pfSense with OpenWRT Guest logon with VLAN
-
Hmm, interesting. I would advise not making any changes until you get the VLAN/VAP config nailed down. It could easily confuse things further.
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
Hmm, interesting. I would advise not making any changes until you get the VLAN/VAP config nailed down. It could easily confuse things further.
Sorry for my absence. We had a death in the family (expected).
Agree with your statement. I had backups and am doing the secondary testing on my #2 spare (that I was offering up).
So, back to where we were:
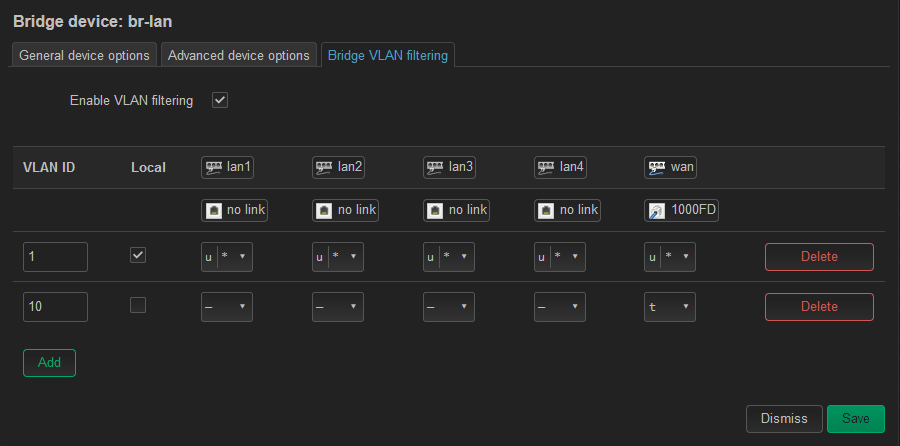
- bridge VLAN filtering is applied per your configuration
- no lockout, config holds
- system auto creates br-lan.1
- GuestTest Interface no longer gets a DHCP address.
New discovery:
- even though I have the Guest WLAN1-1 linked to the "GuestTest" Network interface I can log onto the Guest Network successfully - WTF? But on closer look, it is getting an address on the LAN network 192.168.1.x. I do now have the Local unchecked for the VLAN.10 I'm not sure how?
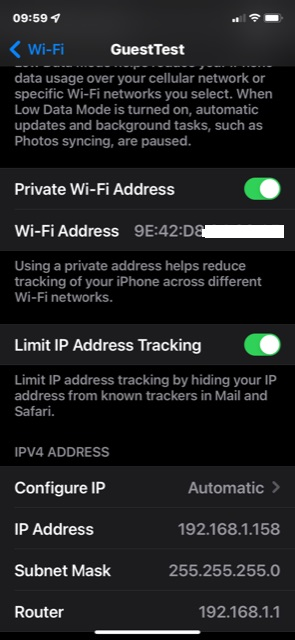
Here are the results you asked for from ip-bridge:
I expected br-lan.1 and br-lan.10port vlan-id lan4 1 PVID Egress Untagged lan3 1 PVID Egress Untagged lan2 1 PVID Egress Untagged lan1 1 PVID Egress Untagged wan 1 PVID Egress Untagged wlan0 1 PVID Egress Untagged br-lan 1 PVID Egress Untagged wlan1 1 PVID Egress Untagged wlan1-1 1 PVID Egress UntaggedOne last piece of information:
I noticed when you had me create the VLAN filtering, I had the br-lan.10 created prior and when I configured the 1 and 10 VLANs in filtering and set the tag/untag PVID the system auto created the device for br-lan.1. So as I was putting this test box back in config, I tried to delete the br-lan.10 and see if it would auto create both the .1 and .10 devices... it does not. And it goes into lockout and I have to revert. I don't expect that to make sense, but I hope my explanation is clear. -
Ok, I spent some time looking at this yesterday. I fired up OpenWRT on an 1100, which I haven't tried in a while. It's the same target (mvebu) and includes much of the same hardware as the WRT3200ACM. Crucially including the same type of Marvel e6XXX switch.
I was able to observe exactly the same things you are seeing. It's broken!
Tellingly when you enable bridge VLAN filtering you should have to reassign the LAN interface to the auto-generated vlan device, br-lan.1 here. But you don't. And in fact if you do you will lose connection. I've yet to find a way to actually see how the switch is configured but it's almost certainly failing to add the internal port as a tagged member of those VLANs. Which is why any additional VLANs fail to pull an IP. And also why you can end up with both interfaces in the same subnet since all VLANs that are added as 'local' end up untagged to the same internal port. Though presumably that port uses PVID 1 so one way traffic...
Luckily you are not really using the switch, you only need to get a VLAN interface passed out to the WAN and be available as an interface to attach the VAP.
An additional complication here is that at some point in the future the OpenWRT stable release may become unbroken at which point your current config will stop working because LAN would then need to be assigned as the VLAN. So I recommend using a config with bridge vlan filtering disabled at least for now.There are at least two configs that should work:
As I initially described, creating a vlan on eth0. Unclear if the vridge is required there for the wifi to work. I suspect it isn'tOr creating a VLAN on the WAN port, so:
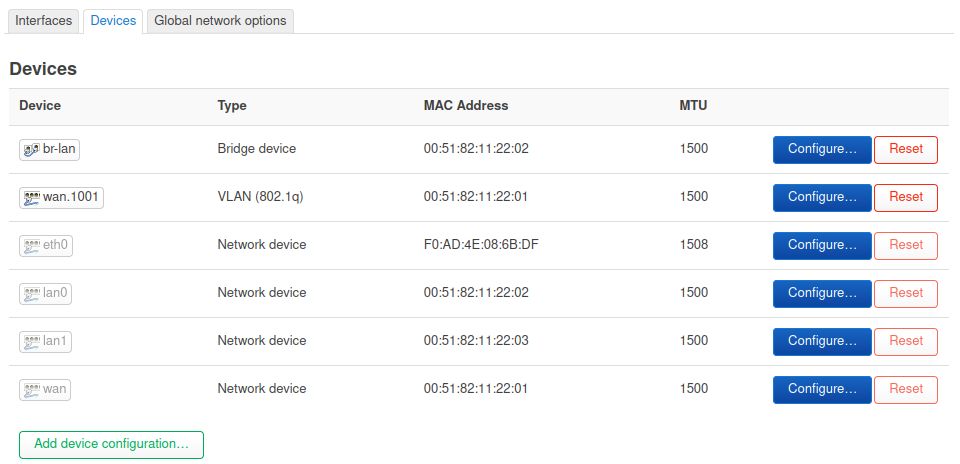
I'll try to confirm that with a wifi interface when I can.
Steve
-
@stephenw10 Thanks Steve!
I've killed the VLAN filtering on br-lan and removed the created/auto created br-lan.1 and br-lan.10
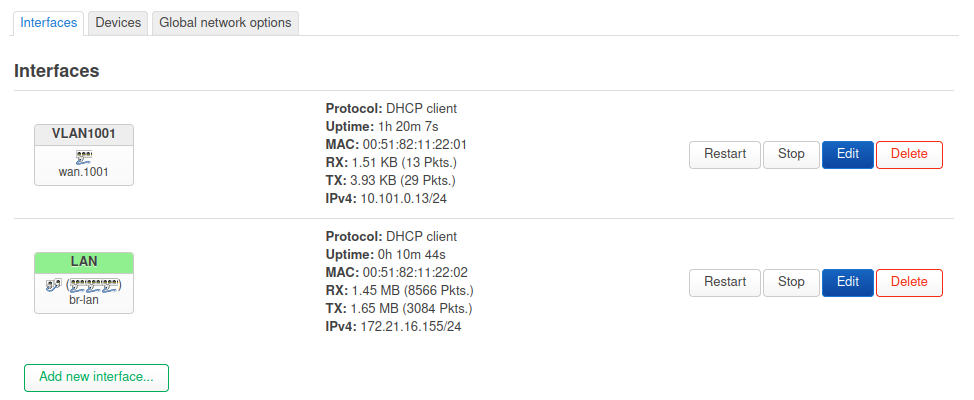
I've put my VLAN 10 onto the wan device as wan.10
Assigned the new wan.10 as the base device for the GuestTest interface. (as a DHCP client)GuestTest gets an IP from the appropriate pfSense network and packets flow on the interface.
I still cannot get a full logon to the Guest WiFi at WLAN1-1.The wireless device MAC shows as an Associated Station on the GUI, but after the login passes auth, it just stalls. On the wireless device the connection just pinwheels.
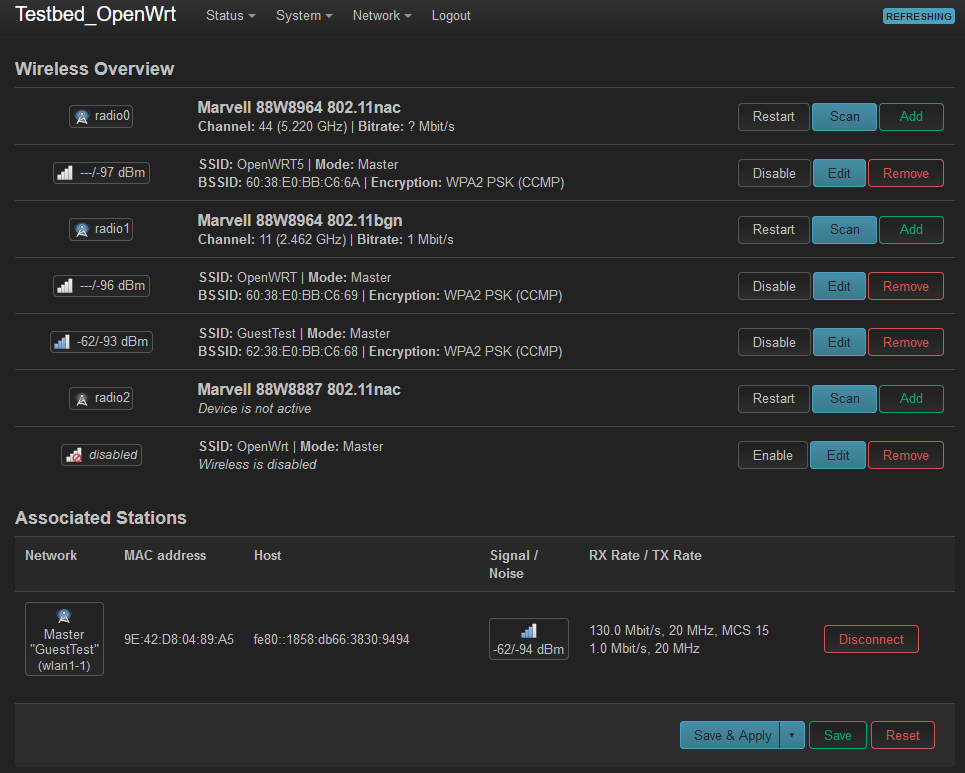
root@Testbed_OpenWrt:~# logread -f Mon Jun 6 09:08:39 2022 daemon.info hostapd: wlan1-1: STA 9e:42:d8:04:89:a5 IEE E 802.11: associated (aid 1) Mon Jun 6 09:08:39 2022 daemon.notice hostapd: wlan1-1: AP-STA-CONNECTED 9e:42: d8:04:89:a5 Mon Jun 6 09:08:39 2022 daemon.info hostapd: wlan1-1: STA 9e:42:d8:04:89:a5 RAD IUS: starting accounting session 661FAB1509F64A01 Mon Jun 6 09:08:39 2022 daemon.info hostapd: wlan1-1: STA 9e:42:d8:04:89:a5 WPA : pairwise key handshake completed (RSN)I'll back out and try the eth0 path.
-
Mmm, I guess it needs the bridge to add the wireless then and doesn't get it without the DSA backend bits.
As an alternative you could use a current snapshot. I can confirm that in yesterdays snapshot the DSA setup works (almost) exactly as described in the docs. There's a bug in 21.02.3 for mvemu and it's now fixed.
The resulting bridge looks like you might expect:
root@OpenWrt:/# bridge v port vlan-id lan1 1 PVID Egress Untagged lan0 1 PVID Egress Untagged wan 1 PVID Egress Untagged 1001 br-lan 1 1001 wlan0 1 PVID Egress Untagged wlan0-1 1001 PVID Egress Untagged root@OpenWrt:/# uname -a Linux OpenWrt 5.10.115 #0 SMP Sun Jun 5 14:58:48 2022 aarch64 GNU/LinuxSteve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
As an alternative you could use a current snapshot. I can confirm that in yesterdays snapshot the DSA setup works (almost) exactly as described in the docs. There's a bug in 21.02.3 for mvemu and it's now fixed.
Steve,
I am sorry for the lack of response yesterday. Had family issues on my mind and let myself go down a rabbit hole.... I should have known better. I did assign the VLAN 10 to the eth0 device and again the interface lost connection. So I went after the Snapshot route you spoke of (that turned into a rabbit hole).
I loaded the snapshot for June 6 and it appeared I had bricked the router. I did the power switch dance and got back to the good partition and tried again as a factory overwrite. Same outcome. Played the power switch cycle again and went back to Linksys, then the factory overwrite snapshot... no response. Surely there is something wrong with the other partition... nope, I was just not thinking clearly. Took the case apart and got my TTL cable out. Was all setup to recover that partition and watched it boot up to a full install. ??? Then I realized that they don't include LuCI in the snapshots... put the case back together, bodged up a connection to the wan interface and loaded LuCI. All's well, I wasted a couple of hours.
I have doctor appointments this morning and will get back on this after I get home... -
@ramosel That is a lot of fiddling for something as simple as assigning a ssid to vlan ;)
And its not even a wifi 6 AP - you know you could pick up a wifi 6 lite model from unifi for $99 ;) Clickity Clickity whatever vlan ID you want to be on.. And it mounts in the ceiling and poe as a AP should be not some ancient relic from by gone days.
-
@johnpoz said in pfSense with OpenWRT Guest logon with VLAN:
$99 ;) Clickity Clickity
But where's the fun in that?

And, yes, sorry @Ramosel, I should have mentioned that LuCI is not in snapshots. I think I also installed luci-ssl separately. And had to install ath9k and the required WPAD stuff since the Espressobin has no wireless hardware by default.
I was looking through the bug list and couldn't find any one thing that matched this exactly. Super frustrating though when you're doing everything right and it turns out a bug stopped it working.
Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
But where's the fun in that?
True - but it works without frustration. And now can spend time using my wifi vs trying to get it to work.. And you can barely see it up in the ceiling vs some blue monster sitting in the corner..
I think I'm just getting old ;)
My idea of fiddling these days is running beta firmware on my AP... if something doesn't work, I roll back.. 6.2.19 which is suppose to make iot connections on 2.4 better. Not so much - had bulbs not turning off when told.. Rolled back to 6.2.18 - this is my idea of fiddling these days ;) hehehe
I reported on their forums what make and model of the bulbs, and what AP I was on.. But haven't gotten around to setting up syslog and sending specific logs there.. They have plenty of other people doing that.. It was too much fiddling ;)
-
@johnpoz said in pfSense with OpenWRT Guest logon with VLAN:
@ramosel That is a lot of fiddling for something as simple as assigning a ssid to vlan ;)
And its not even a wifi 6 AP - you know you could pick up a wifi 6 lite model from unifi for $99 ;) Clickity Clickity whatever vlan ID you want to be on.. And it mounts in the ceiling and poe as a AP should be not some ancient relic from by gone days.
John, does unify have a model with (4) LAN ports? I need that for one location.
-
@ramosel sure they have a poe powered 5 port vlan capable switch $30... I wouldn't tie switch ports with my AP
AP belong in the ceiling or high on the wall, switch ports belong low near the ground ;)
-
I mean this was particularly unlucky. OpenWRT changed to a completely new switch model and this device happened to be included in that. Then the chosen target happened to have a non-obvious bug that made it appear like we were configuring it wrong.

If we had used 19.07 or 21.02 on a different device it probably would have been the 5min setup it should have. -
@stephenw10
OK, back in the saddle. I know I needed a break (not that dealing with family matters was a good break) and I felt I owed you one too.
I got the June 6 Snapshot... did they re-break it?Model Linksys WRT3200ACM Architecture ARMv7 Processor rev 1 (v7l) Target Platform mvebu/cortexa9 Firmware Version OpenWrt SNAPSHOT r19756-d5e48a1e8e / LuCI Master git-22.137.71281-d6dbeddIf I rebuild the network on the br-lan with or without the "Bridge VLAN Filtering"
I get this:root@Testbed_OpenWrt:~# bridge v port vlan-id lan4 1 PVID Egress Untagged lan3 1 PVID Egress Untagged lan2 1 PVID Egress Untagged lan1 1 PVID Egress Untagged wan 1 PVID Egress Untagged wlan0 1 PVID Egress Untagged wlan1 1 PVID Egress Untagged br-lan 1 PVID Egress Untagged root@Testbed_OpenWrt:~# uname -a Linux Testbed_OpenWrt 5.10.115 #0 SMP Mon Jun 6 08:19:20 2022 armv7l GNU/LinuxAt the time I collected the above, the VLAN filtering was invoked and working.
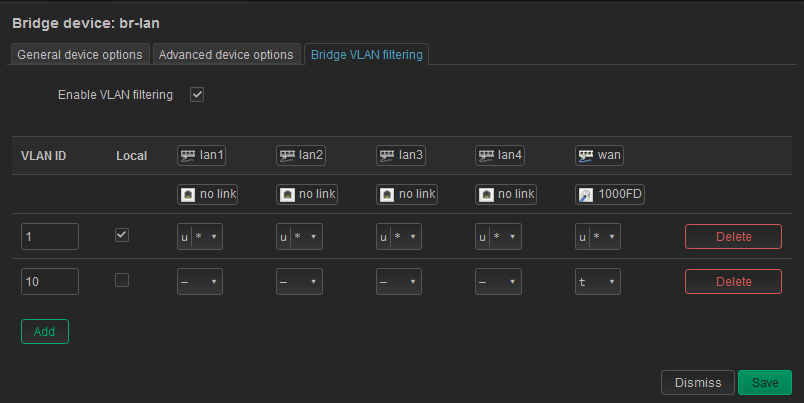
I have not upgraded WPAD as of yet. Just added LuCI and ip-bridge.
-
Hard to imagine it would have broken again but....it's always a possibility!
So you moved LAN to br-lan.1?
You need to set VLAN 10 as local in the bridge filtering so it creates a br-lan.10 device and configures the internal port to include it as tagged so the router can use it.
So for reference:
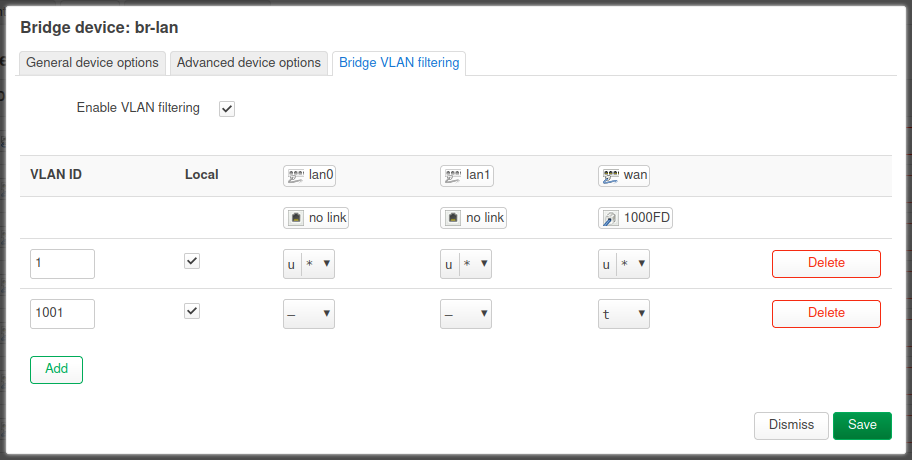
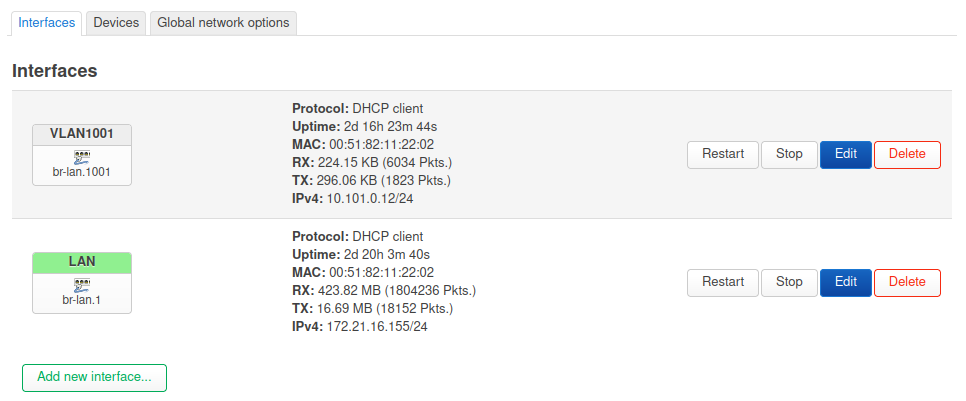
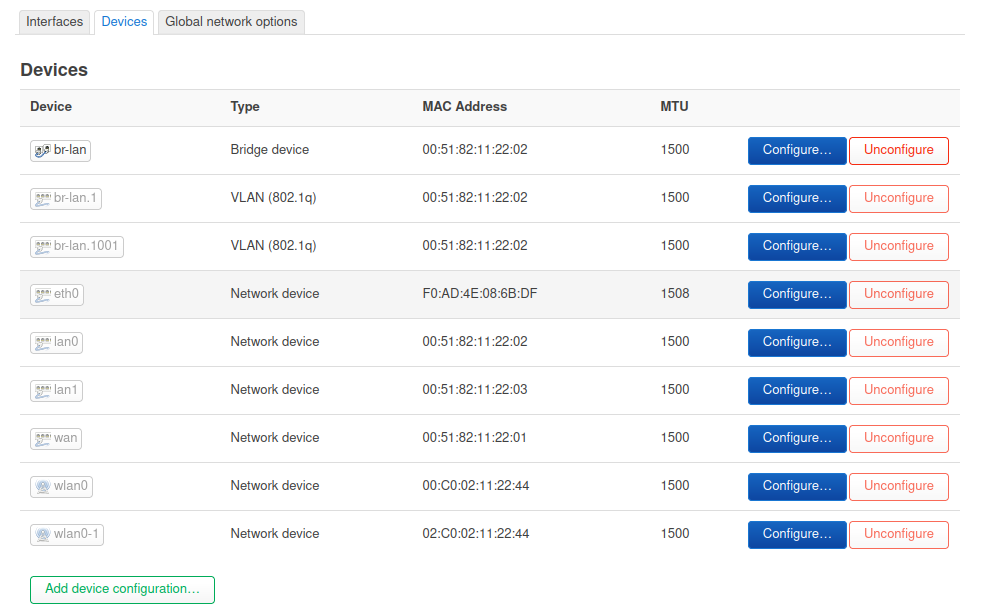
Steve
-
@stephenw10
Thanks, I'll try again.
The good news is, I now know this will work... we may not be there yet, but it will work.
The bad news is:
Yesterday, I could not get the VLAN filtering to create the .1 and .10 devices. I would just get locked out on the save and had to revert. I had to manually create them and then set the VLAN filtering as I posted yesterday. I couldn't get the bridge vlan command to show the .10 device in any manner.
I'm rural and can barely see neighbors but my security conscience tells me to shut the box off and leave this for the next day. This morning I cannot reach LuCI or the SSH. Box looks up, but I can't get to it. I was just about to reset it and had a text to come through on my old iPhone I use for initial testing. A friend sends me a link and when I open it, it's full of ads... wait, pfBlockerNG usually kills all that stuff. I guess I left that phone pinwheeling on a failed logon to GusetTest and it connected. I checked and sure enough, the Guest network is working... and assigning addresses on the correct network. So at least I'm 100% sure pfSense is correctly configured for what we are working on.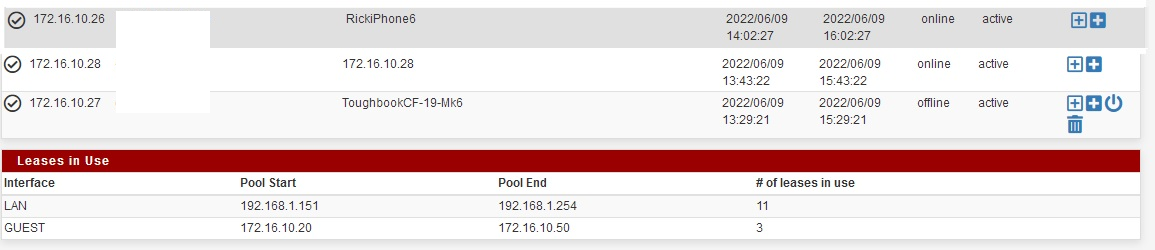
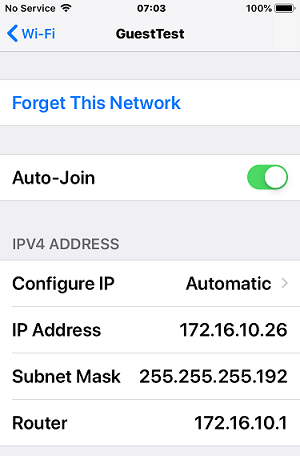
The rest of the bad news is neither of the OpenWRT SSIDs are allowing a logon at this time. At this point I don't know if that is the either/or problem on the wireless of the inability to access the primary network. What I do know is I turned off the wireless on the toughbook and plugged it into one of the LAN ports on the router and it gets a good connection and address on the 192.168.1.0 network.
-
Did you change the LAN interface to use the br-lan.1 device? With DSA doing what it's supposed to you will be locked out without that change.
It's still possible there is a bug in the WRT3200 build. The hardware details need to be correct for DSA to do the right thing with it.
I wish I could find a way to read the actual switch config. Or maybe see what DSA thinks is happening. This is a 5min task with swconfig.

Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
Did you change the LAN interface to use the br-lan.1 device? With DSA doing what it's supposed to you will be locked out without that change.
Thanks for posting that. That is what I suspected I failed to do. I may take the box apart and use a TTL connection and see if I can edit the network file to .1 device. I've got some things to do but I'll get on this later for sure this afternoon.
-
@ramosel said in pfSense with OpenWRT Guest logon with VLAN:
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
Did you change the LAN interface to use the br-lan.1 device? With DSA doing what it's supposed to you will be locked out without that change.
Thank you, Steve!!
It IS working. The Guest network logs on and gets an address on the prescribed network.root@Testbed_OpenWrt:~# bridge vlan port vlan-id lan4 1 PVID Egress Untagged lan3 1 PVID Egress Untagged lan2 1 PVID Egress Untagged lan1 1 PVID Egress Untagged wan 1 PVID Egress Untagged 10 br-lan 1 10 wlan1 1 PVID Egress Untagged wlan0 1 PVID Egress Untagged wlan1-1 10 PVID Egress UntaggedI've put some feelers out to see if/when they expect to release this fix in a 21.02.4 or a 22.xx?? I have to do some strange configuration of my physical network to make the SNAPSHOT work so if the release is imminent, I may wait to push this. My lord, what a slog.
Steve, my offer still stands on the WRT3200ACM hardware. If you'd like to have one in your test library I'll gladly ship one your way. My buddy just sent me another one so now I have a 2 backups and a spare. Just get an address to me.
John, thank you for your help as well. You helped get this ball rolling. I'm not getting old, I'm already there and this may be my last fight. I certainly have learned over the years that the more I know about something, the less I value it's quality. I'm certainly going to start gathering some of the Unify toys and learning the systems. I swore when I retired, I wasn't going to jump into anything else... but I've already broken that promise.
It just goes to show the value of the knowledge and the people in the pfSense community. I reached out on this problem to OpenWRT, Reddit and OneMarcFifty's discord. I got help to a point then it exhausted. The solution was found here.
Rick
Edit to fix the version numbers for OpenWRT. Thanks to the poster who mentioned my mistake to me. Fingers were faster than my brain.
-
Ah, great result!

Yeah, somewhat more involved that anticipated but at least we learned some things along the way. My opinion of the DSA is only slightly dulled, I'm unconvinced of it's advantages. But if everything is going that way I guess we will need to be on board.
I could certainly use a WTR3200ACM if you have spares. I'll PM you.Steve
-
This post is deleted!