Alias Permit, Alias Match, Alias Native
- 'Alias Deny' can use De-Duplication and Reputation Processes if configured.
- 'Alias Permit' and 'Alias Match' will be saved in the Same folder as the other Permit/Match Auto-Rules
- 'Alias Native' lists are kept in their Native format without any modifications.
-
That's not what the screenshot it from though. It's for using existing aliases in the pfBlocker config to customise the auto added firewall rules. And there does appear to be an Issue there. Just narrowing it down.
When typing 't' here I expect to see the IP alias 'Test' I created: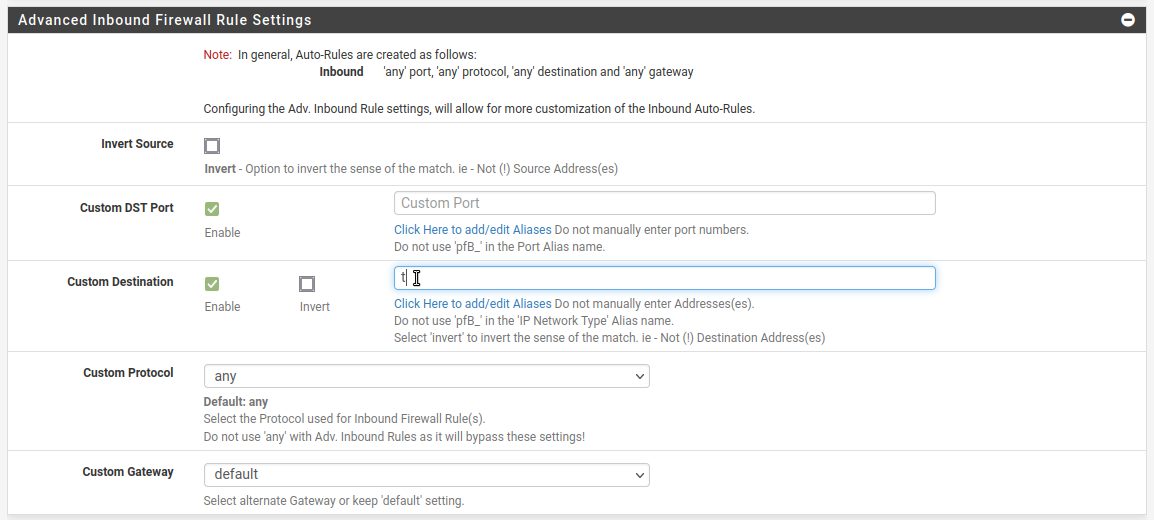
-
Yeah OK it appears to exist in both current pfBlocker package versions but also on all hardware I tested on.
Can we see a screenshot of this working on a 6100?
-
Nope actually this works as expected on the 4100 (and everything else) it just only accepts Network type aliases there not Host.
Steve
-
Ah, sorry if I misunderstood.
re: network alias, that can be one IP by using a /32 mask.