pfSense as initial network filter
-
Hi
I'm a complete newbie with pfSense so please bear with me for any stupid questions.Due to a possible security breach we need to find a way to block devices (pcs/laptops) from accessing our network servers until they have been fully updated and virus scanned. So if a device is connected to the network it is given NO access until it is checked over. It is then allowed to get network access as normal.
I was thinking the Captive Portal service might do this by mac filtering but now not sure this will work. I've done some simple tests on my home network to work out a process and while it seems to work for internet access I can still browse to other pcs even if the device isn't listed as specifically "allowed". I'm also not sure how to block all mac addresses by default and only allow those that are added to the list.
The LAN and WAN interfaces will both be on "private" IP ranges. The LAN interface can be anything we choose but the WAN will be 10.x.y.z as this is the current address range on the network.
So just looking for advice on whether pfSense will actually do what we need and how best to go about this ? Using pfSense to do this may be overkill but we just need a temporary solution in the short term.
Thanks
-
@jarweb pfsense is only able to control devices getting OFF a network. There is no control pfsense really has to keep a device off a local network.
Other than maybe not giving it an IP until their mac has been allowed via dhcp settings, etc.
But if your looking to keep devices off a network until they meet some criteria your looking more like packetfense, and the appropriate network infrastructure.
What is sounds like your asking for is a NAC (network access control) that provides the ability for meeting compliance or auth before a client is allowed to join a network, or a specific vlan.
Is one example that is open source and free way to get into NAC..
@jarweb said in pfSense as initial network filter:
I can still browse to other pcs even if the device isn't listed as specifically "allowed".
This would be what your looking for.
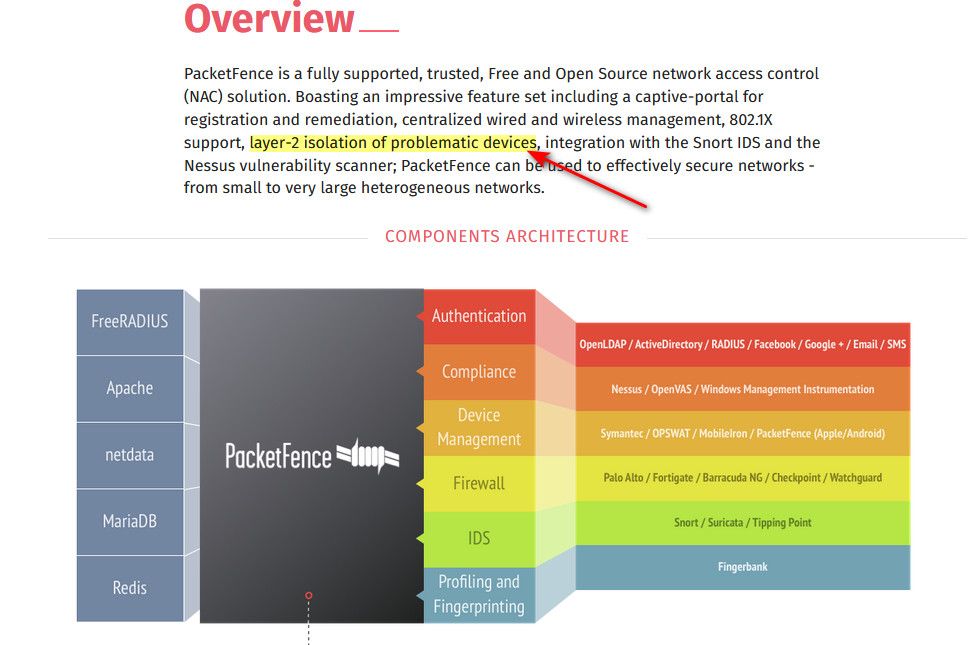
Keep in mind that you would need the appropriate switches and AP to be able to implement such control.
-
Thank you for the recommendation, I have been looking for something that was free and open source.
-
@flat4 said in pfSense as initial network filter:
something that was free and open source.
keep in mind that you do need the appropriate infrastructure - so to be able to actually leverage it, you may need to upgrade/change out some of your switches or AP.. Depending on what you currently are using.
They have a pretty large supported hardware list - but your switch need to support the ability to do stuff.
https://www.packetfence.org/doc/PacketFence_Network_Devices_Configuration_Guide.html
-
@johnpoz Thanks for the reply
Yes, we're looking at the whole network setup so we can implement a proper solution going forward. Lead times on security devices, plus people with the proper skills to set up, is currently quite long so we were hoping for an interim solution just to get us up and running.
If pfSense is not the answer then that's unfortunate, but good to know so I don't spend time investigating if it's just not going to do what we need..
If you think that PacketFence might be an option then I can look into this. But, as you say, will probably need more than just this to allow it to work.
Thanks again.
-
@johnpoz I run cisco 3750 and unifi aps
-
@johnpoz Just a quick follow up to confirm.
So even if we have 2 network interfaces, on different subnets, it's not really possible to use pfSense to filter by mac address (or any other way) for browsing network resources ?
You mentioned there is no control to keep a device off a local network. In theory, even though both subnets are on private IP ranges, the WAN interface would be "sort of" remote, with the LAN interface being the local network interface.Thanks
-
@jarweb pfsense doesn't filter anything by MAC addresses. But you can, however, assign static IP reservations by using the MAC addresses of the hosts on your network(s). Then you can have pfsense do all the filtering that you need, be it on a single network, or multiple networks - physical or virtual.
-
@akuma1x So have I completely misunderstood the mac access control option in Captive Portal ? I thought that this is what it did. You add mac addresses in here to either block or allow access to the network. It might have been cumbersome to do but was hoping it would work in the short term.
-
@jarweb Yes, of course, this is where MAC addresses are used to control access to the captive portal stuff. If you have setup the MAC address table, and set an address to specifically pass, it won't get the authentication screen. You can also do this by IP addresses.
https://docs.netgate.com/pfsense/en/latest/captiveportal/mac-address-control.html
You probably used the wrong term by saying "filtering" in your post, sorry my bad.
-
@akuma1x Sorry, yes, possibly the wrong terminology. But I may still be misunderstanding how it works so would be good to clarify. Should we be able to allow or block specific devices from accessing network resources by adding or removing the mac address from the list in the Captive Portal ? Should this work for SMB access (e.g. using Windows Explorer) as well as web browsers ?
In my initial post I mentioned that it seemed to work when I access web sites (I got the pfSense logon/confirmation page) but I could still browse to pcs on my home network with no apparent restrictions.
Again, I can do more testing, but if it definitely isn't going to work this way then at least I know.
Thanks
-
@jarweb said in pfSense as initial network filter:
So even if we have 2 network interfaces, on different subnets,
Those are not the same network... You can for sure control lan from getting to wan networks..
But you clearly stated..
I can still browse to other pcs even
This is not something pfsense can do
if you have network 192.168.1/24 for example.. You can control access to say 192.168.2/24 but pfsense can not stop 192.168.1.x from talking to 192.168.1.y
This question seems to come like every other day or something.. Pfsense is router, it routes between networks, and yeah it can firewall between network A and network B, or network A and all other networks.. But what it can not do is filter devices on network A from talking to devices on network A..
Have gone over this countless times.. I even went down to the mac level on why this is in a recent thread.
https://forum.netgate.com/post/1041343
If you want to control 192.168.1.x from talking to 192.168.1.y this can be done with what is called private vlans, at the switch level, or AP isolation or Client isolation on AP - this is control at layer 2. If you want to prevent a device from joining network A, and talking to other devices on network A.. Unless it meets specific criteria or auth or come compliance thing like its running a virus scanner or has updated virus list, etc. This is done via NAC..
Now pfsense can control say who it hands out dhcp too, via mac control. You could even prob setup some sort of auth via freerad running on pfsense with your switch for 802.1x control on your infrastructure. Or even maybe put a device on specific vlan - but your switches would need to support being able to do this via radius, etc.
From what you have described, especially with mention of virus scanner running, etc. This would be NAC..
-
@johnpoz Hi, really sorry - I've not been clear.
I have set up a pc with 2 network interfaces on my home network for testing purposes, with pfSense installed
The WAN interface is connected to my home network - on a 192.168.x.y address range
The LAN interface I have connected to a separate small switch and it is set on a 10.0.x.y range. The switch is NOT connected to my home network.
This is similar to what we would need in our office. The WAN interface would be connected to the main network and the LAN we would need to isolate and connect devices to this.
So in this scenario can we use the Captive Portal mac control to allow/deny network access to devices ? If yes, how do we set the default to deny unless a mac address is specifically in the list ? Or is it already set to deny by default ?
Thanks again and sorry for the confusion I've caused.
-
@jarweb yes that would be possible for sure
lan -- pfsense -- other networks.
Pfsense can for sure control lan devices from talking to other devices. But it can not prevent lan device A from talking to lan device B. And could control via mac address devices from getting an IP from dhcp server running on pfsense.
I suggest you read over
https://docs.netgate.com/pfsense/en/latest/captiveportal/index.html
dhcp mac address control
https://docs.netgate.com/pfsense/en/latest/services/dhcp/ipv4.html#mac-address-control
-
@johnpoz Thank you
If I know it should work then I can do some more testing at home to make sure I know how to set the config and then hopefully replicate this in the office.
As I said this is just a stop-gap short term solution until we can get a proper review of the network.
Thanks
-
Yeah, pfSense cannot filter traffic between two devices on the same subnet because that traffic never goes through pfSense. It only passes the switch which is why you must filter it there if you need that.
Steve
-
@johnpoz said in pfSense as initial network filter:
https://www.packetfence.org/doc/PacketFence_Network_Devices_Configuration_Guide.html
Thank you John for sharing.