Inter VLAN routing problems...
-
Looking for some expert pfsense magic... no one on Reddit or anywhere else seems to have the solution. Lots of questions, no answers. Here goes...
I have a Netgate 1100 appliance running pfsense with a L2 switch sitting behind it (Cisco 2960CG) trunking 3 VLANs... all three VLANs are trunking properly with pfsense and all devices in all VLANs can get out to the Internet; however, I can't route between VLANs. I've tried adding "allow any any" ACLs on the VLAN interfaces, but no luck. I can ping the pfsense VLAN interfaces from each VLAN without any problem, but can't reach other hosts on those VLANs. I really only want to do this so I can remotely manage the Cisco switch from a Windows PC w/ ssh via PuTTY. I tried to monitor the FW logs while attempting connections, but there's nothing showing up. Seems like a routing problem...
Any ideas?
-
@jguere said in Inter VLAN routing problems...:
Seems like a routing problem...
No unless you were policy routing traffic out vpn or wan gateway, the default routing table of pfsense knows all the networks its attached to.
I tried to monitor the FW logs while attempting connections
Well by default pfsense would log blocked traffic - so if allowed it wouldn't be logged..
What are the rules on your source vlan your trying to ping another vlan from? Common mistake users have is policy routing.
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#bypassing-policy-routing
Can you say from vlan A ping pfsense interface on vlan B?
Other common issue is firewall on the host your trying to ping.. Sniff (packet capture under diagnostics) on your destination vlan interface, now ping some host in from your source vlan.. Do you see pfsense send on the ping to your destination IP.. If so then its a firewall on the host your trying to ping, or that host is not using pfsense as its gateway. Or that host has a mask wrong and never sends the traffic back to pfsense because it thinks that IP pinging it is local to its network.
Btw it can not be any rules on the destination vlan tab, since those could be nothing.. The return traffic would be allowed by the state created when the traffic was allowed on your source vlan interface of the traffic.
Do you have any rules in floating?
-
@johnpoz Total rookie error! I don't know how I overlooked this, but I failed to set a default gateway on the Cisco switch... problem solved!
-
@jguere said in Inter VLAN routing problems...:
ut I failed to set a default gateway on the Cisco switch... problem solved!
No - that would have nothing to do with anything.. You clearly stated.
with a L2 switch sitting behind it (Cisco 2960CG) trunking 3 VLANs
If your vlans were on pfsense, and you were running your L2 on your switch - switch only needs a gateway for it to get to the internet.
If your switch was routing (which an L2 doesn't even do), then pfsense wouldn't have a clue to the vlans.. And there would only be a transit network between your switch routing and pfsense.
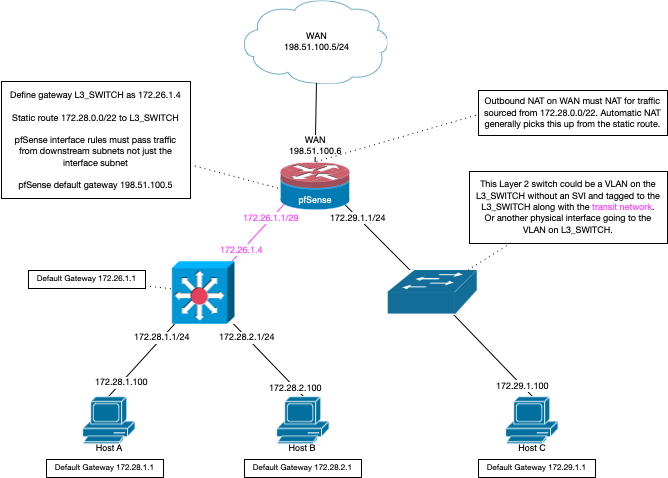
-
@johnpoz the switch needed a gateway for the Mgmt interface to respond to ICMP requests. I was trying to ping from a workstation to the switch's Mgmt interface.
-
@jguere that is not what you stated
I can't route between VLANs
Glad you got it sorted, but nobody can actually help if you do not give accurate description of what your trying to do exactly, and what is not working.
but can't reach other hosts on those VLANs.
Has zero to do with a L2 switch and its gateway for its management IP so you can talk to it from other vlans.