pfSense with CloudFlare (and WireGuard - soon) - setup AD DS
-
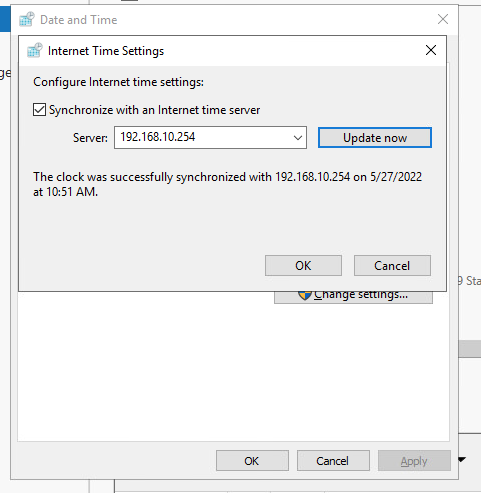
That is what I was doing. I changed the TimeSynch settings in AD DS server to pull from the pfSense - rather than the default of time.windows.com.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
That is what I was doing. I changed the TimeSynch settings in AD DS server to pull from the pfSense - rather than the default of time.windows.com.

This will work fine. Obviously make the NTP stuff in pfSense is set up correctly. But it should be okay out-of-the-box with its defaults.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
Edit: after re-reading your post, most definitely YES, remove those Cloudfare IP addresses from the GENERAL SETUP page. That is NOT where those would go. Instead, they go on the DNS Resolver setup page and apply only after you enable forwarding there.
I would first get everything working with a baseline pfSense setup with regards to DNS. That means DNS Resolver enabled to "resolve" and with "forwarder" NOT enabled. So yes, that would mean for now removing the Cloudfare stuff. Once you get your setup working well, then you can come back and change the DNS Resolver to use the "forwarding" mode by checking that box on the DNS Resolver tab. You NEVER want to enable the DNS Forwarder on pfSense! That is more for legacy stuff. It is a completely different executable (dnsmasq as opposed to unbound which is used for the resolver). To use "forwarding" with the Resolver, simply check the appropriate checkbox on the DNS Resolver setup page. But I would wait on that unless you are highly experienced with DNS setups. Lots of users post here on the forums about DNS problems on pfSense and they are almost always tracked back to incorrect setups. So stay simple and default first. Then make customizations. That way you have a working baseline to return to if a customization goes south.So....currently pfSense is doing ALL DNS and DHCP work. Based on the comments from my posting - the suggestions are to move this to the AD DS (which is what I wanted to do month ago)... LOL, when the round-robin stuff started. So I switched it back (pfSense does everything).
So do you think that I will need to enable or setup DDNS in the AD DS for the CloudFlare ??? or just leave it at pfSense as it is now?
I also want to setup a VPN at some point....will that be at the pfSense level too?
Maybe I made an incorrect assumption. Are you using CloudFare for content filtering via DNS (to block porn and such), or are you using it for a Dynamic DNS Service?
If for Dynamic DNS, then your AD DNS does not figure in here. You simply want CloudFare to identify and update its DNS with the public IP your firewall has at the moment. You configure all of that under SERVICES > DYNAMIC DNS.
But you also show CloudFare DNS server IP addresses on the GENERAL SETTINGS tab of pfSense. What are those there for?
It might also help if you make sure you know the difference between "resolving" and "forwarding" when it comes to the operation of DNS servers. Very different operations, those are. And then dynamic DNS is yet a sort of completely different thing. Some of your questions make it sound to me you are conflating these three when in fact they are quite different.
-
CloudFlare is used for DDNS - not blocking anything. I did it mainly for my HomeAssistant (SmartHome) - I have a sub-domain setup there, which filters traffic from outside my home - to the HomeAssistant server.
I have this in pfSense --
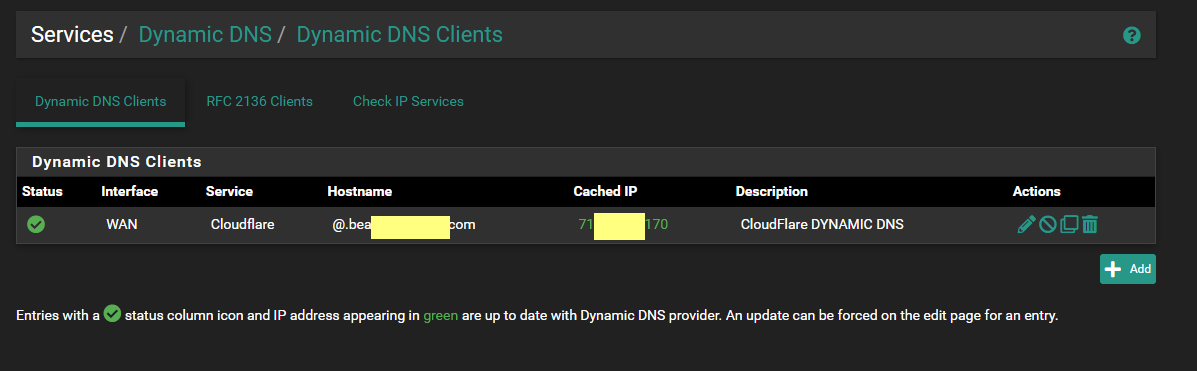
and this in CloudFlare
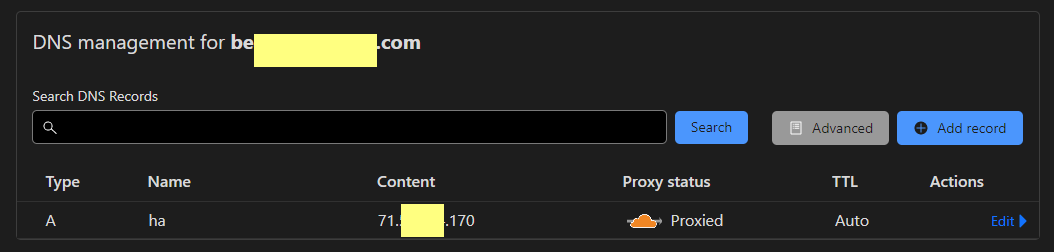
This is all working.
-
Okay, then leave those settings in Dynamic DNS untouched. This setup should be set to route external client requests for your top-level domain to CloudFare which would then respond with whatever your firewall's public IP happened to be at that time.
Oh, and I misspoke in a previous post. If you configure the DNS Resolver in pfSense for forwarding, then "yes" you will want the forwarder's IP address in the SETTINGS > GENERAL SETUP tab of pfSense. But since you only are using CloudFare for the dynamic DNS client, you likely don't want to use forwarding and so you do not need to populate the IP addresses under SETTINGS > GENERAL SETUP.
-
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
Okay, then leave those settings in Dynamic DNS untouched. This setup should be set to route external client requests for your top-level domain to CloudFare which would then respond with whatever your firewall's public IP happened to be at that time.
Oh, and I misspoke in a previous post. If you configure the DNS Resolver in pfSense for forwarding, then "yes" you will want the forwarder's IP address in the SETTINGS > GENERAL SETUP tab of pfSense. But since you only are using CloudFare for the dynamic DNS client, you likely don't want to use forwarding and so you do not need to populate the IP addresses under SETTINGS > GENERAL SETUP.
Now you have me confused.
So, what address do I need where?
CloudFlare DNS are 1.1.1.1 and 1.0.0.1
my pfSense is 192.168.10.254
my AD DS is 192.168.10.250
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
Okay, then leave those settings in Dynamic DNS untouched. This setup should be set to route external client requests for your top-level domain to CloudFare which would then respond with whatever your firewall's public IP happened to be at that time.
Oh, and I misspoke in a previous post. If you configure the DNS Resolver in pfSense for forwarding, then "yes" you will want the forwarder's IP address in the SETTINGS > GENERAL SETUP tab of pfSense. But since you only are using CloudFare for the dynamic DNS client, you likely don't want to use forwarding and so you do not need to populate the IP addresses under SETTINGS > GENERAL SETUP.
Now you have me confused.
So, what address do I need where?
CloudFlare DNS are 1.1.1.1 and 1.0.0.1
my pfSense is 192.168.10.254
my AD DS is 192.168.10.250
Depends on what exactly you want and how your configure your AD DNS. Unless you want to do DNS filtering with CloudFare, then you do not need the CloudFare DNS IP addresses anywhere in pfSense. To do only dynamic DNS, the client setup on that tab is all you need.
Your firewall does not have to talk to CloudFare to resolve your domain (or it shouldn't have to). Your top-level domain, if hosted by an external registrar like CloudFare will be resolved like any other domain. Your AD DNS should really NOT be authoritative for your public top-level domain. Your AD DNS would be authoritative for only your sub-domain.
Who is the registrar for your top-level domain?
-
I bought my domain from GOOGLE. I have already put the CloudFlare entries they sent to me - there. That part is working.
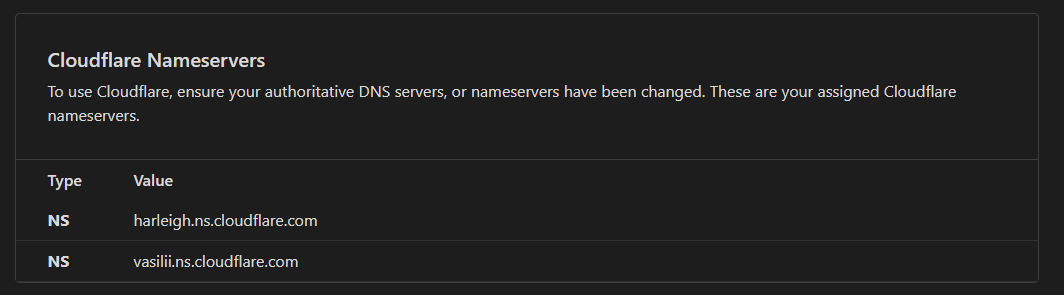
From home and external if I put in browser:
https://ha.{my-domainname}.comIt brings up my HomeAssistant.
I cannot think of - at this time - anything else that I need to access when I am not at home.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
I bought my domain from GOOGLE. I have already put the CloudFlare entries they sent to me - there. That part is working.

From home and external if I put in browser:
https://ha.{my-domainname}.comIt brings up my HomeAssistant.
I cannot think of - at this time - anything else that I need to access when I am not at home.
This is fine. But you do not necessarily need to put any CloudFare DNS IP addresses in pfSense. Here's why:
When any client any place in the world wants to find your domain, it asks its local DNS server (the one the client is configured to use). Let's assume that DNS server is configured as a resolver.
- The DNS server parses out the complete domain name into sections. It starts first with ".com" and goes to the list of DNS roots for the world and says "who is the authoritative server for .com stuff?".
- He gets the reply to "use this one".
- So next, the resolving DNS server asks that specific DNS server who is the authoritative name server for "my-domain" in the ".com" root?.
- In your case, that server will say "CloudFare's DNS server at 1.1.1.1". It will say that because you told Google that CloudFare was your authoritative DNS server.
- So finally, the DNS server who started this resolving job will ask the CloudFare server what is the IP for "my-domain.com"?
- CloudFare at that point would reply with the public IP address of your firewall which that dynamic DNS client keeps updated.
So if you configure the DNS Resolver on pfSense to "resolve", it will do exactly the same thing. It will first ask the DNS root servers and start traversing the tree from there.
Now, where things get sticky is if an external client asked for a hostname from your internal AD domain. In that case you would need to include some info about your sub-domain in your CloudFare record. Most likely you would have a record for the sub-domain that pointed to your AD DNS, but without port forwards and all that hassle, no external client could talk to your AD DNS.
But usually that is not the case. Your internal LAN clients get DHCP and DNS information from the AD Server, and they know to just directly ask the AD DNS service for anything about hosts on your internal domain. Only when they wish to ask about something out on the Internet would the AD DNS server then either resolve it itself (using the steps above), or if configured to forward the AD DNS would ask whatever forwarder it was told to use.
And finally, to close this lesson out, let's consider how "forwarding" works in your setup.
- You configured the DNS Resolver on pfSense to "forward" DNS lookups it is not authoritative for to CloudFare's DNS servers. You do that by checking the "Use Forwarding" checkbox and then putting the CloudFare DNS servers on the SYSTEM > GENERAL SETTINGS page.
- You then go into your AD DNS server and tell it to forward external lookups to pfSense (you put your firewall's LAN IP address in the Forwarder's IP address in the AD DNS setup page).
- A client on your local AD LAN asks for "cnn.com", for example.
- That request goes to your AD DNS server which sees the request is for a domain that it is not authoritative for. So the AD DNS server forwards the request out to pfSense to let the DNS server there figure it out and send back an answer.
- The DNS Resolver on the firewall receives the external lookup request from your AD DNS server. It checks its configuration and sees that it is configured to forward the request out to CloudFare instead of "resolving it" on its own (which it can easily do if configured to do that).
- CloudFare's DNS server receives the request from your pfSense box. It will first check its huge cache to see if it already has the IP address in the cache. If not, it starts the resolving process described back up at the top of this reply. Once CloudFare has the answer (either directly from its cache or via resolving it), it will return the result to pfSense which will in turn send it back to the AD DNS server who finally gives it to the original asking client.
-
Awesome Explaination....

So -- do the following:
- Leave pfSense alone
- Complete the AD DS setup which installs and enables DNS
- Setup the AD DNS and set the port-forwarder setting to my pfSense LAN port
- Install the DHCP role for the AD DS and create a scope (same as I have in pfSense)
- Turn off the DHCP Server service on pfSense

-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
Awesome Explaination....

So -- do the following:
- Leave pfSense alone
- Complete the AD DS setup which installs and enables DNS
- Setup the AD DNS and set the port-forwarder setting to my pfSense LAN port
- Install the DHCP role for the AD DS and create a scope (same as I have in pfSense)
- Turn off the DHCP Server service on pfSense

You got it! That should work for you.
Then later, if you want to get fancy and maybe let CloudFare do content filtering or something (like block porn, known malware domains, etc.), you can configure the DNS Resolver on pfSense to use forwarding mode operation and then put CloudFare's DNS server IP addresses back on the SYSTEM > GENERAL SETTINGS page. But do that ONLY if you want to use CloudFare's filtering stuff. If you don't need the filtering, then go with what we have discussed.
Oh, and even if you do decide on forwarding operation with the pfSense DNS Resolver later, you still want those domain overrides in pfSense for your internal AD domain. You always want those there so pfSense knows who to ask if it needs hostnames. For example, when you display the pfSense ARP table under DIAGNOSTICS, it will try to do reverse lookups on the IP addresses to display hostnames. It needs to know to go ask your AD DNS server about those 192.168.x.x addresses because neither CloudFare nor any other external DNS will have a clue about your internal hosts. Only your AD DNS box knows about them.
-
OK - I forgot a step, and misspoke on another.
- pfSense (remove CloudFlare's DNS settings 1.1.1.1 and 1.0.0.1 ) from SYSTEM >> GENERAL SETUP ?? (i.e. Delete these?) - I had set them to CloudFlare, per a video I watched: https://youtu.be/-uzNMospB5I
-- So you are saying remove these?
That would mean that the DNS would be my ISP, again-- correct?
And So I set this - like so?
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
OK - I forgot a step, and misspoke on another.
- pfSense (remove CloudFlare's DNS settings 1.1.1.1 and 1.0.0.1 ) from SYSTEM >> GENERAL SETUP ?? (i.e. Delete these?) - I had set them to CloudFlare, per a video I watched: https://youtu.be/-uzNMospB5I
-- So you are saying remove these?

That would mean that the DNS would be my ISP, again-- correct?
And So I set this - like so?

Remove the 1.1.1.1 and 1.0.0.1 addresses from the General Settings tab. Leave those lines blank.
That does NOT make your ISP your DNS server, it makes the local
unboundDNS Resolver your DNS server (for the firewall).You still seem to be missing the big picture here. Let's go through this once more:
-
In your Active LAN network you have one or more AD domain controllers that are running the DNS service. Those are the DNS servers for your internal network and are authoritative for that sub-domain and its associated reverse point lookup zones. Your sub-domain is going to be your Active Directory name. In DNS, "authoritative" means the server is where the master copy of the data for that domain lives. The authoritative server "owns" the data for that DNS zone. Other servers may have copies of it, but they do not modify it.
-
You run DHCP on your domain controllers, and those DHCP services are going to give all of your internal LAN clients the IP address of the AD domain controller as the "DNS Server". So all local clients are going to ask the DNS service on the domain controller to find IP addresses for them.
-
For any domain the AD DNS server is not authoritative for (which in practice means anything other than your internal sub-domain), it is going to either attempt to resolve it using the DNS root servers or it is going to forward the request to another DNS server and ask that server to resolve the IP on its behalf. So you have a choice to make on your AD DNS server. Do you want it to "resolve" or "forward"? And if you want it to "forward", you must tell it the IP address of the Forwarder it should use. You can forward to the DNS Resolver on pfSense, or you can forward to any other DNS server on the Internet that you can reach.
-
Your pfSense firewall comes with a DNS resolver binary out-of-the-box called
unbound. It is configured to start and run by default and to "resolve" using the DNS root servers. You don't have to put a single IP address in any DNS box anywhere in the setup for this work. That's why I keep saying "leave those IP address boxes blank". When you leave those IP address boxes empty under DNS Settings on the General Setup tab, then pfSense will automatically ask its internal DNS Resolver (thatunboundexecutable I mentioned) to resolve IP addresses from domain names.unboundis itself a sort of basic DNS server. Everything works just fine with defaults out of the box. Folks, though, seemed determined to shoot themselves in the foot by screwing around with the default DNS setup on pfSense before fully understanding the ramifications of doing that .
. -
You can, if you have a specific reason such as a desire to use an external DNS service for content filtering or some other unique setup, configure the DNS Resolver (
unbound) to "forward" instead of "resolve via the DNS roots". You do that by checking the "Use Forwarding" box and then (and only then) putting the IP address of the DNS forwarding server you wantunboundto ask for IP addresses.
-
I know I am coming across as 'dense' - but I have done this before, and as I stated...something started happening about 7-10 days in. I would start having issues connecting to the Internet. If I would ping a device by name I would get no response (not-found)...but if I did a ping by address with name resolution - it would just give back the IP. I could then get on the AD DS and open DNS - do a root hints refresh and things would work again (7-10 days) or so. Scavenging is enabled for 7 days - so I am thinking that had something to do with it. I got tired of having to do that over and over - so I turned OFF the AD DS server, and eventually deleted it (it was a VM). It was so jacked up - because of all the changes - I figured it would be easier to start from scratch (where I am now).
I also reloaded pfSense and decided to let it handle DNS and DHCP (like my old Netgear ORBI was doing (with a much better FW)).
I am willing to reload pfSense back to Factory Defaults if I can get this working - I just do not want to lose Internet in 7-10 days - one day happened while I was on a SEV-1 Customer Call - That was hard to explain...when I disappeared for 15 minutes when I rebooted everything.
I have watched numerous videos and I have setup many a DC - but usually in a LAB environment at work where It uses the corporate DNS and gateway to get to the Internet. They have their own firewall, etc.
This is for my home where I have my own Cable Modem >> pfSense >> ORBI (in AP mode) for WiFi and everything else is wired.
I am just making sure that I am 'crystal' before I dive in - as messing with the pfSense - I lose ALL INTERNET at home until I get it running again.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
I know I am coming across as 'dense' - but I have done this before, and as I stated...something started happening about 7-10 days in. I would start having issues connecting to the Internet. If I would ping a device by name I would get no response (not-found)...but if I did a ping by address with name resolution - it would just give back the IP. I could then get on the AD DS and open DNS - do a root hints refresh and things would work again (7-10 days) or so. Scavenging is enabled for 7 days - so I am thinking that had something to do with it. I got tired of having to do that over and over - so I turned OFF the AD DS server, and eventually deleted it (it was a VM). It was so jacked up - because of all the changes - I figured it would be easier to start from scratch (where I am now).
I also reloaded pfSense and decided to let it handle DNS and DHCP (like my old Netgear ORBI was doing (with a much better FW)).
I am willing to reload pfSense back to Factory Defaults if I can get this working - I just do not want to lose Internet in 7-10 days - one day happened while I was on a SEV-1 Customer Call - That was hard to explain...when I disappeared for 15 minutes when I rebooted everything.
I have watched numerous videos and I have setup many a DC - but usually in a LAB environment at work where It uses the corporate DNS and gateway to get to the Internet. They have their own firewall, etc.
This is for my home where I have my own Cable Modem >> pfSense >> ORBI (in AP mode) for WiFi and everything else is wired.
I am just making sure that I am 'crystal' before I dive in - as messing with the pfSense - I lose ALL INTERNET at home until I get it running again.
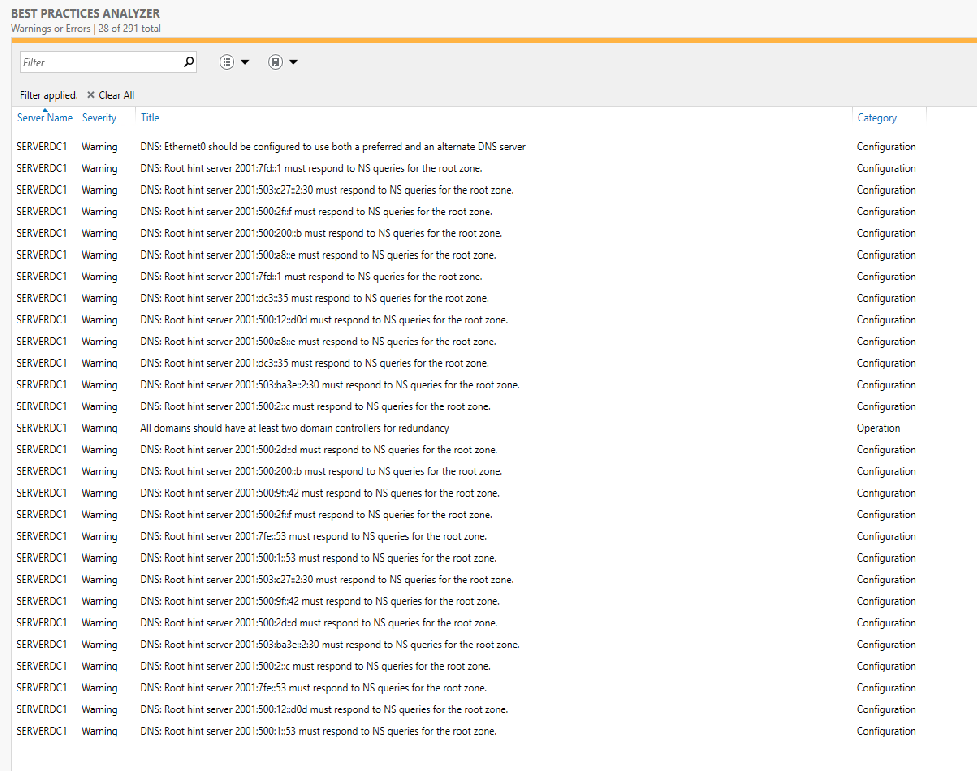
If I understood your original post correctly, when you had this set up the first time you had some things (maybe DHCP and DNS) happening over on pfSense. You just should never do that with Active Directory. AD is very picky about DNS, and it puts some quirky Microsoft stuff in the zones. Much better to let the Microsoft servers handle all DHCP and DNS. In home networks, the best thing in my opinion is to install two domain controllers as virtual machines, and then add the DHCP and DNS feature to both of them as part of the AD setup. With newer Windows Server versions, DHCP can be configured with failover so DHCP won't go down if the DC it is installed on goes down. The secondary DC and its DHCP service will pick up the task. Read up on the Microsoft AD best practices you can find via Google searches. Also run the Best Practices Analyzer wizard on the domain controller. And resolve all the issues it identifies. Some of the other issues you describe sound like the DNS service was not configured 100% correctly in Windows. When you have more than two Windows DNS servers and more than a single domain controller, you have to be careful how you configure the primary and secondary DNS settings on the two domain controllers! Go read the Microsoft docs and heed the advice/info from the Best Practices wizard in Server Manager on the Windows servers.
I have been running the setup I shared with you for years and years without incident all the way back to Server 2008. Let the AD domain controllers do all DHCP and DNS for your LAN and things will work just fine.
The symptom you had of local hosts disappearing out of DNS (you could ping by IP but not by name) indicates DHCP was not updating DNS. That's the big issue with DHCP on pfSense right now. Unless you want the DNS service restarting every time a local host renews its DHCP reservation, you have to disable the auto-registration feature in the pfSense DHCP server. In Windows, using the domain controller's DHCP and DNS services, this auto-registration works wonderfully. Just be sure you tick the checkbox to enable dynamic DNS updates on the DHCP server setup.
So install DHCP and DNS on your domain controllers. Disable the DHCP server on pfSense. Do not use that service on your LAN configuration in pfSense. Make sure DHCP on AD hands out the pfSense LAN interface as the "gateway" and the AD domain controller as the DNS server for all clients.
As for DNS, you can import the DNS roots and let the AD DNS server resolve, or you can leave pfSense at its default setup and tell the AD DNS server to forward zones for which it is not authoritative to pfSense. In my setup, I do the former (my AD DNS does the resolving with no forwarding). Either way you still need to configure the two domain overrides I posted an image of earlier in this thread.
-
Apologies for the delay in a response - I was on VAC last week, and I made myself have a "no-computer-week". lol (see below)
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
If I understood your original post correctly, when you had this set up the first time you had some things (maybe DHCP and DNS) happening over on pfSense. You just should never do that with Active Directory. AD is very picky about DNS, and it puts some quirky Microsoft stuff in the zones. Much better to let the Microsoft servers handle all DHCP and DNS. In home networks, the best thing in my opinion is to install two domain controllers as virtual machines, and then add the DHCP and DNS feature to both of them as part of the AD setup. With newer Windows Server versions, DHCP can be configured with failover so DHCP won't go down if the DC it is installed on goes down. The secondary DC and its DHCP service will pick up the task. Read up on the Microsoft AD best practices you can find via Google searches. Also run the Best Practices Analyzer wizard on the domain controller. And resolve all the issues it identifies. Some of the other issues you describe sound like the DNS service was not configured 100% correctly in Windows. When you have more than two Windows DNS servers and more than a single domain controller, you have to be careful how you configure the primary and secondary DNS settings on the two domain controllers! Go read the Microsoft docs and heed the advice/info from the Best Practices wizard in Server Manager on the Windows servers.
Yeah - I did not understand it either. pfSense was "NOT" doing any of the DNS or DHCP stuff when I was having the problems - but strange things were happening. When I first setup the AD DS on the server - I did the DNS and the DHCP there- In pfSense I had it pointing to 192.168.10.250 (the AD DS IP Address) for DNS and DHCP RELAY was turned ON within pfSense and DHCP SERVER was OFF. It all seemed to work for a while - then I started having issues ever 7-10 days - and a reboot of the pfSense seemed to fix it.
I have been running the setup I shared with you for years and years without incident all the way back to Server 2008. Let the AD domain controllers do all DHCP and DNS for your LAN and things will work just fine.
What I am considering is doing a FACTORY RESET of the pfSense and not change anything except my 3 FW rules - do you think that is how I should do that? (well that and setting the 'names' of things again) -- As I read your steps, I should not put anything here (not even the AD DS information to handle the DNS)???
The symptom you had of local hosts disappearing out of DNS (you could ping by IP but not by name) indicates DHCP was not updating DNS. That's the big issue with DHCP on pfSense right now. Unless you want the DNS service restarting every time a local host renews its DHCP reservation, you have to disable the auto-registration feature in the pfSense DHCP server. In Windows, using the domain controller's DHCP and DNS services, this auto-registration works wonderfully. Just be sure you tick the checkbox to enable dynamic DNS updates on the DHCP server setup.
So install DHCP and DNS on your domain controllers. Disable the DHCP server on pfSense. Do not use that service on your LAN configuration in pfSense. Make sure DHCP on AD hands out the pfSense LAN interface as the "gateway" and the AD domain controller as the DNS server for all clients.
As for DNS, you can import the DNS roots and let the AD DNS server resolve, or you can leave pfSense at its default setup and tell the AD DNS server to forward zones for which it is not authoritative to pfSense. In my setup, I do the former (my AD DNS does the resolving with no forwarding). Either way you still need to configure the two domain overrides I posted an image of earlier in this thread.
I will have to look for the settings you are using. I understand letting AD DS handle the DNS and the DHCP - ideally that is how I want it. But I am sure I had something wrong when I set it all up before - as basically before setting up pfSense (my NETGEAR ORBI was my DNS, my DHCP and my FIREWALL).
-
Well -- yesterday was the day. I made the 'plunge'. I promoted the 2019 server to DC, enabled and setup DNS and DHCP on the server.
I then disabled DHCP Server in pfSense (do I need to turn on DHCP RELAY)?
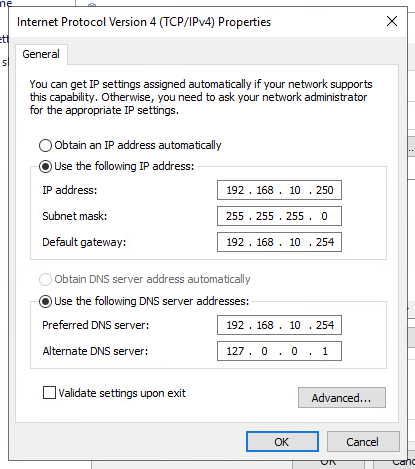
I turned off DNS Resolver in pfSense - and I lost my Internet - everywhere. See below how I have the ETHERNET Adapter in the AD DS server. I went back in and set DNS Resolver to enabled
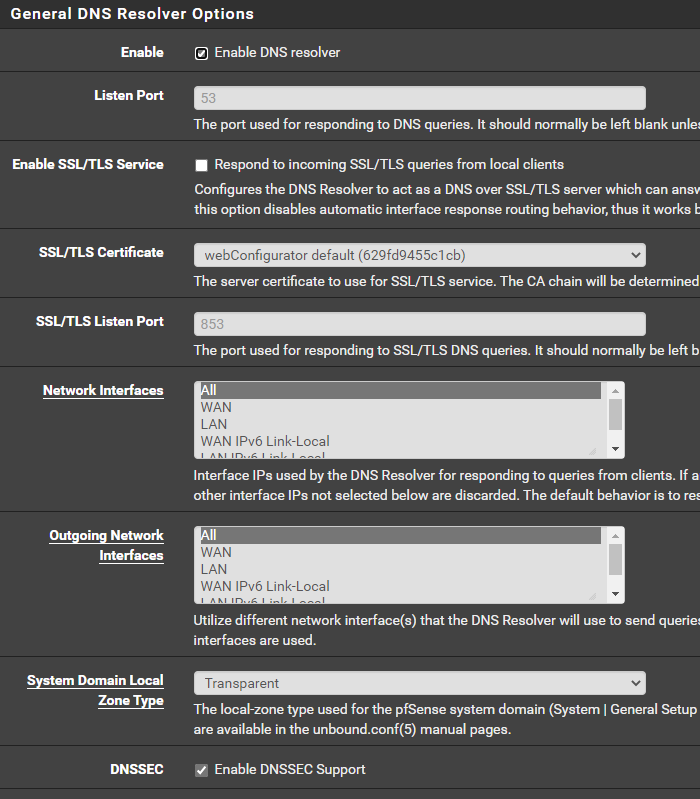
These are the settings in the DNS Resolver (which appear to be the defaults) - only the DNSSEC is checked...nothing else:
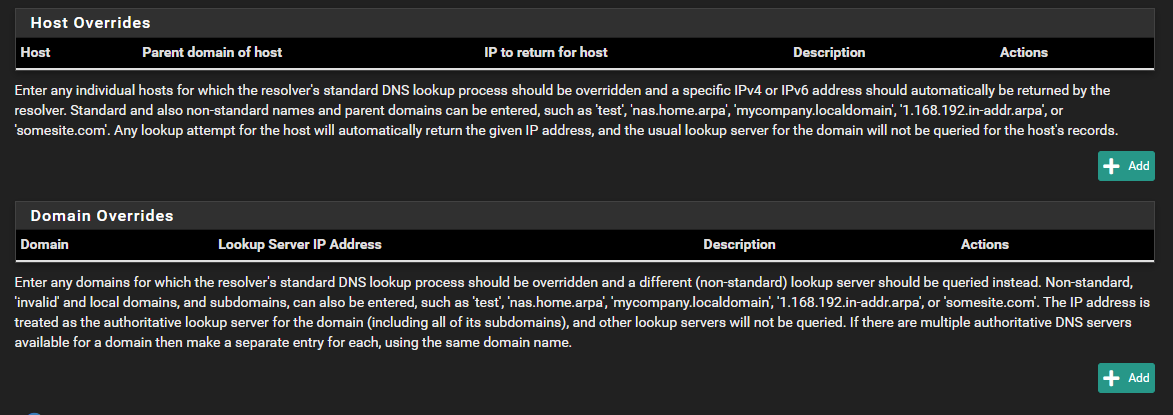
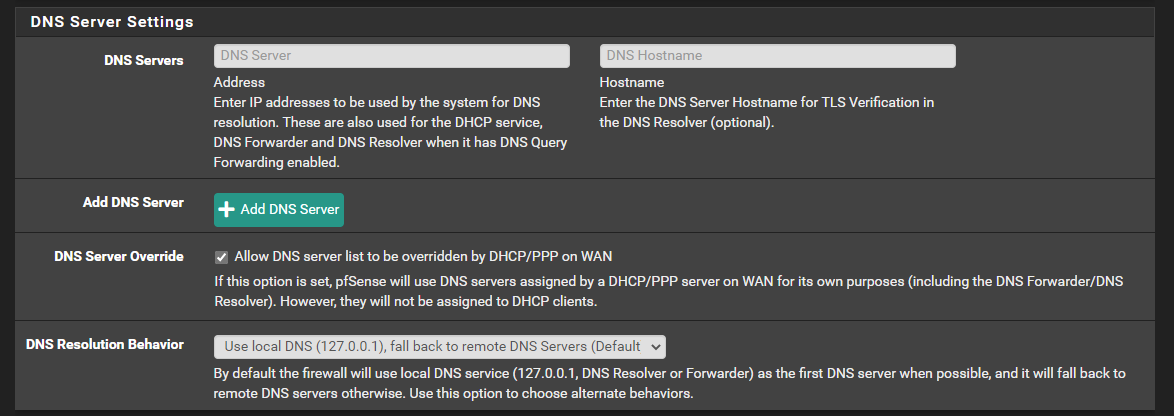
I believe that my next step is to setup these sections?
-
- Do you have your AD DNS server configured to resolve?
- Do you have your AD DNS server's IP address being given out by the AD DHCP server as the DNS for clients to utilize?
- When you say your Internet quits working, can you be more specific. Do you mean browsing or pinging an external host by domain name from a device on your LAN does not work with DNS turned off in pfSense, but it works when DNS in pfSense is enabled? If so, the you do not have things set properly as your either clients seem to be using pfSense for DNS or you do not have the AD DNS server configured to resolve (with roots properly imported).
I promise you this is not difficult at all. You are not getting all of the configuration correct.
-
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
- Do you have your AD DNS server configured to resolve?
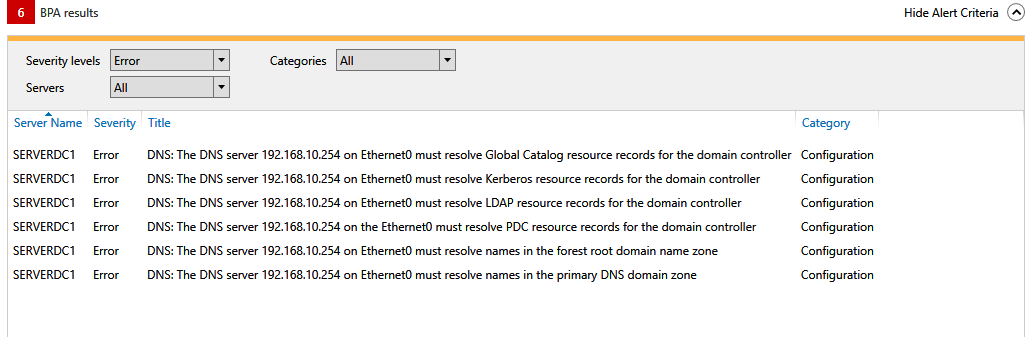
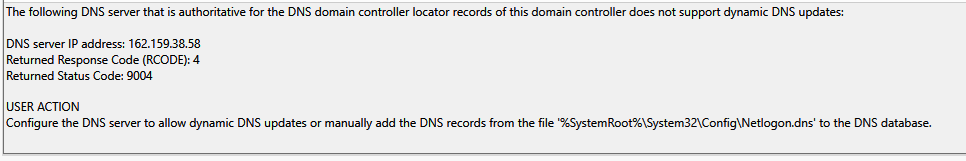
I believe I am. From the AD DNS - not having any issues getting to the Internet. From the DNS tool - all the root hints resolve and I have the following settings (see images)
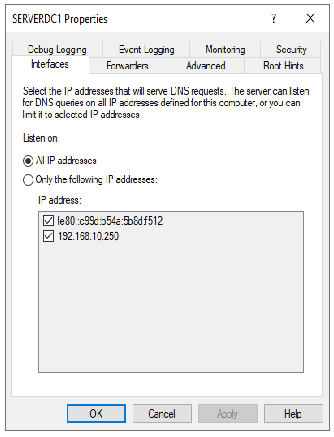
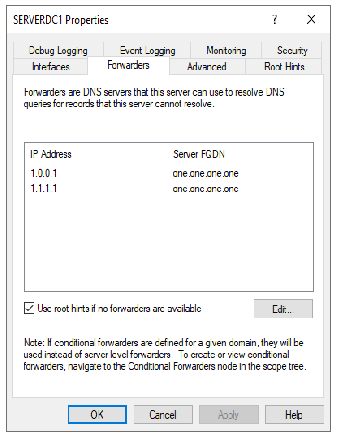
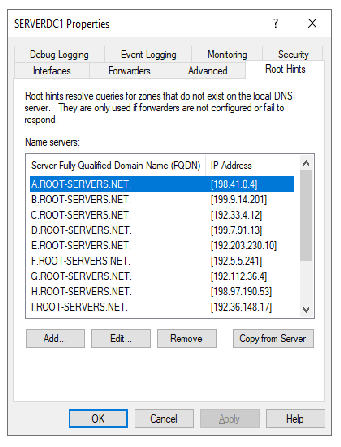
- Do you have your AD DNS server's IP address being given out by the AD DHCP server as the DNS for clients to utilize?
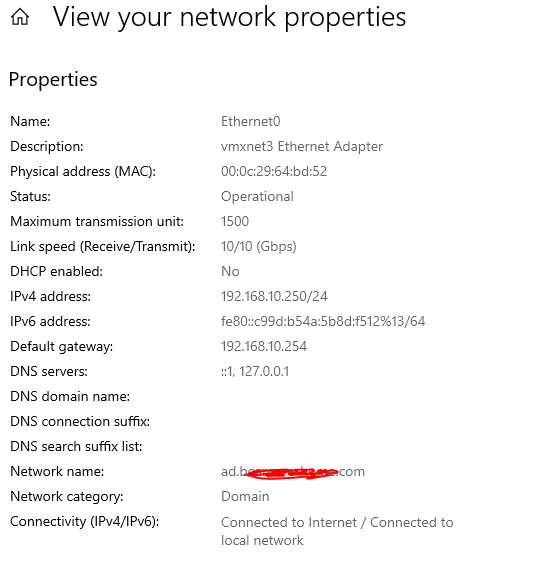
I believe this is working -- this one of my home computers (not joined to the Domain -- yet) - but it looks like it is getting the right IPs ( gateway - 192.168.10.254 = pfSense // 192.168.10.250 = AD DNS )
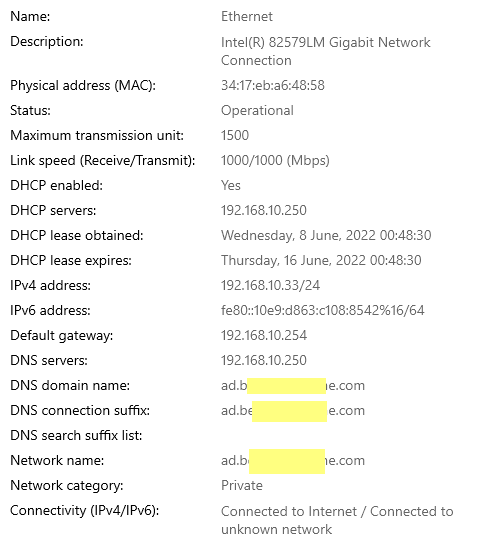
- When you say your Internet quits working, can you be more specific. Do you mean browsing or pinging an external host by domain name from a device on your LAN does not work with DNS turned off in pfSense, but it works when DNS in pfSense is enabled? If so, the you do not have things set properly as your either clients seem to be using pfSense for DNS or you do not have the AD DNS server configured to resolve (with roots properly imported).
When I turned off the DNS Resolver feature in pfSense - then from the machine shown in #2 above - I tried to go to a new website...and I got :page cannot be displayed: error. I also tried to ping google.com and got No Response. Soon as I turned on the DNS resolver on in pfSense and unchecked everything except the DNSSEC (what appears to be the defaults) - everything started working again.
I promise you this is not difficult at all. You are not getting all of the configuration correct.
Yeah - I did not think it was hard either...as I am no idiot...but again, when NETGEAR ORBI was doing all the Routing and DNS and DHCP (never had these problems) - it is just with the pfSense.

If there is anything you want an image of - let me know.
-