RBAC to Role Mapping - Black List services
-
First time with pfsense.. But I use to use m0n0wall .. well.. 10 years ago.
Back to dealing with script kiddy attacks on home lab and need a more beefy solution.
Current issue:
-
RBAC binding: link to Active directory works. I can login as user and it logs in but says "No page assigned to this user! Click here to logout." which implies my AD goup "pf1_admins" which matches group named for role mapping in router, is not right.. or (to baseline) I set single role mapping "WebCft - All pages" (though I did a baseline of added all roles to that group to baseline). Yes I reboot between each group binding change (but my guess is this warning is more if it has to do refresh after upgrades .. not new accounts/groups). Any ideas on what step I missed in role to AD group (remote) mapping? Or link to RTFM.
-
Black list domain filtering. I use to have a web service I linked to that was "dump all" if on this black list. And I put all servers not in my country + few others. Keep down on rif raff poking. Reason is that I am getting slow / low grade password trolling and DDOS on my router which folds once a day now.
I just need something to setup things to filter down the noise.
-
-
 S stephenw10 moved this topic from Problems Installing or Upgrading pfSense Software on
S stephenw10 moved this topic from Problems Installing or Upgrading pfSense Software on
-
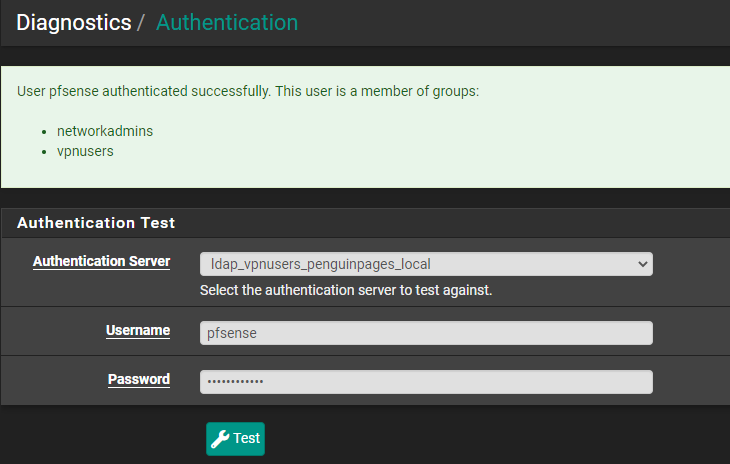
Check Diag > Auth to see what groups it returns.
See: https://docs.netgate.com/pfsense/en/latest/troubleshooting/authentication.html
Checkout the pfBlocker-ng package for blacklist and geo blocking:
https://docs.netgate.com/pfsense/en/latest/packages/pfblocker.html
Steve
-
Thanks for response. Test passes.
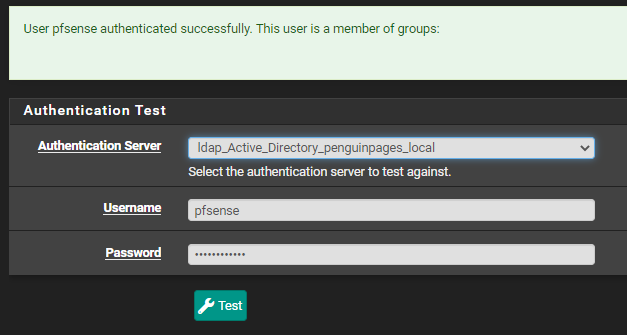
It is some kind of binding to role issue.
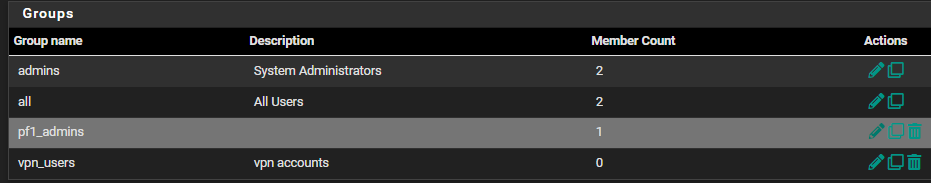
I tried to KISS and just do Webcfg- All Pages..
Login from new private tab
No page assigned.
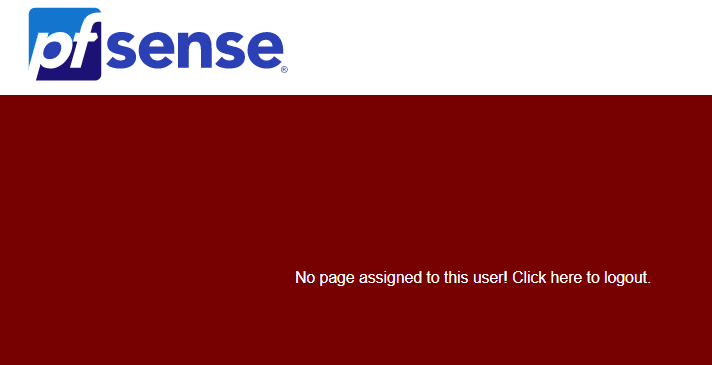
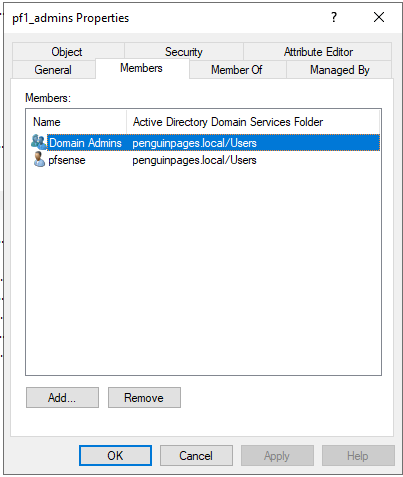
This looks like the logic to bind that user within group "pf1_admins" in AD is not authorized for privilges noted
-
Yeah, it's not returning any groups from AD so it doesn't inherit any privileges in pfSense.
-
I saw same symptom in this recording https://www.youtube.com/watch?v=_xmz1TE0N34 so I did not consider it a baseline / issue.
All three fields on ADSI Editor show short/ group name: (membership shows users with full DN)
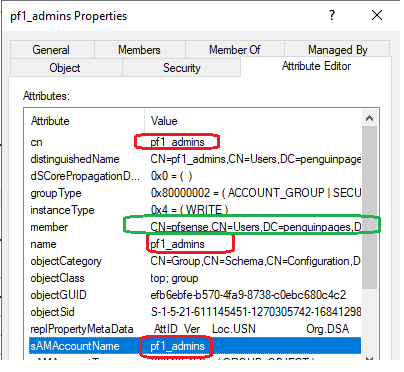
--> Also noted that I did not match AD case changes "sAMAccountName" , neither changes made differenceThe domain context is very flat.. so no OU or sub search to run
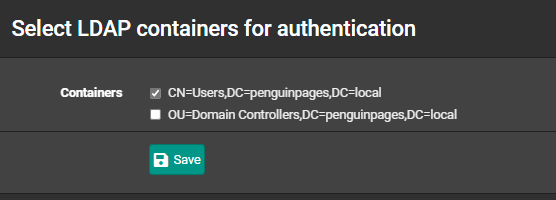
Keep getting in the test auth no returned groups.
Can someone post if this is expected?
Any guidance as to which changes necessitate a reboot (save on time/ baseline)?
For context account of someone to make changes via ansible/TF.. "pf1_admins" is the role I am trying to setup to do that with. Does someone have "Assigned Privileges" list that would match that use case ?PS: Whomever added the Authentication test box into the system <hats off> finally a system to help debut RBAC basics outside beating head and wireshark.
-
@penguinpages said in RBAC to Role Mapping - Black List services:
https://www.youtube.com/watch?v=_xmz1TE0N34
In that video they never actually show the auth test after they have added group membership to the users. But it definitely should return the groups as shown in our own hangout we did on this here: https://youtu.be/n2Z3rr4W2xw?t=2220
It looks like your query is not correct for the group membership perhaps.
I suggest watching that video in it's entirety or at least the LDAP parts. -
Just wanted to respond with close on this issue.
-
DNS and setup of pfBlockerNG-devel plugin helped solve and the youtube videos on it also were help in learning more tuning.
-
AD Auth. Issue was first that I did not have groups named and decriptions matching in AD... which created a bit of rabbit hole.. Then when I just took time to recreate Auth type with AD recommended template, it worked. Thing to know is if you don't get groups respond on query, and can add/ change user group membership and see auth test track those changes.. STOP.. fix AD.. then move on to other things.
Good Return Example: AD group membership matches
Thanks for help and responses to this posting. As I learn more , hopefully I can help others
-