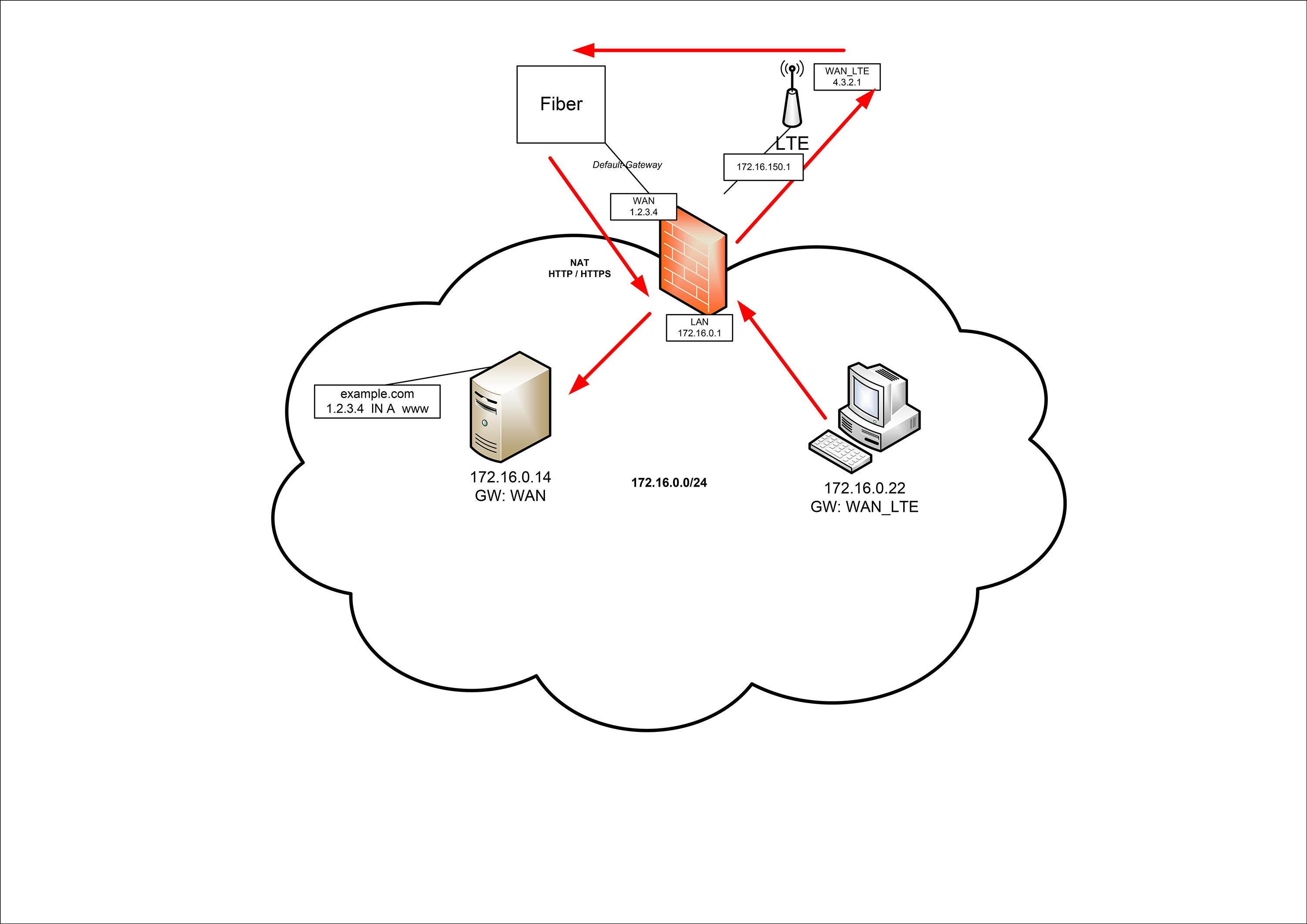
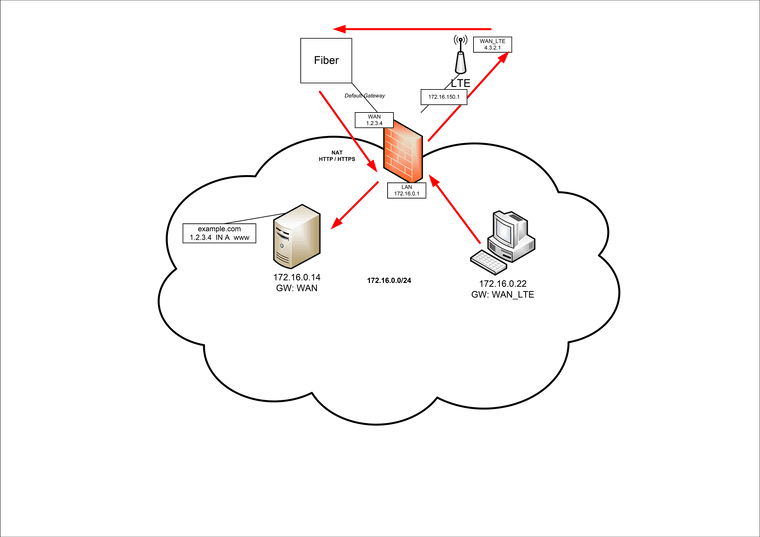
Multiple WAN interfaces - NAT problem
-
Good day together
I have the following problem. I am running a pfSense firewall with 2 WAN gateways. The default gateway goes over a fiber optic line. On this interface there are also NAT entries for the internal network. Further I have a second gateway over LTE which some clients use. This works as far as I can see. But as soon as a client wants to call a URL, which is nated via the primary gateway, the connection blocks. Pinging works but the NAT is not executed. Unfortunately, the LTE modem does not support Bridge Mode.
For illustration purposes, I have created the following image.
I have made the following settings:
- WAN: Block private networks and loopback addresses: Checked
- WAN: Block bogon networks: Checked
- WAN_LTE: Block private networks and loopback addresses: Unchecked
- WAN_LTE: Block bogon networks: Unchecked
NAT:
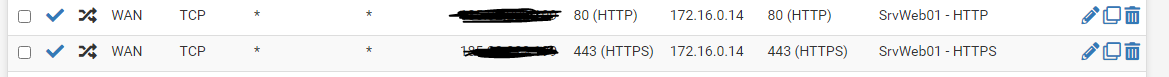
Rules:
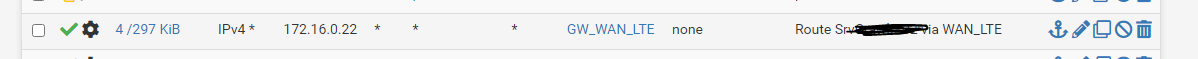
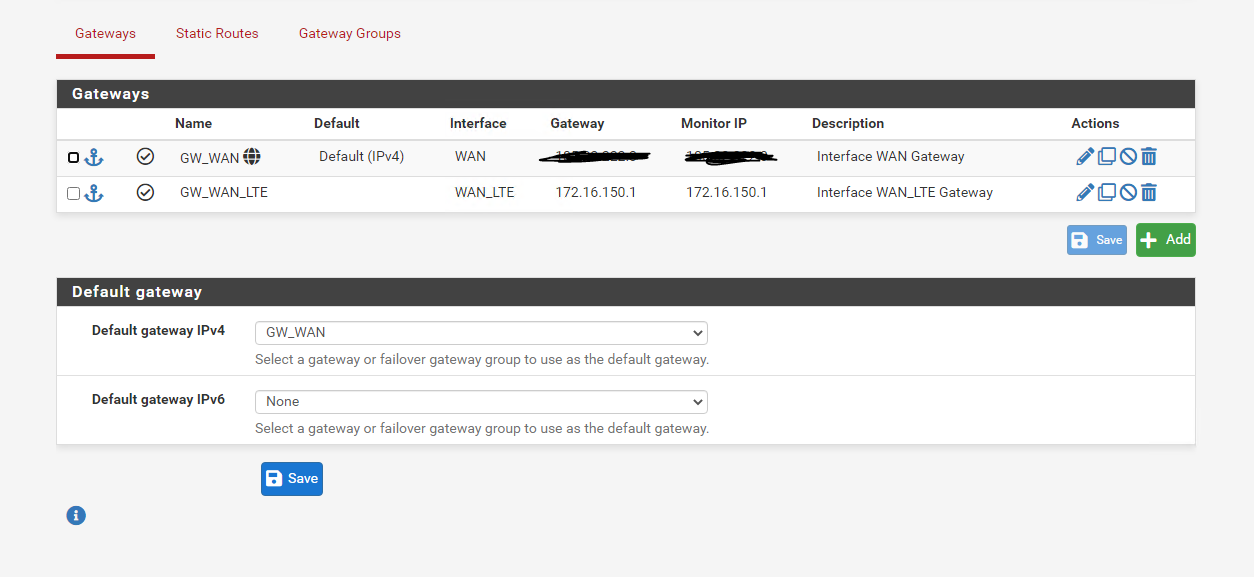
Gateway:
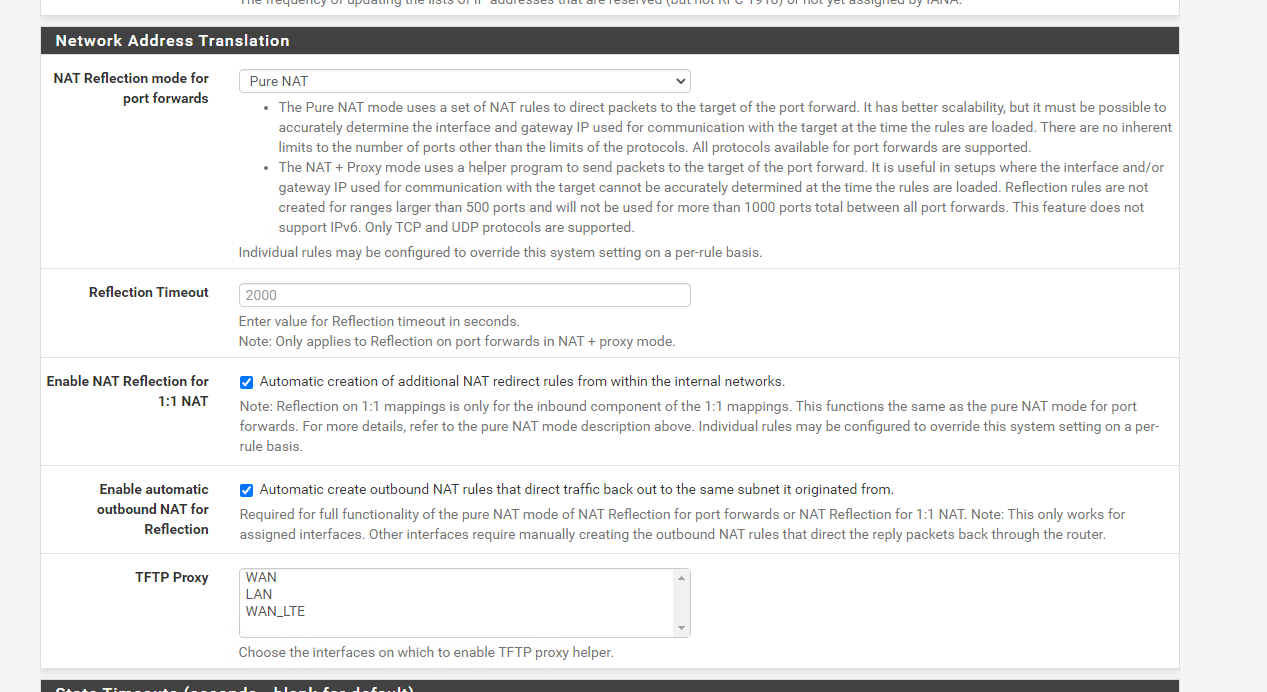
Network Address Translation:
Does anyone have an approach, it seems like the NAT rule doesn't apply.
Thank you and best regards
-
@misterdeeds-0 said in Multiple WAN interfaces - NAT problem:
I am running a pfSense firewall with 2 WAN gateways. The default gateway goes over a fiber optic line. On this interface there are also NAT entries for the internal network. Further I have a second gateway over LTE which some clients use. This works as far as I can see.
So internet works well on LAN devices?
But as soon as a client wants to call a URL, which is nated via the primary gateway, the connection blocks.
Are you talking about a LAN client calling one of the nated address?
Do you use the IP or a host name?WAN_LTE: Block private networks and loopback addresses: Unchecked
WAN_LTE: Block bogon networks: UncheckedThere is no need to have this unchecked as long as there are no incoming connections on the LTE and the modem does masquerading on it.
-
@viragomann Thanks for the answer
So internet works well on LAN devices?
-> Internet works normally. Even if the website is accessed via a client that goes through the default gateway, it works. Only when the client goes via the LTE gateway it does not work.Are you talking about a LAN client calling one of the nated address?
Do you use the IP or a host name?
-> Exactly, I want to use a LAN client to access the web page which is nated behind the public IP of the firewall. use the hostname (DNS) name from the website. But also with the IP the result is identical. The connection is not nated.There is no need to have this unchecked as long as there are no incoming connections on the LTE and the modem does masquerading on it.
-> All right, then I set the checkboxes againDo you have any other ideas? Thanks alot and best regards
-
@misterdeeds-0
The rule you posted above for the source 172.16.0.22 policy routes any traffic to the LTE gateway.
Can't see if there is another rule in place allowing the desired access, but if this rule is applied it can't work at all. -
@viragomann said in Multiple WAN interfaces - NAT problem:
The rule you posted above for the source 172.16.0.22 policy routes any traffic to the LTE gateway.
Can't see if there is another rule in place allowing the desired access, but if this rule is applied it can't work at all.Thanks for the feedback. Here are still all the firewall rules.
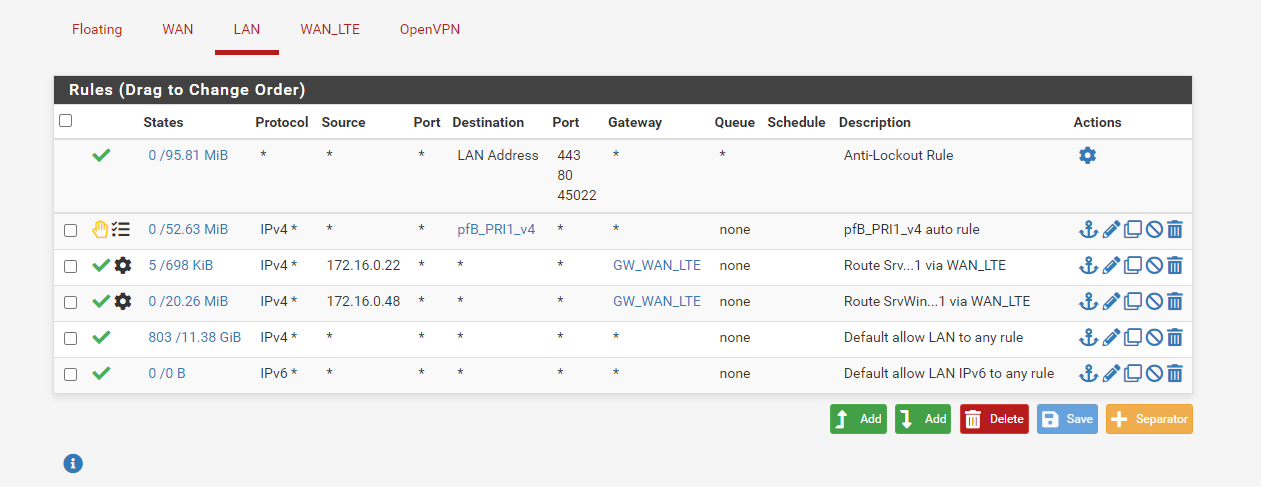
-
@misterdeeds-0
As I mentioned above, you're policy routing traffic to the LTE gateway. What's the sense of this?These rules directs any matching packet to the LTE gateway, hence the concerned IPs are not able to access any local destinations.
So with these rules in place you need an additional for the source IP in question to pass traffic to local destinations, where you don't have to set the gateway option. -
@viragomann said in Multiple WAN interfaces - NAT problem:
As I mentioned above, you're policy routing traffic to the LTE gateway. What's the sense of this?
These rules directs any matching packet to the LTE gateway, hence the concerned IPs are not able to access any local destinations.
So with these rules in place you need an additional for the source IP in question to pass traffic to local destinations, where you don't have to set the gateway option.These clients should only go via the LTE gateway and never via the standard gateway.
I have now created the following rule. Unfortunately, this does not make any difference.
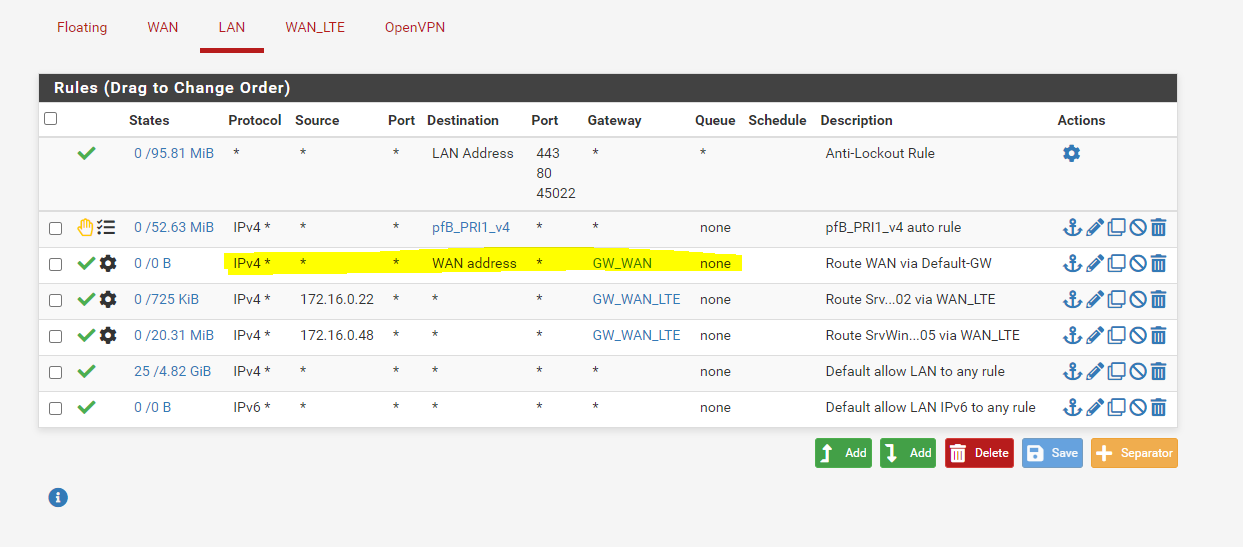
-
@misterdeeds-0
You cannot pass packets to WAN address over the WAN gateway! That cannot work, the packets would never come back.I told you to not touch the gateway option in the rule.
-
@viragomann And what should the rule be if I want the two clients to always go through the LTE gateway but be able to reach the address on the WAN gateway?
-
@misterdeeds-0
Just edit the rule for WAN address and set the gateway to "default".
This rule is applied only if the destination is the WAN address. For all other destinations it is skipped and the next one is probed. -
@viragomann said in Multiple WAN interfaces - NAT problem:
Just edit the rule for WAN address and set the gateway to "default".
This rule is applied only if the destination is the WAN address. For all other destinations it is skipped and the next one is probed.Ok, but how can I define that only these two clients permanently connect to the Internet via LTE gateway?
-
@misterdeeds-0 said in Multiple WAN interfaces - NAT problem:
@viragomann said in Multiple WAN interfaces - NAT problem:
Just edit the rule for WAN address and set the gateway to "default".
This rule is applied only if the destination is the WAN address. For all other destinations it is skipped and the next one is probed.Ok, but how can I define that only these two clients permanently connect to the Internet via LTE gateway?
This do the other two rule with the gateway stated.
However, I assume there client also need to access other internal destinations, for instance the DNS Resolver running on pfSense.
So best practice is to add an alias and add all private networks to it. Call the alias RFC1918. Mine looks like this
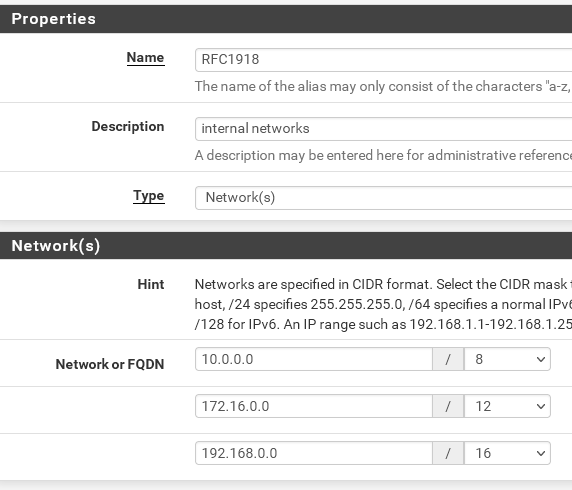
Then edit the policy routing pass rule. At destination check "invert", select "Single host or alias" and enter the alias name (here RFC1918).
With the invert checked means, it applies to any destination, but not the alias and pass the traffic to the LTE gateway.In you case you can also add your WAN address to this alias, so that it is also excluded from passing to LTE.
However, basically there should not be any need to access the WAN IP from inside your network. If you want to use a public FQDN for accessing internal devices, you should better add a DNS override to your local DNS. -
@viragomann Great tip, that's how it works for me. Thanks you very much for the effort!!!