pfSense with CloudFlare (and WireGuard - soon) - setup AD DS
-
I wanted to thank all the folks who helped last year when I first tried setting this up - but things went sideways and I put all on the back burner - well I am back trying to set this all up.
[Environment]
pfSense (Stand-Alone ThinClient)
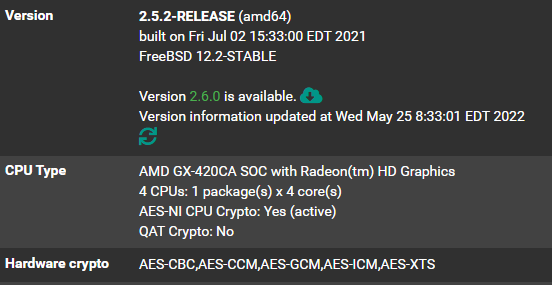
** has DDNS setup and working with CloudFlare and my own Domain.
Domain Controller (ESXi VM)
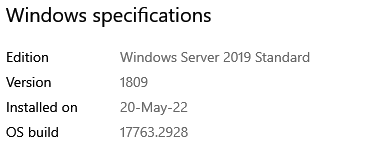
Now I have stood up a new Server 2019 to be the DC. (I gave up on IPv6 - would get it working, only to have it stop in 5-9 days)
As I also have HomeAssistant setup and working - using the CloudFlare and can access it from the outside with 'my' Domain name. I would like to 'not break this'. pfSense currently serves as DNS (resolver) and DHCP to my entire home network. My old ORBI (which was doing this - is in Access Point mode) plugged into the pfSense box (LAN).
My questions are as follows:
- Should I leave pfSense in this role? If so - how do I get rid of all the errors I was seeing related to DNS in the past (examples of what I was seeing before):
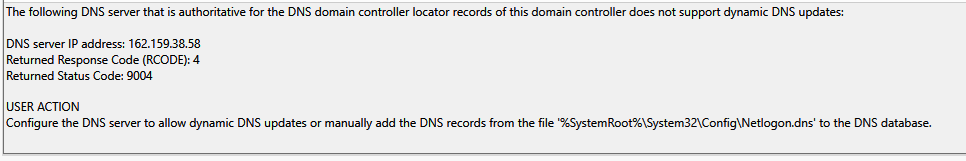
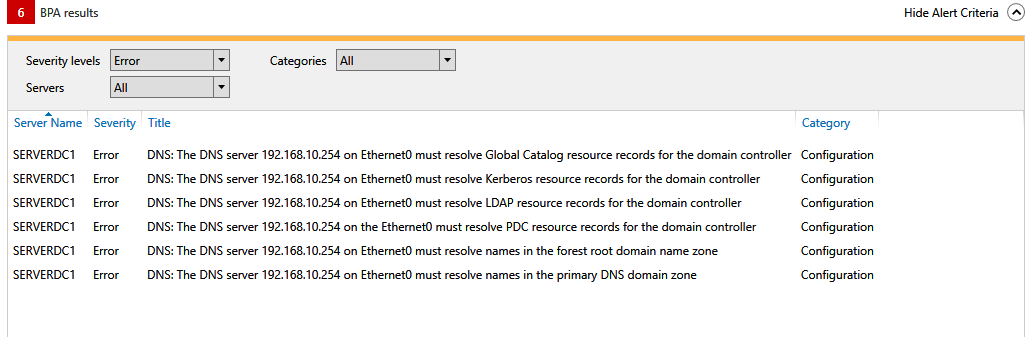
-
What settings should I use in pfSense to make sure I do not break it all when I promote the Server to DC role - as it installs DNS during this process. While I do not have a problem with both performing this role - do not want to create a 'round-robin' if not needed. Currently the server has a static IPv4 address and is using pfSense as it's Gateway and DNS.
-
Should I install the DHCP role to the DC - and if so - how should I setup pfSense?
Thank You in advance.
Curtis
- Should I leave pfSense in this role? If so - how do I get rid of all the errors I was seeing related to DNS in the past (examples of what I was seeing before):
-
I run a Server 2016 domain at home with two DCs and 4 other servers, and the best way to go IMO is to let the DCs handle DNS and DHCP. Set DHCP to give out to the clients, your AD DNS server as the DNS, don't mix it with internet or PFSense DNS. Set the DNS server to forward to your PFSense box what it cannot resolve. I then set PFSense to resolve, no forwarding, not needed, I just let it go to root servers. If you have VLANS via PFSense, set DHCP relay agent on PFSense so that devices in different network segments can find your DHCP server. Your desktops can then pick up GP from your AD, can get other devices on your network resolved from the AD DNS, and with your DC forwarding to PFSense, whatever you have there (Snort, PFBlocker, firewall rules...) can then apply.
-
@Tzvia is 100% correct. When using Active Directory, let it provide both DHCP and DNS services. It is critical that it provide DNS. You can let AD DNS forward to pfSense those queries that it is not authoritative for, but let AD DNS be the authority for your local AD domain and hand out the AD DNS server IP to all of your local clients.
-
Thank you for your input - and that is exactly what I had tried to setup once before - and it appear get caught in some sort of round-robin loop or something and all sorts of 'strangeness'.
Do you have some screen shots of your pfSense and AD DS setup (you can blank your IPs - etc.)?
As I now have my own domain "true top-level' (.com) Domain, I want to use that in my setup. In other words, I want my computers and servers to be {hostname}.{my-domain}.com
In pfSense - should I use DNS RESOLVER or DNS FORWARDER (I think the time I did this where it got in a 'round-robin' lockup I had DSN RESOLVER turned on - and the ENABLE FORWARDER checked.
and then there is the DHCP - I really, really would like to prepare and setup for IPv6...and at one time I had psSense doling out IPv6 addresses -- but they really seemed to be coming from the ISP rather than pfSense. As of right now - IPv6 is doing nothing (except this)
and I have these RULES in my Firewall - to get HomeAssistant to work with my CloudFlare (DDNS) and external access via my domain name.
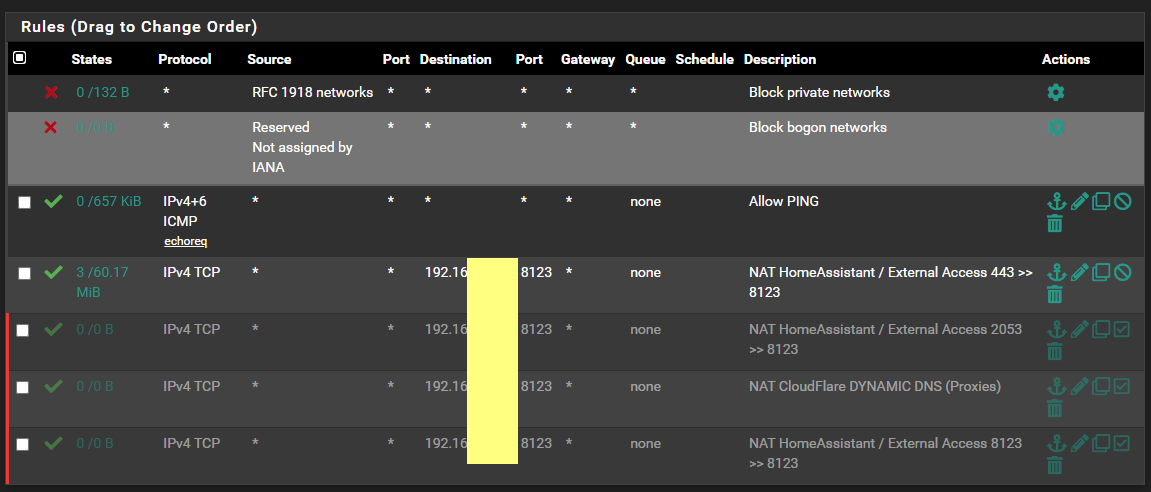
If this will help:
pfSense == 192.168.10.254 (current DHCP Scope is 10.11 - 10.219 )
AD DS == 192.168.10.250I tend to give each room its own IP (in the last octet - for example Kitchen (there are smart appliances) is 10.3x )
Any direction is greatly appreciated.
-
First a question: are you setting up a home network or a business network? Best practice is to have a sub-domain configured for your local network (meaning the LAN behind the firewall) and have your public base domain associated with your public IP. So from the WAN side your domain might be my-domain.com, but on the LAN side in AD you might choose internal.my-domain.com. Here is a link with some best practices in this area: https://techgenix.com/active-directory-naming/. And here is the set of recommended practices from Microsoft itself: https://docs.microsoft.com/en-us/troubleshoot/windows-server/identity/naming-conventions-for-computer-domain-site-ou.
Once you settle on the proper AD domain setup, then add the DHCP and DNS services (features) to your domain controllers. You most definitely want more than one domain controller in most all cases.
Now let's configure DNS on pfSense. Enable the DNS Resolver. It is enabled by default. Do NOT put any IP addresses in the DNS boxes on the GENERAL SETUP page! Leave that at the defaults.
In the screenshots below you will see that I did not originally follow the advice I gave you above. Notice I did not use a sub-domain. I have regretted that starting a few weeks after I set it up until now ...
 . Thus my reason for offering the advice up above. To fix it now requires basically blowing away my AD and starting over. Since it is just a home network, I have not bothered. So, after confessing my original error, let's get you on the right path --
. Thus my reason for offering the advice up above. To fix it now requires basically blowing away my AD and starting over. Since it is just a home network, I have not bothered. So, after confessing my original error, let's get you on the right path --On the DNS Resolver tab click the box to open Custom Options and add the following (put your domain name in place of "themeeks.net", which is mine):
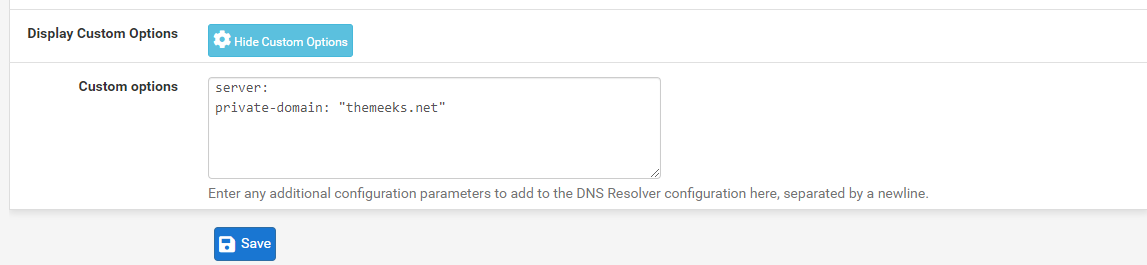
Then scroll down and enter the proper domain overrides into the Domain Overrides section.
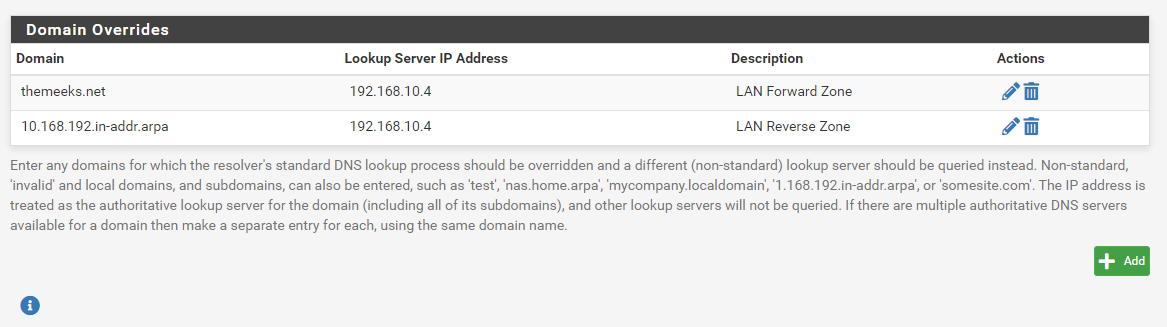
I elected to let my AD DNS servers do resolving. The only DNS service provided by
unboundand the DNS Resolver on pfSense is looking up IP addresses for the local firewall itself. The domain overrides are there so log entries and ARP table listings show my local hostnames.I've experimented back and forth with letting my AD resolve, and then reconfiguring to let my AD forward lookups it is not authoritative for to pfSense where the DNS Resolver there finds the IP. Both ways work. If I wanted to use DNSBL and similar features, I would of course need to let pfSense do all external resolving and only use the AD DNS for the local domain.
-
This is for my home - but I do work from home and test software setups and stuff for my job - so I bring up various servers and such with different configs.
This helps - so I had read one of those articles before, and I was considering using 'internal' or 'ad' for my AD DS (sub-domain). I am trying to document this all as I go along - so hopefully I can share and help others.
I do intend to add a BDC to my network once I am done with the PDC.
Right now pfSense has the CloudFlare DNS settings here (you are saying remove these???) :
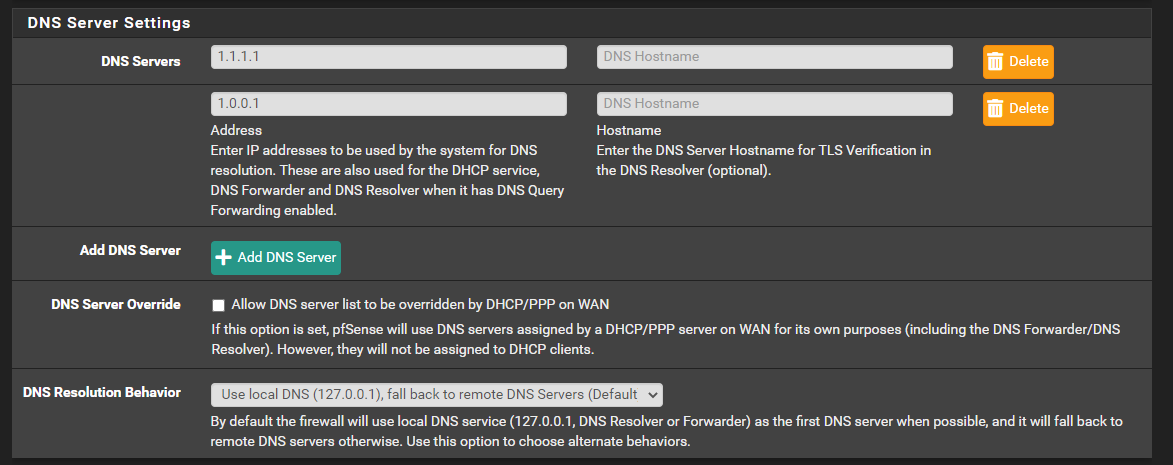
Do I need to put those into the AD DS server instead?
Currently in the CUSTOM OPTIONS of DNS Resolver I have:
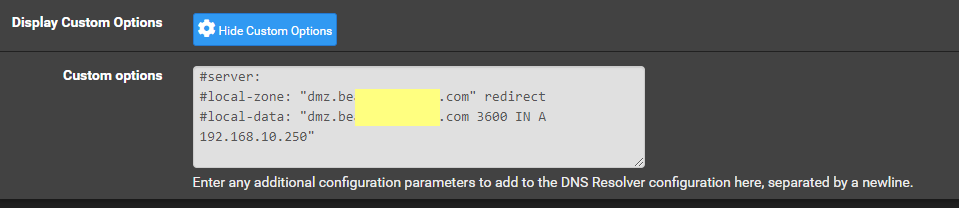
I take it that your Domain Overrides - the 10.4 is your AD DS server?
-
Also do you think it best to move my NTP to the AD DS, and disable this service on the pfSense?
Right now the planned AD DS server is brand new install -- all updates -- static IP and Hostname set. Nothing else in place yet.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
This is for my home - but I do work from home and test software setups and stuff for my job - so I bring up various servers and such with different configs.
This helps - so I had read one of those articles before, and I was considering using 'internal' or 'ad' for my AD DS (sub-domain). I am trying to document this all as I go along - so hopefully I can share and help others.
I do intend to add a BDC to my network once I am done with the PDC.
Right now pfSense has the CloudFlare DNS settings here (you are saying remove these???) :

Do I need to put those into the AD DS server instead?
Currently in the CUSTOM OPTIONS of DNS Resolver I have:

I take it that your Domain Overrides - the 10.4 is your AD DS server?
192.168.10.4 is my PDC, so yes it is also one of the two DNS servers. I only put the one in pfSense because the functionality there is not super critical.
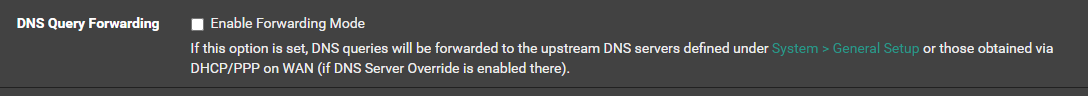
Edit: after re-reading your post, most definitely YES, remove those Cloudfare IP addresses from the GENERAL SETUP page. That is NOT where those would go. Instead, they go on the DNS Resolver setup page and apply only after you enable forwarding there.I would first get everything working with a baseline pfSense setup with regards to DNS. That means DNS Resolver enabled to "resolve" and with "forwarder" NOT enabled. So yes, that would mean for now removing the Cloudfare stuff. Once you get your setup working well, then you can come back and change the DNS Resolver to use the "forwarding" mode by checking that box on the DNS Resolver tab. You NEVER want to enable the DNS Forwarder on pfSense! That is more for legacy stuff. It is a completely different executable (
dnsmasqas opposed tounboundwhich is used for the resolver). To use "forwarding" with the Resolver, simply check the appropriate checkbox on the DNS Resolver setup page. But I would wait on that unless you are highly experienced with DNS setups. Lots of users post here on the forums about DNS problems on pfSense and they are almost always tracked back to incorrect setups. So stay simple and default first. Then make customizations. That way you have a working baseline to return to if a customization goes south. -
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
Also do you think it best to move my NTP to the AD DS, and disable this service on the pfSense?
Right now the planned AD DS server is brand new install -- all updates -- static IP and Hostname set. Nothing else in place yet.
Meh --- 50-50 on that. It is key to have accurate and matching time across AD, so make sure everything points to the same NTP source. In my case I chose to let pfSense be my NTP server, so in the NTP setup on my AD servers I put the IP of my pfSense box as the NTP server to use. But you could certainly also point AD to some Internet time source (even the Microsoft default pool) and then point pfSense to AD as a NTP server source.
-
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
Edit: after re-reading your post, most definitely YES, remove those Cloudfare IP addresses from the GENERAL SETUP page. That is NOT where those would go. Instead, they go on the DNS Resolver setup page and apply only after you enable forwarding there.
I would first get everything working with a baseline pfSense setup with regards to DNS. That means DNS Resolver enabled to "resolve" and with "forwarder" NOT enabled. So yes, that would mean for now removing the Cloudfare stuff. Once you get your setup working well, then you can come back and change the DNS Resolver to use the "forwarding" mode by checking that box on the DNS Resolver tab. You NEVER want to enable the DNS Forwarder on pfSense! That is more for legacy stuff. It is a completely different executable (dnsmasq as opposed to unbound which is used for the resolver). To use "forwarding" with the Resolver, simply check the appropriate checkbox on the DNS Resolver setup page. But I would wait on that unless you are highly experienced with DNS setups. Lots of users post here on the forums about DNS problems on pfSense and they are almost always tracked back to incorrect setups. So stay simple and default first. Then make customizations. That way you have a working baseline to return to if a customization goes south.So....currently pfSense is doing ALL DNS and DHCP work. Based on the comments from my posting - the suggestions are to move this to the AD DS (which is what I wanted to do month ago)... LOL, when the round-robin stuff started. So I switched it back (pfSense does everything).
So do you think that I will need to enable or setup DDNS in the AD DS for the CloudFlare ??? or just leave it at pfSense as it is now?
I also want to setup a VPN at some point....will that be at the pfSense level too?
-
That is what I was doing. I changed the TimeSynch settings in AD DS server to pull from the pfSense - rather than the default of time.windows.com.
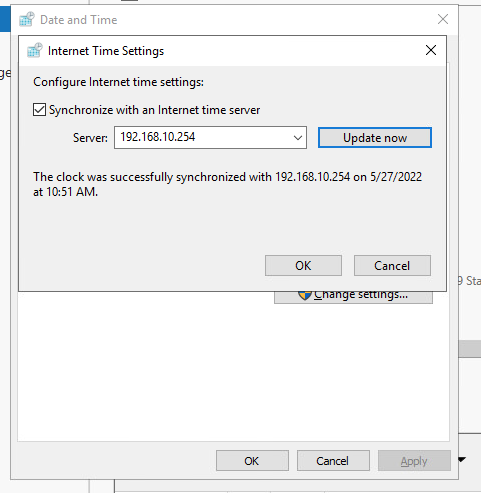
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
That is what I was doing. I changed the TimeSynch settings in AD DS server to pull from the pfSense - rather than the default of time.windows.com.

This will work fine. Obviously make the NTP stuff in pfSense is set up correctly. But it should be okay out-of-the-box with its defaults.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
Edit: after re-reading your post, most definitely YES, remove those Cloudfare IP addresses from the GENERAL SETUP page. That is NOT where those would go. Instead, they go on the DNS Resolver setup page and apply only after you enable forwarding there.
I would first get everything working with a baseline pfSense setup with regards to DNS. That means DNS Resolver enabled to "resolve" and with "forwarder" NOT enabled. So yes, that would mean for now removing the Cloudfare stuff. Once you get your setup working well, then you can come back and change the DNS Resolver to use the "forwarding" mode by checking that box on the DNS Resolver tab. You NEVER want to enable the DNS Forwarder on pfSense! That is more for legacy stuff. It is a completely different executable (dnsmasq as opposed to unbound which is used for the resolver). To use "forwarding" with the Resolver, simply check the appropriate checkbox on the DNS Resolver setup page. But I would wait on that unless you are highly experienced with DNS setups. Lots of users post here on the forums about DNS problems on pfSense and they are almost always tracked back to incorrect setups. So stay simple and default first. Then make customizations. That way you have a working baseline to return to if a customization goes south.So....currently pfSense is doing ALL DNS and DHCP work. Based on the comments from my posting - the suggestions are to move this to the AD DS (which is what I wanted to do month ago)... LOL, when the round-robin stuff started. So I switched it back (pfSense does everything).
So do you think that I will need to enable or setup DDNS in the AD DS for the CloudFlare ??? or just leave it at pfSense as it is now?
I also want to setup a VPN at some point....will that be at the pfSense level too?
Maybe I made an incorrect assumption. Are you using CloudFare for content filtering via DNS (to block porn and such), or are you using it for a Dynamic DNS Service?
If for Dynamic DNS, then your AD DNS does not figure in here. You simply want CloudFare to identify and update its DNS with the public IP your firewall has at the moment. You configure all of that under SERVICES > DYNAMIC DNS.
But you also show CloudFare DNS server IP addresses on the GENERAL SETTINGS tab of pfSense. What are those there for?
It might also help if you make sure you know the difference between "resolving" and "forwarding" when it comes to the operation of DNS servers. Very different operations, those are. And then dynamic DNS is yet a sort of completely different thing. Some of your questions make it sound to me you are conflating these three when in fact they are quite different.
-
CloudFlare is used for DDNS - not blocking anything. I did it mainly for my HomeAssistant (SmartHome) - I have a sub-domain setup there, which filters traffic from outside my home - to the HomeAssistant server.
I have this in pfSense --
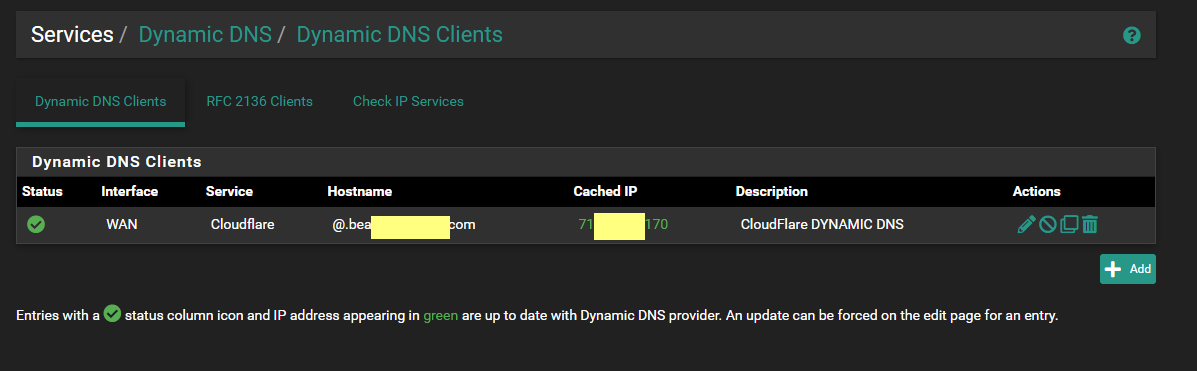
and this in CloudFlare
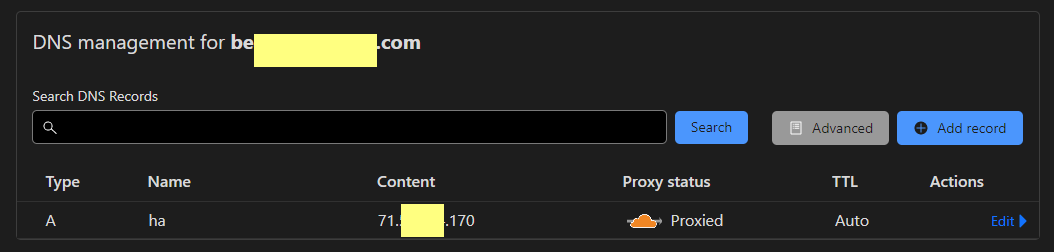
This is all working.
-
Okay, then leave those settings in Dynamic DNS untouched. This setup should be set to route external client requests for your top-level domain to CloudFare which would then respond with whatever your firewall's public IP happened to be at that time.
Oh, and I misspoke in a previous post. If you configure the DNS Resolver in pfSense for forwarding, then "yes" you will want the forwarder's IP address in the SETTINGS > GENERAL SETUP tab of pfSense. But since you only are using CloudFare for the dynamic DNS client, you likely don't want to use forwarding and so you do not need to populate the IP addresses under SETTINGS > GENERAL SETUP.
-
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
Okay, then leave those settings in Dynamic DNS untouched. This setup should be set to route external client requests for your top-level domain to CloudFare which would then respond with whatever your firewall's public IP happened to be at that time.
Oh, and I misspoke in a previous post. If you configure the DNS Resolver in pfSense for forwarding, then "yes" you will want the forwarder's IP address in the SETTINGS > GENERAL SETUP tab of pfSense. But since you only are using CloudFare for the dynamic DNS client, you likely don't want to use forwarding and so you do not need to populate the IP addresses under SETTINGS > GENERAL SETUP.
Now you have me confused.
So, what address do I need where?
CloudFlare DNS are 1.1.1.1 and 1.0.0.1
my pfSense is 192.168.10.254
my AD DS is 192.168.10.250
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
@bmeeks said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
Okay, then leave those settings in Dynamic DNS untouched. This setup should be set to route external client requests for your top-level domain to CloudFare which would then respond with whatever your firewall's public IP happened to be at that time.
Oh, and I misspoke in a previous post. If you configure the DNS Resolver in pfSense for forwarding, then "yes" you will want the forwarder's IP address in the SETTINGS > GENERAL SETUP tab of pfSense. But since you only are using CloudFare for the dynamic DNS client, you likely don't want to use forwarding and so you do not need to populate the IP addresses under SETTINGS > GENERAL SETUP.
Now you have me confused.
So, what address do I need where?
CloudFlare DNS are 1.1.1.1 and 1.0.0.1
my pfSense is 192.168.10.254
my AD DS is 192.168.10.250
Depends on what exactly you want and how your configure your AD DNS. Unless you want to do DNS filtering with CloudFare, then you do not need the CloudFare DNS IP addresses anywhere in pfSense. To do only dynamic DNS, the client setup on that tab is all you need.
Your firewall does not have to talk to CloudFare to resolve your domain (or it shouldn't have to). Your top-level domain, if hosted by an external registrar like CloudFare will be resolved like any other domain. Your AD DNS should really NOT be authoritative for your public top-level domain. Your AD DNS would be authoritative for only your sub-domain.
Who is the registrar for your top-level domain?
-
I bought my domain from GOOGLE. I have already put the CloudFlare entries they sent to me - there. That part is working.
From home and external if I put in browser:
https://ha.{my-domainname}.comIt brings up my HomeAssistant.
I cannot think of - at this time - anything else that I need to access when I am not at home.
-
@bearhntr said in pfSense with CloudFlare (and WireGuard - soon) - setup AD DS:
I bought my domain from GOOGLE. I have already put the CloudFlare entries they sent to me - there. That part is working.

From home and external if I put in browser:
https://ha.{my-domainname}.comIt brings up my HomeAssistant.
I cannot think of - at this time - anything else that I need to access when I am not at home.
This is fine. But you do not necessarily need to put any CloudFare DNS IP addresses in pfSense. Here's why:
When any client any place in the world wants to find your domain, it asks its local DNS server (the one the client is configured to use). Let's assume that DNS server is configured as a resolver.
- The DNS server parses out the complete domain name into sections. It starts first with ".com" and goes to the list of DNS roots for the world and says "who is the authoritative server for .com stuff?".
- He gets the reply to "use this one".
- So next, the resolving DNS server asks that specific DNS server who is the authoritative name server for "my-domain" in the ".com" root?.
- In your case, that server will say "CloudFare's DNS server at 1.1.1.1". It will say that because you told Google that CloudFare was your authoritative DNS server.
- So finally, the DNS server who started this resolving job will ask the CloudFare server what is the IP for "my-domain.com"?
- CloudFare at that point would reply with the public IP address of your firewall which that dynamic DNS client keeps updated.
So if you configure the DNS Resolver on pfSense to "resolve", it will do exactly the same thing. It will first ask the DNS root servers and start traversing the tree from there.
Now, where things get sticky is if an external client asked for a hostname from your internal AD domain. In that case you would need to include some info about your sub-domain in your CloudFare record. Most likely you would have a record for the sub-domain that pointed to your AD DNS, but without port forwards and all that hassle, no external client could talk to your AD DNS.
But usually that is not the case. Your internal LAN clients get DHCP and DNS information from the AD Server, and they know to just directly ask the AD DNS service for anything about hosts on your internal domain. Only when they wish to ask about something out on the Internet would the AD DNS server then either resolve it itself (using the steps above), or if configured to forward the AD DNS would ask whatever forwarder it was told to use.
And finally, to close this lesson out, let's consider how "forwarding" works in your setup.
- You configured the DNS Resolver on pfSense to "forward" DNS lookups it is not authoritative for to CloudFare's DNS servers. You do that by checking the "Use Forwarding" checkbox and then putting the CloudFare DNS servers on the SYSTEM > GENERAL SETTINGS page.
- You then go into your AD DNS server and tell it to forward external lookups to pfSense (you put your firewall's LAN IP address in the Forwarder's IP address in the AD DNS setup page).
- A client on your local AD LAN asks for "cnn.com", for example.
- That request goes to your AD DNS server which sees the request is for a domain that it is not authoritative for. So the AD DNS server forwards the request out to pfSense to let the DNS server there figure it out and send back an answer.
- The DNS Resolver on the firewall receives the external lookup request from your AD DNS server. It checks its configuration and sees that it is configured to forward the request out to CloudFare instead of "resolving it" on its own (which it can easily do if configured to do that).
- CloudFare's DNS server receives the request from your pfSense box. It will first check its huge cache to see if it already has the IP address in the cache. If not, it starts the resolving process described back up at the top of this reply. Once CloudFare has the answer (either directly from its cache or via resolving it), it will return the result to pfSense which will in turn send it back to the AD DNS server who finally gives it to the original asking client.
-
Awesome Explaination....

So -- do the following:
- Leave pfSense alone
- Complete the AD DS setup which installs and enables DNS
- Setup the AD DNS and set the port-forwarder setting to my pfSense LAN port
- Install the DHCP role for the AD DS and create a scope (same as I have in pfSense)
- Turn off the DHCP Server service on pfSense
